当前位置:网站首页>Safe landing practice of software supply chain under salesforce containerized ISV scenario
Safe landing practice of software supply chain under salesforce containerized ISV scenario
2022-07-07 05:17:00 【InfoQ】
Containerization ISV Security challenges for delivery
- Third party and open source components bring security risks : Enterprise software projects tend to rely more and more on components from the vendor tripartite or open source community , These components are often transferred in the software supply chain in the form of basic images . An attacker may exploit a vulnerability in the component , Inject malicious code or control the third-party machine environment , Perform mining from cryptocurrency 、 spam 、 To launch through a large botnet DDoS attack .
- The long link of software delivery buries more risks : From the demand analysis of software development stage 、 Code development 、 Integrate 、 test , To ISV Channel specific software delivery in the delivery phase 、 End customer acceptance , The end-user software in the final running phase runs 、 Operation and maintenance . The whole software supply chain has a long cycle , There may be safety risks in all links , Lead to software vulnerabilities 、 Software backdoor 、 Malicious tampering 、 Intellectual property risk 、 Information leakage and other security threats .
- Containerized operation introduces more risk attack surfaces : Container application deployment depends on Linux The kernel feature , Many hackers exploit kernel system vulnerabilities , Launch targeted escape or intrusion attacks from multiple dimensions such as container runtime components and container application deployment configuration . Recent years K8s、Docker、Istio And other open source communities have exposed many high-risk vulnerabilities , This provides an opportunity for the attacker .
Alibaba cloud native software supply chain solution
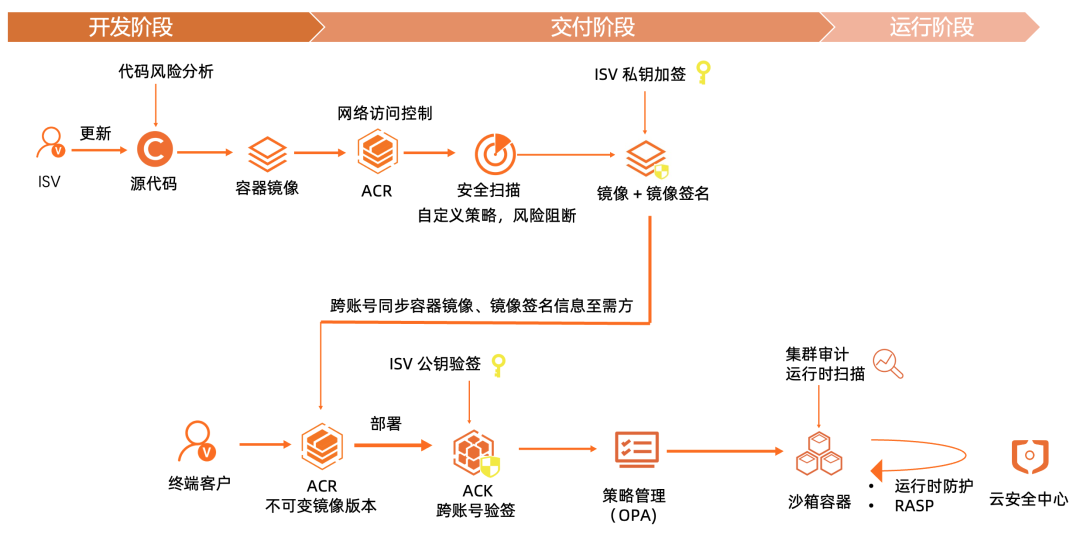
- Image content security ,ACR It provides an enhanced container image scanning engine jointly with the cloud security center , Cover system vulnerabilities 、 Application vulnerability 、 Risk types such as baseline inspection and malicious samples , High recognition rate 、 Low false positive rate vulnerability scanning capability . meanwhile , Provides container image repair capability , Support automated and efficient repair of risk vulnerabilities , Realize the security closed loop from discovery to repair .
- Image cross account delivery , For inter enterprise ISV Application delivery scenarios ,ACR Cross account synchronization capability is provided to ensure the distribution security of container image and signature .ISV Pass the image and the corresponding signature information through ACR Cross account synchronization capability is delivered to ISV Customer instance of . The corresponding image turns on the immutable image version , Ensure that the version of the image cannot be overwritten .ISV Our customers are ACK When deploying images on , Will be based on ISV Public key signature verification , Ensure that the image is complete and from ISV.
- Deploy policy management :ACK be based on OPA Policy engine and rich preset policy templates , Effective constraint application configuration security , Support container business YAML Multi dimensional deployment policy management , Avoid privilege containers 、 Risk image deployment and other risk behaviors , Strengthen the active management capability of container security on the cluster side .
- Safe sandbox container : The end customer uses a secure sandbox container as the runtime , Compared with the original Docker Runtime , Container applications can be run in a lightweight virtual machine sandbox environment , Have a separate kernel , Better security isolation capability , Compared with the community Kata Container More stable .
- Container runtime security : The end customer uses the runtime security monitoring and alarm capabilities of the cloud security center container , Including virus and malicious program attacks in the container or at the host level 、 Intrusions inside containers 、 Main container side attacks such as container escape and high-risk operation warning , Help customers find security threats in assets in a timely manner 、 Grasp the asset security situation in real time .
Alicloud carries Salesforce It has been awarded as an excellent case of software supply chain security of ICT Academy

