当前位置:网站首页>kubeadm系列-01-preflight究竟有多少check
kubeadm系列-01-preflight究竟有多少check
2022-07-05 05:23:00 【runzhliu】
我们知道 kubeadm init 的过程中会进行很多 preflight 的检查,这些主要是指内核参数、模块、CRI 等环境的检查,如果有哪些配置不符合 Kubernetes 的要求,就会抛出 Warning 或者 Error 的信息,下面就是 preflight 的主要逻辑
// Checker validates the state of the system to ensure kubeadm will be
// successful as often as possible.
type Checker interface {
Check() (warnings, errorList []error)
Name() string
}
如果有 diy 的 check 需求,可以在代码里继承这个接口进行扩展,下面举个 check 的例子,很明显 ContainerRuntimeCheck 是对 CRI 也就是容器运行时进行的检查
// ContainerRuntimeCheck verifies the container runtime.
type ContainerRuntimeCheck struct {
runtime utilruntime.ContainerRuntime
}
// Name returns label for RuntimeCheck.
func (ContainerRuntimeCheck) Name() string {
return "CRI"
}
// Check validates the container runtime
func (crc ContainerRuntimeCheck) Check() (warnings, errorList []error) {
klog.V(1).Infoln("validating the container runtime")
if err := crc.runtime.IsRunning(); err != nil {
errorList = append(errorList, err)
}
return warnings, errorList
}
而真正起到检查的作用是下面这个函数,其实就是宿主机执行一下 crictl info,并且接收其返回,老铁们不妨在宿主机上直接运行一下看看结果
// IsRunning checks if runtime is running
func (runtime *CRIRuntime) IsRunning() error {
if out, err := runtime.crictl("info").CombinedOutput(); err != nil {
return errors.Wrapf(err, "container runtime is not running: output: %s, error", string(out))
}
return nil
}
所有的 Check 里面是会有小部分交错的部分,比如说检查防火墙的问题,先会对 Firewall 这个服务做 service check,然后才会对具体的端口进行检查
下面是所有 check 的统计
- CRI: 检查容器运行时是否有在运行
- Service: 检查是否enable和active
- Firewall: 检查防火墙是否有关闭
- Port: 检查某些端口是否有放开
- Privileged: 检查一些权限的问题
- Dir Available: 检查目录是否有效
- File Available: 检查文件是否有效
- File Existing: 检查文件是否存在
- File Content: 检查文件中是否有指定的内容
- In Path: 检查某些可执行文件是否在指定的目录
- Hostname: 检查主机名的格式
- HTTP Proxy: 检查本机是否有Proxy设置
- HTTP Proxy CIDR: 检查本机有哪些地址会走Proxy
- System Verification: 检查系统版本
- Kubernetes Version: 检查Kubernetes的版本
- Kubelet Version: 检查Kubelet的版本
- SwapCheck: 检查Swap是否关闭
- External Etcd Version: 检查外部etcd的版本
- Image Pull: 检查镜像仓库是否连通
- Num CPU: 检查本机CPU数量是否符合kubeadm的最低要求
- Mem: 检查本机内存是否符合kubeadm的最低要求
真正在做检查的时候,还会区分是 controlplane 还是普通的 worker 节点,不同角色具体要做的检查是不尽相同的
我们看一下 In Path 这个检查,也就是检查一些必要的二进制文件或者命令是否已经安装,另外还要看 mandatory 如果是 true 的话,那就是必须要符合的,否则就是可有可无,不过如果没有就会提示出来,会建议用户去安装的
InPathCheck{
executable: "crictl", mandatory: true, exec: execer},
InPathCheck{
executable: "conntrack", mandatory: true, exec: execer},
InPathCheck{
executable: "ip", mandatory: true, exec: execer},
InPathCheck{
executable: "iptables", mandatory: true, exec: execer},
