当前位置:网站首页>SQL injection vulnerability (MySQL and MSSQL features)
SQL injection vulnerability (MySQL and MSSQL features)
2022-07-01 17:26:00 【errorr0】
front MySQL I talked a lot , But I forgot to say Mysql database Some characteristics of , So I'm talking about MSSQL Inject front , I put Mysql database Let's talk about some details in .
Mysql
With phpstudy Integrated MySQL Come on , Its database exists phpstudy/PHPTutorial/MySQL/data in
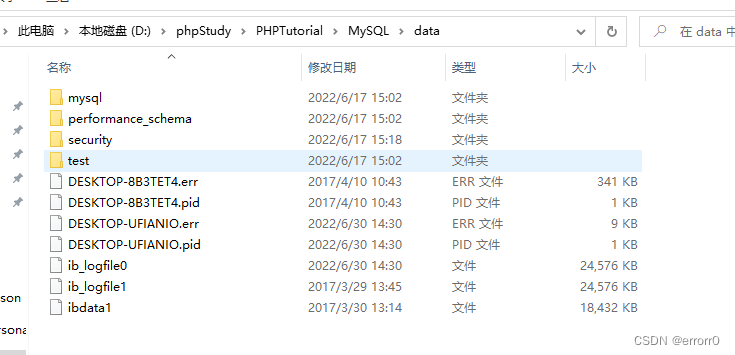
You can directly see that we have four databases :mysql、performance_schema、security、test. So we're in MySQL Command line terminal show databases have a look .
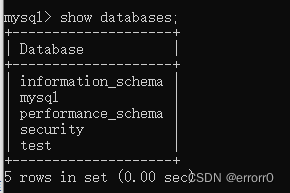
You can see one more Library information_schema, That is, this library allows attackers to have a more convenient and unified way to check the database and table after finding the closure payload,information_schema Inventory lies in MySQL5.1+, And in version 5 This library didn't exist before .
The original intention of designing this library is for administrators to query and modify the library more conveniently . But there's no way , Once convenient for administrators , If the administrator falls , It is convenient for attackers .
If you need to get the information in the database , There are several key tables in this library that need to be learned together ,
SCHEMATA surface : Provides the current mysql Information of all databases in the instance . yes show databases Is the result of this table .
TABLES surface : Provides information about tables in the database ( Include views ). It describes in detail which table belongs to schema, Table type , Watch engine , Creation time and other information . yes show tables from schemaname Is the result of this table .
COLUMNS surface : Provides column information in the table . Specifies all the columns of a table and the information for each column . yes show columns from schemaname.tablename Is the result of this table .
besides , We also need to know some column names in the table

There is a table_schema, This thing is the database name , So we can do some research on this library where The limit is reached. You want to query the tables in the Library .

This watch is a little ugly , Just read what I wrote .
We can see it up here columns There is a column name in the table table_name, This thing means the name of the data table , That is, we can finally query the data in the table by limiting the table name .
It's almost MySQL Inject the most conventional knowledge points , Here's a simple one Check the library 、 Look up the table 、 List 、 Check field Of payload.
Check the library :-1' union select 1,2,group_concat(schema_name) from information_schema.schemata--+
Look up the table :-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = 'security'--+
List :-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name = 'users'--+
Check field :-1' union select 1,group_concat(id),group_concat(concat_ws('~',username,password)) from users--+over, Next, let's talk about today's focus ,MSSQL Inject .
MSSQL
Usually SQL Inject Our study is mainly aimed at MySQL database , Here's a wake-up call , If MySQL database If you are not familiar with the injection of, it is recommended to brush more sqli-labs To consolidate MySQL, Otherwise, if you learn everything, it's easy to be unfamiliar, messy and easy to forget .
MSSQL Also known as SQL server database , And MySQL The similarity is still very high , Because of and MySQL Very similar , There are some MySQL I won't elaborate on what I have said .
Pre knowledge
And MySQL identical ,MSSQL Similar to MySQL in information_schema The default existence of the library can be easily queried , Although it is not a library .
MSSQL There are three default tables in each database sysdatabases、sysobjects、syscolumns
sysdatabases : The table is saved in master In the database , All the database names are saved in this table , And Library ID, And some related information .
sysobjects: SQL-SERVER This system table exists in every database of , It stores all the objects created in the database , Such as restraint 、 The default value is 、 journal 、 The rules 、 Stored procedure, etc , Each object occupies a row in the table .
syscolumns: The table is located in each database , It contains all the column names in this library .
Knowing the meaning of three tables, we can use this to query any data we want , But in addition to the database table, the other two of the three tables store some constraint 、 The default value is 、 journal wait , These storage will affect our query of sensitive data , At this time, we need to find a column to classify which are some restricted storage , What are some data stores .

