当前位置:网站首页>D @ safety and dip1000
D @ safety and dip1000
2022-07-01 17:47:00 【fqbqrr】
original text
I want to know them @ Safety and dip1000 Of The goal is . Ensure the memory security of the whole program ? Multiword variable How about the data competition in the update ?
@safe Yes , But it's not simple , because main Not the only possible entry point , And there @trusted.
D at present :
Shared data must be marked "shared".@safe The code can't access shared data ( Just use -preview=nosharedaccess Make sure ). If you want to deal with shared data , To write @system/@trusted The code does not itself Make sure Thread safety .
Be careful DIP1000 Will not make @safe More secure . It allows the former @system The code becomes @safe. If you have written this kind of code , be DIP1000 Very good . without ,DIP1000 It doesn't affect you .
as follows , no need -dip1000 or -ftransition=dip1000 Compiling , But it's not safe. :
int[] global;
@safe
void f0(int[] val) {
global = val;
}
@safe
void f1() {
int[3] local = [1, 2, 3];
f0(local);
}
DIP 1000 Will refuse .
Yes , Myna quite a lot . If Myna Not through -preview=dip1000 Show it , Then it is more impossible to scold it . because DIP1000 Will eventually become Default , The problem will disappear .
vice versa :-preview=dip1000 Yes Loophole , Without a switch No, . But these are more likely Get fixed , Because someone really cares about finishing DIP1000.
d author : Even though @safe Does not provide complete memory security , but @live Make up for other parts .
Programmers can manually With a lock To avoid Multiword variable Data competition in .
pb:
Um. ? I understand that even if there is no @live, Modular compiler Errors and misuse @trusted,@safe The code should be 100% Memory safe .
add to ownership / To borrow What the system does ( or Should be done Of ), image DIP1000 equally , Can be found in @safe In the code , You need to work in @system/@trusted Things , such as Manual memory release .
Implemented today @safe The problem is pressing The blacklist To achieve it .
I said, " should " and " Module compiler error " yes with reason Of .
however , That is to use White list Realization , There is still a Should not go further White list error . for example , Several recent fixes -preview=dip1000 Of , It's for This type of error .
Yes , Misuse @trusted,@live Only in @ System /@ Security As Check Tools are a little useful .@live Not done ownership / To loan What the system should do . I have pointed out , But most people still seem to assume that . I don't understand why . The proposed design has been public for a long time , It's obvious that @safe Almost useless in code , because @live That's it. Function Annotations .@live comparison ownership / To loan , It's very superficial , Therefore, it is of little use .
To borrow / Check Systems and ownership There are two things . To borrow / The viewer Ensure once Only one variable access or Multiple invariants visit . ownership And Manage memory yes relevant Yes, but Completely different The theme of .Rust in notorious Of ownership The system because Mobile semantics , Only... Are allowed at a time An ownership .
D Medium To borrow / The viewer , I haven't Fully understand What problems should it solve .
In my submission , stay @safe It is allowed that Original pointer It's a basic mistake . stay @safe In the code , Be similar to C#/Java/ other , Should be Completely opaque Of Manage memory . It's easier , and D It's complicated .
@live To write @[email protected] The code doesn't help .
In order to make @safe or @trusted Code dependency @live Of Ownership invariants ,( for example ,“ Non domain The pointer has Point to memory ”),@safe Code cannot violate These invariants . because @live The invariant of is only in @live Function to enforce , And allow @safe Code calls non @live function , The result is , allow @safe Code violation @live invariant , therefore @safe or @trusted Code cannot rely on These invariants .
To solve this problem , New rules must be introduced , for example :
1, all @safe The function must also be @live.
2,@safe Function cannot call Not @live function .
Of course , Adding such rules will actually destroy every existing D Every one of the projects @safe function , It is completely infeasible in practice , This is the current @live Design is the reason for the dead end .
No, @live, Can't prevent Release twice .@live Only... Are allowed at a time One ownership , And with the Mobile semantics relation .
If you write @safe Code , Has received Protect . No more @live.
边栏推荐
- What are the legal risks of NFT brought by stars such as curry and O'Neill?
- [wrung Ba wrung Ba is 20] [essay] why should I learn this in college?
- Penetration practice vulnhub range Nemesis
- Research Report on development prediction and investment direction of nylon filament sewing thread in China (2022 Edition)
- Depth first traversal and breadth first traversal [easy to understand]
- February 16, 2022 Daily: graph neural network self training method under distribution and migration
- Nielseniq found that 60% of the re launched products had poor returns
- Thinkphp6 - CMS multi wechat management system source code
- Petrv2: a unified framework for 3D perception of multi camera images
- 官宣!香港科技大学(广州)获批!
猜你喜欢

