当前位置:网站首页>What are cache penetration, cache breakdown, and cache avalanche
What are cache penetration, cache breakdown, and cache avalanche
2022-07-04 17:26:00 【51CTO】
Stored in cache ⼤ Most of them are hot data ,⽬ The key is to prevent ⽌ Requests can get data directly from the cache ,⽽ No ⽤ visit Mysql.
- Cache avalanche : If something in the cache ⼀ moment ⼤ Batch hotspot data expires at the same time , That could lead to ⼤ Volume request direct access Mysql 了 , The solution is to increase the expiration time ⼀ Point random value , In addition, if you build ⼀ individual ⾼ can ⽤ Of Redis Clustering is also anti ⽌ slow Save avalanche effectively ⼿ paragraph
- Cache breakdown : Similar to cache avalanche , Cache avalanche is ⼤ Batch hotspot data is invalid ,⽽ Cache breakdown is Refer to ⼀ Hot spots key Sudden failure , It also led to ⼤ Volume request direct access Mysql database , This is cache breakdown , solve ⽅ The case is to consider this hot spot key No Set the expiration time
- Cache penetration : If ⼀ Always visit redis Of ⼤ The amount key All in redis Does not exist in the ( For example, hackers deliberately forge ⼀ Something messy key), It will also put pressure on the data ⼒, This is cache penetration , solve ⽅ Case is to make ⽤ The bloon filter , Its work ⽤ Namely If it thinks ⼀ individual key non-existent , So this key There is no certainty that there is , So you can add ⼀ Layer bron filter comes Intercept what doesn't exist key
边栏推荐
- Visual studio 2019 (localdb) mssqllocaldb SQL Server 2014 database version is 852 and cannot be opened. This server supports 782
- 新享科技发布小程序UniPro小优 满足客户移动办公场景
- Is it safe for Bank of China Securities to open an account online?
- Which domestic cloud management platform manufacturer is good in 2022? Why?
