当前位置:网站首页>Chmod command principle and usage details [easy to understand]
Chmod command principle and usage details [easy to understand]
2022-07-02 17:20:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
Chmod The command is mainly used to modify 、 Set file permissions
chmod There are two main ways to modify file permissions : Alphabet and number
Although the numerical method is simpler than the alphabetic method , But the number method is based on the alphabetic method , So let's introduce the alphabetic method first .
1、 Alphabet :chmod (u g o a) (+ – =) (r w x) ( file name )
Above is chmod Usage of , Each bracket is a parameter , The first three brackets are mainly used together, that is chmod + Set the mode + file name ; Let's first introduce the meaning of these parameters :
[u g o a] | meaning |
|---|---|
u | user Represents the owner of the file |
g | group Indicates that it belongs to the same group as the owner of the file ( group ) person , That is, user groups |
o | other Represents other user groups |
a | all It represents all three-is |
[+ – =] | meaning |
|---|---|
+ | Increase the permissions |
– | Revoke authority |
= | Set permissions |
[r w x] | meaning |
|---|---|
r | read Represents read , For a directory , without r jurisdiction , Then it means not to pass ls Check out the contents of this directory . |
w | write Representation can be written , For a directory , without w jurisdiction , That means you can't create new files in the directory . |
x | excute For executables , For a directory , without x jurisdiction , Then it means not to pass cd Enter this directory . |
usage :chmod + Set the mode + file name Setting mode in the middle , We should treat each other separately u(user), g(group), o(other) Set the permissions .
chmod u+rwx, g+rwx, o+rwx filename Change the command description to filename file , give user、group、other Both read、write、excute Authority Therefore, the setting mode should include permission settings for three user types , They are independent , They don't influence each other .
Illustrate with examples :
chmod u+rw filename State for filname, Give only user user , read、write jurisdiction
chmod u+rwx, g+rw filename Instructions for filename, give user user read、write、excute jurisdiction ; give group user read、write jurisdiction Be careful :(chmod + Set the mode + file name ) The setting mode includes three types of users (u、g、o) Permission settings for , These three are independent , Mutual interference .
2、 Digital method
The number method is based on the letter method , If you understand the alphabet , Digital method is easy to understand , And easy to use .
usage :chmod + Number combination + file name A combination of numbers usually consists of three numbers :
The first number corresponds to the user of the alphabetic method u(user)
The second number corresponds to the user of the alphabetic method g(group)
The third number corresponds to the alphabetic user o(other)
in addition :
r (read) —————-> 4
w (write) —————-> 2
x (excute) —————-> 1
Example details :
Digital method :chmod 777 file name <———– Corresponding ————–> Alphabet : chmod u+rwx, g+rwx, o+rwx file name
The first number 7: On behalf of the user u Authority rwx, 4 (r) + 2 (w) + 1 (x) = 7
The second number 7: On behalf of the user g Authority rwx, 4 (r) + 2 (w) + 1 (x) = 7
The third number 7: On behalf of the user o Authority rwx, 4 (r) + 2 (w) + 1 (x) = 7
Illustrate with examples :
Digital method :chmod 755 filename Corresponding Alphabet : chmod u+rwx, g+rx, o+rx filename
Digital method :chmod 751 filename Corresponding Alphabet : chmod u+rwx, g+rx, o+x filename
Digital method :chmod 765 filename Corresponding Alphabet : chmod u+rwx, g+rw, o+rx filenameAfter the above introduction , Should be for chmod I understand the usage of .
appendix —— chmod Another explanation of the numerical method : The above explanation is based on the method of summation , The following uses binary method to explain, digital method to express : r w x Permissions are represented by three binary digits : First digit (0 or 1) Express r, by 1 Indicates valid , 0 Invalid Second digit (0 or 1) Express w, by 1 Indicates valid ,0 Invalid Third digit (0 or 1) Express x, by 1 Indicates valid , 0 Invalid 000 <———————> No authority 100 <———————> r(read) <—–> 4 010 <———————> w(write) <—–> 2 001 <———————-> x(excute) <—-> 1 101 <———————-> rx <—-> 5 110 <———————-> rw <—-> 6 111 <———————-> rwx <—–> 7
Reference material : http://www.cnblogs.com/loaderman/p/6547609.htmlhttp://blog.csdn.net/leilu2008/article/details/8507037http://blog.chinaunix.net/uid-21880738-id-1813031.htmlhttp://www.cnblogs.com/chengJAVA/p/4319420.htmlhttps://zhidao.baidu.com/question/168415347.html
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/148020.html Link to the original text :https://javaforall.cn
边栏推荐
- Eye of depth (II) -- matrix and its basic operations
- 相信自己,这次一把搞定JVM面试
- Use of openpose
- 配置基于接口的ARP表项限制和端口安全(限制用户私自接入傻瓜交换机或非法主机接入)
- LSF basic command
- 【Leetcode】13. Roman numeral to integer
- Talk about an experience of job hopping and being rejected
- TCP拥塞控制详解 | 2. 背景
- Flutter: 动作反馈
- [essay solicitation activity] Dear developer, RT thread community calls you to contribute
猜你喜欢

