当前位置:网站首页>Ice Scorpion V4.0 attack, security dog products can be fully detected
Ice Scorpion V4.0 attack, security dog products can be fully detected
2022-08-05 03:22:00 【Safe Dog News】
Disclaimer
Solemnly declare: The technology, ideas and tools involved in this account are only for learning and communication for the purpose of safety. No one may use them for illegal purposes, otherwise the consequences will be borne by themselves!
During the past two years of large-scale offensive and defensive drills, the "Ice Scorpion" caught many defensive units by surprise and miserable.But then, in response to the characteristics of Ice Scorpion, security manufacturers have also taken measures to update their own security products.When the horn of this year's actual offensive and defensive battles was officially launched, Ice Scorpion unexpectedly attacked with the "new look of 4.0", which once again made many defensive units unable to cope with it.
Faced with this threat, the Security Dog team has updated the rule base of "Webshell killing engine" on the afternoon of July 25, 2022.At the same time, SafeDog's products also have the function of "Injecting Memory Horse" for Ice Scorpion 4.0, and the "Memory Horse Killing Engine" supports detection by default.
This article will introduce the features and defense suggestions of Ice Scorpion V4.0, hoping to help defensive units during actual combat.
One
Ice Scorpion V4.0
1.The origin of the ice scorpion
The traditional webshell management tool "Chopper" has obvious attack traffic characteristics and is easy to be intercepted by detection equipment. Attackers urgently need a webshell with encrypted communication function.Due to traffic encryption, traditional WAF and IDS devices are difficult to detect.Therefore, a dynamic binary encrypted website management client "Ice Scorpion" came into being. The threats such as web page backdoor attacks and fileless attacks brought by Bing Scorpion have brought great trouble to traditional security products.
2Ice Scorpion V4.0
"Ice Scorpion" is one of the most popular WebShell management tools. The first-generation WebShell management tool "Chopper" has obvious traffic characteristics and can be easily detected.The traffic of Ice Scorpion is encrypted, which can effectively avoid the detection of traffic devices; the "Ice Scorpion" client is developed in Java, the latest version is v4.0, the management side is cross-platform, and supports ASP/ASPX/JSP/PHP and other environments.

Figure 1
In the latest V4.0, support Java Agent fileless land injection into memory horse.

Figure 2
It can be said that the revision of the Ice Scorpion made some of the measures and methods that the defenders made against the Ice Scorpion last year go to waste.
Second
Defense Suggestions for Ice Scorpion V4.0
1, Defendable points
(1) Focus on defending against file upload, file writing, and file inclusion vulnerabilities; (2) Built-in for Ice Scorpion V4.0Analyze the traffic side of all types of webshells, and detect each type of webshells in a targeted manner; (3) Enable monitoring of abnormal system behaviors to detect dangerous behaviors such as rebound shells and execution of high-risk system commands; (4) Do a good job of checking the security baseline, revise the security baseline in time, and record and warn of suspicious behaviors of suspicious files to facilitate auditing. |
2, Security Dog Cloud Eye can detect Ice Scorpion V4.0
The new-generation cloud host intrusion monitoring and security management platform "Cloud Eye" has functions such as "Webshell killing" and "Memory horse detection" that support the application of Ice Scorpion 4.0Attack detection. |
In addition, when an attacker uses the Ice Scorpion tool to connect to a virtual terminal and execute commands, functions such as "process monitoring" can also be detected.
Host Webshell killing

Figure 3
Host memory check

Figure 4
3Security Dog Cloud Armor can detect Ice Scorpion V4.0
The adaptive container security management system "Yunjia" supports functions such as "Image Webshell Scanning", "Container Webshell Scanning", and "Container Memory Horse Detection"Detect the attack of Ice Scorpion 4.0. |
In addition, when an attacker uses the Ice Scorpion tool to connect to a virtual terminal and execute commands, functions such as "process monitoring" and "behavior model" can also be detected.
Mirror Webshell killing

