当前位置:网站首页>Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5
Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5
2022-07-02 19:09:00 【Feita plum】

![]() In this lesson , You will learn how to use FortiEDR RESTful API.
In this lesson , You will learn how to use FortiEDR RESTful API.

 By showing RESTful API The ability to , You will be able to use RESTful API And FortiEDR Interact with the management console .
By showing RESTful API The ability to , You will be able to use RESTful API And FortiEDR Interact with the management console .

 What is? API? You can easily put FortiEDR The functionality of is integrated into the organization's existing software .FortiEDR The central manager supports REST http Of API, For accessing security and communication control data , And equipment and software configuration and operation . Essentially , This is a way to copy the functions of the management console through programming . You can manage device and software configurations 、 Analyze events and repair equipment , None of this requires the use of an administrative console .
What is? API? You can easily put FortiEDR The functionality of is integrated into the organization's existing software .FortiEDR The central manager supports REST http Of API, For accessing security and communication control data , And equipment and software configuration and operation . Essentially , This is a way to copy the functions of the management console through programming . You can manage device and software configurations 、 Analyze events and repair equipment , None of this requires the use of an administrative console .

 RESTful API How it works ? It is based on HTTP Of REST. It USES SSL encryption , And JSON The format returns the protocol information . Token based authentication can be used , Password based authentication can also be used . To use password based authentication , You need to make sure that users are assigned Admin and Rest API role . You can USERS Of the management console under ADMINISTRATION Tab . The API Use several different methods —get To read data ,POST or PUT To update . It has DELETE And some other orders .
RESTful API How it works ? It is based on HTTP Of REST. It USES SSL encryption , And JSON The format returns the protocol information . Token based authentication can be used , Password based authentication can also be used . To use password based authentication , You need to make sure that users are assigned Admin and Rest API role . You can USERS Of the management console under ADMINISTRATION Tab . The API Use several different methods —get To read data ,POST or PUT To update . It has DELETE And some other orders .

 One of the most common problems reported is , When new users first try to use API when , Unauthorized messages will appear . The reason is that the password needs to be reset . When a new user logs into the management console for the first time , Will be forced to change the password . Because it doesn't work API Reset password , So you will get an error message . The solution is simple . To solve this problem , Please click ADMINISTRATION Tab, click USERS. Find the user in the list and click reset password . open “ Reset password ” Dialog box . eliminate “ The next time you log in, you need to change your password ” Check box , Then enter the password and click “ Reset ”. Users should now be able to pass API Sign in . perhaps , You can ask users to use API Log in to the management console and reset their password before calling .
One of the most common problems reported is , When new users first try to use API when , Unauthorized messages will appear . The reason is that the password needs to be reset . When a new user logs into the management console for the first time , Will be forced to change the password . Because it doesn't work API Reset password , So you will get an error message . The solution is simple . To solve this problem , Please click ADMINISTRATION Tab, click USERS. Find the user in the list and click reset password . open “ Reset password ” Dialog box . eliminate “ The next time you log in, you need to change your password ” Check box , Then enter the password and click “ Reset ”. Users should now be able to pass API Sign in . perhaps , You can ask users to use API Log in to the management console and reset their password before calling .

![]() There are two ways to access API. The first way is to use CLI Applications , such as Curl. The figure above shows a typical Curl request . If you use a self signed certificate for the central manager ( This is the default setting ), Then use -k Bypass certificate validation . Input -H, Then enter the authorization type and credentials , Then input URL Parameters . Sample commands to JSON Format returns a list , It contains the organization name 、 Allocated seats 、 Seats in use 、 Expiration date, etc .
There are two ways to access API. The first way is to use CLI Applications , such as Curl. The figure above shows a typical Curl request . If you use a self signed certificate for the central manager ( This is the default setting ), Then use -k Bypass certificate validation . Input -H, Then enter the authorization type and credentials , Then input URL Parameters . Sample commands to JSON Format returns a list , It contains the organization name 、 Allocated seats 、 Seats in use 、 Expiration date, etc .
The second method is to use image Postman or Insomania In this way GUI Applications . You will see with just Curl The format of the request is the same , But formatted as Postman Format . First , choice GET Method , Then input URL Parameters :https://<FortiEDRHOST>/management-rest/organizations/list-organizations. In the image above , You can see a command in the application itself . You can see in the upper left corner GET, And then there was URL Parameters — In this case , You ask for a list of all organizations in a multi tenant environment . Under it , You can see Authorization tab . stay “TYPE” Select... From the drop-down list “Basic Auth”, Enter your username and password . In this lesson, you will learn more about authentication . At the bottom , You can see the result returned from the request , A list of all organizations JSON file . You can see the name of the organization 、 Allocated seats 、 Seats in use 、 Expiration date, etc .

