当前位置:网站首页>What should I do if my computer sharing printer refuses access
What should I do if my computer sharing printer refuses access
2022-07-04 20:41:00 【Xiaobai one click reinstallation system】
Why is access denied when connecting a shared printer to a computer ? Friends who often use printers , Often share a printer with multiple computers , What should I do if the computer sharing printer refuses access ? Here is a way to share with you .
There are more details System reassembly Tutorials are available for reference
1、 With win10 Take the system as an example , Right click the start menu icon on the desktop , Then select run to open the run window , Or you can go directly through win+r Shortcut key to open .

2、 Then enter gpedit.msc Press enter again .

3、 In the window of local security policy , In the left column, follow the security settings - The local policy - Click to open the configuration of user permission assignment .

4、 Then find the service item of accessing this computer from the network in the expanded right window , Right click and then click properties .

5、 Then click add user or group in the properties window of accessing this computer from the network .

6、 Click Advanced... In the window that appears to select users or groups .

7、 Then see this interface and click find now , Then click the user name as Guest Users of , Then click ok .

8、 Then double click to open the service item of denying access to this computer from the network .

9、 Then click the user name again Guest Users of , Click delete and then click OK to complete .

Why is access denied when connecting a shared printer to a computer ? Friends who often use printers , Often share a printer with multiple computers , What should I do if the computer sharing printer refuses access ? Here is a way to share with you .
1、 With win10 Take the system as an example , Right click the start menu icon on the desktop , Then select run to open the run window , Or you can go directly through win+r Shortcut key to open .

2、 Then enter gpedit.msc Press enter again .

3、 In the window of local security policy , In the left column, follow the security settings - The local policy - Click to open the configuration of user permission assignment .

4、 Then find the service item of accessing this computer from the network in the expanded right window , Right click and then click properties .

5、 Then click add user or group in the properties window of accessing this computer from the network .

6、 Click Advanced... In the window that appears to select users or groups .

7、 Then see this interface and click find now , Then click the user name as Guest Users of , Then click ok .

8、 Then double click to open the service item of denying access to this computer from the network .

9、 Then click the user name again Guest Users of , Click delete and then click OK to complete .

