当前位置:网站首页>Concrete CMS vulnerability
Concrete CMS vulnerability
2022-07-03 02:41:00 【Khan security team】
Introduce
We have written about concrete here before CMS The article . In that article , We described how we managed to exploit the double race condition vulnerability in the file upload function to obtain remote command execution . In this post , We will show what we found when we conducted a penetration test on one of our customers at the end of last year Concrete CMS Multiple vulnerabilities in . All these vulnerabilities have been fixed , We want to thank their team for their cooperation on these issues . For more information , see also “ Mitigation measures ” part , Learn about security tips for solving password poisoning and about improving this CMS Other tips for security .
Elevated privileges
Let's start with the problem of privilege escalation found at the beginning of the test . User groups have a hierarchy , They inherit permissions from each other . We have a user with limited permissions “Editor”, So we ask ourselves , If we try to make “Editors” Group moved to “Administrators” What will happen next , Will we inherit their authority ?
For the first time, try to move the editor under the administrators group
The attempt failed
blamed , It seems that our attempt failed , Developers actually thought of this , He is checking our permissions at the back end . But that's not all , We found another endpoint , We can try the same operation , So let's try again , Check whether the permissions of all endpoints are consistent
For the second time, try to move the editor under the administrators group
The editing group is now under the administrator , Inherit their authority
ok , Look at this. , They seem to have forgotten to implement permission checks on this endpoint , We have managed to use users with very limited permissions (“ edit ” role ) take “ edit ” Group moved to “ Administrators ” Next . We must log out and log in again to refresh our sessions and permissions . look , We can now access the entire control panel “ Administrators ”
PrivEsc succeed , We are now administrators
SSRF
As the first 1 Described in part , The control panel contains design features SSRF. We showed how to get RCE, But the first thing we actually use is this SSRF. Obviously , This SSRF Used before , Now they have taken some mitigation measures . The purpose of this function is to allow editors to download files from remote servers and save them locally .
SSRF Design
We used Burp Suite Of Collaborator Payload , We immediately received a callback :
Received callback
AWS Instance metadata is blocked , Oh no ! As mentioned earlier , We are well aware that this has been used , And some repairs have been made . Can we bypass these fixes ?
Instance metadata is not allowed
Some file extensions are blocked (.php And others ), You cannot use redirection . What else can we do ?
Redirection is not allowed / Blacklists are also used to expand
We found that we can use a well-known php Tips to bypass the extended blacklist ( /info.php/test.html Still request info.php but CMS Now I think .html Is a request extension that is whitelisted , The server will actually execute a .php Extension ) Then transfer to the local network hub , Access the internal network server . from Internet to turn to Intranet:
stay LAN Internal rotation
You can use it to enumerate and identify internal Web Applications . ad locum , We are reading the typical phpinfo The output of the file .
Internal access Web The server
stay LAN Medium rotation is good , You can combine it with various disposable GET Vulnerabilities are linked , But this is not enough for us . The whole goal in the cloud environment is to access the instance metadata server and steal IAM voucher . We have successfully used our good old friends DNS Rebind to achieve this . thank emil_lerner Provide this very useful service . We tried some of them , But this effect is the best , Our setting is 0! As a reminder , You may have to send 2-3 Only requests can succeed , Because in essence, you are trying to win the competitive conditions here ( Check time 、 Use your time ), because Concrete CMS The team has been in place before many verifications .
Use DNS Rebind to get AWS IAM role
We obtained the AWS IAM role :
AWS IAM role
From instance metadata AWS IAM secret key
The moral of the story is , There are always more skills to try , You just need enough persistence .
Password reset poisoning
We have written about Drupal and Joomla This type of attack . We also want to try here , It seems that we are right . Poison the host header below :
Malicious request to reset password
Will cause password reset link poisoning .
Poisoning password reset link
This is the email that will be sent to the user :
Email with poison link
Mitigation measures
SSRF and PrivEsc The loophole was at the end of last year 8.5.7 and 9.0.1 Fixed in version . You should upgrade to the latest version . For password poisoning , Please be there. Concrete CMS Set specifications in the management panel url. For specific CMS More tips on security , Please refer to the following pages for configuration best practices :https ://documentation.concretecms.org/developers/introduction/configuration-best-practices . Once again, we would like to thank their team for their support and cooperation in quickly solving these problems .
边栏推荐
- Gbase 8C system table PG_ class
- Mathematical statistics -- Sampling and sampling distribution
- C语言中左值和右值的区别
- The left value and the right finger explain better
- "Analysis of 43 cases of MATLAB neural network": Chapter 43 efficient programming skills of neural network -- Discussion Based on the characteristics of the new version of MATLAB r2012b
- GBase 8c系统表-pg_am
- How to change the panet layer in yolov5 to bifpn
- Check log4j problems using stain analysis
- Memory pool (understand the process of new developing space from the perspective of kernel)
- Two dimensional format array format index subscript continuity problem leads to return JSON format problem
猜你喜欢

