当前位置:网站首页>Tencent security released the white paper on BOT Management | interpreting BOT attacks and exploring ways to protect
Tencent security released the white paper on BOT Management | interpreting BOT attacks and exploring ways to protect
2022-07-08 00:09:00 【Tencent security】
Limited edition shoes 、 Concert tickets 、 Train tickets 、 Limited seconds …… These rush buying scenes , Why can't you always grab ? actually , With you “ Fight fast ” Many of them are not real people , It's malice BOT. Malicious BOT Usually use proxy or second dial IP、 Mobile group control and other means , To crawl information and data 、 Collect wool and other malicious attacks , It is increasingly damaging the interests of enterprises and users .
To help enterprises fully understand BOT Flow composition 、 Attack characteristics 、 Harm, etc , And provide malicious information for enterprises BOT Flow protection ideas .6 month 30 Japan , Tencent security released 《BOT Management white paper 》( hereinafter referred to as 《 white paper 》), Yes 2022 In the first half of BOT The flow situation is analyzed in depth . conference , Tencent security WAF Senior product expert maziyang Yes 《 white paper 》 A detailed interpretation of , Introduced the mainstream malicious BOT Traffic countermeasures , Help enterprises prevent new attacks .
meanwhile , Kong song, deputy director of the open source and software security department of the Institute of cloud computing and big data, China Academy of information and communications brought 《 The new trend of application security in the cloud era 》 Keynote speech of , Zhangweiyao, information security director of Huazhu Group Also shared with Huazhu Group BOT Attack protection practice , For enterprises to deal with BOT Attack provides experience reference .
BOT The attack is industrialized 、 Popularization 、 Automation trends
So-called BOT, yes Robot( robot ) For short , Generally refers to invisible virtual robots , It can also be regarded as intelligent software that automatically completes a task .BOT Traffic , It refers to... On the Internet Web Website 、APP application 、API Interface through tool script 、 Automated program traffic accessed by non manual operations such as crawlers or simulators .
BOT The quality of the flow is determined by its intention and behavior , Such as search engine 、 Normal traffic such as statistics and advertising programs can improve website ranking , Website monitoring to improve user experience BOT Called good BOT Traffic ; And use proxy or second dial IP、 Mobile group control and other means to achieve information data crawling 、 Plucking wool 、 Plug in cheating and other malicious attacks BOT Is malicious BOT Traffic .
Under the catalysis of the rapid development of digital technology and the epidemic , The digital transformation of enterprises accelerates , The traffic in cyberspace is growing explosively . According to the 《BOT Management white paper 》 Statistics display ,2022 In the first half of BOT Traffic accounts for about% of the total Internet traffic 60%, On average, it reaches 110 Billion +; Among them, those with malicious aggressiveness BOT The proportion of flow is as high as 46%, malice BOT The harm of flow needs urgent attention .

(《BOT Management white paper 》 Show ,2022 Malicious in the first half of the year BOT The flow accounts for 46%)
Ma Ziyang is 《 white paper 》 It means ,BOT The complexity and frequency of attacks are escalating ,2022 In the first half of , Extremely malicious on average every month BOT The proportion of traffic will reach 27%, malice BOT The traffic growth trend is rapid, and multiple ends are mixed , The target of attack is from business resource type BOT Gradually switch to business content API type BOT, Multi terminal BOT Mixed flow , With BOT The constant iteration of Technology ,BOT Technology is more used in network attacks .
- BOT Attack industrialization 、 Popularization 、 Concealment 、 automation
- 2022 In the first half of BOT The means and technology of attack are more popular ,BOT The initiation of traffic is no longer limited to the grey and black production business .
- 2022 In the first half of BOT Technological means vary , malice BOT It is more difficult to identify and protect traffic .
- 2022 In the first half of the year, cyber attacks became more automated 、 Weaponization .
