当前位置:网站首页>Information Security Experiment 3: the use of PGP email encryption software
Information Security Experiment 3: the use of PGP email encryption software
2022-07-07 09:22:00 【Not enough to eat】
One 、 Purpose and requirements of the experiment
1. Familiar with public key cryptosystem , Understand the basic principle of certificate , Familiar with digital signature ;
2. Skillfully use PGP Basic operation , It can encrypt mail or transmission documents ;
Two 、 Experimental content
1 Create a private key and public key pair
Use PGPtray Before , Need to use PGPkeys Generate a pair of keys , Including private key ( Only itself can access ) And a public key ( Can let exchange E-Mail People are free to use ).
2 Exchange public keys with others
After creating the key pair , You can work with others PGP Users communicate . To use encrypted communication , Then they need their public key . And if they want to communicate with you, they also need your public key . A public key is a block of information , Publish public key ( You can put the public key on the key server , You can also paste the public key to a file or E-Mail Zhongfa wants to exchange with it E-Mail People who ).
3 Verify the public key and make it valid
When getting someone's public key , Add it to the public key ring . First, determine the accuracy of the public key . When it is determined that this is a valid public key , You can sign to show that you think this key can be used safely . in addition , It can also give the owner of this public key a certain degree of trust .
4 Yes E -Mail Encrypt and digitally sign
When the key pair is generated and the key has been exchanged , You can do that. E–Mail Information and files are encrypted and digitally signed . If used E–Mail Application support plug_ins, Choose the appropriate option to encrypt ; If E–Mail The application does not support plug_ins, It can be E–Mail The information is sent to the clipboard and encrypted from there . If you also want to include some documents , It can be downloaded from Windows Exporer Encrypt and digitally sign on , And then hang up to E–Mail Send .
5 Yes E-Mail Decrypt and verify