Figure 5
Container Webshell Killing

Figure 6
Container memory detection

Figure 7
References
https://github.com/rebeyond/Behinder
边栏推荐
- Use SuperMap iDesktopX data migration tool to migrate ArcGIS data
- 腾讯云【Hiflow】新时代自动化工具
- Question about #sql shell#, how to solve it?
- Open Source License Description LGPL
- Object.defineProperty monitors data changes in real time and updates the page
- sql server 安装提示用户名不存在
- Simple description of linked list and simple implementation of code
- 引领数字医学高地,中山医院探索打造未来医院“新范式”
- QT MV\MVC structure
- 龙蜥社区第二届理事大会圆满召开!理事换届选举、4 位特约顾问加入
猜你喜欢
word分栏小记
QT language file production
Bubble Sort and Quick Sort
MRTK3 develops Hololens application - gesture drag, rotate, zoom object implementation
【已解决】Unity Coroutinue 协程未有效执行的问题
After the large pixel panorama is completed, what are the promotion methods?
Dynamic management of massive service instances

How to Add Category-Specific Widgets in WordPress
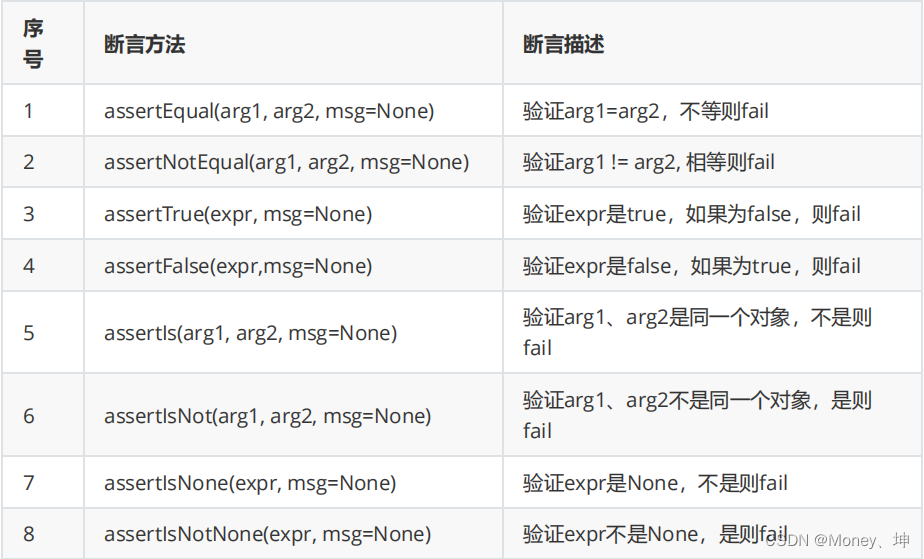
【软件测试】自动化测试之unittest框架

How Jin Cang database correctness verification platform installation file
随机推荐
[Storage] Dawning Storage DS800-G35 ISCSI maps each LUN to the server
如何在WordPress中添加特定类别的小工具
语法基础(变量、输入输出、表达式与顺序语句)
From "useable" to "easy to use", domestic software is self-controllable and continues to advance
沃谈小知识 |“远程透传”那点事儿
毕设-基于SSM房屋租赁管理系统
The usage of try...catch and finally in js
PostgreSQL数据库 用navicat 打开表结构的时候报错 cannot update secondarysnapshot during a parallel operation 怎么解决?
Use SuperMap iDesktopX data migration tool to migrate map documents and symbols
Native js realizes the effect of selecting and canceling all the multi-select boxes
MRTK3 develops Hololens application - gesture drag, rotate, zoom object implementation
使用二维码传输文件的小工具 - QFileTrans 1.2.0.1
【软件测试】自动化测试之unittest框架
[论文笔记] MapReduce: Simplified Data Processing on Large Clusters
2022高处安装、维护、拆除考试题模拟考试题库及在线模拟考试
High Item 02 Information System Project Management Fundamentals
Why is the pca component not associated
One hundred - day plan -- -- DAY2 brush
Step by step how to perform data risk assessment
达梦8数据库导出导入