当前位置:网站首页>Web architecture design process
Web architecture design process
2022-07-07 05:40:00 【Qin Tian】
Catalog
One 、 Architecture evolution
1、 The initial set up
Framework based , Running on the Tomcat In the container . file 、 database 、 The application is on a server .
2、 Service separation
As the number of users increases , A single server cannot meet the load of the system , The application server and data server can be deployed separately , If possible, you can also deploy the file server separately .
3、 Reverse proxy
In order to improve the service processing capacity , We are Tomcat Add a proxy server in front of the container , such as Nginx、apache also . The user's request is sent to the reverse proxy , Then the reverse proxy forwards the request to the back-end server . Strictly speaking ,Nginx Belong to web The server , Generally deal with static html、css、js request , and Tomcat Belong to web Containers , Designed to handle JSP request , Of course Tomcat Also support html Of , It just didn't work Nginx All right .
4、 Dynamic and static separation
Based on the above Nginx Reverse proxy , We can also achieve Dynamic and static separation , Static requests such as html、css、js Wait for the request to be given to Nginx Handle , Dynamic requests are distributed to the backend Tomcat Handle .Nginx Upgrade to 1.9.5+ Can be opened HTTP/2.0 Time , Accelerate website access . Of course , If the company doesn't need money , CDN It's also a good choice .
5、 Service split
In this era when distributed microservices have become popular , In fact, we don't need to step on too many pits , It's easy to split . There are relatively mature technologies on the market , For example, Alibaba open source Dubbo( The official made it clear that the maintenance has begun ),Spring The family's SpringCloud, Of course, how to implement it , Both technology and business should be well controlled .
Microservices and lightweight communications :
- Synchronous communication and asynchronous communication
- The remote invocation RPC
- REST
- Message queue
6、 Continuous integration deployment
After service split , With it comes continuous integration deployment , You may use the following tools :Docker、Jenkins、Git、Maven. The basic topology is as follows :

The evolution of the entire continuous integration platform architecture is shown in the figure below :

7、 Service cluster
Linux Clusters are mainly divided into three categories ( High availability cluster , Load balancing cluster , Scientific computing cluster ). Actually , The load balancing cluster is the most common one we come into contact with in production .
(1) Load balancing implementation
- DNS Load balancing , General domain name registrants dns Server does not support
- Four layer load balancing (F5、LVS), Working in TCP Under the agreement
- Seven layer load balancing (Nginx、haproxy), Working in Http Under the agreement
(2) Distributed session
Everybody knows , Services are generally divided into stateful and stateless , And distributed sessoion For stateful Services .
8、 Read / write separation
MySql Master slave configuration , Read write separation and introduction of middleware , Open source MyCat, Ali's DRDS All good choices . If high availability is required , But there is no corresponding technical guarantee , It is recommended to use Alibaba cloud's RDS perhaps Redis Correlation database , Save time, effort and money .
9、 Cache optimization
The introduction of caching is nothing more than to reduce the pressure of back-end database services , Prevent it " Strike ". Common cache services are ,Ehcache、OsCache、MemCache、Redis, Of course, these are the mainstream cache technology implementation that can stand the test , especially Redis It has been widely used in distributed cluster services , And proved its superior performance .
10、 Message queue
1、 Asynchronous notification : For example, SMS verification , E-mail verifies these non real-time feedback logical operations .

2、 Flow cutting : It should be a common scenario in message queues , Generally, it is widely used in seckill or group robbery activities .
3、 Log processing : Logs are essential in the system , But how to deal with the logs issued by Gao and is really a technical job , Carelessness may overwhelm the whole service . We often use open source logs in our work ELK, Why add one in the middle Kafka perhaps redis That's the reason ( The difference between an influx of people and a queue ).
4、 Message communication : Point to point communication ( Individual to individual ) Or publish subscribe mode ( The chat room ).
11、 The log service
Mentioned in the message queue ELK Open source log component is a good choice for small and medium-sized start-ups .
12、 Security optimization
All these above , If there is no guarantee of safety, it may return to zero .