 The figure above shows some useful API command . you are here FortiEDR RESTful API The manual can get a complete list and detailed instructions .
The figure above shows some useful API command . you are here FortiEDR RESTful API The manual can get a complete list and detailed instructions .

 Why use Postman? This is the API A very simple way to interact , It is a clean and simple interface , It preserves API Request history , So you can have a list of previous work done , You can reuse a request , So you don't have to enter all the information again .
Why use Postman? This is the API A very simple way to interact , It is a clean and simple interface , It preserves API Request history , So you can have a list of previous work done , You can reuse a request , So you don't have to enter all the information again .
Here are some uses postman The technique of . First , Make sure the correct request method is selected on the left side of the screen . In the example shown above , You can see a PUT request . The second is URL Parameters . Later in this lesson , You will learn more about body Knowledge of parameters . You can also refer to it FortiEDR RESTful API Guide to get a complete list of options . Some request types require body parameters . under these circumstances , choice Body tab , choice raw, Then select... From the drop-down list on the right side of the screen JSON (application/ JSON) Format . Then you can enter your... In the text field body Parameters . The example shown above changes the event 51516 The state of .

 Take a look at using API Sample workflow . In this scenario , You will be in FortiEDR Investigate threats in the environment . First , You need a list of events , Classify it as malicious or suspicious , And it has the operation of blocking or simulating blocking .
Take a look at using API Sample workflow . In this scenario , You will be in FortiEDR Investigate threats in the environment . First , You need a list of events , Classify it as malicious or suspicious , And it has the operation of blocking or simulating blocking .
here , What you search is information , Instead of changing anything , So you use GET Method . then , Input URL Parameters . You have seen some examples , But this time you are looking for a list of events , So from https Start , Then input FortiEDR host . You can use IP Address or name ( for example acme).fortiedr.com. After the host address , Always input management-rest, Then there are categories 、 event , And then there was call—— In this case, it's list- event . Then add search criteria . By using & Number , You can search multiple search parameters at a time . In this case , You need to search for categories and operations . You can also enter multiple values for each condition , Separate with commas . In this case , We look for two possible classifications and two possible operations .
This search returns JSON List of formats . Every event has quite a lot of information — event ID、 technological process 、 route 、 date 、 state 、 What rules have been violated , wait . To continue the sample workflow , Suppose we are investigating the event shown in the figure above . Pay attention to the event ID, 46426. Next , You will use this in new requests ID.


 Now? , Get the event just copied ID Original event details for . You will send another GET request , This request gets the event ID Original data items , Then add fulldatarequed =true.
Now? , Get the event just copied ID Original event details for . You will send another GET request , This request gets the event ID Original data items , Then add fulldatarequed =true.
Again , You will receive a JSON list , This time, the details about the original item are displayed . Use this information to retrieve the executable . So , You will need the original Eventld、MainProcessld and Application route . Copy these values into a separate text file , So that they can be used later to retrieve samples of malware . There are several things to remember . First , there Eventld Field and the event you copied in the previous picture ID Different . This is the original event ID, This is what you need to retrieve files . The application path must be converted to URL Coding format .


 Now use the information just obtained , Use GET Command to retrieve the executable . Then input URL Parameters . In this case , You need to find the information stored in the forensics , So change the parameter to forensics , And then there was get-event-file command . Then use the information just copied — Original event ID、 process ID And application path — Tell the system the exact file you are looking for .
Now use the information just obtained , Use GET Command to retrieve the executable . Then input URL Parameters . In this case , You need to find the information stored in the forensics , So change the parameter to forensics , And then there was get-event-file command . Then use the information just copied — Original event ID、 process ID And application path — Tell the system the exact file you are looking for .
If you click Send, Your results will be similar to what you see in the upper right corner of the screen . It looks like nonsense , But it is actually a password protected compressed file , Include the file you requested . To get a file in a usable format , have access to Send and Download. Use “ send out ” Drop down menu selection “ send out ” and “ download ”. Now you can save locally zip file . To extract an executable , Input password enCrypted, Capitalization C.