You can see sysdatabases The only content in the database table is the database
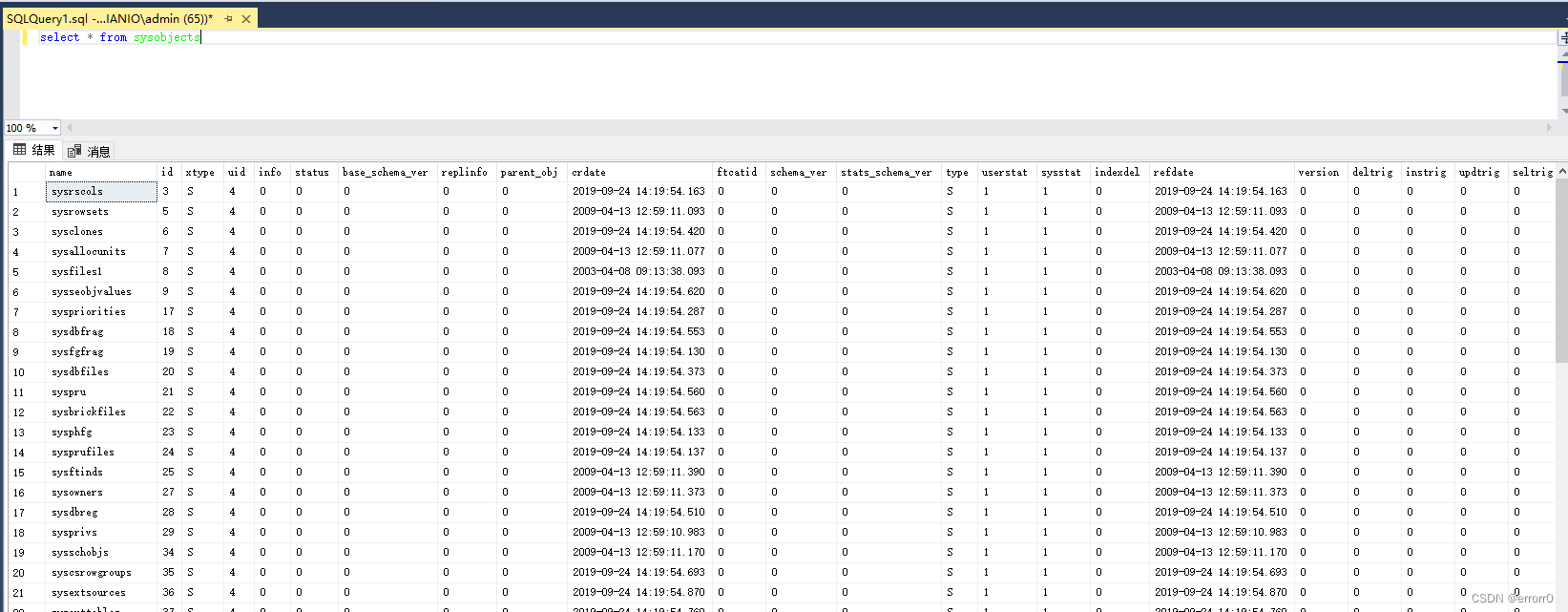
sysobjects A pile of watches , There is everything , So I found a classification standard , That's one of them xtype
| xtype | char(2) | object type . Common Columns .xtype It can be one of the following object types : C = CHECK constraint D = Default value or DEFAULT constraint F = FOREIGN KEY constraint L = journal FN = Scalar function IF = Embedded table functions P = stored procedure PK = PRIMARY KEY constraint ( The type is K) RF = Copy filter stored procedure S = The system tables TF = Table function TR = trigger U = User table UQ = UNIQUE constraint ( The type is K) V = View X = Extended stored procedure |
You can see ,U type It's the user table , So we use this restriction to query

success , You can see all four data sheets . Finally, there is only one question left , That is how to find the key list we want to find . because syscolumns Not only the columns in the data table are stored in , And views , Many of these also greatly affect our query of data , So we still need to use a column to distinguish them .
After my inquiry and study, I learned ,sysobjects Medium id Column and syscolumns Medium id Column Foreign key link , What do you mean ? in other words syscolumns There is one in the column of id Means corresponding to sysobjects Medium id, And our watch is from sysobjects Zhongdelai , What's interesting is that we can pass on sysobjects Medium id get syscolumns Column data for , Finally, it's easy to check the fields .

