当前位置:网站首页>Good looking UI mall source code has been scanned, no back door, no encryption
Good looking UI mall source code has been scanned, no back door, no encryption
2022-07-01 17:32:00 【banzhuan678】
brief introduction :
Based on Hongmeng network, develop a product based on PHP+MySQL Developed virtual commodity system sharing , Use D After scanning the shield, there is no back door to encrypt the file , You can download the reference if necessary
Download address of online disk :
http://zijiepan4.xyz/6tMtGjTuHhu0
picture :


边栏推荐
- 【C语言基础】12 字符串
- [splishsplash] about how to receive / display user parameters, MVC mode and genparam on GUI and JSON
- Research Report on development monitoring and investment prospects of China's smart environmental protection industry (2022 Edition)
- Pytest learning notes (13) -allure of allure Description () and @allure title()
- There is a new breakthrough in quantum field: the duration of quantum state can exceed 5 seconds
- (1) CNN network structure
- Mysql database - Advanced SQL statement (2)
- How to write good code - Defensive Programming Guide
- 开发那些事儿:EasyCVR集群设备管理页面功能展示优化
- Redis distributed lock
猜你喜欢
String的trim()和substring()详解
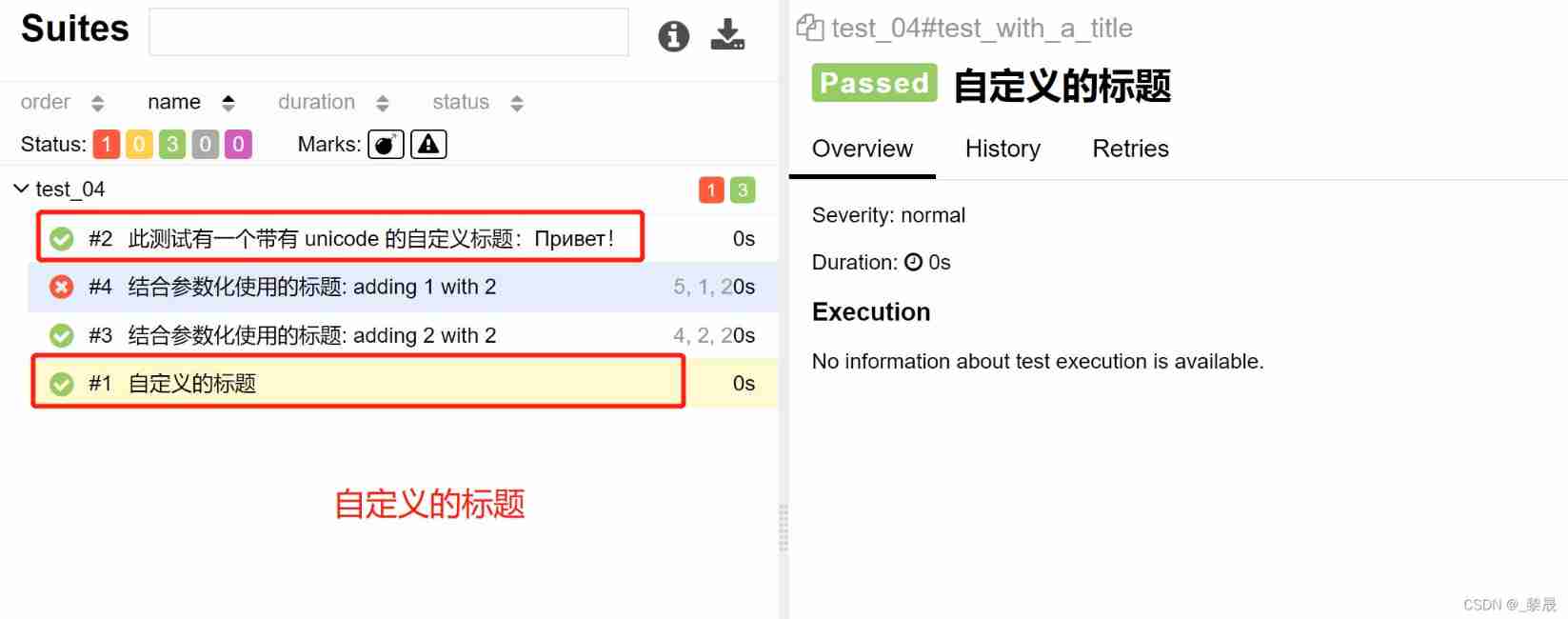
Pytest learning notes (13) -allure of allure Description () and @allure title()

Sword finger offer 20 String representing numeric value
![[mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code](/img/de/1f572c62a0d034da9a8acb5c2f9602.jpg)
[mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code

SQL注入漏洞(Mysql与MSSQL特性)
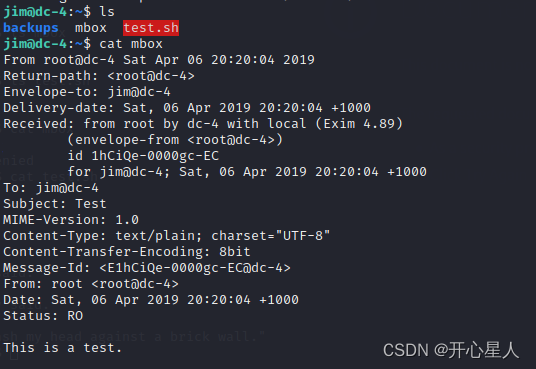
【Try to Hack】vulnhub DC4
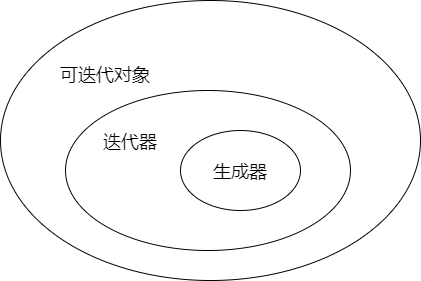
The difference and relationship between iteratible objects, iterators and generators