When someone sends you encrypted E–Mail when , Break down the content , At the same time, the additional signature is verified to confirm that the data is sent from the determined sender and has not been modified . If used E–Mail Application support plug_ins, Choose the appropriate option to encrypt ; If E–Mail The application does not support plug_ins, It can be E–Mail The information is sent to the clipboard for encryption , Copy the information to the clipboard and decrypt . If you also want to include some documents , It can be downloaded from Windows Exporer Decrypt on .
3、 ... and 、 Experimental environment
function Windows XP/2000 The computer of the operating system .
Four 、 Experimental steps and result analysis
1. Create a private key and public key pair
1.1 Create user
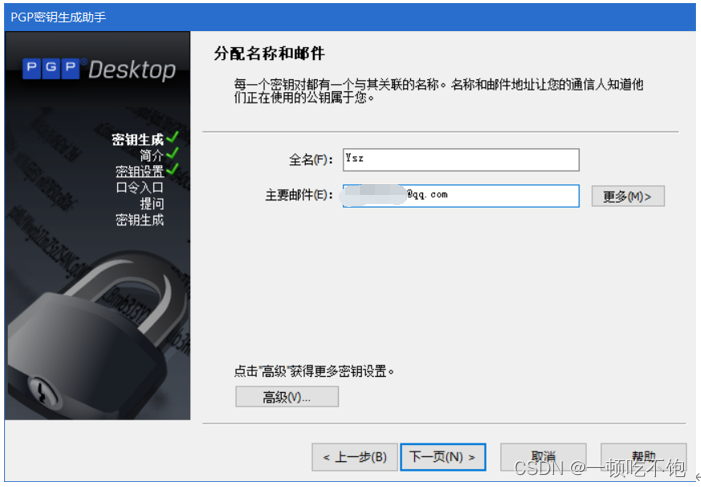
1.2 Generate private key pair and public key pair
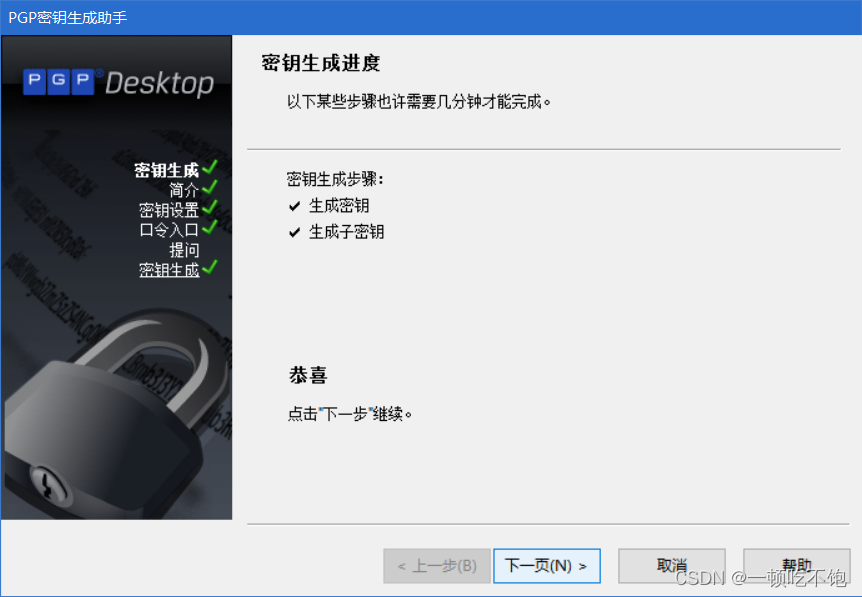
Successfully created
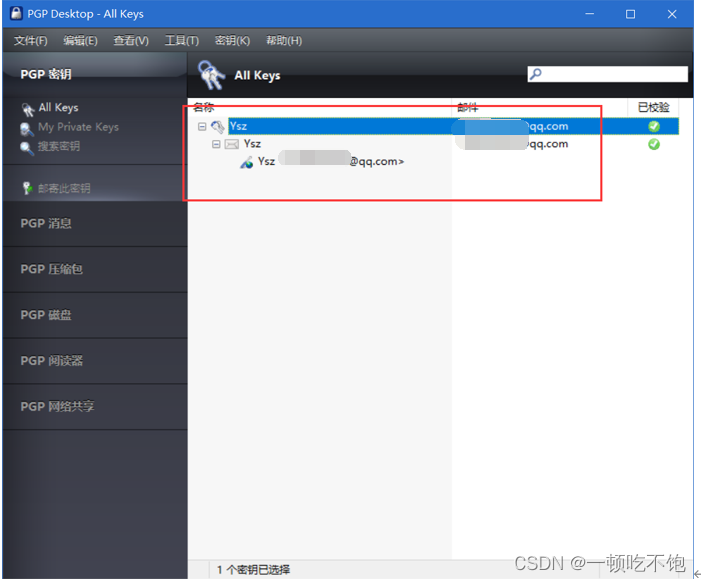
2、 Exchange public keys with others
2.1 Export public key
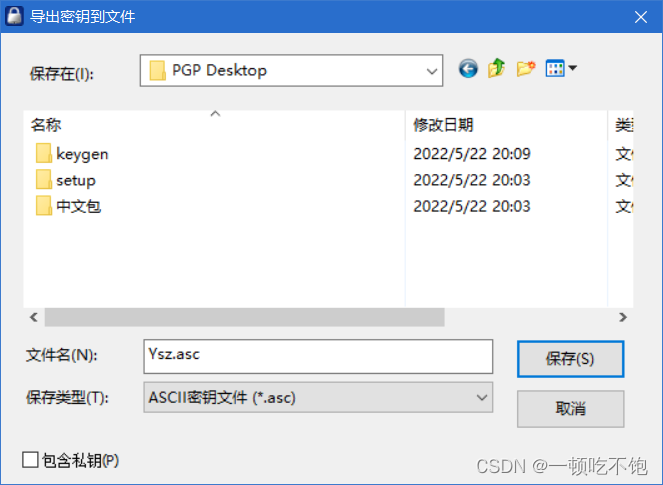
2.1 Send the public key to the other party of the communication
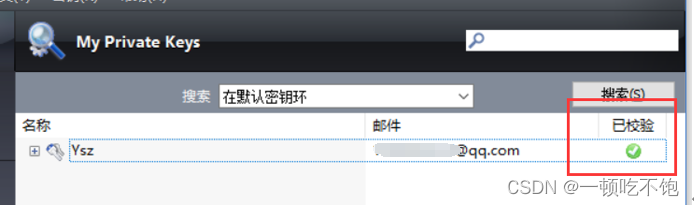
3 Verify the public key and make it valid
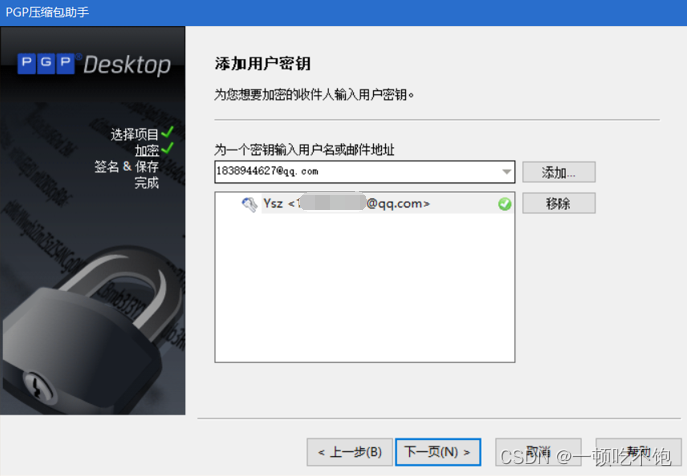