Improve the security of the whole link
- Safe delivery : adopt ACR Cross user synchronization links ensure the distribution security of images and signatures . adopt ACR Image tagging and ACK Cross account verification ensures that the contents of the image are trusted . And because the whole delivery process is based on the exclusive synchronization link , It can ensure that the information transferred in the software supply chain will not be accidentally disclosed .
- The security policy : Turn on ACR Mirror security scan policy , Ensure the content security of the image while blocking the delivery of the risk image . The implementation of ACK OPA Deploy policy management , Ensure that the container application configuration is effectively constrained to block the operation of similar privileged containers .
- Safe operation : be based on ACK Safe sandbox container running container , The application runs in a lightweight virtual machine sandbox environment , Have a separate kernel , Better security isolation capability . Based on the cloud security center container runtime security monitoring and alarm capabilities , Avoid malicious attacks at the container or host level , Early warning of high-risk operations .
Improve the efficiency of safety management
- Highly automated : adopt ACR Automatic synchronization 、 Automatic scanning 、 Automatic endorsement ,ACK Automatic signature verification 、 Automatic policy enforcement , And automatically block the follow-up process function after risk identification , Realize containerization DevSecOps The process of .
Alibaba cloud container service escorts the upgrading of the original biochemical architecture of the enterprise cloud

边栏推荐
猜你喜欢

Liste des hôtes d'inventaire dans ansible (je vous souhaite des fleurs et de la romance sans fin)
如何设计 API 接口,实现统一格式返回?
QT simple layout box model with spring
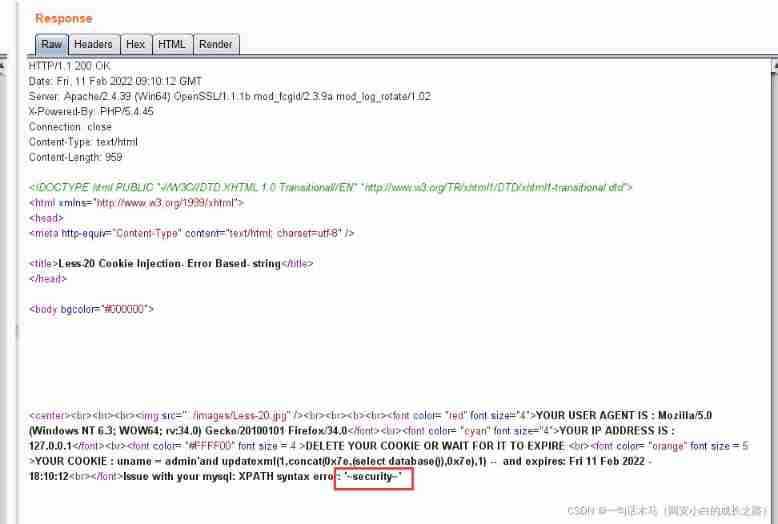
SQL injection cookie injection
Sublime tips

How to design API interface and realize unified format return?
Is it necessary to renew the PMP certificate?
Auto. JS get all app names of mobile phones

The sooner you understand the four rules of life, the more blessed you will be
Operand of null-aware operation ‘!‘ has type ‘SchedulerBinding‘ which excludes null.
随机推荐
pytest测试框架——数据驱动
How does redis implement multiple zones?
Two methods of thread synchronization
Analysis -- MySQL statement execution process & MySQL architecture
Longest common subsequence (LCS) (dynamic programming, recursive)
NPDP产品经理认证,到底是何方神圣?
想要选择一些部门优先使用 OKR, 应该如何选择试点部门?
带你遨游银河系的 10 种分布式数据库
U++4 接口 学习笔记
What changes will PMP certification bring?
Creation and use of thread pool
Leetcode longest public prefix
10 distributed databases that take you to the galaxy
与利润无关的背包问题(深度优先搜索)
全链路压测:影子库与影子表之争
批量归一化(标准化)处理
torch optimizer小解析
Why JSON is used for calls between interfaces, how fastjson is assigned, fastjson 1.2 [email protected] Mapping relatio
Development thoughts of adding new requirements in secondary development
Weebly mobile website editor mobile browsing New Era