当前位置:网站首页>Section 26 detailed explanation and demonstration of IPSec virtual private network configuration experiment - simulation experiment based on packettracer8.0
Section 26 detailed explanation and demonstration of IPSec virtual private network configuration experiment - simulation experiment based on packettracer8.0
2022-07-03 03:14:00 【dare to try @】
Catalog
- 1 Network topology and experimental requirements
- 2 Configuration process and commands — be based on PacketTracer8.0 simulation experiment
- 2.1 To configure IP And routing table
- 2.2 experiment 1: Beijing -- Established between Shanghai VPN Tunnel , And verify ;
- 2.3 experiment 2: The two companies can access the Internet , But it doesn't affect VPN Tunnel
- 2.4 experiment 3: The headquarters in Beijing and the newly established branch in Guangzhou have also been established vpn Tunnel
- 2.5 experiment 4
- 2.6 Error query and processing commands when troubleshooting
- Reference article
1 Network topology and experimental requirements
1.1 Experimental Topology
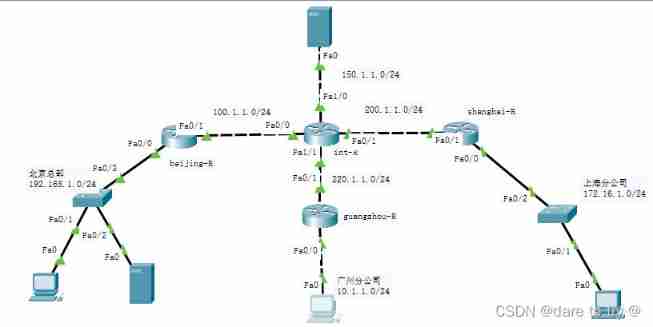
1.2 The experimental requirements
(1) The intermediate router acts as the Internet , Private IP.
(2) experiment 1: Beijing – Established between Shanghai VPN Tunnel , And verify ;
(3) experiment 2: In the experiment 1 On the basis of , The two companies are required to have access to the Internet , But it doesn't affect VPN Tunnel ;
(4) experiment 3: In the experiment 1 And experiments 2 On the basis of , The headquarters in Beijing and the newly established branch in Guangzhou have also been established vpn Tunnel ;
(5) experiment 4: In the experiment 1~3 On the basis of , Guangzhou and Shanghai are required not to establish vpn Tunnel , But Guangzhou and Shanghai can communicate with each other safely .( Guangzhou uses a tunnel from its headquarters in Beijing , Then from Beijing to Shanghai ).
2 Configuration process and commands — be based on PacketTracer8.0 simulation experiment
2.1 To configure IP And routing table
(1) Configure each host and server manually IP Address .
(2) Use the command to configure the interface of each router IP Address ..
(3) Configure routing table .
# by beijing-R To configure IP And routing table
en
conf t
ho beijing-R
int f0/0
ip add 192.168.1.254 255.255.255.0
no shut
exit
int f0/1
ip add 100.1.1.1 255.255.255.0
no shut
exit
ip route 0.0.0.0 0.0.0.0 100.1.1.2
do show ip int b
do wr
# by guangzhou-R To configure IP And routing table
en
conf t
ho guangzhou-R
int f0/0
ip add 10.1.1.254 255.255.255.0
no shut
exit
int f0/1
ip add 220.1.1.1 255.255.255.0
no shut
exit
ip route 0.0.0.0 0.0.0.0 220.1.1.2
do show ip int b
do wr
# by shanghai-R To configure IP And routing table
en
conf t
ho shanghai-R
int f0/0
ip add 172.16.1.254 255.255.255.0
no shut
exit
int f0/1
ip add 200.1.1.2 255.255.255.0
no shut
exit
ip route 0.0.0.0 0.0.0.0 200.1.1.1
do show ip int b
do wr
# by int-R To configure IP And routing table
en
conf t
ho int-R
int f0/0
ip add 100.1.1.2 255.255.255.0
no shut
exit
int f0/1
ip add 200.1.1.1 255.255.255.0
no shut
exit
int f1/0
ip add 150.1.1.254 255.255.255.0
no shut
exit
int f1/1
ip add 220.1.1.2 255.255.255.0
no shut
exit
do show ip int b
do wr
2.2 experiment 1: Beijing – Established between Shanghai VPN Tunnel , And verify ;
2.2.1 Specific configuration and commands
''' stay beijing-R Internet interface configuration of router IPsecVPN'''
''' First step : Manage connections , Create and write policy sets '''
''' The second step : Data connection , Create and write transmission mode '''
''' The third step : Create and write map The mapping table , And apply to the port '''
conf t
crypto isakmp policy 1
encryption aes
group 2
hash sha
authentication pre-share
exit
crypto isakmp key zziqqvm-1 address 200.1.1.2
acc 100 permit ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255
crypto ipsec transform-set zztran esp-aes esp-sha-hmac
crypto map zzmap 1 ipsec-isakmp
set peer 200.1.1.2
match address 100
set transform-set zztran
exit
int f0/1
crypto map zzmap
exit
do wr
''' stay shanghai-R Internet interface configuration of router IPsecVPN'''
''' First step : Manage connections , Create and write policy sets '''
''' The second step : Data connection , Create and write transmission mode '''
''' The third step : Create and write map The mapping table , And apply to the port '''
conf t
crypto isakmp policy 1
encryption aes
group 2
hash sha
authentication pre-share
exit
crypto isakmp key zziqqvm-1 address 100.1.1.1
acc 100 permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255
crypto ipsec transform-set zztran esp-aes esp-sha-hmac
crypto map zzmap 1 ipsec-isakmp
set peer 100.1.1.1
match address 100
set transform-set zztran
exit
int f0/1
crypto map zzmap
exit
do wr
2.2.2 verification
Beijing headquarters PC Go to ping Shanghai Branch PC, See if ping through , success ping through .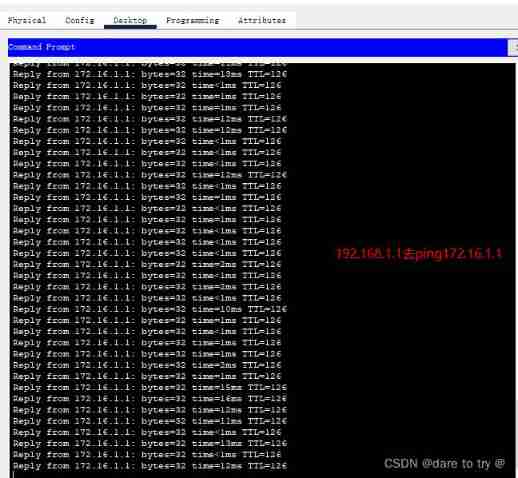