In Ma Ziyang's view ,BOT Traffic needs multi-dimensional governance : From the data dimension , It is necessary to protect the data and information of core assets from BOT Infringe upon ; From a business perspective , Need protection BOT Impact on platform business stability ; From the perspective of security , It is necessary to protect the basic settings from the scanner . Rely on client-side risk identification 、 Security intelligence 、 Intelligent analysis , It can help build a multi-level and systematic defense line for detection and response .
meanwhile , The white paper combs, including crawler robots 、 Grab robot 、 Spam bots 、 Social media robots, etc 9 Kind of BOT Common types , as well as BOT Main countermeasures and Countermeasures . for example , Rule based intelligence + Client risk identification + machine learning +AI Of Anti-BOT programme , Through rule intelligence, there will be abnormal IP( agent 、 Scanner 、 Threat Intelligence )、BOT Access features for fast filtering , Then, check whether it is a real person or a real machine through the client-side risk identification 、 Finally, through the back-end machine learning +AI The analysis of the scheme leads to abnormal access behavior , And dispose of .
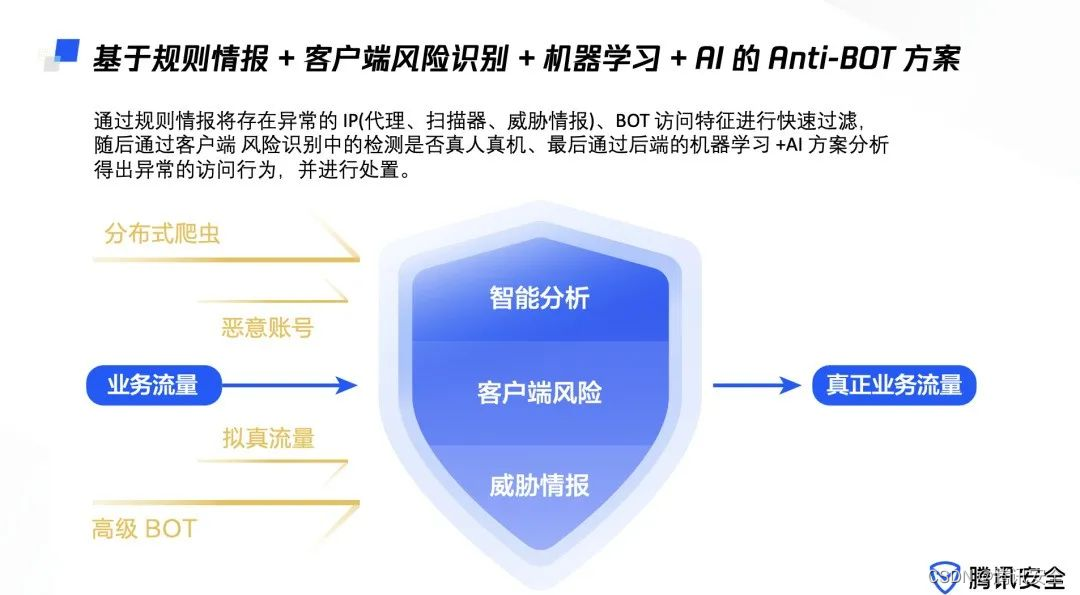
( Rule based intelligence + Client risk identification + machine learning +AI Of Anti-BOT programme )
WAF Become one of the most critical means of applying security protection
In the face of the continuous evolution of network attacks on the cloud and BOT The surge in traffic ,WAF The exploration and innovation of security solutions has become a new driving force for global security manufacturers . meanwhile , With containerization 、 Microservices, development, operation and maintenance (DevOps) And so on ,WAF Products are becoming cloud native WAF evolution , And it can better adapt to the cloud computing environment, which is more fine-grained for network security 、 More agile 、 More flexible requirements .
Kong song is 《 The new trend of application security in the cloud era 》 In the speech , The current application security situation is grim 、 Security capabilities need to be upgraded , In terms of quantity , Frequent security incidents , only 2021 Websites in China were tampered with 、 Counterfeiting 、 There are three kinds of security incidents implanted in the back door as high as 20 All the , And cloud application is the main goal ; In terms of type , Attack methods are showing a new trend ,2021 Among all the attacks on e-commerce websites in 57% from BOT launch .

( Kong song 《 The new trend of application security in the cloud era 》)
“WAF As one of the most critical means to realize application security protection , Constantly adapt to changes in security needs , Inherit hardware WAF、 Software WAF Cloud of core functions WAF, Rely on the foundation Web protective 、CC Malicious attack protection 、 Reptile protection 、 Vulnerability virtual patch 、 Sensitive information is leak proof 、 The six core capabilities of web page tamper resistance can quickly form a security strategy to deal with new vulnerabilities and update the whole network , Whereas BOT The means of attack are constantly developing , The future needs to be BOT The protection is constantly advanced , And then escort the operation safety .” Kongsong said .
