当前位置:网站首页>Summary of interview questions (2) IO model, set, NiO principle, cache penetration, breakdown avalanche
Summary of interview questions (2) IO model, set, NiO principle, cache penetration, breakdown avalanche
2022-07-03 11:12:00 【It's xiaoqingqing】
1. several IO Model ,
Blocking IO、 Non blocking IO、 Multiplexing IO、 Signal driven IO, asynchronous IO ( In my previous article, I explained in detail IO Several models of Blocking , Non blocking ,io Multiplexing , Signal driven and asynchronous io_ It's xiaoqingqing's blog -CSDN Blog
2.Java Collection classes
Java The set classes in are divided into 4 Categories: , By 4 Interfaces to represent ,
They are Set、List、Queue、Map. among ,Set、List、Queue、 Inherit from Collection Interface .
Set Stands for disordered 、 A collection of elements that are not repeatable .
List Stands for orderly 、 A collection of elements that can be repeated .
Queue First in first out (FIFO) Queues .
Map Represents a mapping relationship (key-value) Set .
Java Provides many collection implementation classes , They are all direct or indirect implementation classes of these interfaces , One of the more common ones is :HashSet、TreeSet、ArrayList、LinkedList、ArrayDeque、HashMap、TreeMap etc. .
The interface or implementation of the collection class mentioned above , All in java.util It's a bag , Most of these implementations are non thread safe . Although not thread safe , But the performance of these classes is better . If you need to use thread safe collection classes , You can use Collections Tool class , This tool class provides synchronizedXxx() Method , You can wrap these collection classes into thread safe collection classes .
java.util In the collection class under the package , There are also a few thread safe collection classes , for example Vector、Hashtable, They are very old API. Although they are thread safe , But the performance is very poor , It's not recommended anymore .

3.NIO Implementation principle of
(Buffer、Channel、Selector)
NIO Is based on IO Implementation of multiplexing model , It contains three core components , Namely Buffer、Channel、Selector.
1. NIO yes Facing the buffer Of , stay NIO All data in the is processed through a buffer .Buffer Is the buffer object , Whether reading or writing , Data is entered first Buffer Of .Buffer The essence of is an array , Usually it's an array of bytes , It can also be other types of arrays .Buffer It's an interface , Its implementation classes are ByteBuffer、CharBuffer、ShortBuffer、IntBuffer、LongBuffer、FloatBuffer、DoubleBuffer.
2. Channel It's a passage , It can be used to read and write data . Unlike flow , The flow is unidirectional , and Channel yes two-way Of . Data can be obtained by Channel Read Buffer in , It can also be done through Channel Write to Buffer in . To support different devices ,Channel Interfaces have several subclasses , Such as FileChannel Used to access disk files 、SocketChannel and ServerSocketChannel be used for TCP Protocol network communication 、DatagramChannel be used for UDP Protocol network communication .
3. Selector It's a multiplexer , It can monitor Listening to the Internet IO The state of . It can continuously poll registered Channel, If a Channel There is a connection on 、 Read 、 The write event occurred , Then this Channel It 's ready , Will be Selector Poll it out . All polled Channel aggregate , We can go through SelectionKey Get , And then we do the following IO operation .
4. Cache penetration 、 Cache breakdown 、 What's the difference between cache avalanches , How to solve ?
Cache penetration : The client queries data that doesn't exist at all , Make the request go directly to the storage layer , The load is too large , Even down . The reason for this , It may be that the business layer mistakenly deleted the data in the cache and Library , It could also be a malicious attack , Special access to data that does not exist in the library .
Solution :
1. Caching empty objects : After a storage layer miss , Still store null values in the cache layer , When the client accesses the data again , The cache layer directly returns a null value .
2. The bloon filter : Store the data in the bloon filter , Block with filter before accessing cache , If the data does not exist, it directly returns a null value .
Cache breakdown : A hot data , It's very visited . At the moment of its cache failure , A large number of requests go directly to the storage layer , Cause the service to crash .
· Solution :
1. Never expire : No expiration time is set for hotspot data , So there won't be any of these problems , This is a “ Physics ” The on the never expires . Or set a logical expiration time for each data , When the data logic is found to be out of date , Use a separate thread to rebuild the cache .
2. Add mutex lock : Add mutex to data access , When a thread accesses the data , Other threads can only wait . After this thread access , The data in the cache will be rebuilt , At that time, other threads can take values directly from the cache .
Cache avalanche : At some point , The cache layer cannot continue to provide services , Cause all requests to go directly to the storage tier , Cause database downtime . It may be that a large amount of data in the cache expires at the same time , May be Redis Node failure , Resulting in a large number of requests that cannot be processed .
· Solution :
1. Avoid data expiration at the same time : When setting expiration time , Add a random number , Avoid a lot of key At the same time .
2. Enable degradation and fusing measures : In the event of an avalanche , If the application is not accessing the core data , The predefined information is returned directly / Null value / error message . Or in the event of an avalanche , For requests to access the cache interface , The client does not send the request to Redis, I'm going straight back .
3. Build highly available Redis service : Use sentinel or cluster mode , Deploy multiple Redis example , Individual nodes are down , It can still keep the whole service available .
边栏推荐
- 【蓝桥杯选拔赛真题44】Scratch消灭骷髅军团 少儿编程scratch蓝桥杯选拔赛真题讲解
- 2022 pinduogai 100000 sales tutorial
- 如何让让别人畏惧你
- Matlab memory variable management command
- Qt:qss custom QSlider instance
- 8年测试工程师总结出来的《测试核心价值》与《0基础转行软件测试超全学习指南》
- ORACLE 11G 单机冷备数据库
- 在职美团测试工程师的这八年,我是如何成长的,愿技术人看完都有收获
- Summary of the history of Mathematics
- First line of code kotlin notes
猜你喜欢

硬 货 | 一改测试步骤代码就全写?为什么不试试用 Yaml实现数据驱动?