2.3 experiment 2: The two companies can access the Internet , But it doesn't affect VPN Tunnel
2.3.1 Specific configuration and commands
''' stay beijing-R Internet interface configuration of router PAT And static port mapping '''
conf t
int f0/0
ip nat inside
exit
int f0/1
ip nat outside
exit
acc 150 deny ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255
acc 150 permit ip 192.168.1.0 0.0.0.255 any
ip nat inside source list 150 int f0/1 overload
ip nat inside source static tcp 192.168.1.2 80 100.1.1.3 80
''' stay shanghai-R Internet interface configuration of router PAT'''
conf t
int f0/0
ip nat inside
exit
int f0/1
ip nat outside
exit
acc 150 deny ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255
acc 150 permit ip 172.16.1.0 0.0.0.255 any
ip nat inside source list 150 int f0/1 overload
2.3.2 verification
(1) Use the... Of Beijing headquarters and Shanghai branch respectively PC Go to ping Servers on the Internet . success ping through , Explain that you can surf the Internet .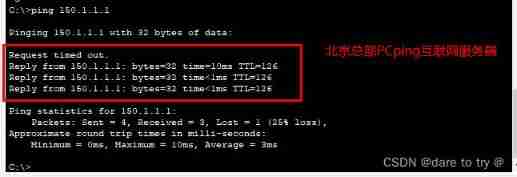
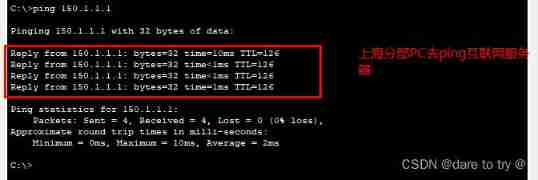
(2) Beijing headquarters PC Go to... Again ping Shanghai Branch PC, success ping through .
2.3.3 Precautions for this experiment
In the experiment 2 in , Both Beijing headquarters and Shanghai branch are equipped with NAT And IPsecVPN, Note that the router matches first NAT, Match again IPsecVPN. Then when the conditions match, the router will send the source IP Address translation to public network IP, Then send it to match VPN, here VPN It may not match . So configuration NAT when ,NAT Of ACL The table must be done first VPN Two of them IP Address exemption .
2.4 experiment 3: The headquarters in Beijing and the newly established branch in Guangzhou have also been established vpn Tunnel
- 1) Every time you configure ACL Table time , It needs to be done first show ip access Check the configured table number , View the required information or avoid table number conflicts , Be careful ACL The order of entries in the table .
2.4.1 Specific configuration and commands
''' stay beijing-R Configuration on router '''
''' First step : stay beijing-R Internet interface configuration of router IPsecVPN'''
''' The second step : Set up NAT Immunity '''
''' First step : stay beijing-R Internet interface configuration of router IPsecVPN'''
# Stage 1 : Manage connections , Create and write policy sets
# Stage two : Data connection , Create and write transmission mode
# 3、 ... and : Create and write map The mapping table , And apply to the port
# The transmission set and transmission mode are the same as those of Shanghai Branch , Because this experiment is in experiment 1 On the basis of , Therefore, you can no longer configure
conf t
crypto isakmp key zziqqvm address 220.1.1.1
acc 110 permit ip 192.168.1.0 0.0.0.255 10.1.1.0 0.0.0.255
crypto map zzmap 2 ipsec-isakmp
set peer 220.1.1.1
match address 110
set transform-set zztran
exit
do wr
''' The second step : Set up NAT Immunity '''
# Beijing headquarters PAT Matching table needs to be done VPN Beijing and Guangzhou companies IP Address or network segment exclusion , And we must pay attention to ACL Entry order of
conf t
do show ip acc
ip acc ex 150
no 20
deny ip 192.168.1.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 any
exit
do show ip acc
do wr
''' stay guangzhou-R Configuration on router '''
''' The first step is guangzhou-R Internet interface configuration of router IPsecVPN'''
''' The second step : To configure PAT And settings NAT Immunity '''
''' The first step is guangzhou-R Internet interface configuration of router IPsecVPN'''
# Stage 1 : Manage connections , Create and write policy sets
# Stage two : Data connection , Create and write transmission mode
# 3、 ... and : Create and write map The mapping table , And apply to the port
conf t
crypto isakmp policy 1
encryption aes
group 2
hash sha
authentication pre-share
exit
crypto isakmp key zziqqvm address 100.1.1.1
acc 110 permit ip 10.1.1.0 0.0.0.255 192.168.1.0 0.0.0.255
crypto ipsec transform-set zztran esp-aes esp-sha-hmac
crypto map zzmap 2 ipsec-isakmp
set peer 100.1.1.1
match address 110
set transform-set zztran
exit
int f0/1
crypto map zzmap
exit
do wr
''' The second step : To configure PAT And settings NAT Immunity '''
# In order that Guangzhou branch can access the Internet , stay guangzhou-R Internet interface configuration of router PAT, Pay attention to setting at the same time NAT Immunity
conf t