- Ali cloud, VPN Virtual private network and security group configuration
- If you build your own computer room , Configure the firewall security policy by yourself
- Related service access , such as Mysql、Redis、Solr If there are no special needs, try to use intranet access and set authentication
- Try to use a proxy server , Don't open too many ports
- https coordination HTTP/2.0 It's also a good choice
Two 、 Design principles
1、 High availability
- Load balancing ( Load balancing algorithm )
- Reverse proxy
- Service isolation
- Service restriction
- service degradation ( Automatic graceful degradation )
- Failover
- Time out to try again ( Agent timeout 、 Container timeout 、 Front end timeout 、 Middleware timeout 、 Database timeout 、NoSql Overtime )
- Rollback mechanism ( Online rollback 、 Database version rollback 、 Transaction rollback )
2、 High concurrency
- Client cache ( Reduce network bandwidth 、 Reduce server stress 、 Reduce network latency )
- HTTP cache
- Multi level cache
- Distributed cache
- Connection pool
- Asynchronous concurrency
3、 Distributed transactions
- Two stage submission ( Strong consistency )
- Three stage commit ( Strong consistency )
- Message middleware ( Final consistency ), Recommend Ali's RocketMQ
4、 queue
- Task queue
- Message queue
- Request queue
5、 Database technology
- Master slave copy ( extensible 、 Available backups )
- Read / write separation ( Improve query speed 、 Reduce IO bottleneck 、 High expansion )
- Vertical expansion of monomer ( Separation of business 、 High expansion 、 High performance )
- Horizontal expansion of monomer ( High expansion 、 High performance )
- Data heterogeneity
6、 Network security
- SQL Inject
- XSS attack
- CSRF attack
- Denial of service (DoS,Denial of Service) attack
7、 Load balancing
- The Internet ( Global load balancing ,DNS polling 、CDN Network distribution )
- Hardware ( Local load balancing , Load Balancer 、 Address translation gateway , Efficient but expensive )
- Software ( Local load balancing ,Linux Virtual Server、Nginx、HAProxy)

3、 ... and 、 Essential tools
1、 operating system
Linux( necessary )、 Microsoft
2、 Load balancing
DNS、F5、LVS、Nginx、OpenResty、HAproxy、 Load balancing SLB( Alibaba cloud )
3、 Distributed framework
Dubbo、Motan、Spring Cloud
4、 database middleware
DRDS ( Alibaba cloud )、Mycat、360Atlas
5、 Message queue
RabbitMQ、ZeroMQ、Redis、ActiveMQ、Kafka
6、 Registry Center
Zookeeper、Redis
7、 cache
Redis、Oscache、Memcache、Ehcache
8、 Integrated deployment
Docker、Jenkins、Git、Maven
9、 Storage
OSS、NFS、FastDFS、MogileFS
11、 database