InPathCheck{
executable: "mount", mandatory: true, exec: execer},
InPathCheck{
executable: "nsenter", mandatory: true, exec: execer},
InPathCheck{
executable: "ebtables", mandatory: false, exec: execer},
InPathCheck{
executable: "ethtool", mandatory: false, exec: execer},
InPathCheck{
executable: "socat", mandatory: false, exec: execer},
InPathCheck{
executable: "tc", mandatory: false, exec: execer},
InPathCheck{
executable: "touch", mandatory: false, exec: execer})
最后我们看一下 System Verification,主要是针对主机的系统来进行一些模块的检测,我们主要看一下 Linux 下的检查,内核很多模块有以及没有,还是有较大的差别的,所以不要轻视这部分的检查,以为主要是 Linux 系统就没啥问题了,有时候恰恰是这部分的内容更难排查
// DefaultSysSpec is the default SysSpec for Linux
var DefaultSysSpec = SysSpec{
OS: "Linux",
KernelSpec: KernelSpec{
Versions: []string{
`^3\.[1-9][0-9].*$`, `^([4-9]|[1-9][0-9]+)\.([0-9]+)\.([0-9]+).*$`}, // Requires 3.10+, or newer
// TODO(random-liu): Add more config
// TODO(random-liu): Add description for each kernel configuration:
Required: []KernelConfig{
{
Name: "NAMESPACES"},
{
Name: "NET_NS"},
{
Name: "PID_NS"},
{
Name: "IPC_NS"},
{
Name: "UTS_NS"},
{
Name: "CGROUPS"},
{
Name: "CGROUP_CPUACCT"},
{
Name: "CGROUP_DEVICE"},
{
Name: "CGROUP_FREEZER"},
{
Name: "CGROUP_PIDS"},
{
Name: "CGROUP_SCHED"},
{
Name: "CPUSETS"},
{
Name: "MEMCG"},
{
Name: "INET"},
{
Name: "EXT4_FS"},
{
Name: "PROC_FS"},
{
Name: "NETFILTER_XT_TARGET_REDIRECT", Aliases: []string{
"IP_NF_TARGET_REDIRECT"}},
{
Name: "NETFILTER_XT_MATCH_COMMENT"},
{
Name: "FAIR_GROUP_SCHED"},
},
Optional: []KernelConfig{
{
Name: "OVERLAY_FS", Aliases: []string{
"OVERLAYFS_FS"}, Description: "Required for overlayfs."},
{
Name: "AUFS_FS", Description: "Required for aufs."},
{
Name: "BLK_DEV_DM", Description: "Required for devicemapper."},
{
Name: "CFS_BANDWIDTH", Description: "Required for CPU quota."},
{
Name: "CGROUP_HUGETLB", Description: "Required for hugetlb cgroup."},
{
Name: "SECCOMP", Description: "Required for seccomp."},
{
Name: "SECCOMP_FILTER", Description: "Required for seccomp mode 2."},
},
Forbidden: []KernelConfig{
},
},
Cgroups: []string{
"cpu", "cpuacct", "cpuset", "devices", "freezer", "memory", "pids"},
CgroupsOptional: []string{
// The hugetlb cgroup is optional since some kernels are compiled without support for huge pages
// and therefore lacks corresponding hugetlb cgroup
"hugetlb",
// The blkio cgroup is optional since some kernels are compiled without support for block I/O throttling.
// Containerd and cri-o will use blkio to track disk I/O and throttling in both cgroup v1 and v2.
