当前位置:网站首页>Security Issues and Prevention in Web3
Security Issues and Prevention in Web3
2022-08-05 11:39:00 【Blockchain Interstellar Society】
Web3 builds a decentralized online world based on blockchain technology and is known for its high security.

However, the blockchain is also a network constructed of code, and there are inevitably some loopholes in it, which makes its security not so absolute.The web2 network we use now also has many security holes, but in reality, most people will not be attacked by hackers etc. when using the Internet.This is because in many cases, attackers spend a lot of energy on attacking users with little "benefits". From this point of view, we should probably thank Web2 for not unlocking the value potential of data.
In Web3, digital content is transformed into digital assets, from which attackers can obtain large amounts of money.From the reports of many blockchain security incidents, we can find that the attacked blockchain often loses millions or tens of millions of dollars in funds, and even hundreds of millions of lost security incidents often occur.In the face of this huge benefit, it is worthwhile for hackers to spend a lot of energy to find loopholes in the blockchain and break it.

One of the great features of Web3 is letting users take charge of their own data and accounts.This also creates some new problems, which is that we need to learn how to manage our own encrypted wallets, private keys, etc.Although Web2 has been criticized by many people for relying on the centralized management method of a certain enterprise or organization to keep data and privacy out of control, it is undeniable that the security protection capabilities of some credible enterprises and authoritative organizations are also very good.High.For example, in the banking system, it is very rare for the user's account to be compromised by hackers, resulting in the loss of funds.
In Web3, users are responsible for the security of their own accounts, and many people lack security awareness, which makes a large number of airdrop scams, phishing and other behaviors also exist in Web3.

As an emerging field, Web3 currently faces many challenges.
Many users and institutions lack effective education and awareness when entering Web3, which makes a huge difference in the technology and security protection adopted in the construction process of Web3.This difference results in many Web3 projects appearing safe to users or project parties, but likely to appear to attackers as an unlocked door.
In addition, with the expansion of the blockchain ecosystem, many attackers destroy the blockchain ecosystem through some lurking malicious nodes.Therefore, securing and managing nodes in the blockchain in a scalable manner has also become a major challenge for the project side.
Some of the technologies used in the blockchain system are very complex, and developers must be able to understand it very clearly, which is also a very noteworthy point for developers.challenge.At the same time, blockchain also requires developers to be able to ensure the correctness of their application design.If these two challenges are not successfully addressed, it is easy for hackers who know it better to find vulnerabilities, and attackers can view the system and program source code at any time.
边栏推荐
- 支持向量机SVM
- 机器学习——逻辑回归
- 巴比特 | 元宇宙每日必读:中国1775万件数字藏品分析报告显示,85%的已发行数藏开通了转赠功能...
- How about Ping An Mengwa Card Insurance?Let parents read a few ways to identify products
- 623. Add a row to a binary tree: Simple binary tree traversal problems
- 时间格式2020-01-13T16:00:00.000Z中的T和Z分别表示什么,如何处理
- Naive bayes
- What do T and Z in the time format 2020-01-13T16:00:00.000Z represent and how to deal with them
- Gray value and thermal imaging understanding
- TiDB 6.0 Placement Rules In SQL Usage Practice
猜你喜欢