Add automatic model generation function to hade

Practice of traffic recording and playback in vivo

Classes and objects - initialization and cleanup of objects - constructor call rules
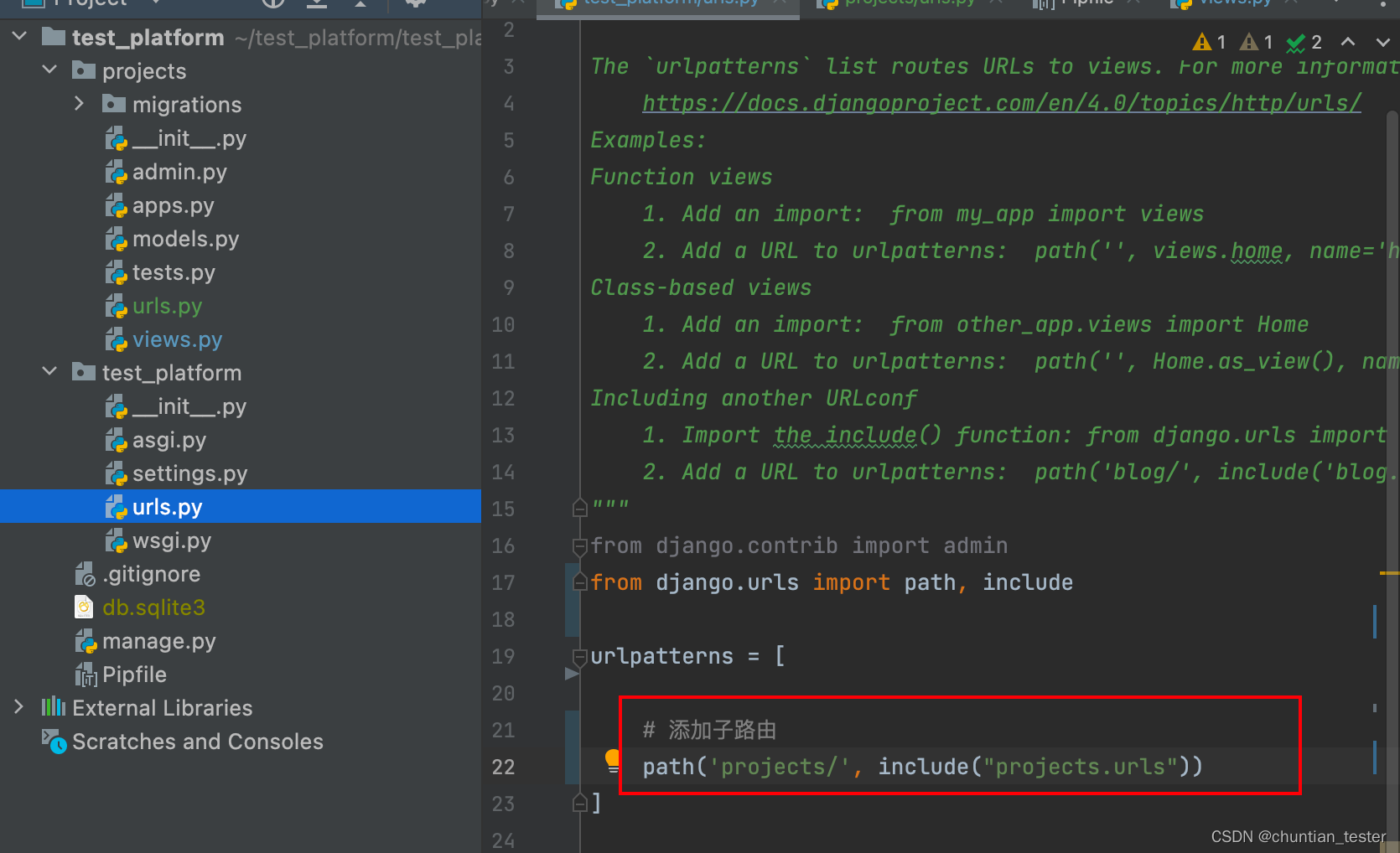
Create + register sub apps_ Define routes, global routes and sub routes
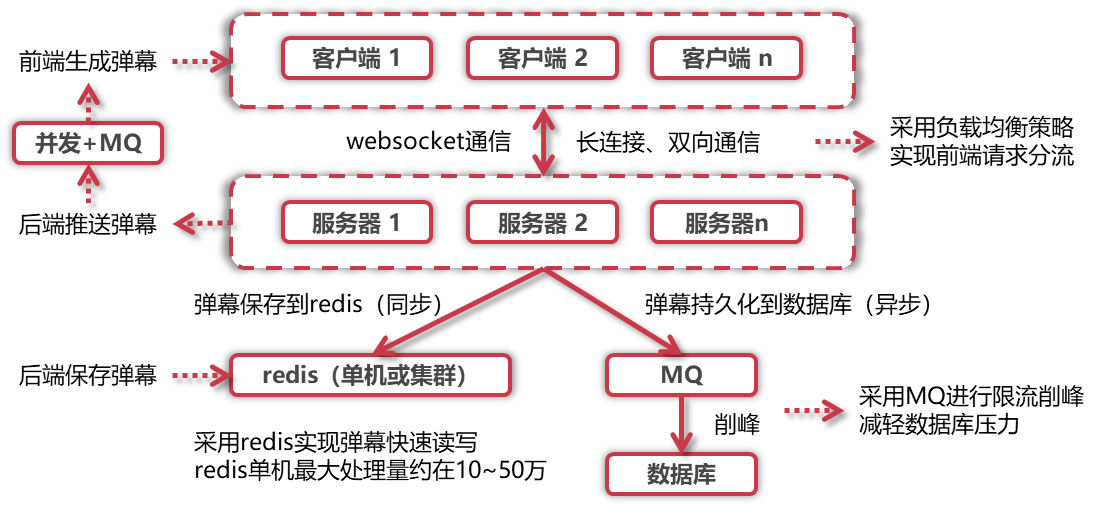
面试项目技术栈总结
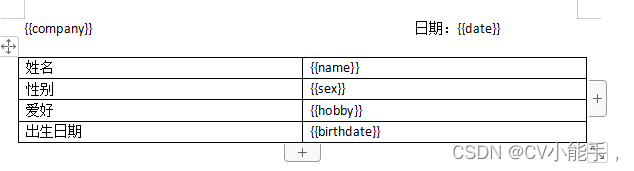
easyPOI
[advanced ROS] Lesson 6 recording and playback in ROS (rosbag)
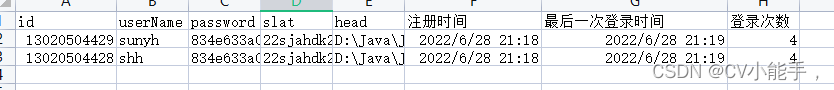
easyExcel

Restcloud ETL cross database data aggregation operation

Thread safe singleton mode
随机推荐
Informatics Olympiad one general question bank 1006 a+b questions
Didi programmers are despised by relatives: an annual salary of 800000 is not as good as two teachers
SQL statement
awk从入门到入土(3)awk内置函数printf和print实现格式化打印
Build a private cloud disk cloudrev
A2L file parsing based on CAN bus (2)
How to change the panet layer in yolov5 to bifpn
搭建私有云盘 cloudreve
Gbase 8C trigger (I)
【教程】chrome关闭跨域策略cors、samesite,跨域带上cookie
GBase 8c系统表pg_database
Gbase 8C system table PG_ collation
Linear rectification function relu and its variants in deep learning activation function
As a leader, how to control the code version and demand development when the epidemic comes| Community essay solicitation
HTB-Devel
MUX VLAN Foundation
random shuffle注意
Wechat - developed by wechat official account Net core access
GBase 8c 创建用户/角色 示例二
Memory pool (understand the process of new developing space from the perspective of kernel)
![[advanced ROS] Lesson 6 recording and playback in ROS (rosbag)](/img/84/abde1c0d5441eb8dec2bacb60d19e9)