"blkio",
},
CgroupsV2: []string{
"cpu", "cpuset", "devices", "freezer", "memory", "pids"},
CgroupsV2Optional: []string{
"hugetlb", "blkio"},
RuntimeSpec: RuntimeSpec{
DockerSpec: &DockerSpec{
Version: []string{
`1\.1[1-3]\..*`, `17\.0[3,6,9]\..*`, `18\.0[6,9]\..*`, `19\.03\..*`, `20\.10\..*`},
GraphDriver: []string{
"aufs", "btrfs", "overlay", "overlay2", "devicemapper", "zfs"},
},
},
}
边栏推荐
猜你喜欢
Stm32cubemx (8): RTC and RTC wake-up interrupt
C语言杂谈1
质量体系建设之路的分分合合
Simple modal box
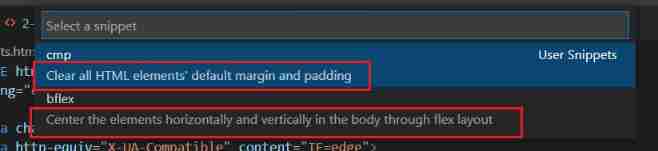
Use of snippets in vscode (code template)

Gbase database helps the development of digital finance in the Bay Area
![[to be continued] [UE4 notes] L1 create and configure items](/img/20/54ba719be2e51b7db5b7645b361e26.jpg)
[to be continued] [UE4 notes] L1 create and configure items
JVM call not used once in ten years
Quick sort summary
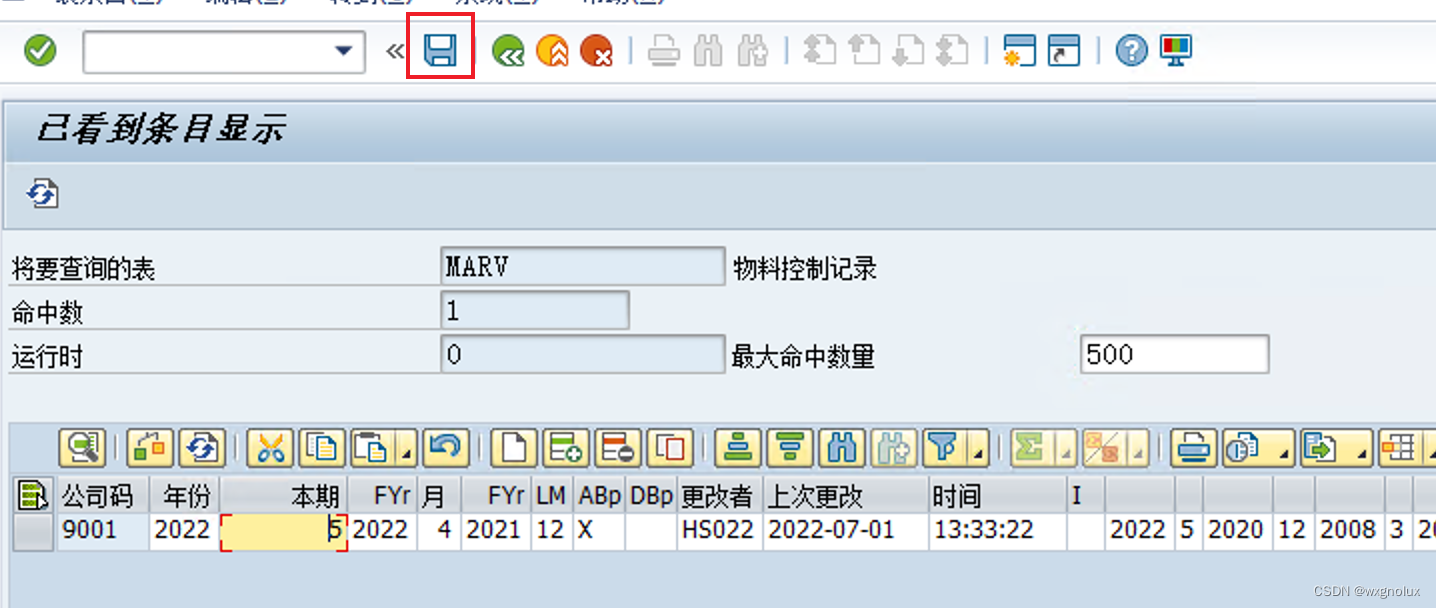
SAP-修改系统表数据的方法
随机推荐
Use of room database
Improvement of pointnet++
Service fusing hystrix
PMP考生,请查收7月PMP考试注意事项
[转]:Apache Felix Framework配置属性
Applet live + e-commerce, if you want to be a new retail e-commerce, use it!
Haut OJ 1347: addition of choice -- high progress addition
Pointnet++学习
A new micro ORM open source framework
Applet Live + e - commerce, si vous voulez être un nouveau e - commerce de détail, utilisez - le!
Haut OJ 2021 freshmen week II reflection summary
嵌入式数据库开发编程(零)
2022年上半年国家教师资格证考试
How can the Solon framework easily obtain the response time of each request?
支持多模多态 GBase 8c数据库持续创新重磅升级
C language Essay 1
小程序直播+電商,想做新零售電商就用它吧!
[es practice] use the native realm security mode on es
[to be continued] [UE4 notes] L3 import resources and project migration
Fragment addition failed error lookup