Tencent security WAF It's based on AI One stop shop for Web Business operation risk protection scheme , Precipitated Tencent 20 Many years of experience in business security operation and black and gray industry confrontation , In addition to preventing against Web Common attacks on application layer , It can also effectively prevent reptiles 、 Plucking wool 、 Brute force 、CC Such attacks , adopt Web Intrusion Prevention 、0day Bug fix 、 Malicious access penalty 、 Cloud backup, tamper proof and other multi-dimensional defense strategies comprehensively protect the system and business security of the website , Escort customers' cloud security .

( Tencent security WAF BOT Management system )
in the light of BOT protective , Tencent security WAF Combine security intelligence with BOT IP Combination of identification modules , At the same time, with the help of client-side risk identification system and multi-dimensional real-time analysis , Established BOT Detection response system , Quickly perceive the threat level of the source 、 Dealing with distributed BOT、 Advanced continuous BOT etc. . Tencent security WAF To build the BOT Solution , Can identify known and unknown BOT, And according to the business impact and detection methods , Yes BOT Classification, qualitative and quantitative , For each different type of BOT Assign appropriate management policies , Try to reduce the burden of the origin server and the impact on business and IT Influence , Avoid customer service resources being occupied .
According to maziyang ,BOT Man machine confrontation is more difficult , One is to ensure that the access is not forged , The second is to turn the unknown into the known , Third, real-time response 、 Identify advanced persistence BOT And malice BOT Impact on business . Tencent security WAF With the help of threat intelligence module 、 Client side risk identification module , Help customers build a defense line of client risk perception 、 Security intelligence line 、 Intelligent analysis defense , Form a dynamic closed loop based on data drive BOT management .
Tencent security WAF Our technical strength has been IDC、 Sullivan 、Forrester And other international authoritative research institutions . It's just 2021 year 12 month , Tencent security BOT Management ability has also been Forrester《Now Tech: Bot Management, Q4 2021》 Approval of the report . at present , Tencent security WAF It has been widely used in Pan Internet 、 Finance 、 Government affairs and other fields , By Tencent music 、 Carrefour 、 Bank for economic construction 、 Huazhu group 、 Only play high praise from customers in different industries such as technology .
Tencent security WAF Help enterprises build BOT Protective weapon
stay 《 white paper 》 conference , Zhangweiyao, director of information security of Huazhu group, brought WAF Product response BOT Experience sharing of attack . According to Zhang Weiyao , Huazhu group has businesses all over the world 17 A country , Facing the core API vulnerable 、 Customer data anti disclosure 、 The risk of multi terminal access is wide and the risk of hotel price information being crawled , At the same time, a large number of core interfaces are continuously BOT Traffic access , Affect normal business access .
To be specific , Key specific API Yi often faces replay attacks 、 Malicious scanning and other risky behaviors ; In terms of data security, we need to focus on protecting the customer privacy data involved in the internal system ;APP、H5、 Multiple client access types such as applets result in high attack camouflage ; Besides , Malicious crawler visits are mixed 、 Crawl a lot of hotel price information , As a result, the hotel price is automatically crawled and traversed , Preferential strategies are known by peers . In view of this , It needs to be targeted BOT Strategy , Explain the safety risks .

( The overall network architecture of Huazhu )
Zhang Weiyao said , From the perspective of the overall network architecture, Huazhu is a hybrid Cloud Architecture , And some applications are running on Tencent cloud , At the same time, the offline computer room and Tencent security WAF We got through . Thanks to Tencent security WAF Provided BOT Solution , Huazhu has realized the right BOT Fine grained analysis of traffic , At the same time, with the help of Tencent security BOT management , Realized with BOT Advanced analysis of data , Include BOT Characteristics analysis 、BOT Detailed feature dimension including label exception publishing , as well as BOT Exception access UA Ranking 、BOT UA The client characteristic dimension represented by the access type .
Besides , Through front-end confrontation 、 Add login status 、 Four measures for big data behavior analysis and human-machine identification , Tencent security WAF Help Huazhu group to quickly identify the types of client risks , Shut out malicious terminals , And can effectively find group control equipment . meanwhile , Based on machine learning model + Real time traffic statistical analysis , Effectively discover users with abnormal access , For agents 、IDC Wait for non base station users 、BOT High scores and other suspicious users set man-machine identification verification code , Block non human traffic .