Penetration practice vulnhub range Keyring
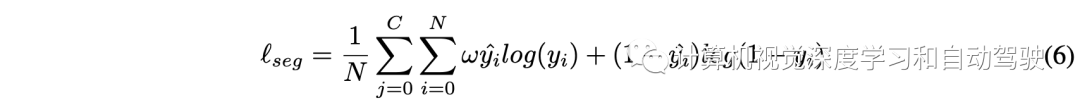
PETRv2:一个多摄像头图像3D感知的统一框架
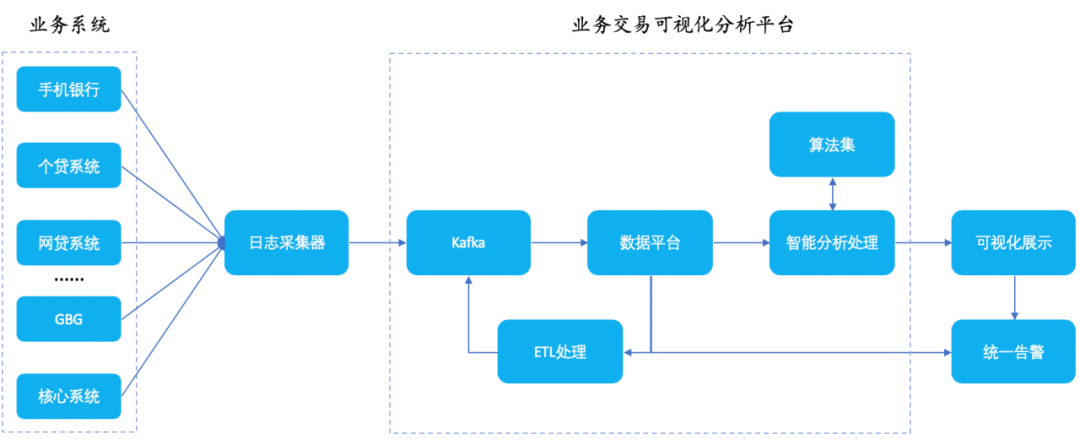
Intelligent operation and maintenance practice: banking business process and single transaction tracking
Oom caused by improper use of multithreading

Cassette helicopter and alternating electric field magnetic manometer DPC
There is a new breakthrough in quantum field: the duration of quantum state can exceed 5 seconds

In aks, use secret in CSI driver mount key vault

Gold, silver and four want to change jobs, so we should seize the time to make up

Intel's open source deep learning tool library openvino will increase cooperation with local software and hardware parties and continue to open

Kernel stray cat stray dog pet adoption platform H5 source code
随机推荐
pyqt5中,在控件上画柱状图
ISO 27001 Information Security Management System Certification
Debiasing word embeddings | talking about word embedding and deviation removal # yyds dry goods inventory #
MySQL -- explain performance optimization
MES production equipment manufacturing execution system software
中国锦纶长丝缝纫线发展预测与投资方向研究报告(2022版)
China metallocene polyethylene (MPE) Industry Research Report (2022 Edition)
【Try to Hack】vulnhub DC4
RadHat搭建内网YUM源服务器
提交review时ReviewBoard出现500错误解决方法
Thinkphp6 - CMS multi wechat management system source code
Nielseniq found that 60% of the re launched products had poor returns
Sword finger offer II 105 Maximum area of the island
The reviewboard has 500 errors when submitting a review. Solutions
vulnhub靶场-hacksudo - Thor
Penetration practice vulnhub range Keyring
Source code of new campus errand / campus task platform on mutual station
中国一次性卫生用品生产设备行业深度调研报告(2022版)
Openlayers customize bubble boxes and navigate to bubble boxes
[mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code