Yyds dry inventory MySQL RC transaction isolation level implementation
Why should you consider using prism
vulnhub靶场-Hacker_Kid-v1.0.1
随机推荐
unity3d扩展工具栏
In aks, use secret in CSI driver mount key vault
Report on Market Research and investment prospects of ammonium dihydrogen phosphate industry in China (2022 Edition)
如何使用 etcd 实现分布式 /etc 目录
pyqt5中,在控件上画柱状图
Depth first traversal and breadth first traversal [easy to understand]
Unity3d extended toolbar
Petrv2: a unified framework for 3D perception of multi camera images
C language implementation of sum of two numbers [easy to understand]
Research Report on development prediction and investment direction of nylon filament sewing thread in China (2022 Edition)
Openlayers customize bubble boxes and navigate to bubble boxes
中国茂金属聚乙烯(mPE)行业研究报告(2022版)
(12) About time-consuming printing
Gaussdb (for MySQL):partial result cache, which accelerates the operator by caching intermediate results
MySQL learning summary
Develop those things: easycvr cluster device management page function display optimization
剑指 Offer 20. 表示数值的字符串
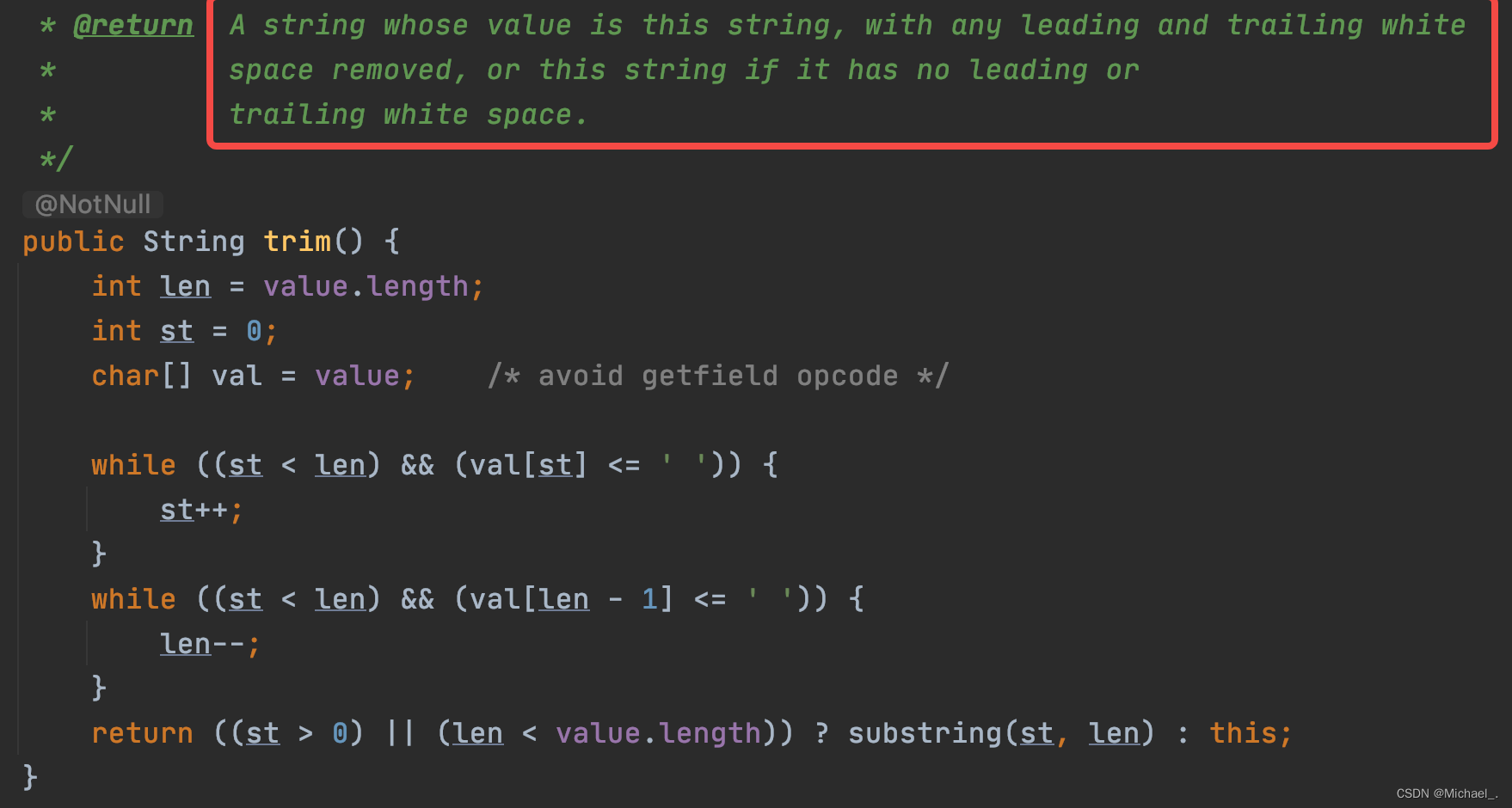
String的trim()和substring()详解
How to write good code - Defensive Programming Guide
Mysql database - Advanced SQL statement (2)