( Huazhu group security through Tencent WAF Realized business value )
At the practical effect level , Tencent security WAF Help Huazhu group protect domain names 140+, Provide website security protection , And pass BOT Behavior management governance 99% Malice BOT Reptile traffic , adopt BOT Traffic analysis found that there was ultra vires API, Also through access BOT SDK Realize the unified protection and control of multiple terminals , Help enterprises finally realize business value .
Under the epidemic , Further development of cyberspace traffic , Make malicious BOT It is more difficult to identify and protect traffic , malice BOT Events emerge one after another , The logic of key online business systems of enterprises is becoming more and more complex . Tencent security WAF Through to BOT Manage typical scenarios for hierarchy , in the light of Web End 、 Mobile 、API Take different treatment strategies , Help enterprises build one-stop BOT Solution .
future , Tencent security WAF It will also continuously optimize and upgrade products and services , Fight against malicious traffic with enterprises and partners , Achieve efficiency 、 Intelligent malice BOT protective .
Click on the link below , You can download the full version of Tencent security 《BOT Management white paper 》, Unlock BOT The way of flow management !
边栏推荐
- Resolve the URL of token
- Chisel tutorial - 00 Ex.scala metals plug-in (vs Code), SBT and coursier exchange endogenous
- Binary sort tree [BST] - create, find, delete, output
- Handwriting a simulated reentrantlock
- 35岁真就成了职业危机?不,我的技术在积累,我还越吃越香了
- 【编程题】【Scratch二级】2019.03 垃圾分类
- 数据湖(十五):Spark与Iceberg整合写操作
- 串联二极管,提高耐压
- Anaconda+pycharm+pyqt5 configuration problem: pyuic5 cannot be found exe
- Go time package common functions