4、 Yes E -Mail Encrypt and digitally sign
4.1 Encrypt file

Add key
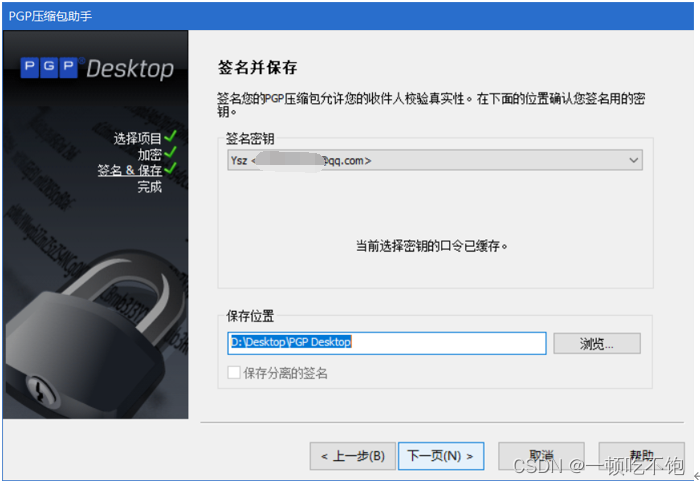
4.2 Digitally sign
4.3 Send the encrypted file to the other party
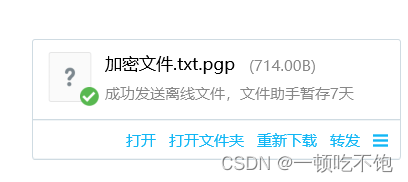
5、 Yes E-Mail Decrypt and verify
5.1 Decrypt the file after receiving it
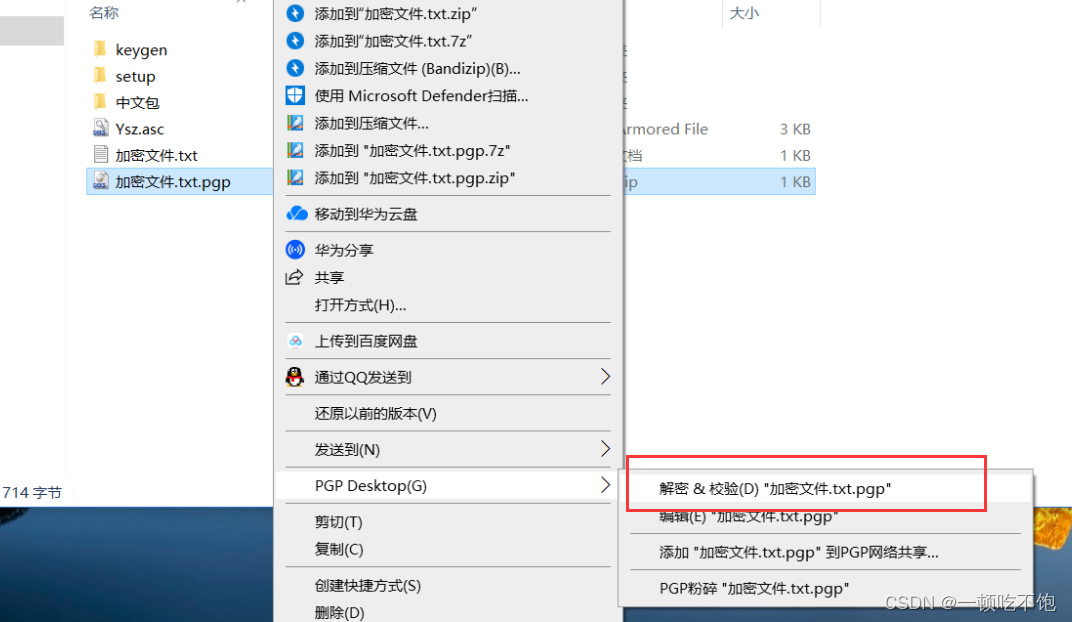
5.2 Decryption succeeded
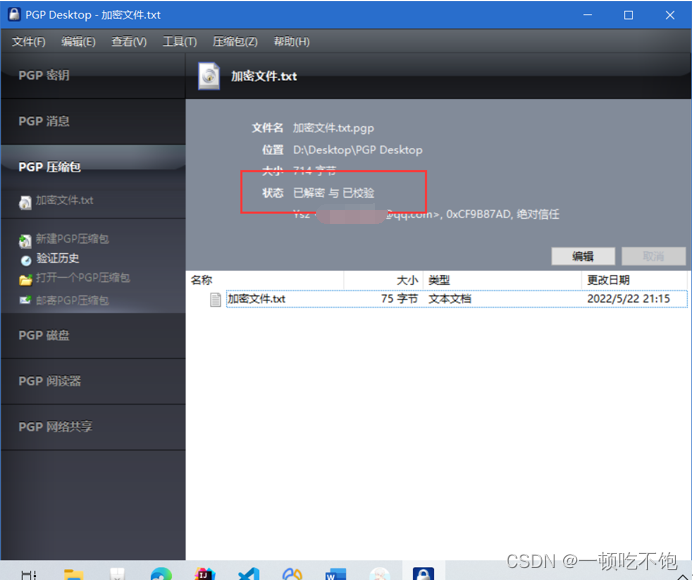
- Summary of the experiment
Through this experiment , I am right. PGP With a deeper understanding .PGP Is a complete e-mail security software package , Include encryption 、 To identify 、 Electronic signature and compression technology .PGP It can provide information protection functions on independent computers , Make this security system more complete . It can be used to keep messages confidential to prevent unauthorized people from reading , It can also digitally sign the message so that the recipient can confirm the sender of the message , And be sure that the email has not been tampered with . It can provide a safe way of communication , There is no need for any confidential channel to pass the key in advance .
