当前位置:网站首页>How to deal with data leakage and deletion related to business life and death?
How to deal with data leakage and deletion related to business life and death?
2020-11-07 20:15:00 【InfoQ】
One 、 introduction
1. What is database auditing ?
For a warehouse , If you want to guard against theft , The common practice is to install monitoring at the entrance and exit , Once there's a problem , Call the monitor to find the abnormal situation . It's similar to databases , There's also access to the database , Monitor all connections and entrances , You can record all the movements , Once there's a problem , By querying historical actions and analyzing them , You can find key information .
Therefore, database audit can be understood as recording the user's behavior of accessing the database , Positioning illegal actions , Go back to the source afterwards , The function of improving database security .
2. Common auditing methods
Common audit methods include the following categories :
(1) Application level audit
Audit directly in the application system , Before the statement is sent to the database background, the audit is done first , Does not affect database performance , I don't care what database is used at the bottom , But the pressure on the application system is relatively large , And the application system needs to parse statements , There's a certain amount of complexity .
(2) Transport layer audit
Often capture packet parsing implementation , It has no effect on the upper and lower levels , But also parse the statement , There's a certain amount of complexity , And if the transport layer is communicating through encryption , Will not be able to parse .
(3) Kernel audit
Directly on the kernel , All functions can be realized , It also minimizes performance impact , But it will have an impact on backstage stability , High requirements for developers , Whether it's open source or not , Will be very careful to support auditing directly on the kernel .
(4) Plug in audit
For open source databases , There are usually plug-ins to add functionality . Auditing can be embedded directly in the kernel as plug-ins , Of course, it will have a certain impact on database performance , But also because it's directly embedded in the kernel , A lot of first-hand information can be obtained directly , For example, if there is no way to avoid the above syntax parsing, there is no need to do , And it can also get more information about the running state directly , Can develop powerful and flexible audit functions .
Link to the original text :【https://www.infoq.cn/article/a4DNNeVBNuGqLJMR0HhK】. Without the permission of the author , Prohibited reproduced .
版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
边栏推荐
- 把 4个消息队列都拉到一个群里后,他们吵起来了
- From technology to management, the technology of system optimization is applied to enterprise management
- How to learn technology efficiently
- 「混合云」会是云计算的下一个战场吗?
- [note] error while loading pyv8 binary: exit code 1 solution
- 统计文本中字母的频次(不区分大小写)
- gitlab 持续集成开发环境之CI/CD
- 从技术谈到管理,把系统优化的技术用到企业管理
- 一次公交卡被“盜刷”事件帶來的思考
- 课堂练习
猜你喜欢

工作1-3年的程序员,应该具备怎么样的技术能力?该如何提升?

使用“1”个参数调用“DownloadString”时发生异常:“操作超时”

Web API系列(三)统一异常处理

盘点那些争议最大的编程观点,你是什么看法呢?

Using rabbitmq to implement distributed transaction
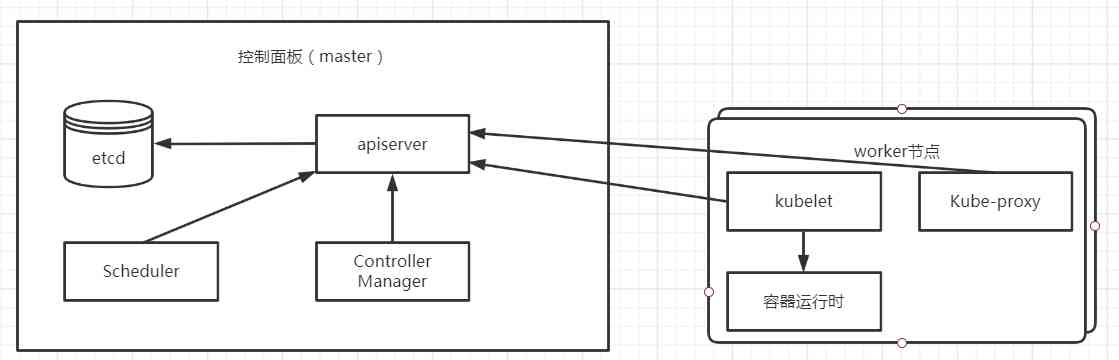
Kubernetes (1): introduction to kubernetes