select * from syscolumns where id=(select id from sysobjects where name='users')
Or you can check directly id Plug in
select * from syscolumns where id=885578193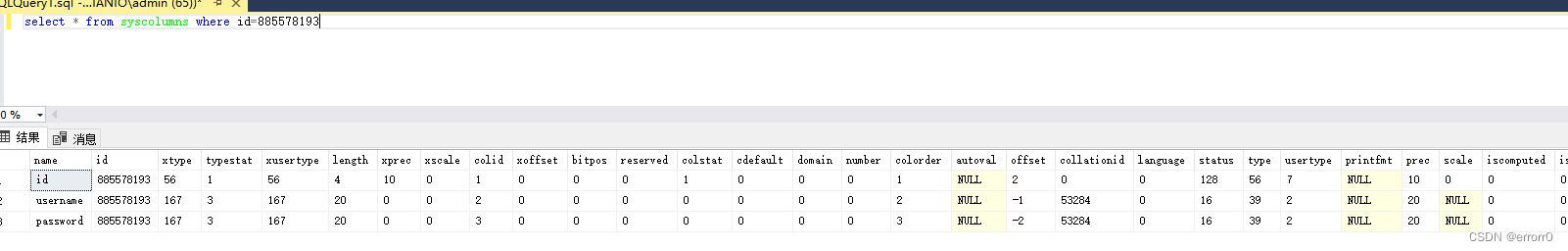
Only this and nothing more ,MSSQL Exists by default in library 、 surface 、 Column That's all , Next, I want to put us in SQL Inject Some common functions that need to be used in .
| function | paraphrase |
|---|---|
| host_name() | Returns the name of the server-side computer |
| Current_user | Returns the user of the current database |
| db_name () | Returns the name of the current database |
| CHAR() | take ASCII Code to character , If there is no input 0 ~ 255 Between ASCII Code value ,CHAR() return NULL |
| Object_id() | Return the database table name , Usually used for 16 Base or SQL Code conversion |
| col_name ( table_id , column_id ) | Returns the specified field in the specified table |
| Substring() | Returns a substring , example :substring(“123456” ,1,3) return “123” |
| Cast() | Explicitly converting an expression of one data type to another |
MSSQL.
MMSQL The features of are almost the same , Let's talk about a few more topics later
Reference resources :SQL Injected Mssql Inject _ Yuanyuan's blog -CSDN Blog _mssql Inject
know SQLSERVER Medium syscolumns surface - Programming house
SQL Database system tables sysobjects What's in it ??_ Baidu knows
边栏推荐
- 判断一棵二叉树是否为平衡二叉树
- Is the securities account given by the head teacher of goucai school safe? Can I open an account?
- Sword finger offer 20 String representing numeric value
- 深度优先遍历和广度优先遍历[通俗易懂]
- 拼接字符串,得到字典序最小的结果
- Redis6.0 新功能
- Integer array merge [JS]
- 提交review时ReviewBoard出现500错误解决方法
- Soft test network engineer full truth simulation question (including answer and analysis)
- (28) Shape matching based on contour features
猜你喜欢
Redis Distributed Lock
vulnhub靶场-hacksudo - Thor
Vulnhub range hacker_ Kid-v1.0.1

Iommu/smmuv3 code analysis (10) page table operation
字节跳动数据平台技术揭秘:基于 ClickHouse 的复杂查询实现与优化

