当前位置:网站首页>Cryptographic technology -- key and ssl/tls
Cryptographic technology -- key and ssl/tls
2022-07-02 23:08:00 【yiixiou】
Key definition
The key is a huge number . The key concept in cryptography is the size of the key space . The size of the key space is determined by the length of the key . common DES The key length is 7 byte ,DES-DES2 and DES-DES3 The key lengths are 14 Byte and 21 byte ,AES The key length is 128,192 or 256 The bit .
Here's the thing , The key and plaintext have the same value . If the plaintext is worth millions , Then the key that can crack the plaintext should have the same value .
Various keys
- Symmetric cryptographic key : Encryption and decryption use the same key . Also known as shared key password .
- Public key cryptographic key : Encryption and decryption use different keys . Encrypted is called public key , The decryption is called the private key . Public and private keys are also called key pairs .
- Message authentication code (MAC) The key of : The sender and receiver use the shared key for authentication .MAC It can only be calculated by the person who holds the legal key . take MAC Attached to the communication message , Identify whether the communication content has been tampered with or camouflaged . shortcoming :MAC There is a risk of tampering and camouflage in leakage .
- Key of digital signature : Different keys are used for signature generation and verification . The person who holds the private key generates a signature , The public key is used for authentication .
- session key : A key that can only be used once in communication . Such as : visit https:// The opening page ,Web Between the server and the browser SSL/TLS Encrypted communication , The key used in this communication is limited to this communication , Belongs to session key . advantage : Even if intercepted, it can only decipher the content of this communication , The confidentiality of other communications is not compromised .
- Master key : A key that has been reused .
- The key used to encrypt the content (Contents Encrypting Key, CEK): Content encryption key . Session keys are often used CEK.
- The key used to encrypt the key (Key Encrypting Key, KEK): Key encryption key . The master key often does KEK. somewhat : Reduce the number of keys that need to be declared .
Key management
- Key generation : Random number generation 、 Password generation (Password Based Encryption, PBE).
- Distribution key : Symmetric algorithm key faces the problem of key distribution , Because encryption and decryption use the same key . You can use a shared key in advance , Using a key distribution center , Use public key password, etc .
- Key update : A technology that improves the confidentiality of communications . This technology has backward security ( One way hash function is one-way , It's difficult to calculate backwards ), It can prevent decoding the contents of past communications .
- Key saving : When the key needs to be reused , We need to consider the problem of key preservation . Session keys are not considered .
- Void key .
SSL/TLS Definition
SSL/TLS It's a kind of Web Protocols widely used in servers .SSL The full name is Secure Socket Layer,TLS The full name is Transport Layer Security.
Client and server
Web The browser and Web Server follows HTTP Hypertext transfer protocol to communicate , Web Browsers are also called HTTP client ,Web Servers are also called HTTP The server . We can use SSL/TLS bearing HTTP, Through the superposition of the two protocols , It can be done to HTTP Communication for ( Requests and responses ) To encrypt , To prevent eavesdropping .SSL/TLS The job of
The working process needs to ensure three points :(1) The sending process cannot be bugged ;(2) The sending process cannot be tampered ;(3) Finally, the sender can be confirmed ;1,2,3 The points correspond to the confidentiality of the key 、 integrity 、 Certification issues .SSL and TLS The difference between
TLS yes SSL Subsequent versions , Added AES Symmetric cipher algorithm , Deleted DES, Added for CBC How to attack .
边栏推荐
- Share 10 JS closure interview questions (diagrams), come in and see how many you can answer correctly
- ping域名报错unknown host,nslookup/systemd-resolve可以正常解析,ping公网地址通怎么解决?
- 中国信通院、清华大学、腾讯安全,云原生安全产学研用强强联合!