ETH数据集下载及相关问题

Eye of depth (III) -- determinant of matrix

上传代码到远程仓库报错error: remote origin already exists.
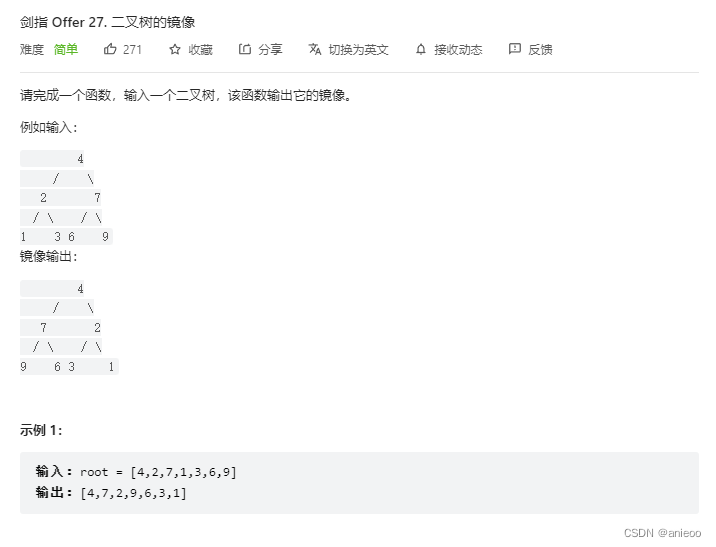
Sword finger offer 27 Image of binary tree
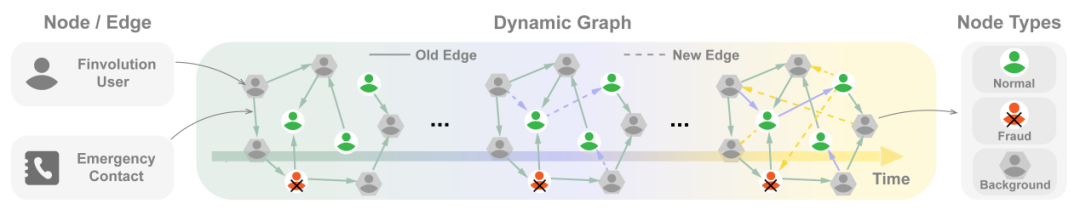
Dgraph: large scale dynamic graph dataset
![[leetcode] 14. Préfixe public le plus long](/img/70/e5be1a7c2e10776a040bfc8d7711a0.png)
[leetcode] 14. Préfixe public le plus long
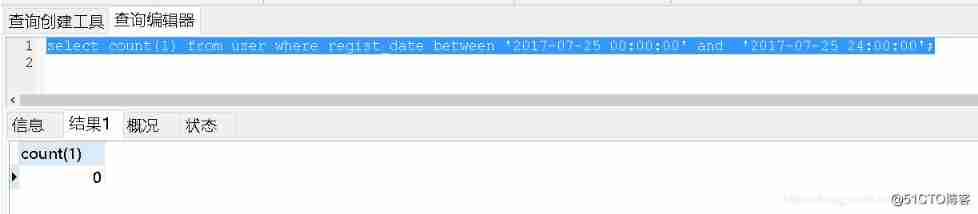
In MySQL and Oracle, the boundary and range of between and precautions when querying the date

Chapter 3 of hands on deep learning - (1) linear regression is realized from scratch_ Learning thinking and exercise answers