 Next , Delete malicious executables from the user's device . You can use PUT Request to complete this operation . This is a forensics function , Therefore, access to evidence / Remedial equipment . then , Use the format you see here to specify the device name 、 Name and path of the executable file to be deleted . The file should disappear from the device , As the example above shows .
Next , Delete malicious executables from the user's device . You can use PUT Request to complete this operation . This is a forensics function , Therefore, access to evidence / Remedial equipment . then , Use the format you see here to specify the device name 、 Name and path of the executable file to be deleted . The file should disappear from the device , As the example above shows .


 After retrieving the executable , Evaluate it by testing it in a secure sandbox environment . for example , Suppose you verify that the file is malicious . You may want to put the affected collectors into a high security collector group , To curb infection , Until you completely repair the equipment . So , Send a PUT command . You are sending inventory related information , So enter inventory / Mobile collector . Then enter the collector name and target group —— In this case, it is a high security collector group . You can verify the results in the management console . The example in the above figure shows you that you have successfully cwin7-32 Move from the default collector group to the high security collector group .
After retrieving the executable , Evaluate it by testing it in a secure sandbox environment . for example , Suppose you verify that the file is malicious . You may want to put the affected collectors into a high security collector group , To curb infection , Until you completely repair the equipment . So , Send a PUT command . You are sending inventory related information , So enter inventory / Mobile collector . Then enter the collector name and target group —— In this case, it is a high security collector group . You can verify the results in the management console . The example in the above figure shows you that you have successfully cwin7-32 Move from the default collector group to the high security collector group .


 After repairing the device or creating an exception , Mark this event as Handled, So that other management console users know that you have handled it . You can also mark it as Read. To change the event state , Please send a PUT request . You need to modify the event in the event category . then , Event must be specified ID. This time, , You have to finish body Field . take read Set to true, take handle Set to false, Indicates that the event is no longer handled . It is always a good idea to add comments explaining how to handle events and other relevant information . You can do this in the admin console EVENT VIEWER Tab to verify your changes . In the picture above , You can see that the event has been handled , And your comment has been added to event HANDLING window . If you look closely , You can see a light colored sign in the background , It indicates that the event has been handled , And the event is plain text , This means that it is marked as read .
After repairing the device or creating an exception , Mark this event as Handled, So that other management console users know that you have handled it . You can also mark it as Read. To change the event state , Please send a PUT request . You need to modify the event in the event category . then , Event must be specified ID. This time, , You have to finish body Field . take read Set to true, take handle Set to false, Indicates that the event is no longer handled . It is always a good idea to add comments explaining how to handle events and other relevant information . You can do this in the admin console EVENT VIEWER Tab to verify your changes . In the picture above , You can see that the event has been handled , And your comment has been added to event HANDLING window . If you look closely , You can see a light colored sign in the background , It indicates that the event has been handled , And the event is plain text , This means that it is marked as read .


 The figure above shows another solution . Suppose you check the file that triggers the alarm , Found that it is not malware . under these circumstances , You may want to create an exception . You can also pass API To achieve this . Use POST command . In the event category , stay URL Enter... In the parameter events/create-exception. then , You must specify exception parameters , It applies to events ID, Then there is the collector group that you want to apply exceptions , In the example shown above , yes Sales Group , Not all collector groups . We can also specify the destination . The example shown above shows , Exceptions apply to collector groups 、 All destinations and all users .
The figure above shows another solution . Suppose you check the file that triggers the alarm , Found that it is not malware . under these circumstances , You may want to create an exception . You can also pass API To achieve this . Use POST command . In the event category , stay URL Enter... In the parameter events/create-exception. then , You must specify exception parameters , It applies to events ID, Then there is the collector group that you want to apply exceptions , In the example shown above , yes Sales Group , Not all collector groups . We can also specify the destination . The example shown above shows , Exceptions apply to collector groups 、 All destinations and all users .