- 从2022年Q1财报看携程的韧性和远景
- Pytorch training CPU usage continues to grow (Bug)
- Splunk audit setting
- 數據分析學習記錄--用EXCEL完成簡單的單因素方差分析
- [Solved] Splunk: Cannot get username when all users are selected“
- `Usage of ${}`
- Editor Caton
猜你喜欢

The first batch of Tencent cloud completed the first cloud native security maturity assessment in China

首批 | 腾讯云完成国内首个云原生安全成熟度评估
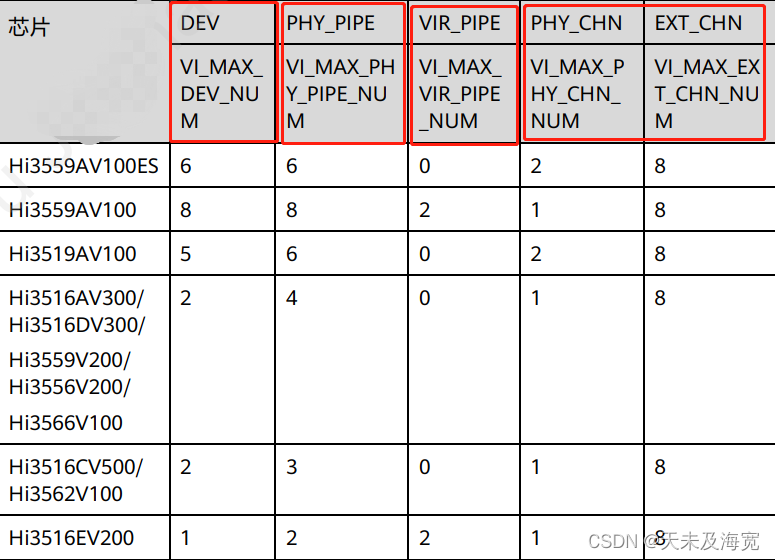
海思 VI接入视频流程
![Jielizhi, production line assembly link [chapter]](/img/0d/102596ad13aafd9c6133509d9064dd.png)
Jielizhi, production line assembly link [chapter]

Learning records of data analysis (II) -- simple use of response surface method and design expert

Construction of Hisilicon 3559 universal platform: draw a frame on the captured YUV image
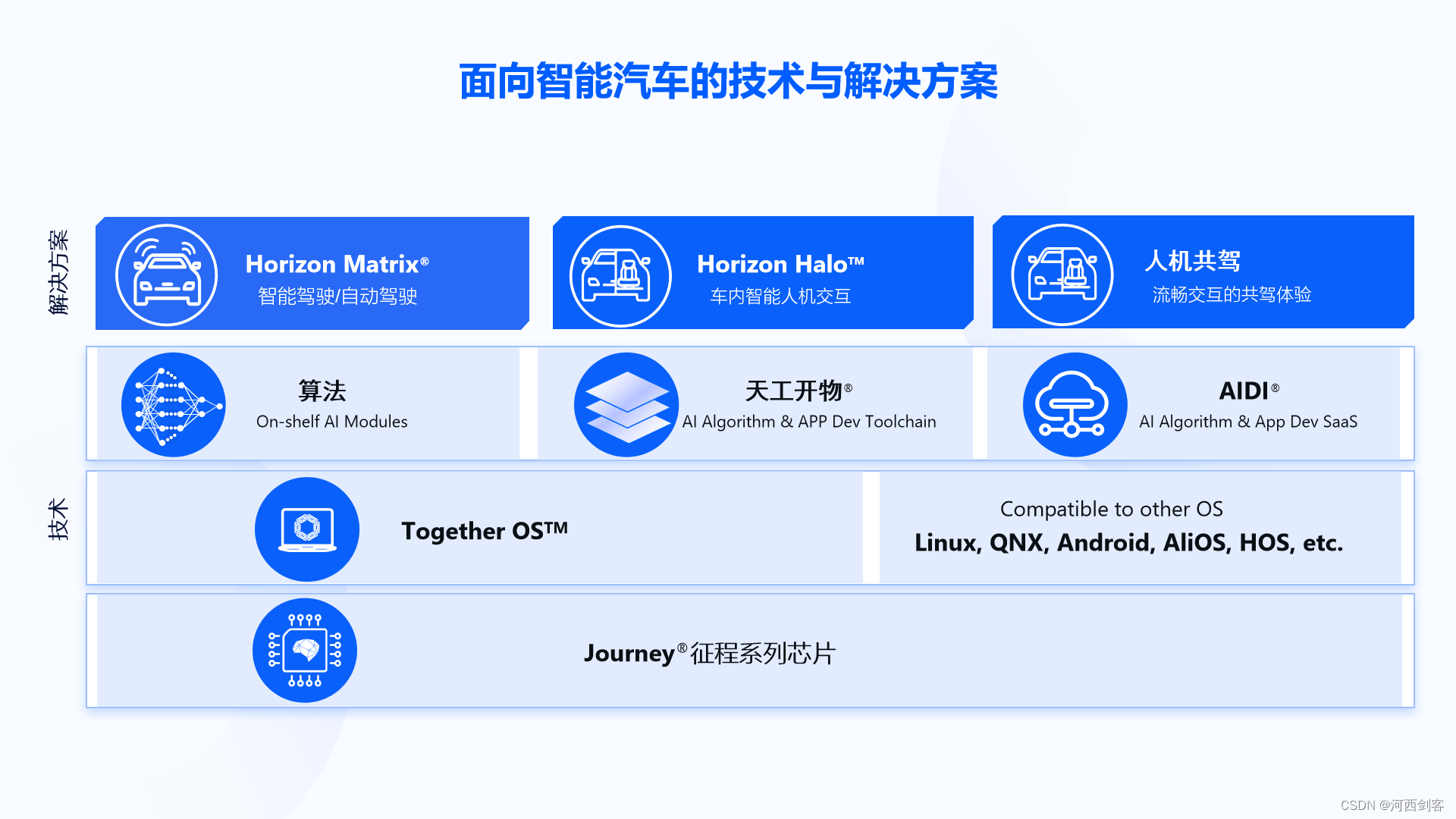
地平线2022年4月最新方案介绍
海思3559万能平台搭建:在截获的YUV图像上旋转操作
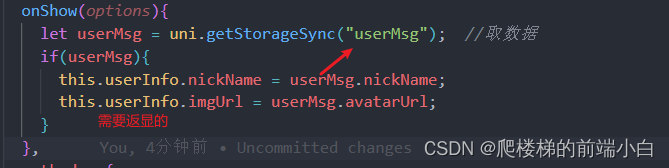
Uniapp wechat login returns user name and Avatar
數據分析學習記錄--用EXCEL完成簡單的單因素方差分析
随机推荐
Tronapi-波场接口-源码无加密-可二开--附接口文档-基于ThinkPHP5封装-作者详细指导-2022年7月1日08:43:06
Share 10 JS closure interview questions (diagrams), come in and see how many you can answer correctly
[chestnut sugar GIS] ArcScene - how to make elevation map with height
STM32之ADC
Jerry's built-in shutdown current is 1.2ua, and then it can't be turned on by long pressing [chapter]
QT qsplitter splitter
电路设计者常用的学习网站
LC173. 二叉搜索树迭代器
【喜欢的诗词】好了歌
Addition, deletion, modification and query of handwritten ORM (object relationship mapping)
Uniapp wechat login returns user name and Avatar
pytorch训练CPU占用持续增长(bug)
移动端 1px 像素兼容性问题,实现1px 边框
Introduction to the latest plan of horizon in April 2022
The kth largest element in the [leetcode] array [215]
Splunk audit 的设定
Construction of Hisilicon 3559 universal platform: draw a frame on the captured YUV image
Strictly abide by the construction period and ensure the quality, this AI data annotation company has done it!
Mask R-CNN
泛型与反射,看这篇就够了