MySql、Redis、MongoDB、PostgreSQL、Memcache、HBase
12、 The Internet
private network VPC、 Elastic public network IP、CDN
Reprint :
WEB Architecture Design Overview - A hundred miles of Twilight - Blog Garden
边栏推荐
- 利用OPNET进行网络单播(一服务器多客户端)仿真的设计、配置及注意点
- Initial experience of annotation
- Différenciation et introduction des services groupés, distribués et microservices
- 论文阅读【Semantic Tag Augmented XlanV Model for Video Captioning】
- Reading the paper [sensor enlarged egocentric video captioning with dynamic modal attention]
- 4. 对象映射 - Mapping.Mapster
- [reading of the paper] a multi branch hybrid transformer network for channel terminal cell segmentation
- Most commonly used high number formula
- Egr-20uscm ground fault relay
- 删除文件时提示‘源文件名长度大于系统支持的长度’无法删除解决办法
猜你喜欢
ssm框架的简单案例

The year of the tiger is coming. Come and make a wish. I heard that the wish will come true
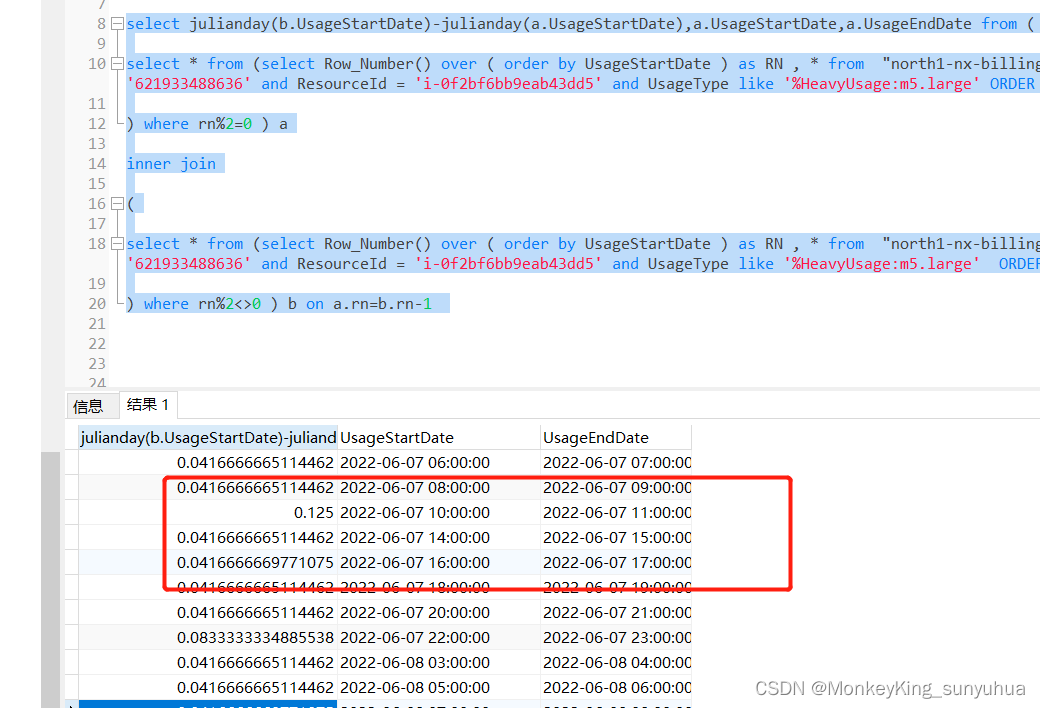
sql查询:将下一行减去上一行,并做相应的计算
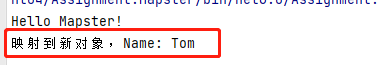
4. Object mapping Mapster
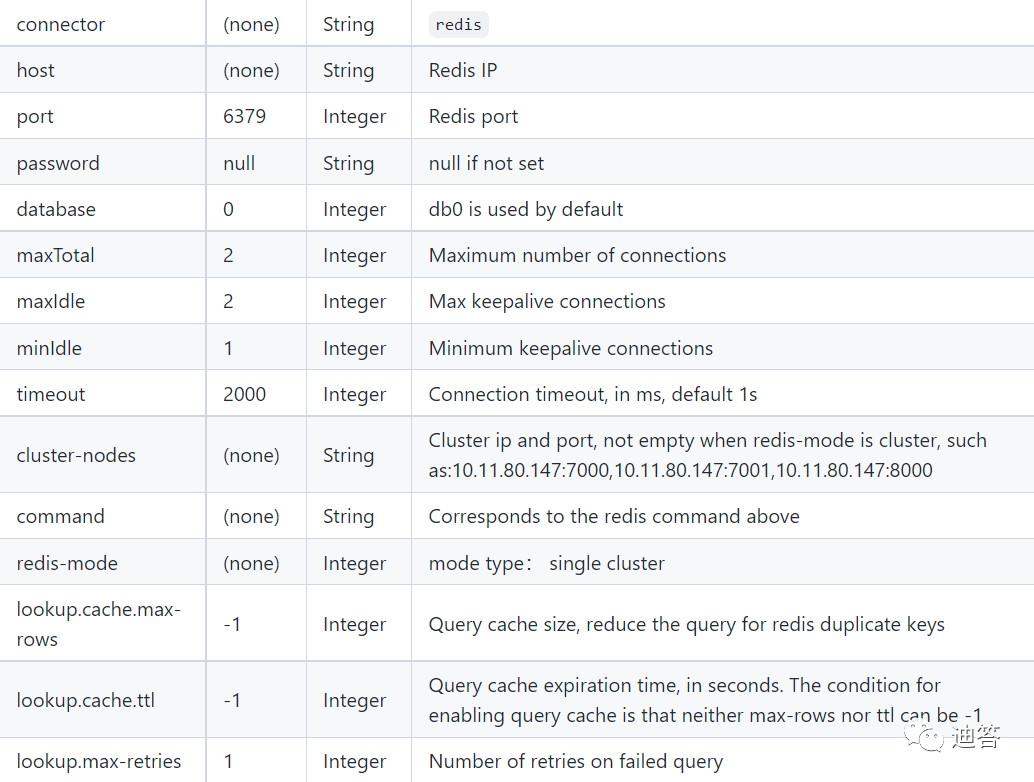
Flink SQL realizes reading and writing redis and dynamically generates hset key
5. Data access - entityframework integration
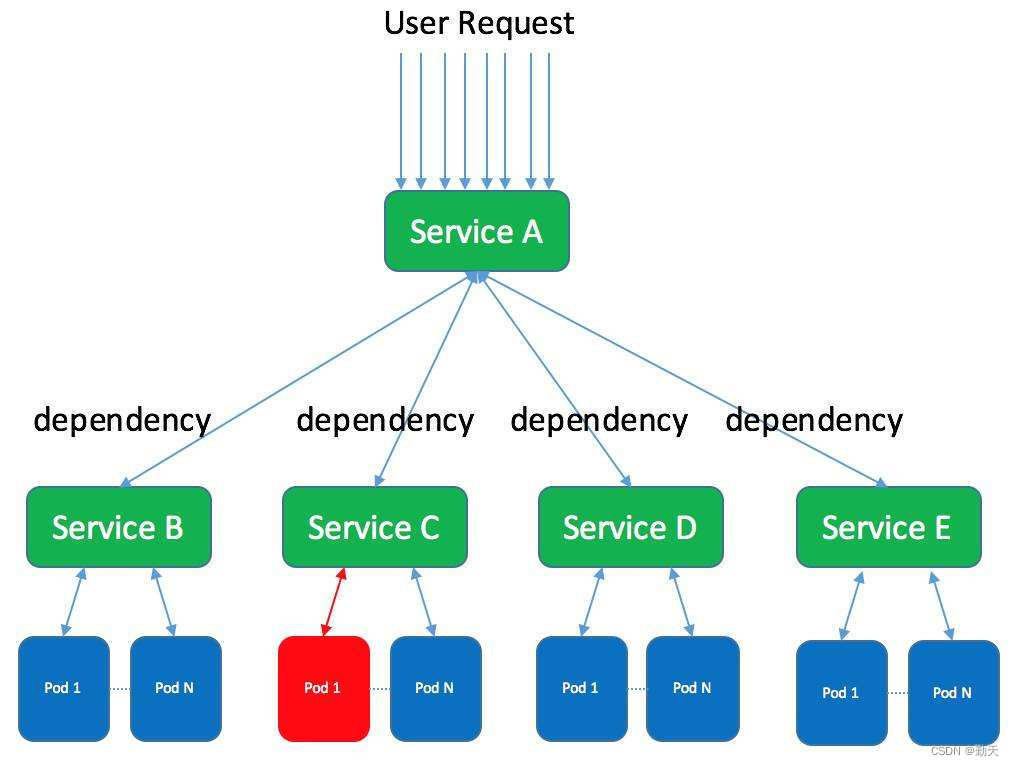
集群、分布式、微服務的區別和介紹
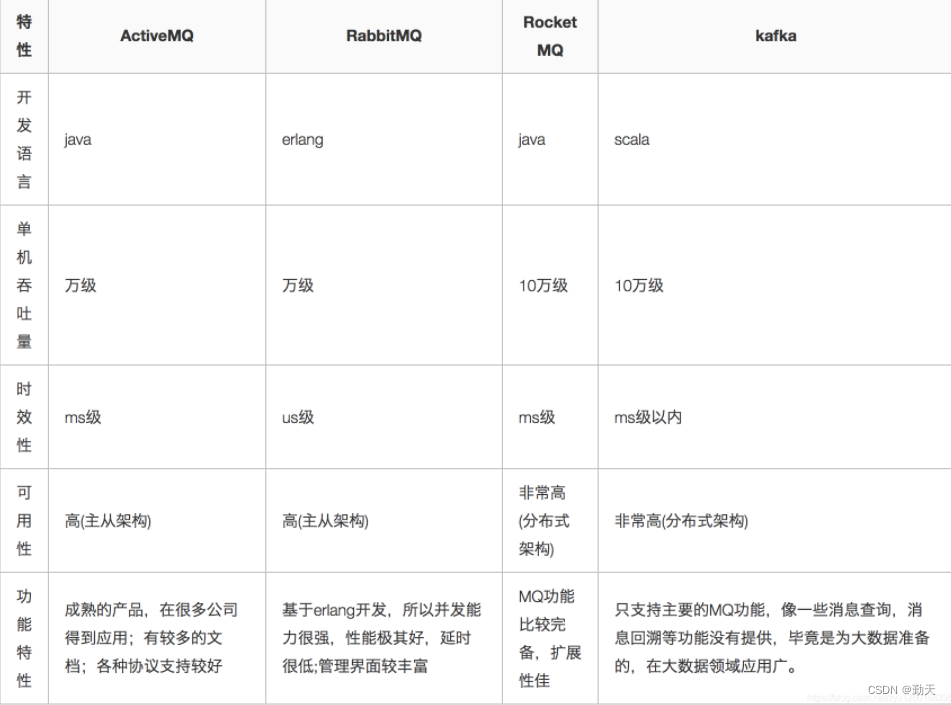
常用消息队列有哪些?