猜你喜欢

BSS 7230 flame retardant performance test of aviation interior materials
Kubectl 好用的命令行工具:oh-my-zsh 技巧和窍门
Problems faced when connecting to sqlserver after downloading (I)
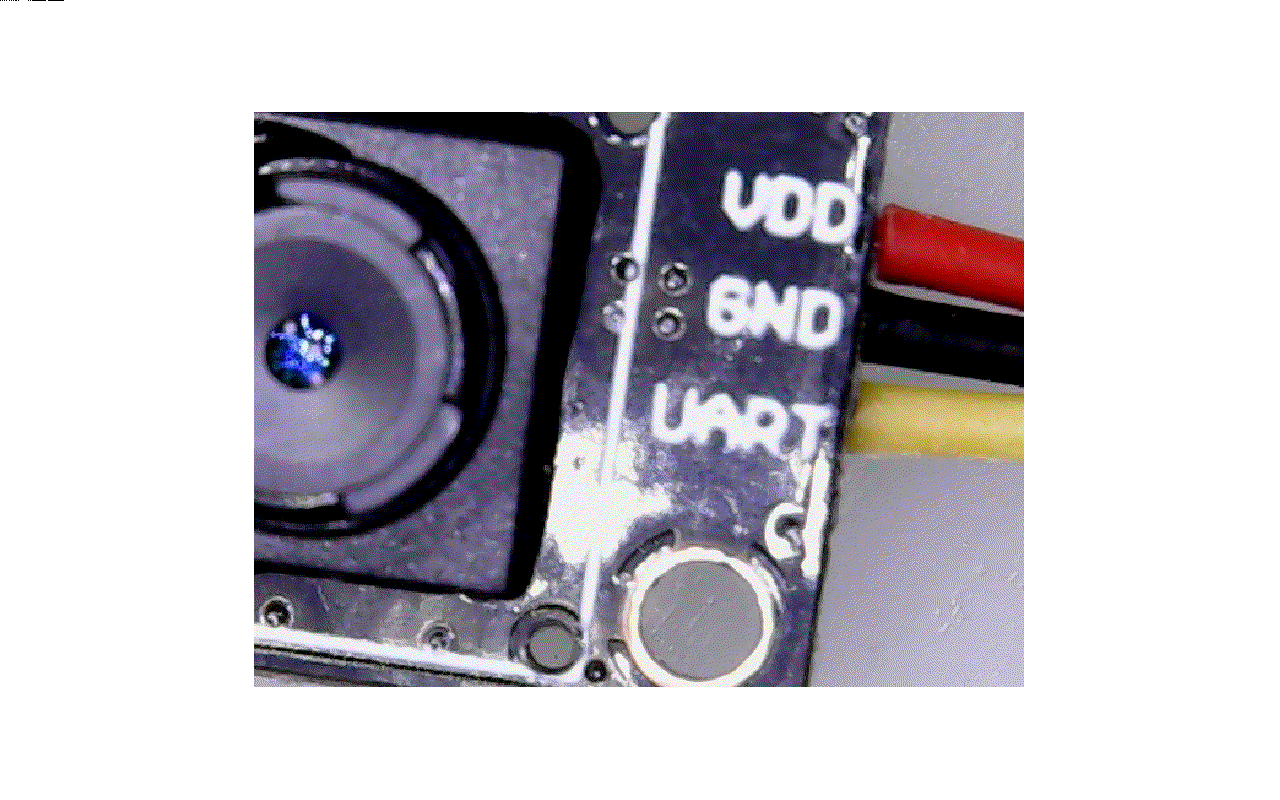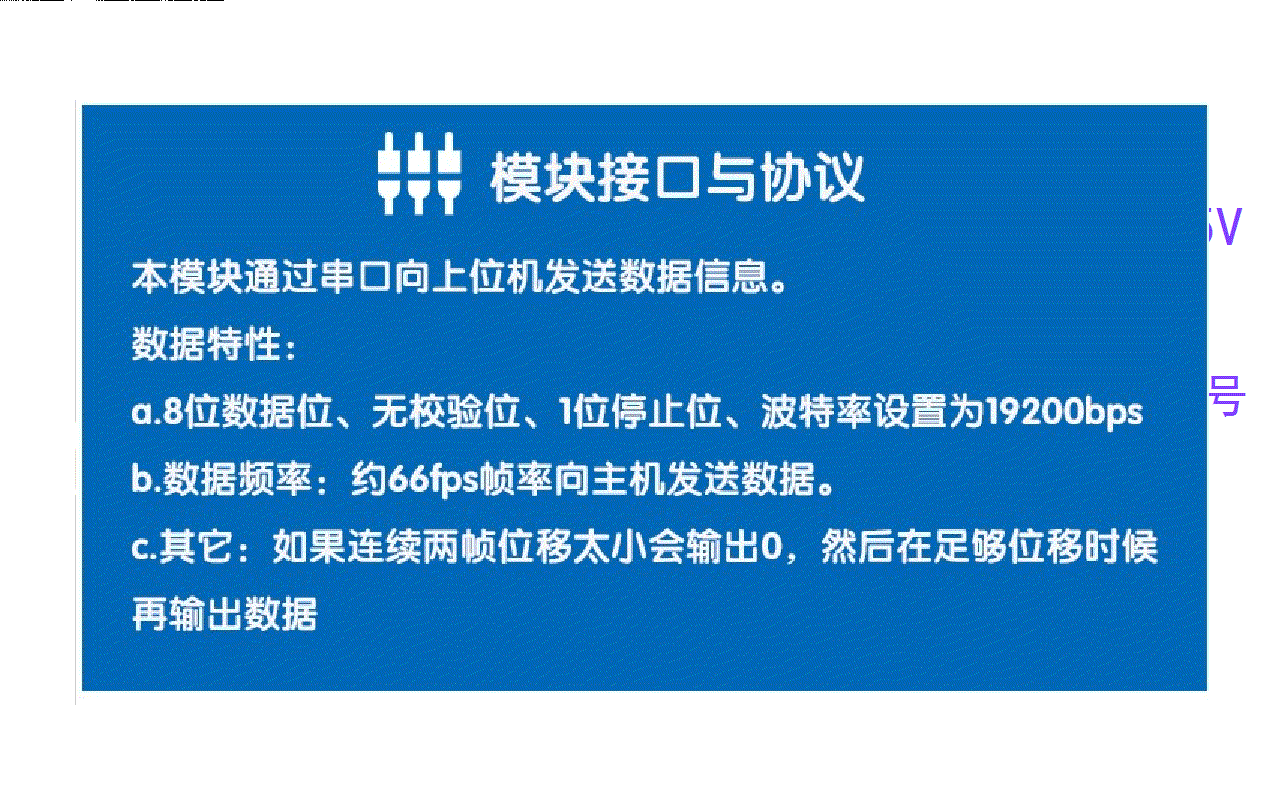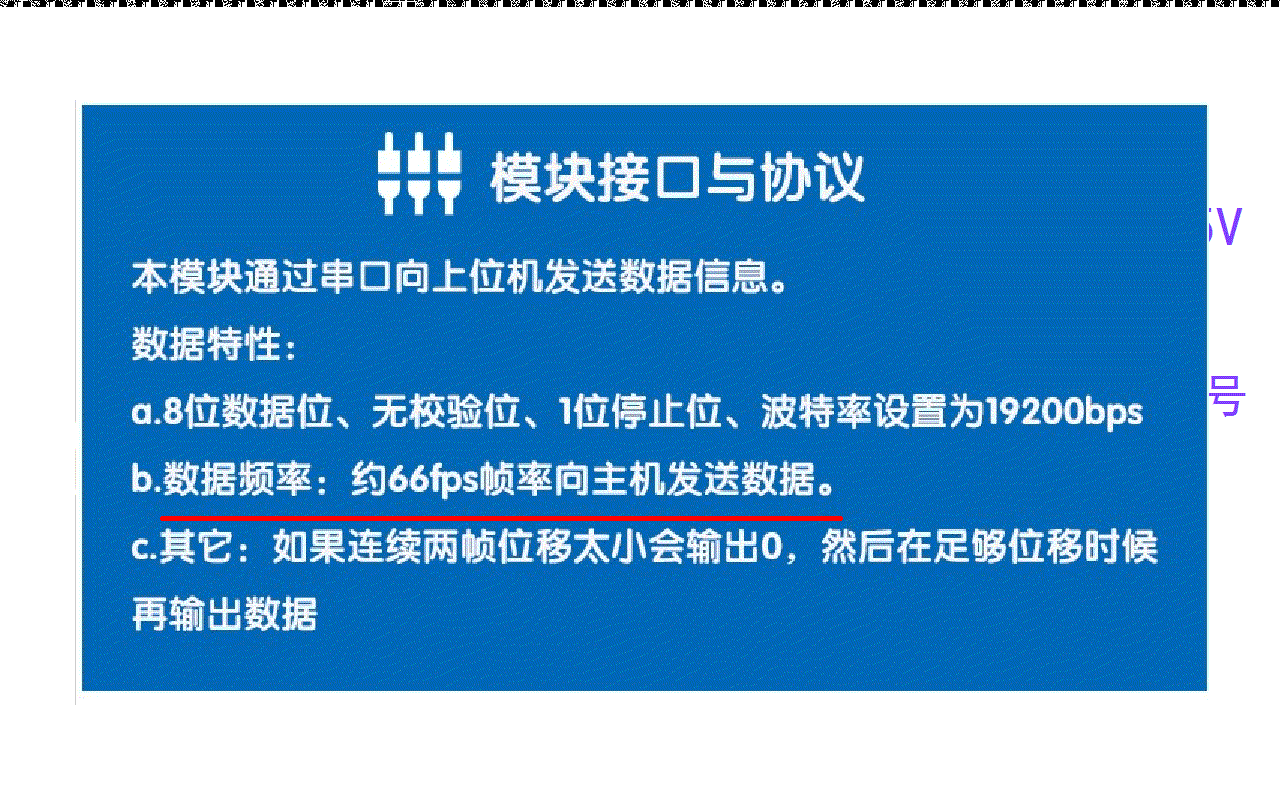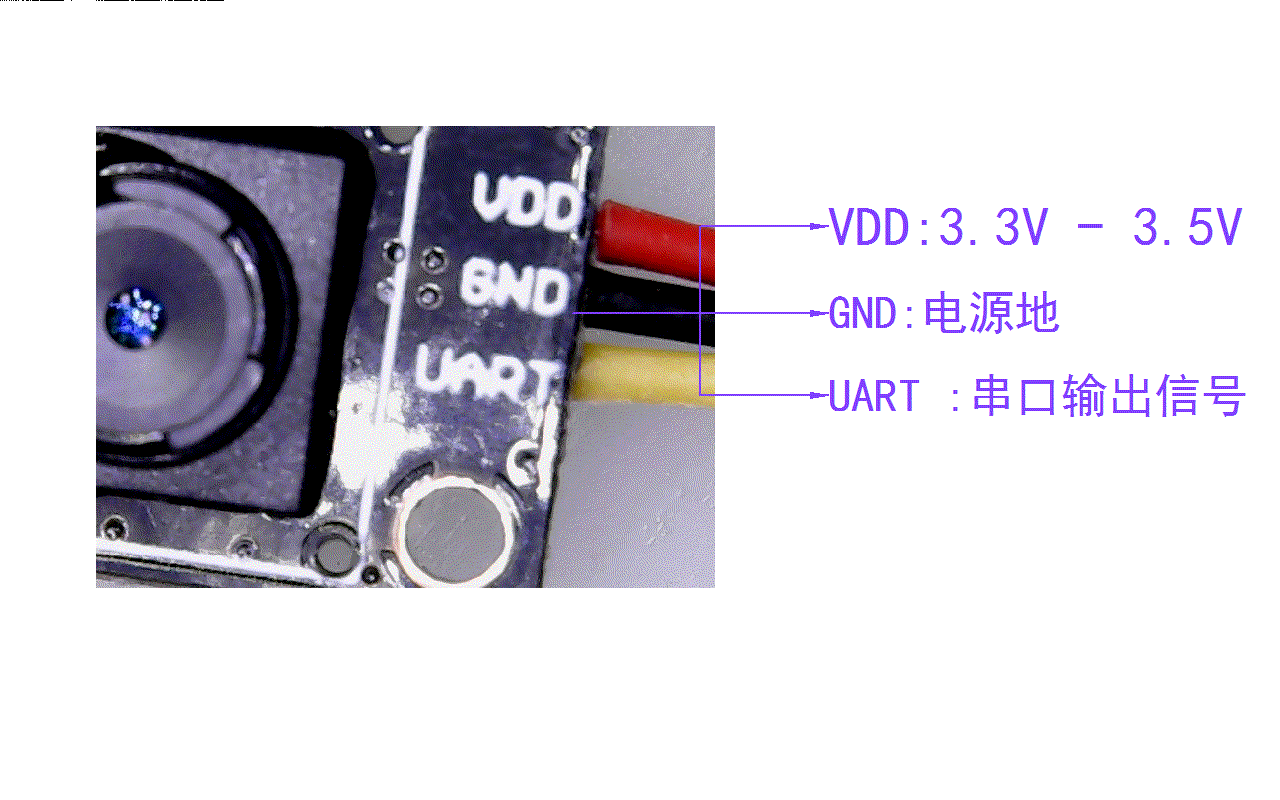
Preliminary test of optical flow sensor: gl9306
52岁的周鸿祎,还年轻吗?

Rectification characteristics of fast recovery diode
Daily question brushing record (16)

腾讯安全发布《BOT管理白皮书》|解读BOT攻击,探索防护之道

Install sqlserver2019
Automated testing: robot framework is a practical skill that 90% of people want to know
随机推荐
10 schemes to ensure interface data security
在网页中打开展示pdf文件
Handwriting a simulated reentrantlock
Chisel tutorial - 04 Control flow in chisel
【leetcode】day1
Detailed explanation of interview questions: the history of blood and tears in implementing distributed locks with redis
The result of innovation in professional courses such as robotics (Automation)
关于组织2021-2022全国青少年电子信息智能创新大赛西南赛区(四川)复赛的通知
2022.7.7-----leetcode. six hundred and forty-eight
数据湖(十五):Spark与Iceberg整合写操作
[the most detailed in history] statistical description of overdue days in credit
One click free translation of more than 300 pages of PDF documents
2022.7.7-----leetcode.648
Stm32f1 and stm32cubeide programming example - rotary encoder drive
快速上手使用本地测试工具postman
Solutions to problems in sqlserver deleting data in tables
Scrapy framework
limit 与offset的用法(转载)
At the age of 35, I made a decision to face unemployment
Kubectl 好用的命令行工具:oh-my-zsh 技巧和窍门
 https://mktsaas.tencent-cloud.com/web/jumpmini.html?scene=0064DC57C7212AD2B52833BC0D9A3C4B&platform=1
https://mktsaas.tencent-cloud.com/web/jumpmini.html?scene=0064DC57C7212AD2B52833BC0D9A3C4B&platform=1