- How to implement a delay queue?
- 周大福践行「百周年承诺」,真诚服务推动绿色环保
- Cypher task design and task locking mechanism of isomorphic and heterogeneous graphs
- Display opencv drawn pictures on MFC picture control control
- DataKit——真正的统一可观测性 Agent
- KS007基于JSP实现人个人博客系统
猜你喜欢
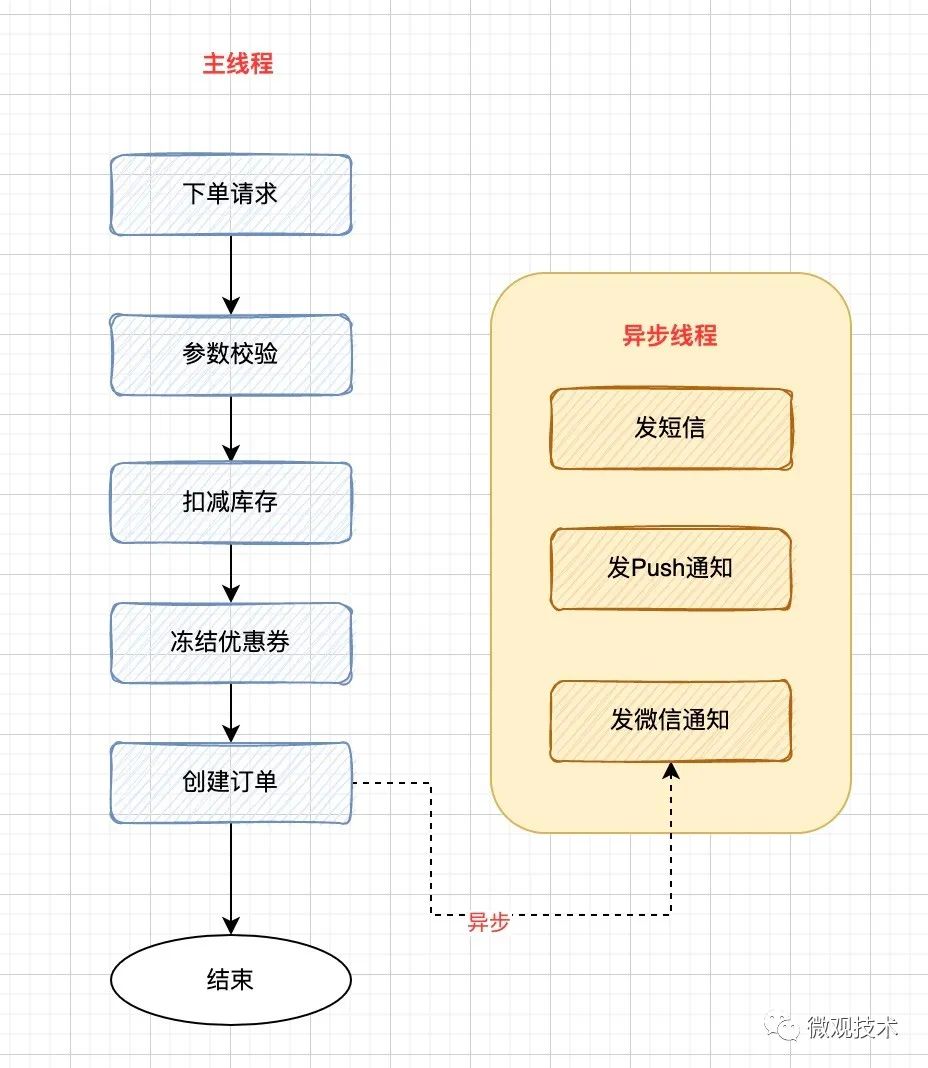
聊聊异步编程的 7 种实现方式

How to choose one plus 10 pro and iPhone 13?
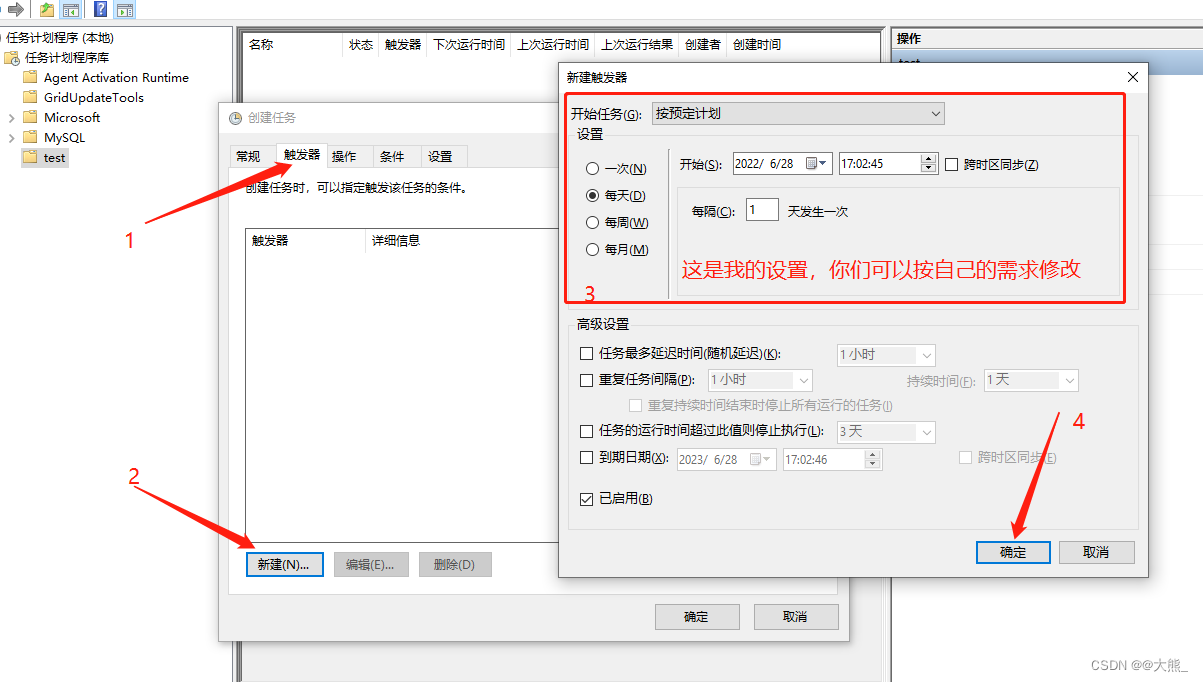
利用win10计划任务程序定时自动运行jar包
Blood spitting finishing nanny level series tutorial - play Fiddler bag grabbing tutorial (2) - first meet fiddler, let you have a rational understanding
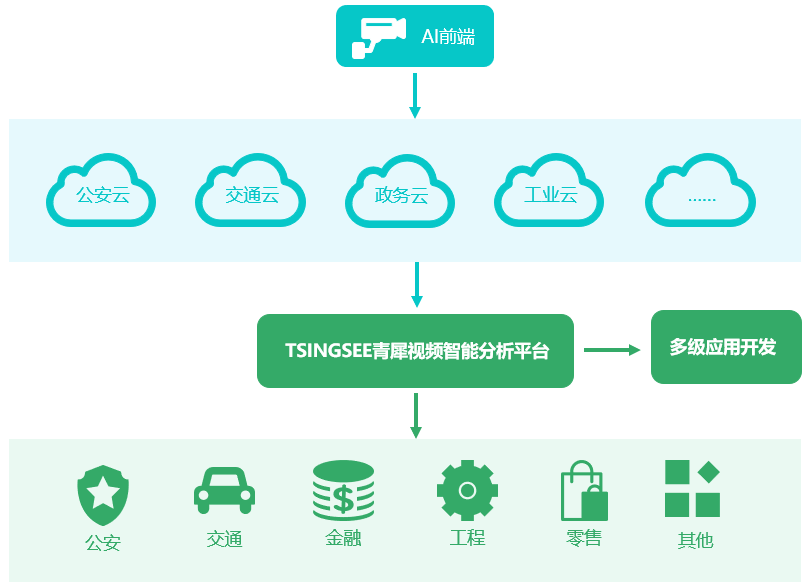
Go development: how to use go singleton mode to ensure the security of high concurrency of streaming media?
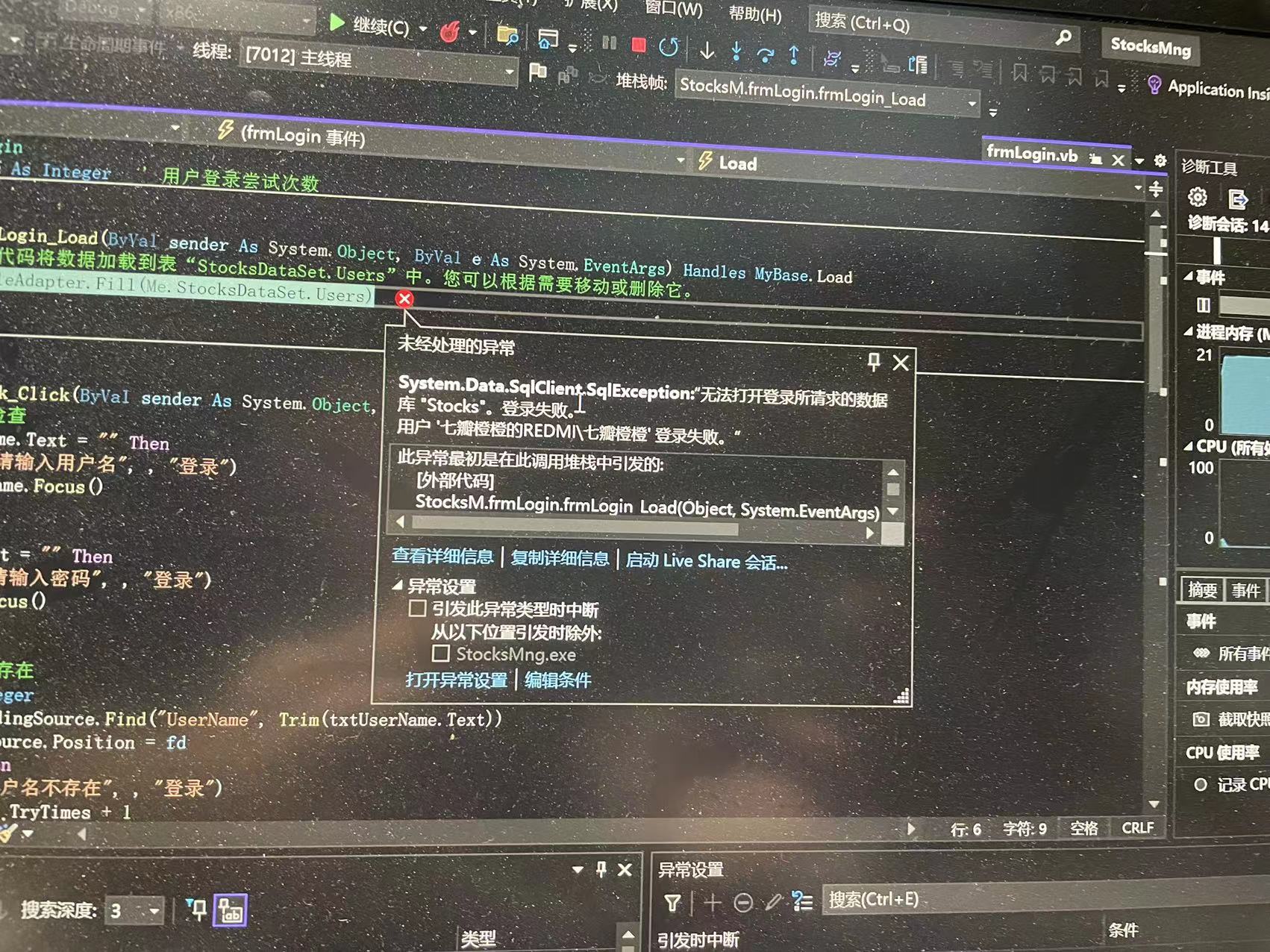
Vb无法访问数据库stocks
Why do you say that the maximum single table of MySQL database is 20million? Based on what?