int f0/0
ip nat inside
exit
int f0/1
ip nat outside
exit
acc 150 deny ip 10.1.1.0 0.0.0.255 192.168.1.0 0.0.0.255
acc 150 permit ip 10.1.1.0 0.0.0.255 any
ip nat inside source list 150 int f0/1 overload
2.4.2 verification
Beijing headquarters PC Go to ping Guangzhou Branch PC, success ping through .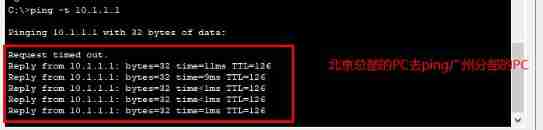
2.4.3 Precautions for this experiment
Be sure to remember to revise the Beijing headquarters PAT In configuration ACL Match table , Will need to do VPN Beijing and Guangzhou companies IP Address or network segment exclusion , And we must pay attention to ACL Entry order of .
2.5 experiment 4
- 1) According to the requirements of the experiment , There is no new branch from Guangzhou to Shanghai VPN, Then we can only use the VPN, Reuse from Beijing to Shanghai VPN). Due to the VPN And from Beijing to Shanghai VPN Already there. , And yes, you can go VPN The flow is limited , Then you only need to add other flows to the restrictions .
- 2) During the experiment , Be sure to use it many times “show ip acc” see ACL surface , Clarify the function of each table and the whole transmission process of data frames , What needs to be added to these tables , And be sure to pay attention to the order .
2.5.1 Specific configuration and commands
''' stay guangzhou-R Configuration on router '''
''' First step : First of all, we need to transfer Guangzhou to Shanghai IP Address settings NAT Immunity , Be sure to pay attention to ACL The order of the tables '''
''' The second step : Add at the external network interface IPsecVPN Configuration of '''
# Set up NAT Immunity
conf t
do show ip acc
ip acc ex 150
no 20
deny ip 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255
permit ip 10.1.1.0 0.0.0.255 any
exit
do show ip acc
# To configure IPsecVPN
acc 110 permit ip 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255
do show ip acc
do wr
''' stay beijing-R Configuration on router '''
''' First step : Set up NAT Immunity '''
''' The second step : Add at the external network interface IPsecVPN Configuration of '''
# The router in Beijing is only for 192.168.1.0 Of IP Conduct NAT transformation , Therefore, the first step here does not need to be set
# Add at the external network interface IPsecVPN Configuration of
conf t
do show ip acc
acc 100 permit ip 10.1.1.0 0.0.0.255 172.16.1.0 0.0.0.255
acc 110 permit ip 172.16.1.0 0.0.0.255 10.1.1.0 0.0.0.255
do show ip acc
do wr
''' stay shanghai-R Configuration on router '''
''' First step : First of all, we need to transfer Guangzhou to Shanghai IP Address settings NAT Immunity , Be sure to pay attention to ACL The order of the tables '''
''' The second step : Add at the external network interface IPsecVPN Configuration of '''
# Set up NAT Immunity
conf t
do show ip acc
ip acc ex 150
no 20
deny ip 172.16.1.0 0.0.0.255 10.1.1.0 0.0.0.255
permit ip 172.16.1.0 0.0.0.255 any
exit
do show ip acc
# To configure IPsecVPN
acc 100 permit ip 172.16.1.0 0.0.0.255 10.1.1.0 0.0.0.255
do show ip acc
do wr
2.5.2 verification
Guangzhou Branch PC Go to ping Shanghai Branch PC, success ping through . During the experiment , From the beginning, I always ping no , After checking many times, no problem is found , After saving the router and restarting it many times, it succeeds , Maybe the software platform has bug.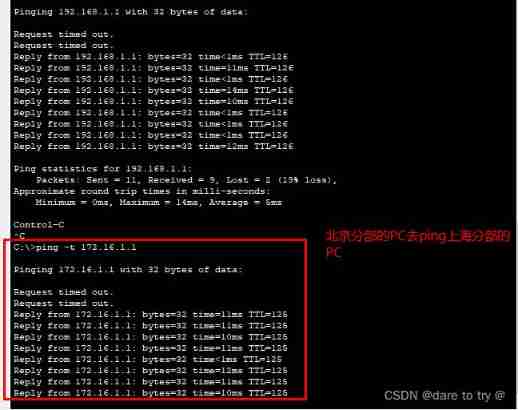
2.6 Error query and processing commands when troubleshooting
show crypto isakmp policy # View the content of the configured security policy set
show crypto isakmp sa # Check the status of phase one
show crypto ipsec sa # View the application status of phase II
show crypto ipsec transform-set # Check the status of phase II transmission mode
show ip acc
# It could be a platform bug, Try saving and restarting multiple times .
write
reload
Reference article
[1] 《IPsecVPN Configuration experiment —— be based on PacketTracer8.0 simulation experiment 》
边栏推荐
- TCP handshake three times and wave four times. Why does TCP need handshake three times and wave four times? TCP connection establishes a failure processing mechanism
- C language beginner level - pointer explanation - paoding jieniu chapter
- 内存泄漏工具VLD安装及使用
- 900W+ 数据,从 17s 到 300ms,如何操作
- MySql实战45讲【SQL查询和更新执行流程】
- Creation and destruction of function stack frame
- 从C到Capable-----利用指针作为函数参数求字符串是否为回文字符
- 【PyG】理解MessagePassing过程,GCN demo详解
- PAT乙级“1104 天长地久”DFS优化思路
- Three.js本地环境搭建
猜你喜欢
I2C 子系统(二):I3C spec