Girls who want to do software testing look here

(27) Open operation, close operation, morphological gradient, top hat, black hat

Mysql database - Advanced SQL statement (2)
String的trim()和substring()详解
Pytest learning notes (13) -allure of allure Description () and @allure title()
随机推荐
美国国家安全局(NSA)“酸狐狸”漏洞攻击武器平台技术分析报告
(十六)ADC转换实验
SQL question brushing 586 Customers with the most orders
JDBC: deep understanding of Preparedstatement and statement[easy to understand]
中国氮化硅陶瓷基板行业研究与投资前景报告(2022版)
判断一棵二叉树是否为平衡二叉树
SQL注入漏洞(Mysql与MSSQL特性)
整形数组合并【JS】
换掉UUID,NanoID更快更安全!
中国超高分子量聚乙烯产业调研与投资前景报告(2022版)
MySQL learning summary
Free lottery | explore the future series of blind box digital copyright works of "abadou" will be launched on the whole network!
Flux d'entrées / sorties et opérations de fichiers en langage C
China biodegradable plastics market forecast and investment strategy report (2022 Edition)
荣威 RX5 的「多一点」产品策略
China sorbitol Market Forecast and investment strategy report (2022 Edition)
越来越多地使用 SLO 来实现可观测性|DevOps
Report on research and investment prospects of UHMWPE industry in China (2022 Edition)
Research Report on development monitoring and investment prospects of China's smart environmental protection industry (2022 Edition)
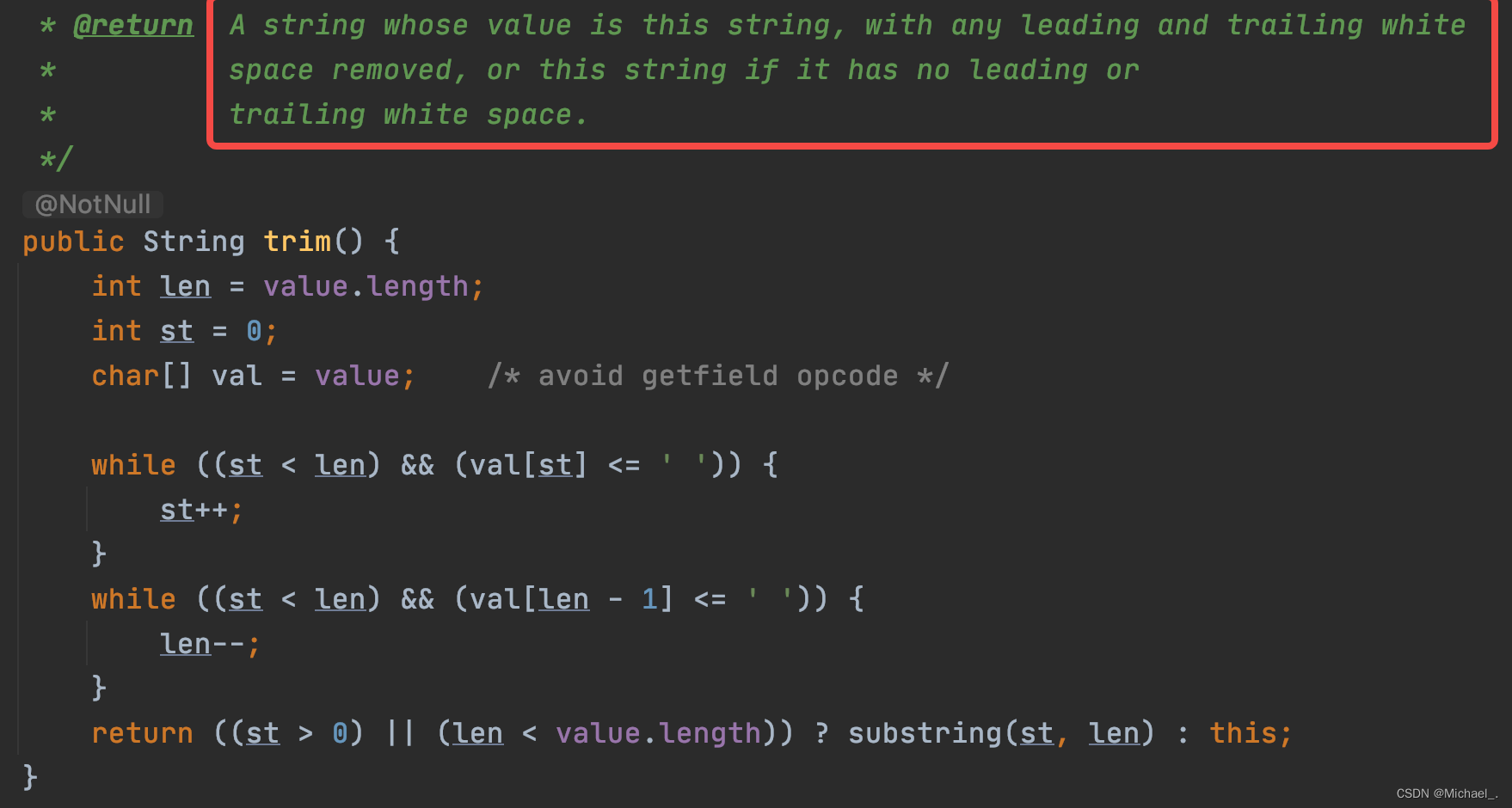
Detailed explanation of string's trim() and substring()