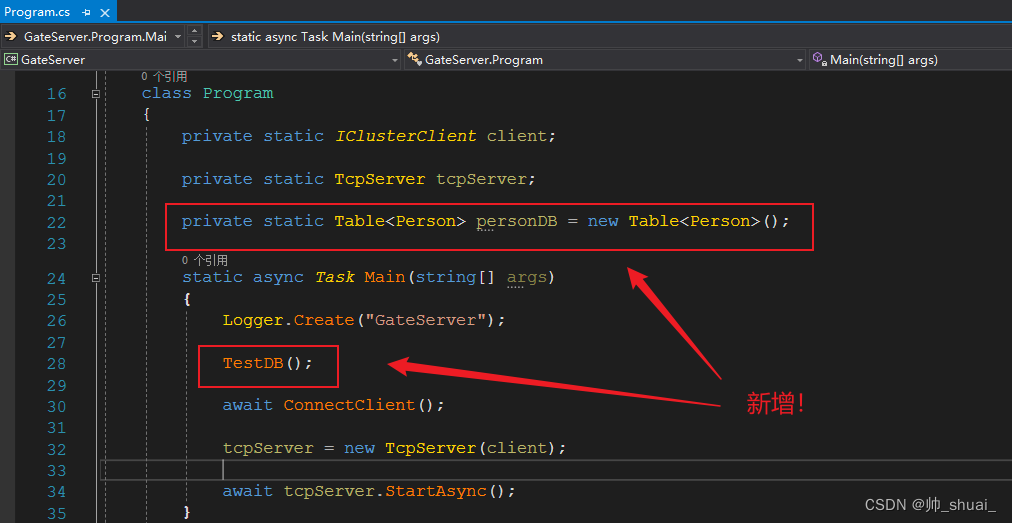
C# 更加优质的操作MongoDB数据库

VB cannot access database stocks

Solution of dealer collaboration system in building materials industry: empowering enterprises to build core competitiveness
随机推荐
电子元器件B2B商城系统开发:赋能企业构建进销存标准化流程实例
Ble HCI flow control mechanism
PingCode 性能测试之负载测试实践
Understand ThreadLocal in one picture
Can you really use MySQL explain?
OPPO小布推出预训练大模型OBERT,晋升KgCLUE榜首
太方便了,钉钉上就可完成代码发布审批啦!
VSCode修改缩进不成功,一保存就缩进四个空格
周大福践行「百周年承诺」,真诚服务推动绿色环保
缓存穿透、缓存击穿、缓存雪崩分别是什么
Blood spitting finishing nanny level series tutorial - play Fiddler bag grabbing tutorial (2) - first meet fiddler, let you have a rational understanding
Load test practice of pingcode performance test
Go语言循环语句(第10课下)
手里10万元存款买什么理财产品收益最高?
[Acwing] 58周赛 4489. 最长子序列
leetcode:421. 数组中两个数的最大异或值
世界环境日 | 周大福用心服务推动减碳环保
How can programmers improve the speed of code writing?
Two methods of MD5 encryption
建筑建材行业经销商协同系统解决方案:赋能企业构建核心竞争力