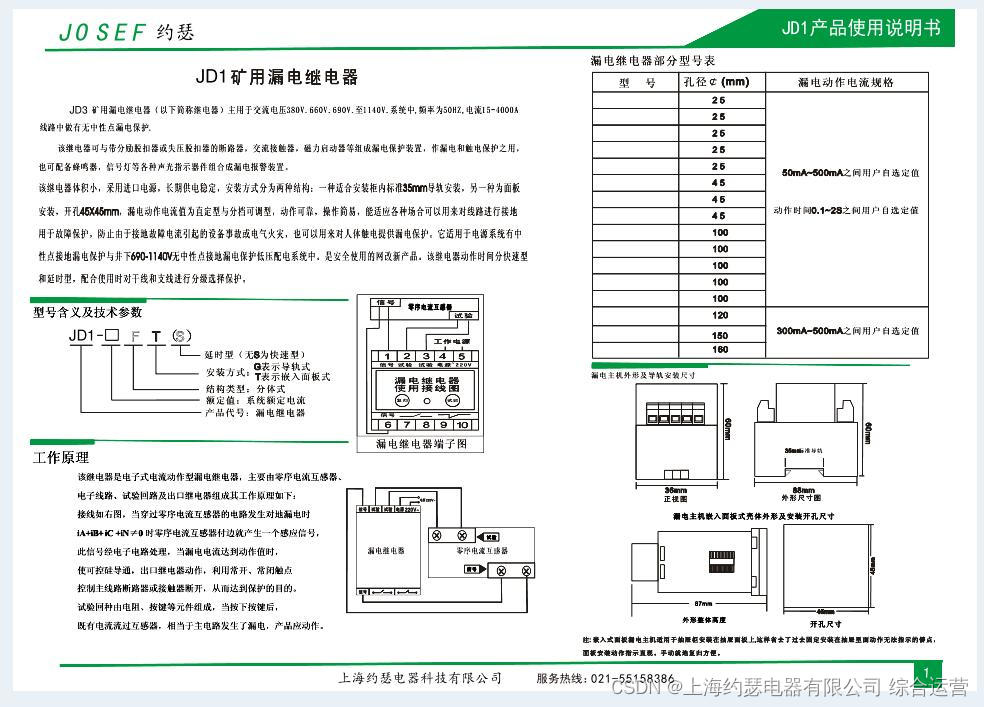
Leakage relay jd1-100
《5》 Table
随机推荐
论文阅读【Semantic Tag Augmented XlanV Model for Video Captioning】
As we media, what websites are there to download video clips for free?
MySQL数据库学习(8) -- mysql 内容补充
《5》 Table
Pinduoduo product details interface, pinduoduo product basic information, pinduoduo product attribute interface
Lombok插件
京东商品详情页API接口、京东商品销量API接口、京东商品列表API接口、京东APP详情API接口、京东详情API接口,京东SKU信息接口
【js组件】date日期显示。
Mapbox Chinese map address
纪念下,我从CSDN搬家到博客园啦!
导航栏根据路由变换颜色
拼多多商品详情接口、拼多多商品基本信息、拼多多商品属性接口
Preliminary practice of niuke.com (9)
Summary of the mean value theorem of higher numbers
Zero sequence aperture of leakage relay jolx-gs62 Φ one hundred
Design, configuration and points for attention of network unicast (one server, multiple clients) simulation using OPNET
什么是依赖注入(DI)
TabLayout修改自定义的Tab标题不生效问题
[论文阅读] Semi-supervised Left Atrium Segmentation with Mutual Consistency Training
实现网页内容可编辑