边栏推荐
- QT writing the Internet of things management platform 38- multiple database support
- Flet教程之 06 TextButton基础入门(教程含源码)
- Flet教程之 05 OutlinedButton基础入门(教程含源码)
- 电脑页面不能全屏怎么办?Win11页面不能全屏的解决方法
- go笔记(3)Go语言fmt包的用法
- Integretee integrates into Moonriver through xcm, bringing enterprise class privacy solutions to its ecosystem
- Wireshark network packet capture
- 泰山OFFICE技术讲座:关于背景(底纹和高亮)的顺序问题
- Practice examples to understand JS strong cache negotiation cache
- YOLOv5s-ShuffleNetV2
猜你喜欢
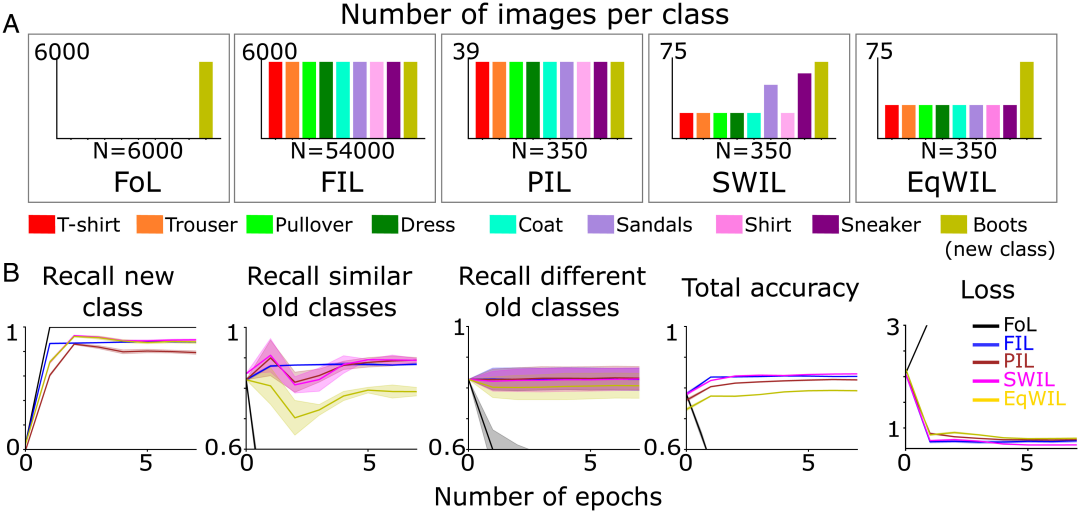
针对深度学习的“失忆症”,科学家提出基于相似性加权交错学习,登上PNAS