![]() answer :A
answer :A


 answer :A
answer :A


 By mastering the objectives involved in this lesson , You learned how to be in FortiEDR Use in RESTful API.
By mastering the objectives involved in this lesson , You learned how to be in FortiEDR Use in RESTful API.

边栏推荐
- 27: Chapter 3: develop Passport Service: 10: [registration / login] interface: after the registration / login is OK, save the user session information (uid, utoken) to redis and cookies; (one main poi
- 全志A33使用主线U-Boot
- 新手必看,点击两个按钮切换至不同的内容
- Mysql高级篇学习总结8:InnoDB数据存储结构页的概述、页的内部结构、行格式
- 教程篇(5.0) 09. RESTful API * FortiEDR * Fortinet 网络安全专家 NSE 5
- R language dplyr package Na_ The if function converts the control in the vector value into the missing value Na, and converts the specified content into the missing value Na according to the mapping r
- Page title component
- Troubleshooting: kubectl reports an error validationerror: unknown field \u00a0
- [0701] [论文阅读] Alleviating Data Imbalance Issue with Perturbed Input During Inference
- 拦截器与过滤器的区别
猜你喜欢
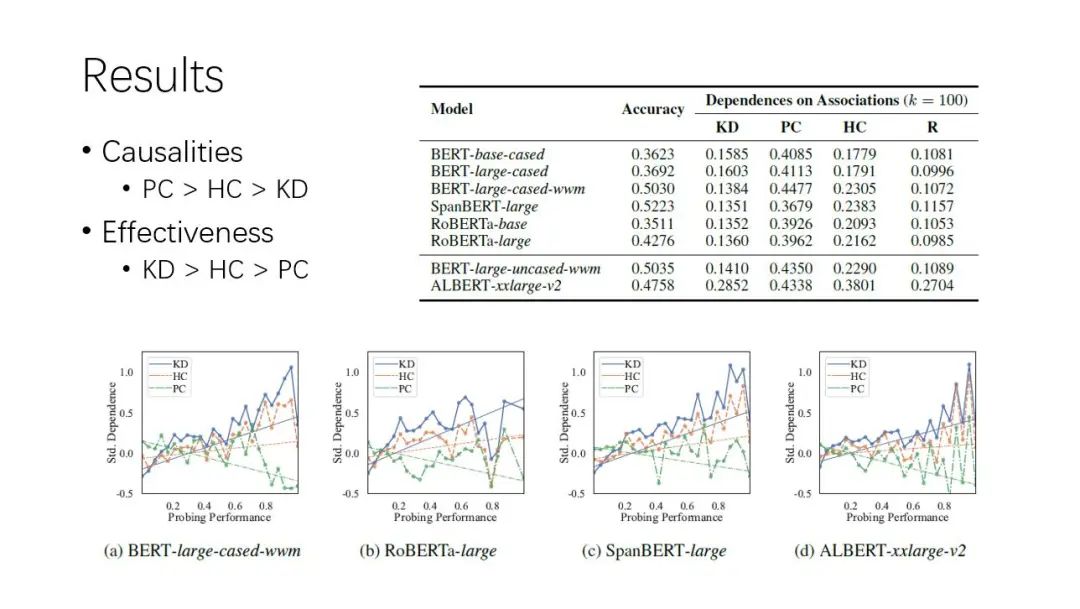
Introduction to the paper | analysis and criticism of using the pre training language model as a knowledge base

Leetcode (81) -- search rotation sort array II
Learning summary of MySQL advanced 6: concept and understanding of index, detailed explanation of b+ tree generation process, comparison between MyISAM and InnoDB