Nature:猪死亡1小时后,器官再次运转
没开发人员,接到开发物联网系统的活儿,干不干?
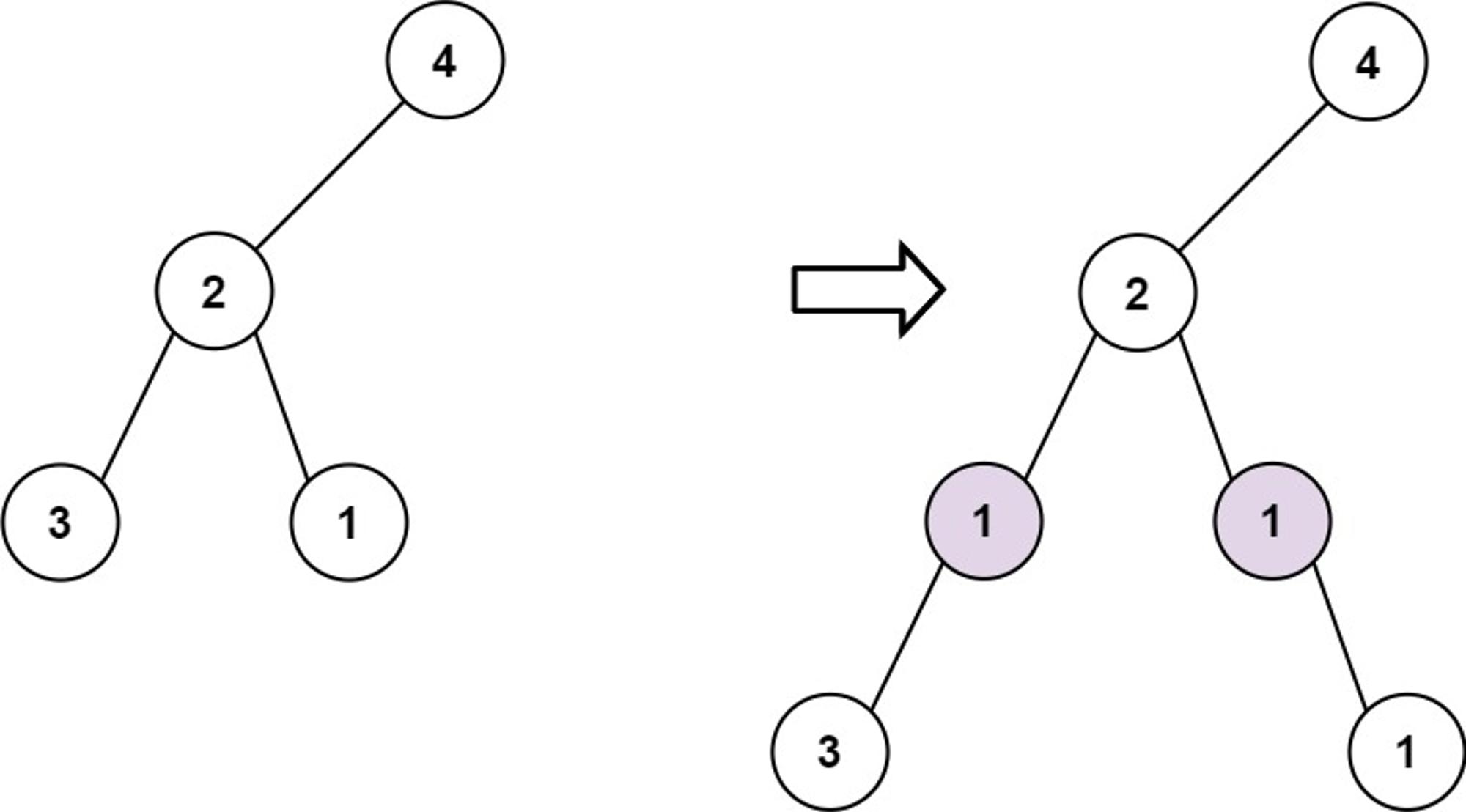
623. Add a row to a binary tree: Simple binary tree traversal problems