B2B mall system development of electronic components: an example of enabling enterprises to build standardized purchase, sale and inventory processes
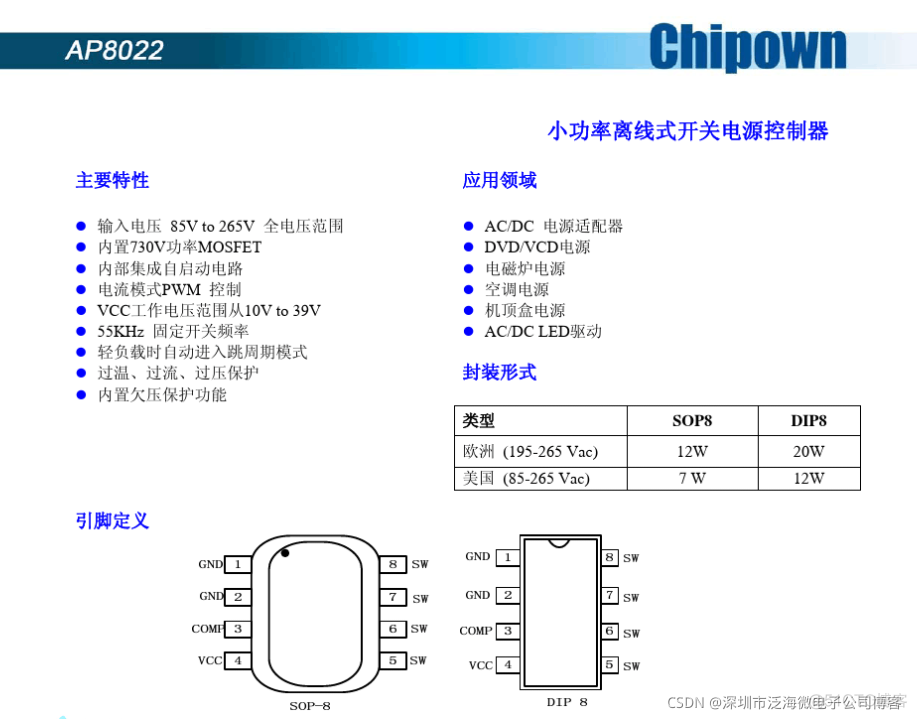
AP8022开关电源小家电ACDC芯片离线式开关电源IC
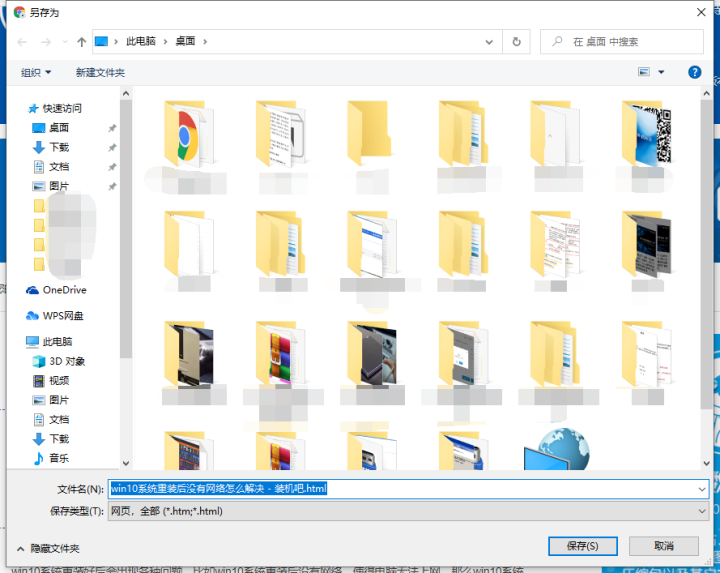
电脑怎么保存网页到桌面上使用
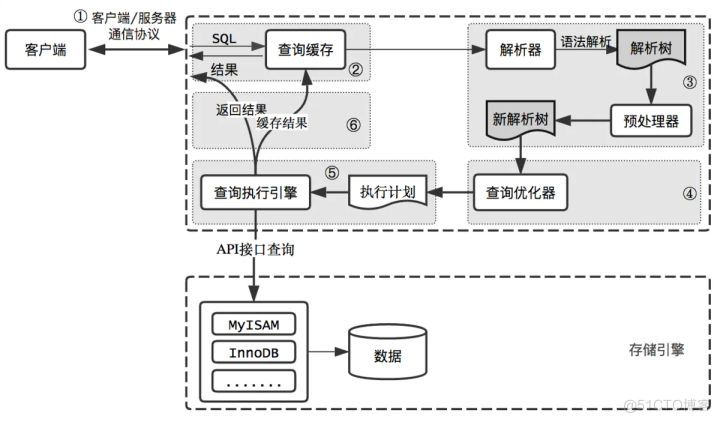
How is the entered query SQL statement executed?
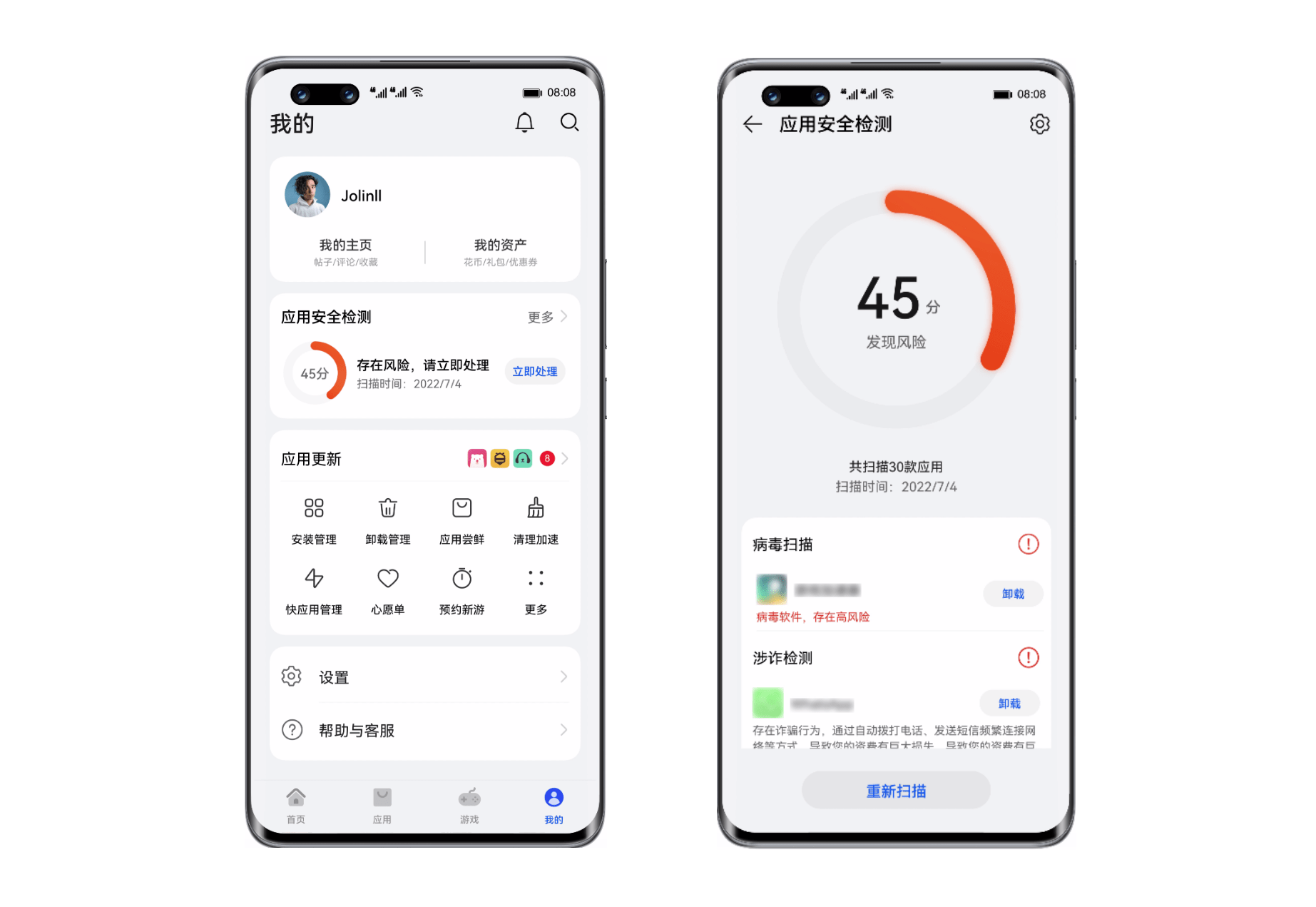
Huawei Nova 10 series supports the application security detection function to build a strong mobile security firewall
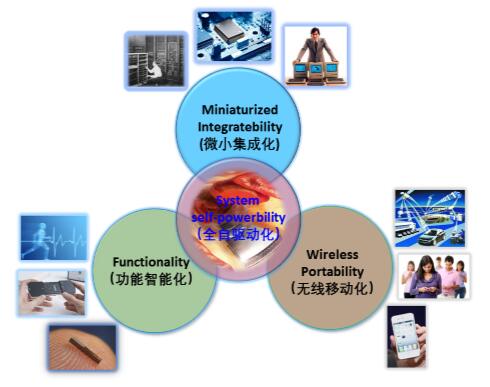
What is the application technology of neural network and Internet of things