Software testing redis database

I, a tester from a large factory, went to a state-owned enterprise with a 50% pay cut. I regret it
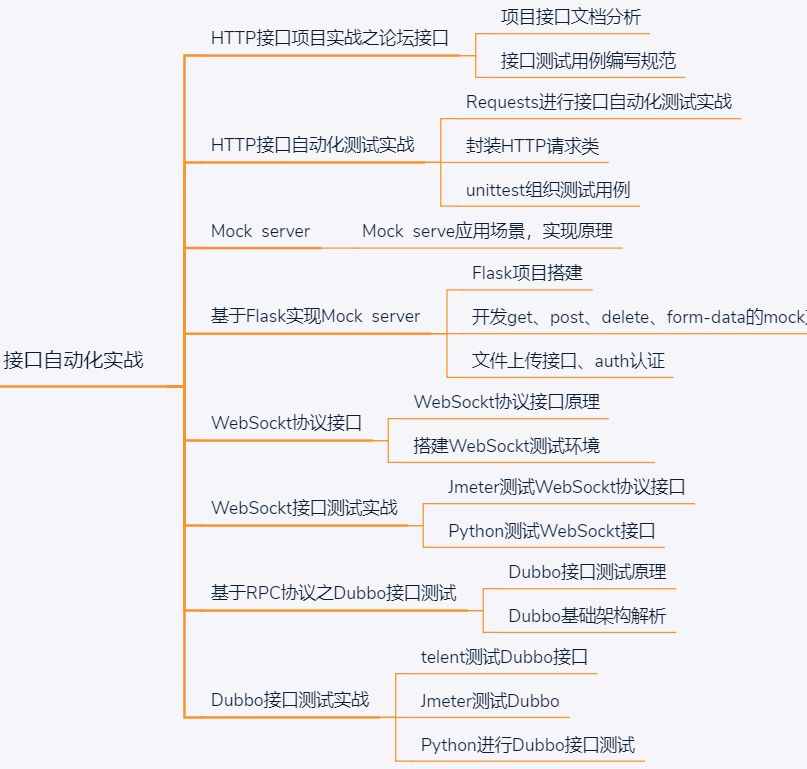
我对测试工作的一些认识(资深测试人员总结)
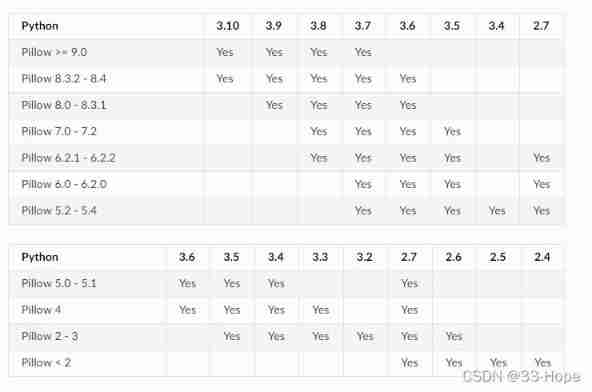
Error installing the specified version of pilot

17K薪资要什么水平?来看看95后测试工程师的面试全过程…

【蓝桥杯选拔赛真题44】Scratch消灭骷髅军团 少儿编程scratch蓝桥杯选拔赛真题讲解

11. Provider service registration of Nacos service registration source code analysis

How did I grow up in the past eight years as a test engineer of meituan? I hope technicians can gain something after reading it

Do you really need automated testing?
随机推荐
公司测试部门来了个00后卷王之王,老油条感叹真干不过,但是...
Lecture 1 number field
我,大厂测试员,降薪50%去国企,后悔了...
【蓝桥杯选拔赛真题44】Scratch消灭骷髅军团 少儿编程scratch蓝桥杯选拔赛真题讲解
如何让让别人畏惧你
The solution that prompts "system group policy prohibits the installation of this device" under win10 system (home version has no group policy)
. Net core - a queuing system for wechat official account
one hot 独热码
QT: QSS custom qtoolbutton instance
独家分析 | 关于简历和面试的真 相
Imread change image display size
I, a tester from a large factory, went to a state-owned enterprise with a 50% pay cut. I regret it
Multiple IO transfer - preamble
搭建ADG后,实例2无法启动 ORA-29760: instance_number parameter not specified
ExecutorException: Statement returned more than one row, where no more than one was expected.
Latest sales volume of pinduoduo
UI自动化测试如何走出困境?价值又如何体现?
The element form shows the relationship between elementary transformation and elementary matrix
glassfish org. h2.server. Shutdownhandler classnotfoundexception exception exception handling
月薪过万的测试员,是一种什么样的生活状态?