The JS solution cannot be executed after Ajax loads HTML

Advanced concurrent programming series 9 (lock interface analysis)

HMS core push service helps e-commerce app to carry out refined operation
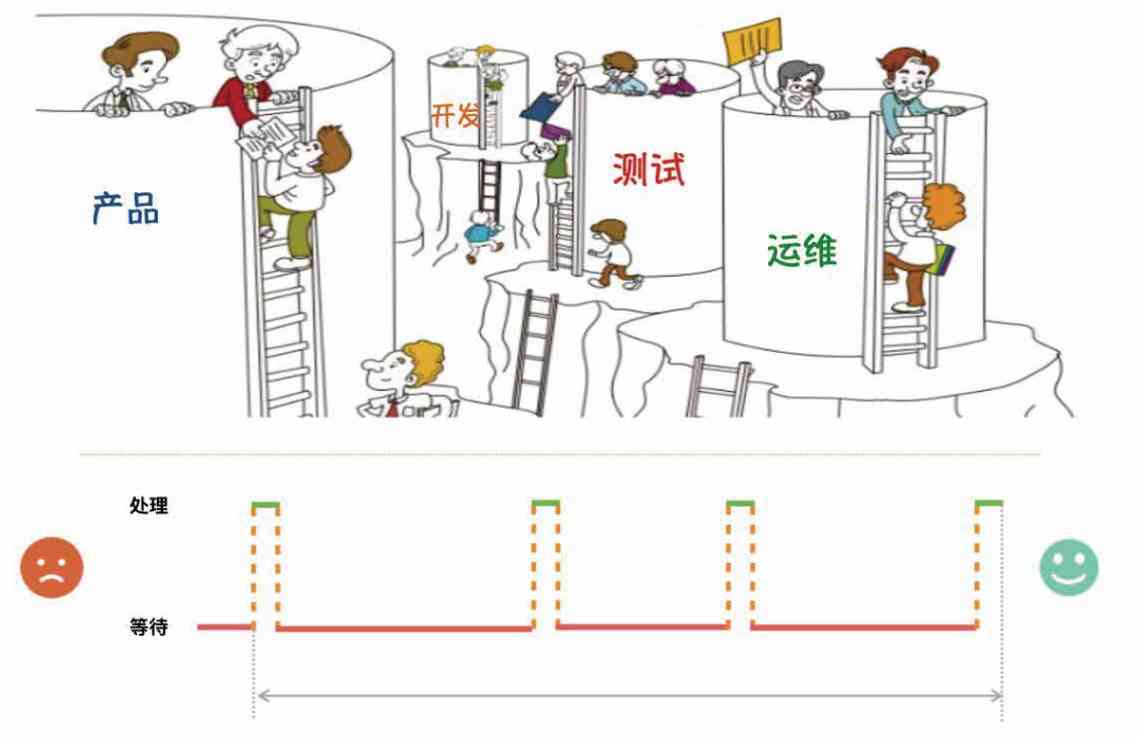
From technology to management, the technology of system optimization is applied to enterprise management
随机推荐
如何应对事关业务生死的数据泄露和删改?
Exception calling 'downloadstring' with '1' arguments: 'operation timed out'
利用线程通信、解决缓存穿透数据库雪崩
「混合云」会是云计算的下一个战场吗?
30岁后,你还剩下什么?
Git submission specification
websocket+probuf.原理篇
傲視Kubernetes(一):Kubernetes簡介
【涂鸦物联网足迹】物联网主流通信方式
Business facade and business rule
HandlerMethodArgumentResolver使用和原理
C語言重點——指標篇(一文讓你完全搞懂指標)| 從記憶體理解指標 | 指標完全解析
[original] the impact of arm platform memory and cache on the real-time performance of xenomai
Kubernetes服务类型浅析:从概念到实践
Chinese sub forum of | 2020 PostgreSQL Asia Conference: Pan Juan
Analysis of the original code of [QT] qthread
Andque.
Advanced concurrent programming series 9 (lock interface analysis)
【C++学习笔记】C++ 标准库 std::thread 的简单使用,一文搞定还不简单?
Git代码提交操作,以及git push提示failed to push some refs'XXX'