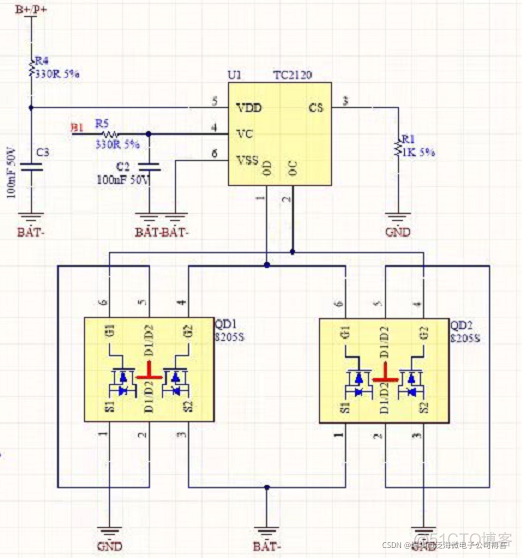
FS4061A升压8.4V充电IC芯片和FS4061B升压12.6V充电IC芯片规格书datasheet
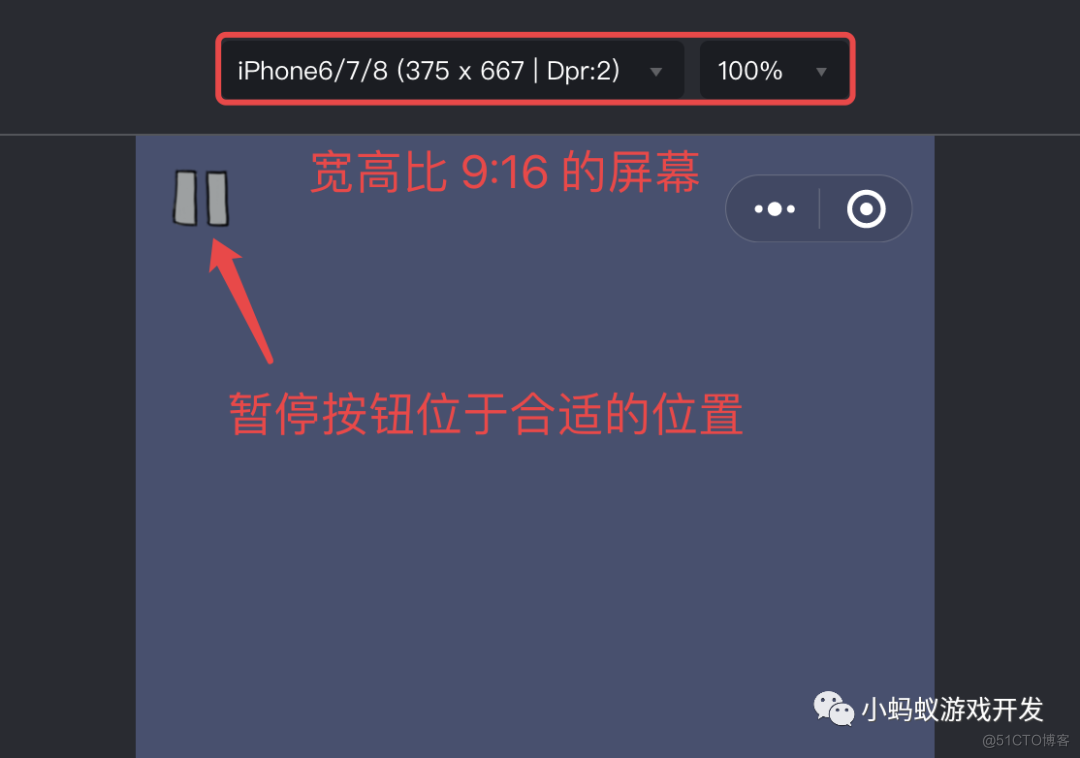
如何让你的小游戏适配不同尺寸的手机屏幕
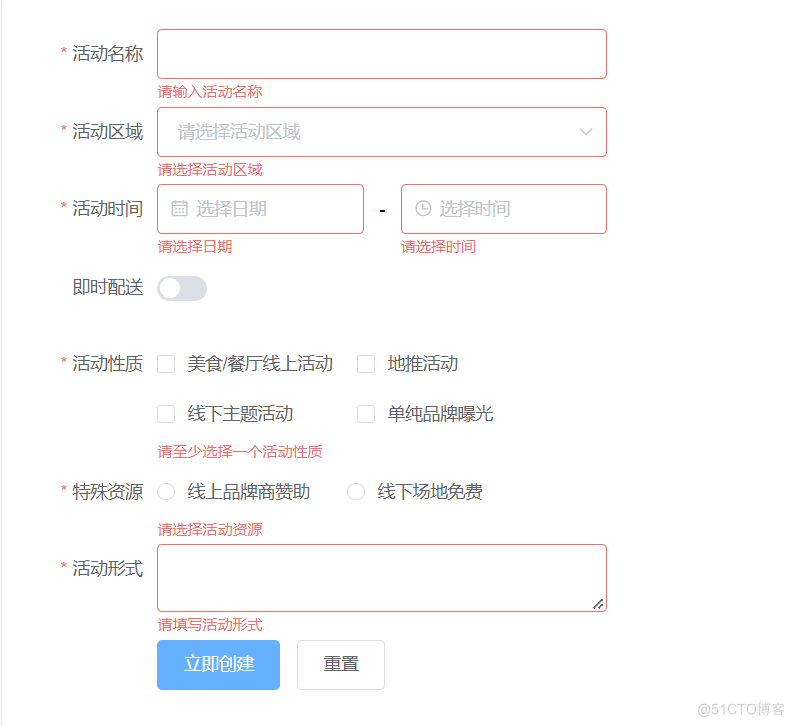
Common verification rules of form components -1 (continuously updating ~)
随机推荐
2022 Health Exhibition, Beijing Health Expo, China Health Exhibition, great health exhibition November 13
哈希(Hash)竞猜游戏系统开发功能分析及源码
什么是区块哈希竞猜游戏系统开发?哈希竞猜游戏系统开发(案例成熟)
电脑怎么保存网页到桌面上使用
软件客户端数字签名一定要申请代码签名证书吗?
C server log module
Regular replacement [JS, regular expression]
Process of manually encrypt the mass-producing firmware and programming ESP devices
Why is the maximum speed the speed of light
Is it necessary to apply for code signing certificate for software client digital signature?
强化学习-学习笔记2 | 价值学习
Flet教程之 08 AppBar工具栏基础入门(教程含源码)
Optimization cases of complex factor calculation: deep imbalance, buying and selling pressure index, volatility calculation
栈:如何实现有效括号的判断?
Detailed explanation of Audi EDI invoice message
Optimize if code with policy mode [policy mode]
C # better operation mongodb database
【深度学习】一文看尽Pytorch之十九种损失函数
On communication bus arbitration mechanism and network flow control from the perspective of real-time application
实践示例理解js强缓存协商缓存