Http-Sumggling缓存漏洞分析

2022 CCF国际AIOps挑战赛决赛暨AIOps研讨会报名已开启
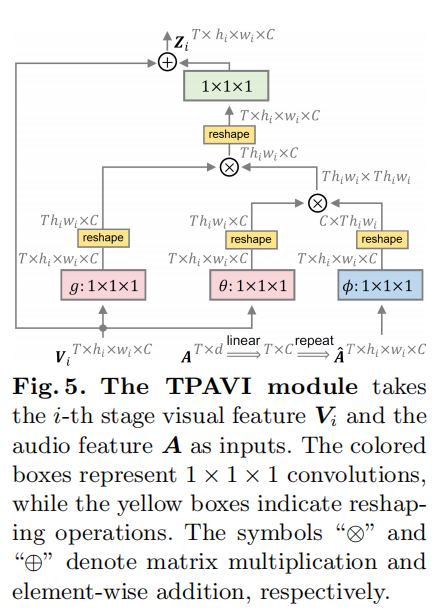
ECCV 2022 | 视听分割:全新任务,助力视听场景像素级精细化理解
普通二本毕业八年,京东就职两年、百度三年,分享大厂心得

数据治理体系演进简介

Flink Yarn Per Job - JobManger 申请 Slot
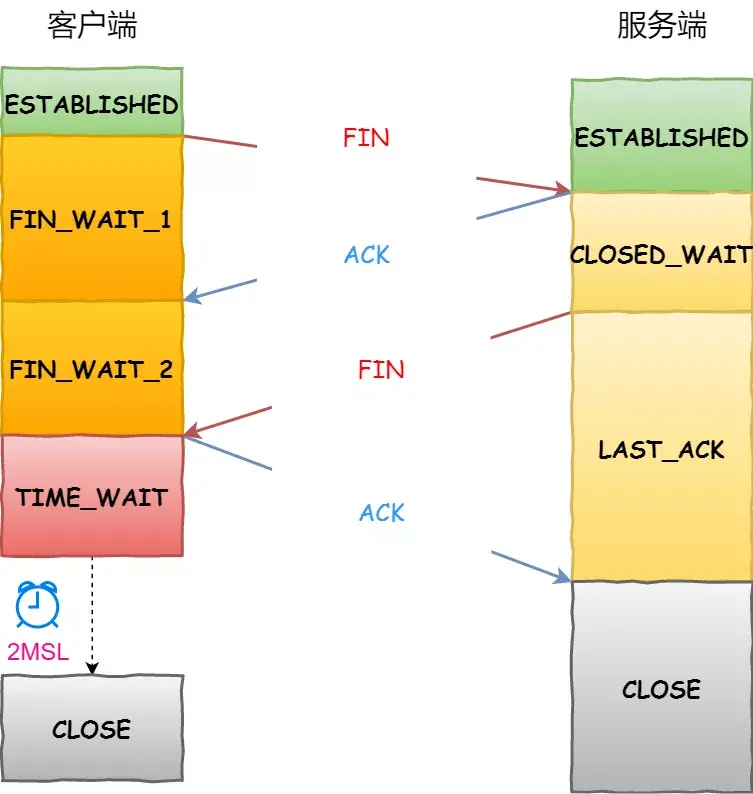
Byte Qiu Zhao confused me on both sides, and asked me under what circumstances would the SYN message be discarded?
随机推荐
How to write a blog with Golang - Milu.blog development summary
Linux:记一次CentOS7安装MySQL8(博客合集)
#yyds干货盘点#【愚公系列】2022年08月 Go教学课程 001-Go语言前提简介
SkiaSharp 之 WPF 自绘 投篮小游戏(案例版)
动手学深度学习_GoogLeNet / Inceptionv1v2v3v4
使用Windbg过程中两个使用细节分享
PPOCR 检测器配置文件参数详解
Integration testing of software testing
Linux: Remember to install MySQL8 on CentOS7 (blog collection)
Machine Learning - Ensemble Learning
hdu4545 Magic String
Go编译原理系列9(函数内联)
Support Vector Machine SVM
5G NR system messages
365 days challenge LeetCode1000 questions - Day 050 add a row to the binary tree binary tree
5G NR 系统消息
JS 从零手写实现一个call、apply方法
互联网行业凛冬之至,BATM的程序员是如何应对中年危机的?
What do T and Z in the time format 2020-01-13T16:00:00.000Z represent and how to deal with them
张朝阳对话俞敏洪:一边是手推物理公式,一边是古诗信手拈来