I2C subsystem (I): I2C spec
![MySQL Real combat 45 [SQL query and Update Execution Process]](/img/cd/3a635f0c3bb4ac3c8241cb77285cc8.png)
MySQL Real combat 45 [SQL query and Update Execution Process]

C language beginner level - pointer explanation - paoding jieniu chapter

C语言初阶-指针详解-庖丁解牛篇

一文带你了解 ZigBee

Yiwen takes you to know ZigBee
![[Chongqing Guangdong education] cultural and natural heritage reference materials of China University of Geosciences (Wuhan)](/img/19/815e7cba81f6eb52db5ef0db556dfd.jpg)
[Chongqing Guangdong education] cultural and natural heritage reference materials of China University of Geosciences (Wuhan)
从C到Capable-----利用指针作为函数参数求字符串是否为回文字符

Creation and destruction of function stack frame
随机推荐
Réglez la hauteur et lancez le système. Currenttimemillis catton
The difference between componentscan and componentscans
Use of check boxes: select all, deselect all, and select some
用docker 連接mysql的過程
VS 2019配置tensorRT
Destroy the session and empty the specified attributes
New programmers use the isXXX form to define Boolean types in the morning, and are discouraged in the afternoon?
Idea set method call ignore case
从输入URL到页面展示这中间发生了什么?
程序员新人上午使用 isXxx 形式定义布尔类型,下午就被劝退?
About HTTP cache control
MySQL practice 45 lecture [row lock]
I2C 子系統(四):I2C debug
vfork执行时出现Segmentation fault
基于Qt的yolov5工程
el-tree搜索方法使用
PHP constructor with parameters - PHP constructor with a parameter
后管中编辑与预览获取表单的值写法
Yiwen takes you to know ZigBee
左连接,内连接