边栏推荐
猜你喜欢
STM32 serial port register library function configuration method
![Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]](/img/5f/a3e7ed3617f1fec024eaba086ddd2a.jpg)
Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]
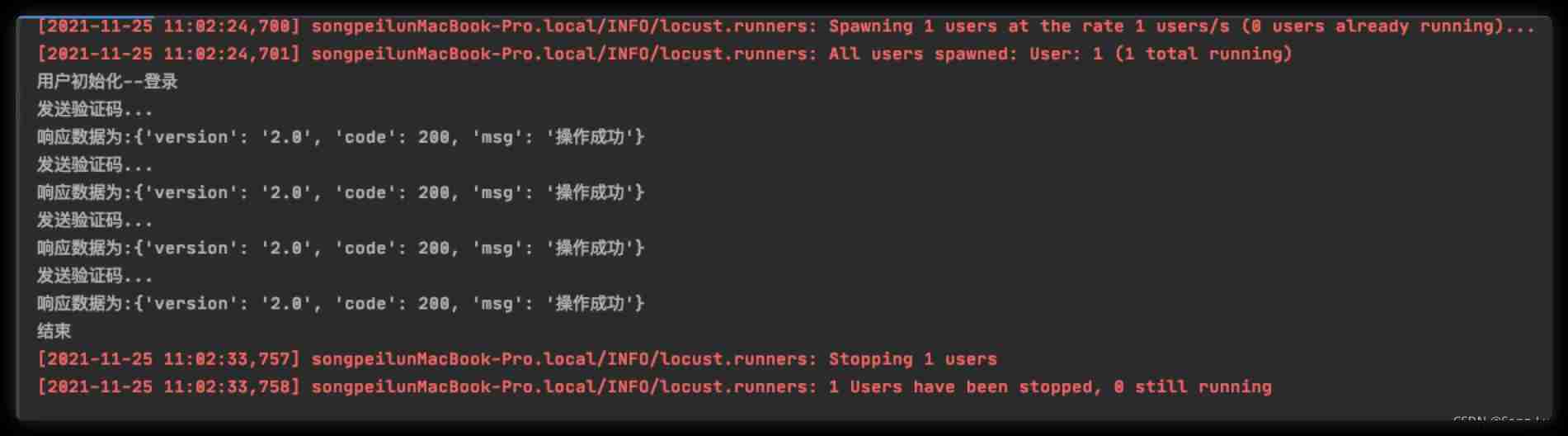
Locust performance test 2 (interface request)
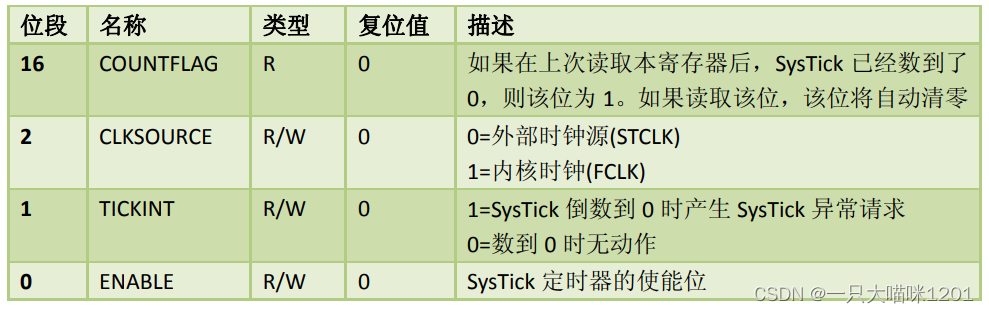
Systick滴答定时器

信息安全实验三 :PGP邮件加密软件的使用
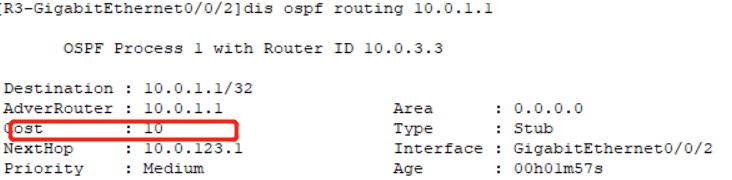
Huawei HCIP - datacom - Core 03 jours

PMP Exam Preparation experience systematically improve project management knowledge through learning
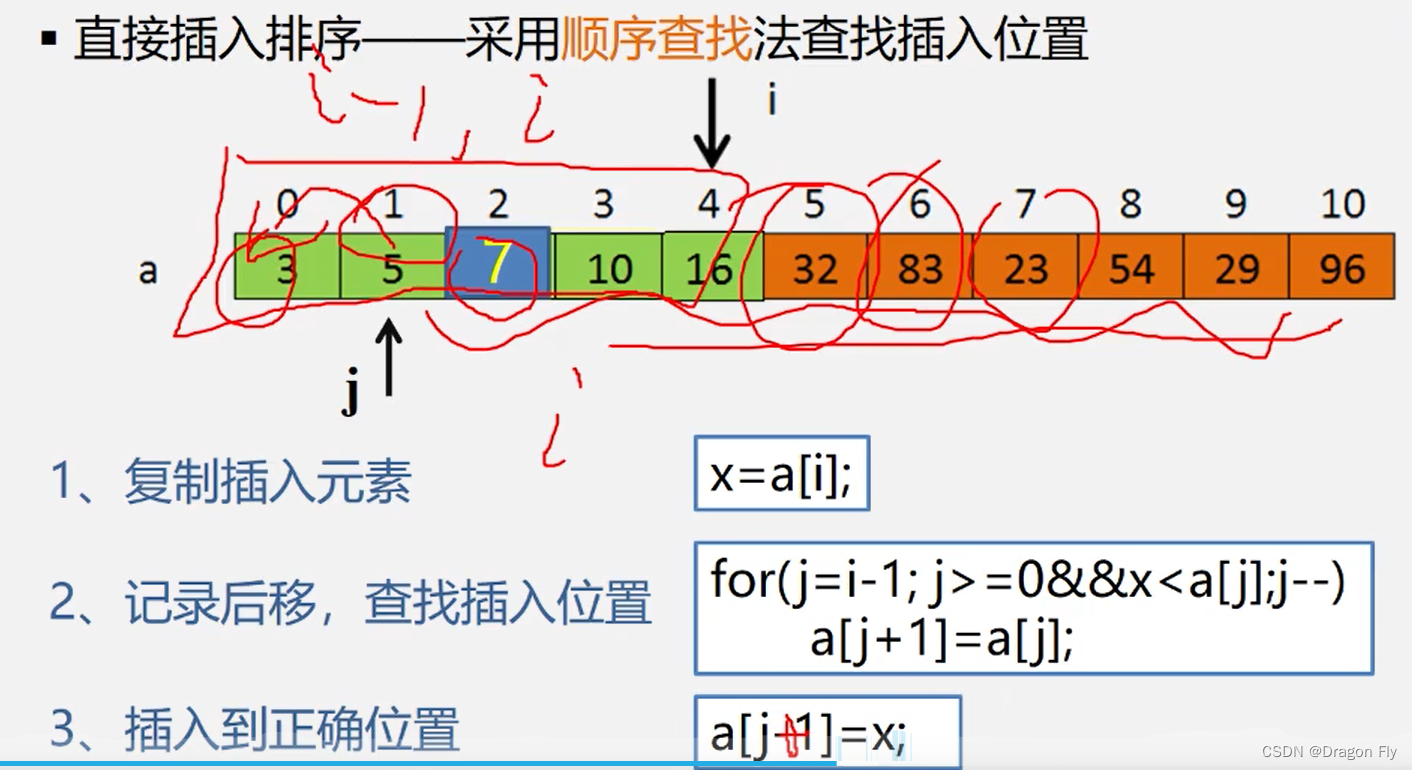
十二、排序
Storage of data in memory
【Istio Network CRD VirtualService、Envoyfilter】
随机推荐
Record of structured interview
When inputting an expression in the input box, an error is reported: incorrect string value:'\xf0\x9f... ' for column 'XXX' at row 1
[chaosblade: delete pod according to the tag, pod domain name access exception scenario, pod file system i/o failure scenario]
C language pointer (exercises)
Network request process
5A summary: seven stages of PMP learning
端口复用和重映像
Postman setting environment variables
JMeter JDBC batch references data as input parameters (the simplest method for the whole website)
华为HCIP-DATACOM-Core_03day
Port multiplexing and re imaging
Why is access to the external network prohibited for internal services of the company?
Unittest simple project
External interrupt to realize key experiment
C language pointer (special article)
網易雲微信小程序
Jenkins task grouping
Druid monitoring - Introduction to JMX usage and principle
Run can start normally, and debug doesn't start or report an error, which seems to be stuck
PMP experience learning and sharing process