STM32G0 USB DFU 升级校验出错-2

开发固定资产管理系统,开发固定资产管理系统用什么语音
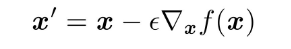
深度学习数学基础
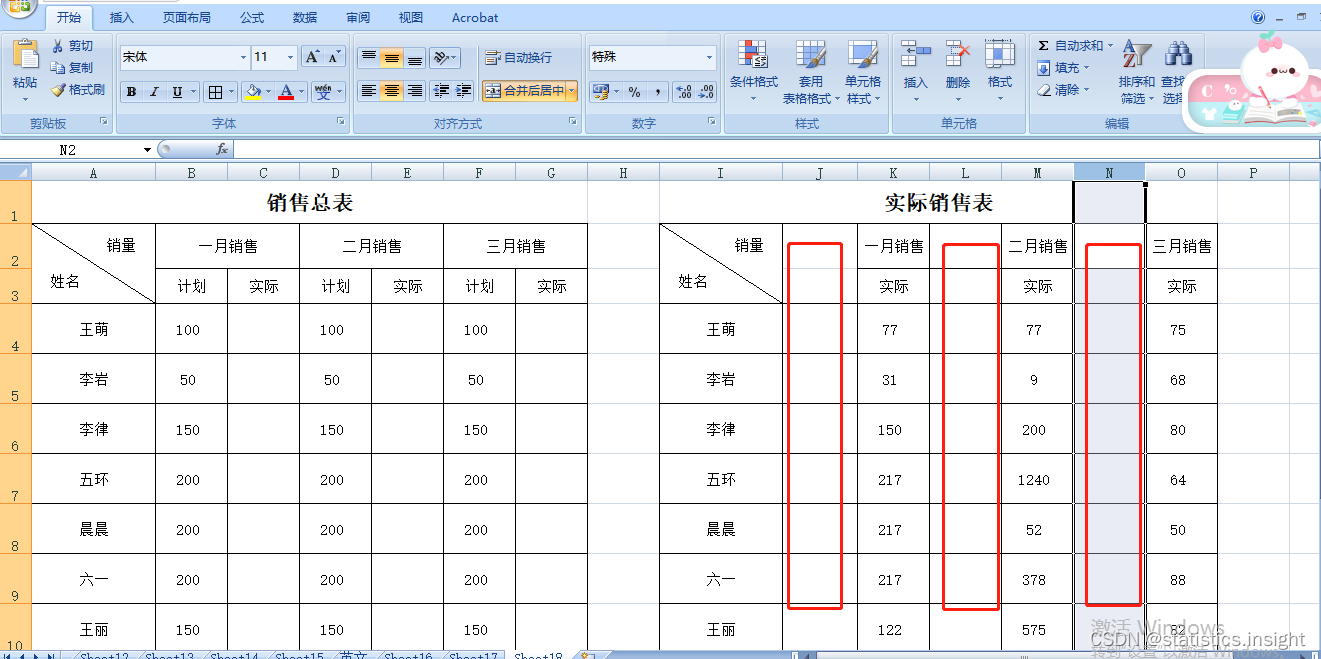
Excel如何进行隔行复制粘贴

Transformation of thinking consciousness is the key to the success or failure of digital transformation of construction enterprises

Troubleshooting: kubectl reports an error validationerror: unknown field \u00a0

High frequency interview questions
随机推荐
Tutoriel (5.0) 10. Dépannage * fortiedr * fortinet Network Security expert NSE 5
二进制操作
[test development] software testing - concept
R language dplyr package Na_ The if function converts the control in the vector value into the missing value Na, and converts the specified content into the missing value Na according to the mapping r
Introduction to sap s/4hana OData mock service
学习八股文的知识点~~1
Mini Golf Course: a good place for leisure and tourism in London
迷你高尔夫球场:伦敦休闲旅游好去处
数据降维——主成分分析
ORA-01455: converting column overflows integer datatype
R语言使用epiDisplay包的cox.display函数获取cox回归模型汇总统计信息(风险率HR、调整风险率及其置信区间、模型系数的t检验的p值、Wald检验的p值和似然比检验的p值)、汇总统计
论文导读 | 关于将预训练语言模型作为知识库的分析与批评
How to enable the run dashboard function of idea
Talk about the design of red envelope activities in e-commerce system
Emmet基础语法
【每日一题】第一天
R language ggplot2 visualization: visualize the line chart and add customized X-axis label information to the line chart using labs function
How to clean up discarded PVs and their corresponding folders
Singapore summer tourism strategy: play Singapore Sentosa Island in one day
Troubleshooting: kubectl reports an error validationerror: unknown field \u00a0