当前位置:网站首页>On the adjacency matrix and adjacency table of graph storage
On the adjacency matrix and adjacency table of graph storage
2022-07-03 03:10:00 【Liyueyue classmate】
Adjacency matrix a matrix that represents the relationship between vertices , The storage method is : A two-dimensional array stores the adjacency relationship between vertices in the graph .
In an undirected graph , If there is a connection between two nodes , So we initialize map[i][j]=map[j][i]=1, If not connected, set it to 0.
Give me a picture :

According to the above initialization method, the representation of its adjacency matrix :

If it's a weighted graph , Then give him a weight , Generally, nodes that are not connected are assigned INF(0x3f3f3f3f)
Storage advantages of adjacency matrix : Quickly determine whether there is a connection between the two nodes , Quickly calculate the degree between nodes . Adjacency matrix is the simplest and most common storage method in my opinion
-------------------------------------------------------------- Next, let's look at the adjacency table ----------------------------------------
Adjacency list is a chain storage method of graph , It contains two parts, vertex and adjacency . The vertices Contains vertex information and a pointer to the first adjacent node . Adjacency point Contains its own subscript and pointer to the next adjacent node .
Their structure is as follows :


Ideas : We regard each node as the head node , The nodes it points to build a single linked list in reverse order .

Code :
struct node
{
int v;// Adjacency subscript
node* next;// Point to the next adjacent point
}
node* head[maxn];
void adde(int u, int v)// Insert an edge , Refer to the reverse linked list creation process
{
node* s = new node;
s->v = v;
s->next = head[u];
head[u] = s;
}
void creat()
{
char x, y;
int i, u, v;
cin >> n >> m;
for (i = 0; i < m; i++)
{
cin >> x >> y;
u = x - 'a';
v = y - 'a';// Convert character numbers to numeric numbers
adde(u, v);
}
}
边栏推荐
- [C语言]给账号密码进行MD5加密
- labelme标记的文件转换为yolov5格式
- About HTTP cache control
- Use of check boxes: select all, deselect all, and select some
- MySQL practice 45 [global lock and table lock]
- I2C 子系统(一):I2C spec
- 基于QT的tensorRT加速的yolov5
- tensorflow转pytorch笔记;tf.gather_nd(x,y)转pytorch
- Installation and use of memory leak tool VLD
- Reset or clear NET MemoryStream - Reset or Clear . NET MemoryStream
猜你喜欢
Add automatic model generation function to hade
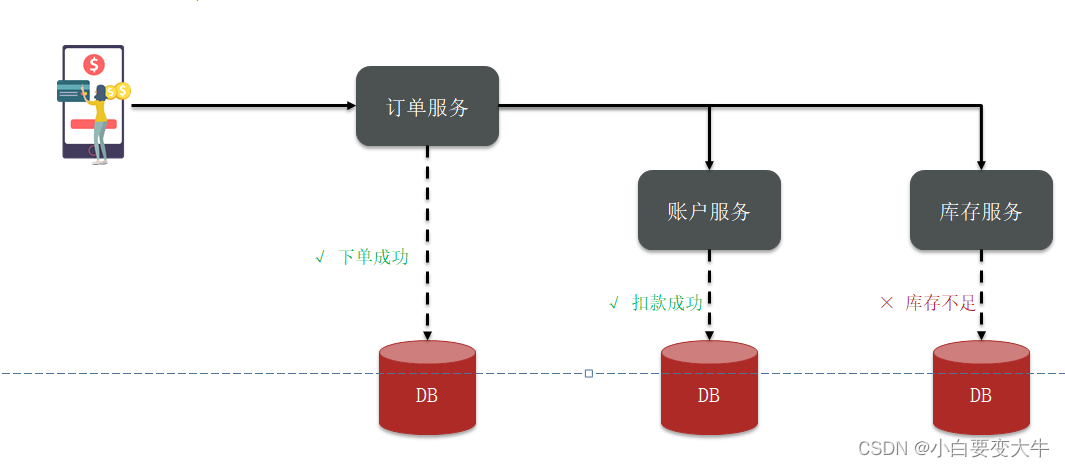
Distributed transaction
Kubernetes family container housekeeper pod online Q & A?
I2C subsystem (II): I3C spec
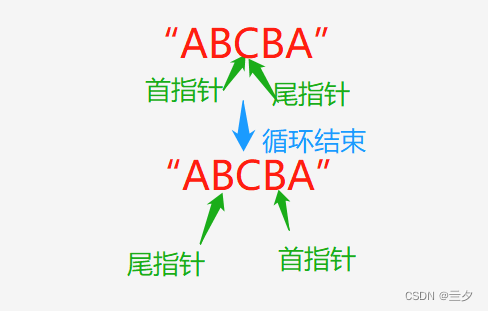
From C to capable -- use the pointer as a function parameter to find out whether the string is a palindrome character
![MySQL practice 45 [global lock and table lock]](/img/23/fd58c185ae49ed6c04f1a696f10ff4.png)
MySQL practice 45 [global lock and table lock]

Pytorch配置
![[Chongqing Guangdong education] cultural and natural heritage reference materials of China University of Geosciences (Wuhan)](/img/19/815e7cba81f6eb52db5ef0db556dfd.jpg)
[Chongqing Guangdong education] cultural and natural heritage reference materials of China University of Geosciences (Wuhan)
![MySQL Real combat 45 [SQL query and Update Execution Process]](/img/cd/3a635f0c3bb4ac3c8241cb77285cc8.png)
MySQL Real combat 45 [SQL query and Update Execution Process]
![45 lectures on MySQL [index]](/img/f6/70be00028908cbd9ed7f2c77687cee.png)
45 lectures on MySQL [index]
随机推荐
tensorflow转pytorch笔记;tf.gather_nd(x,y)转pytorch
QT based tensorrt accelerated yolov5
MySql实战45讲【事务隔离】
The idea cannot be loaded, and the market solution can be applied (pro test)
处理数据集,使用LabelEncoder将所有id转换为从0开始
Can I use read-only to automatically implement properties- Is read-only auto-implemented property possible?
idea 加载不了应用市场解决办法(亲测)
Concrete CMS vulnerability
How to return ordered keys after counter counts the quantity
分布式事务
Use cve-2021-43893 to delete files on the domain controller
MySql實戰45講【SQL查詢和更新執行流程】
Creation and destruction of function stack frame
Force freeing memory in PHP
VS 2019安装及配置opencv
用docker 连接mysql的过程
Cron表达式介绍
迅雷chrome扩展插件造成服务器返回的数据js解析页面数据异常
labelimg生成的xml文件转换为voc格式
vfork执行时出现Segmentation fault