【Leetcode】13. 罗马数字转整数
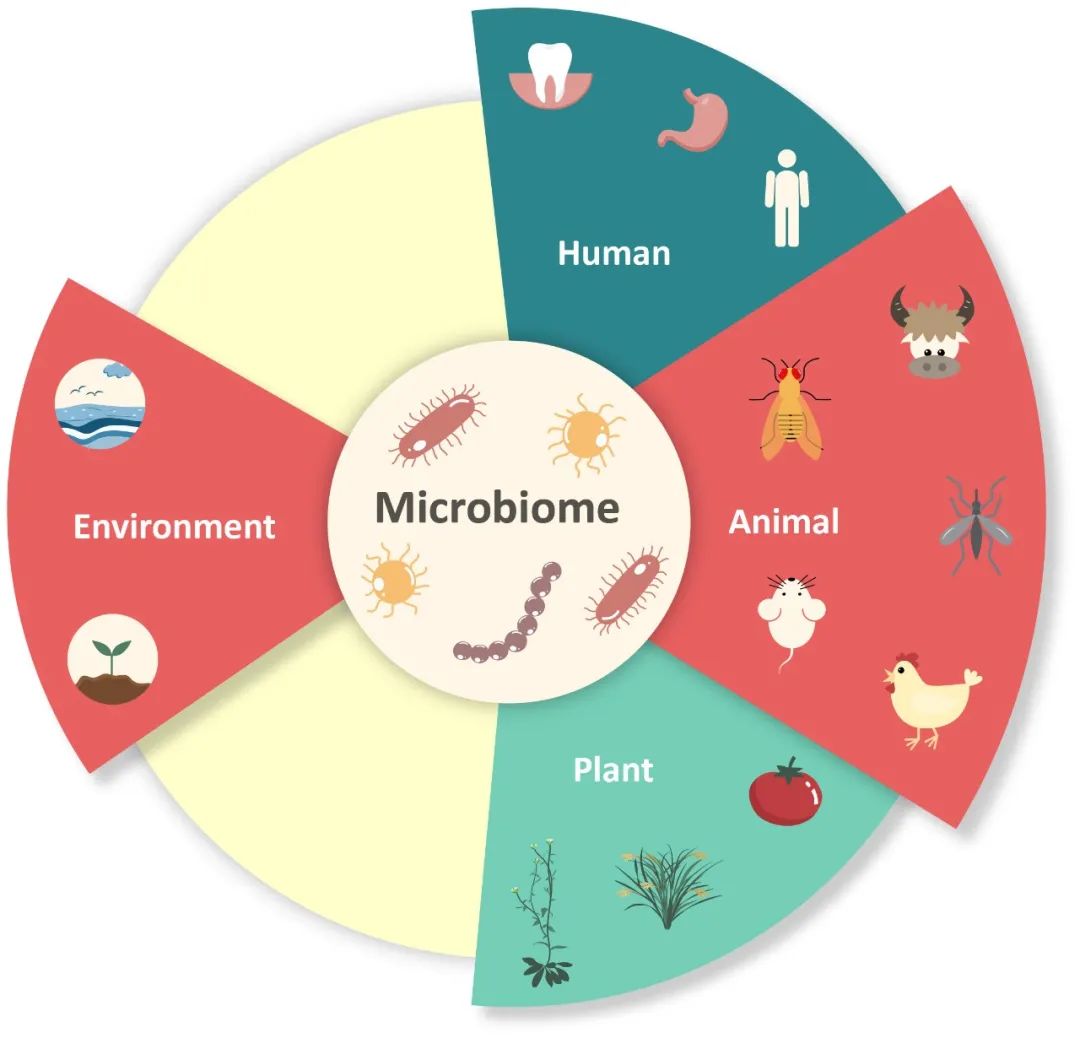
你想要的宏基因组-微生物组知识全在这(2022.7)
随机推荐
相信自己,这次一把搞定JVM面试
2020 "Lenovo Cup" National College programming online Invitational Competition and the third Shanghai University of technology programming competition (a sign in, B sign in, C sign in, D thinking +mst
綠竹生物沖刺港股:年期內虧損超5億 泰格醫藥與北京亦莊是股東
Cell: Tsinghua Chenggong group revealed an odor of skin flora. Volatiles promote flavivirus to infect the host and attract mosquitoes
Qwebengineview crash and alternatives
剑指 Offer 22. 链表中倒数第k个节点
Talk about an experience of job hopping and being rejected
C语言自定义函数的方法
Error when uploading code to remote warehouse: remote origin already exists
Fuyuan medicine is listed on the Shanghai Stock Exchange: the market value is 10.5 billion, and Hu Baifan is worth more than 4billion
What if the default browser cannot be set?
Blog theme "text" summer fresh Special Edition
class和getClass()的区别
Detailed explanation of @accessories annotation of Lombok plug-in
远程办公对我们的各方面影响心得 | 社区征文
Flutter: 动作反馈
R及RStudio下载安装教程(超详细)
IP address translation address segment
How to quickly distinguish controlled components from uncontrolled components?
Domestic relatively good OJ platform [easy to understand]