当前位置:网站首页>Key points and difficulties of the course "information content security" at Harbin Institute of Technology
Key points and difficulties of the course "information content security" at Harbin Institute of Technology
2022-07-01 23:34:00 【Wusu】
《 Information content security 》 Key points and difficulties of course knowledge
Chapter one summary
1. What are the subjects of network security threats ?
2. What is cyberspace ? What are the four elements of cyberspace ?
3.《 Network security law 》 Subject in 、 What are the main objects ? Try to list the basic responsibilities and obligations of each subject .
4. What is cyberspace ? What is Cyberspace Security ? What are the research directions of Cyberspace Security ?
5. The main content of the national network power strategy ? What are the main network security departments in our government ?
6. What is cyberspace sovereignty ? What are the basic principles ?( Independent, equal and autonomous jurisdiction )
7. What is information content security ?
8. What are the main threats to information content security ? What are the typical events ?
( Net anti-terrorism, anti-corruption, intellectual property rights, cults, anti secession, privacy protection )
9. Information content security technology mainly includes ?
10. What are the challenges faced by information content security technology ?( Large amount of data , High computational complexity , New network technology , Social contradictions are deep )
( What is the essential root of network and information security problems ?)
Chapter two Access to network information
1. What are the two types of ways to obtain network information ? Try to compare their main characteristics .
2.BPF What is the principle of catching packets ?
3. What is the main process of the passive packet capture program ?
4.IP What information does the first part mainly contain ? How to extract in packet analysis ?
5.TCP What information does the first part mainly contain ? How to extract in packet analysis ?
6. How to improve the performance of packet capture system in the environment of large traffic network ?
7. How to improve the ability of single machine to catch packets ? What core problems does zero copy packet capture mainly solve ?
8. What is the main idea of website information crawling ? Describe the information crawling algorithm of stand-alone Web pages with pseudo code .
9. Use multiple computers to crawl information from multiple websites , What are the core problems to be solved ? What are the main strategies ?
10. Describe the information crawling algorithm of multi machine single website with pseudo code .
11. This paper briefly introduces the composition of website information monitoring system based on active acquisition technology .
12. sketch Pagerank The main idea of the algorithm .
13. What are the search strategies for web crawling ? What kind of application scenarios are they suitable for ?
14. Try to compare the similarities and differences between active acquisition and passive acquisition .
( How to trace the source of illegal activities on the Internet ?)
The third chapter String matching algorithm
1. What are the classification and evaluation indicators of string matching algorithm ?
2. The main idea of string matching algorithm optimization ?
3. Try to compare the advantages and disadvantages of different string matching algorithms .
4.KMP The basic flow of the algorithm ? Be able to give solution steps for actual data .
5.BM The basic flow of the algorithm ?( Main data structure ) Be able to give solution steps for actual data .
6.AC The basic flow of the algorithm ?( Failure function ) Be able to give solution steps for actual data .
7.WM The basic flow of the algorithm ? Be able to give solution steps for actual data .
8. How to further optimize AC Algorithm ?( Memory space optimization )
9. How to further optimize WM Algorithm ?( Mode length sensitivity )
10. For tens of millions of pattern sets , How to optimize string matching algorithm ?
( Specific IP Address or URL A pattern set of addresses , How to optimize string matching algorithm ?)
Chapter four Text classification
1. Quantitative representation of text ? The main process of text classification system ?
2. What are the main classification methods ? Compare their advantages and disadvantages .
3. Classification method based on rule induction ? Be able to give solution steps for actual data .
4. Classification method based on decision tree (C4.5)? Be able to give solution steps for actual data .
5. Bayesian classification method ? Be able to give solution steps for actual data .
6.KNN classification method ? Be able to give solution steps for actual data .
7. When the sample set is updated frequently , Which classification method is more suitable ?
8. What are the main clustering methods ? What are the characteristics of each ?
9.K-Means Clustering method ?
10. Hierarchical clustering ? The main similarities and differences of clustering methods based on splitting and aggregation ?
The fifth chapter Information content security management
1.C/S And P2P The characteristics of the publishing methods ?
2.C/S In mode , How to respond to ?
3.P2P Typical architecture of network ?
4.P2P In mode , How to respond to ?
5. Main privacy protection methods ?
6. Location privacy protection method ?
Reference materials :
《 Network security development kit details 》
《 Flexible string matching algorithm 》
《 Text mining 》
《P2P Network measurement and analysis 》
边栏推荐
- Commemorate becoming the first dayus200 tripartite demo contributor
- ConcurrentSkipListMap——跳表原理
- [micro service sentinel] @sentinelresource details
- 云信小课堂 | IM及音视频中常见的认知误区
- 认识--Matplotlib
- 2021 RoboCom 世界机器人开发者大赛-本科组初赛
- y53.第三章 Kubernetes从入门到精通 -- ingress(二六)
- Airserver latest win64 bit personal screen projection software
- SWT / anr problem - SWT causes low memory killer (LMK)
- Door level modeling - after class exercises
猜你喜欢

Concepts of dictionary, hash table and array

Distance measurement - Hamming distance
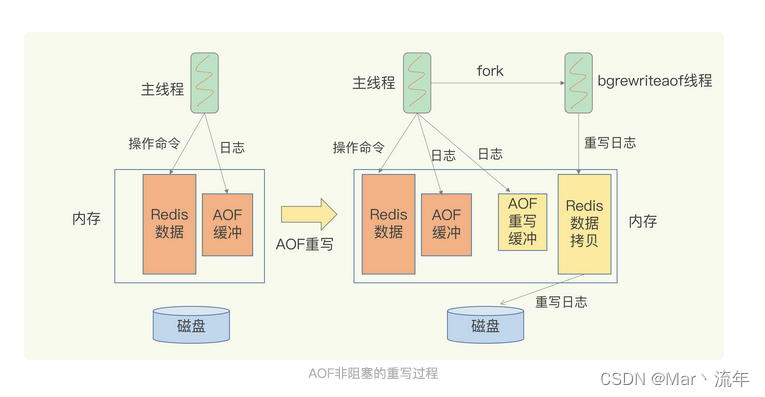
Redis AOF log

What category does the Internet of things application technology major belong to

安全协议重点

Redis RDB snapshot

2022 R1 fast opening pressure vessel operation test questions and answers
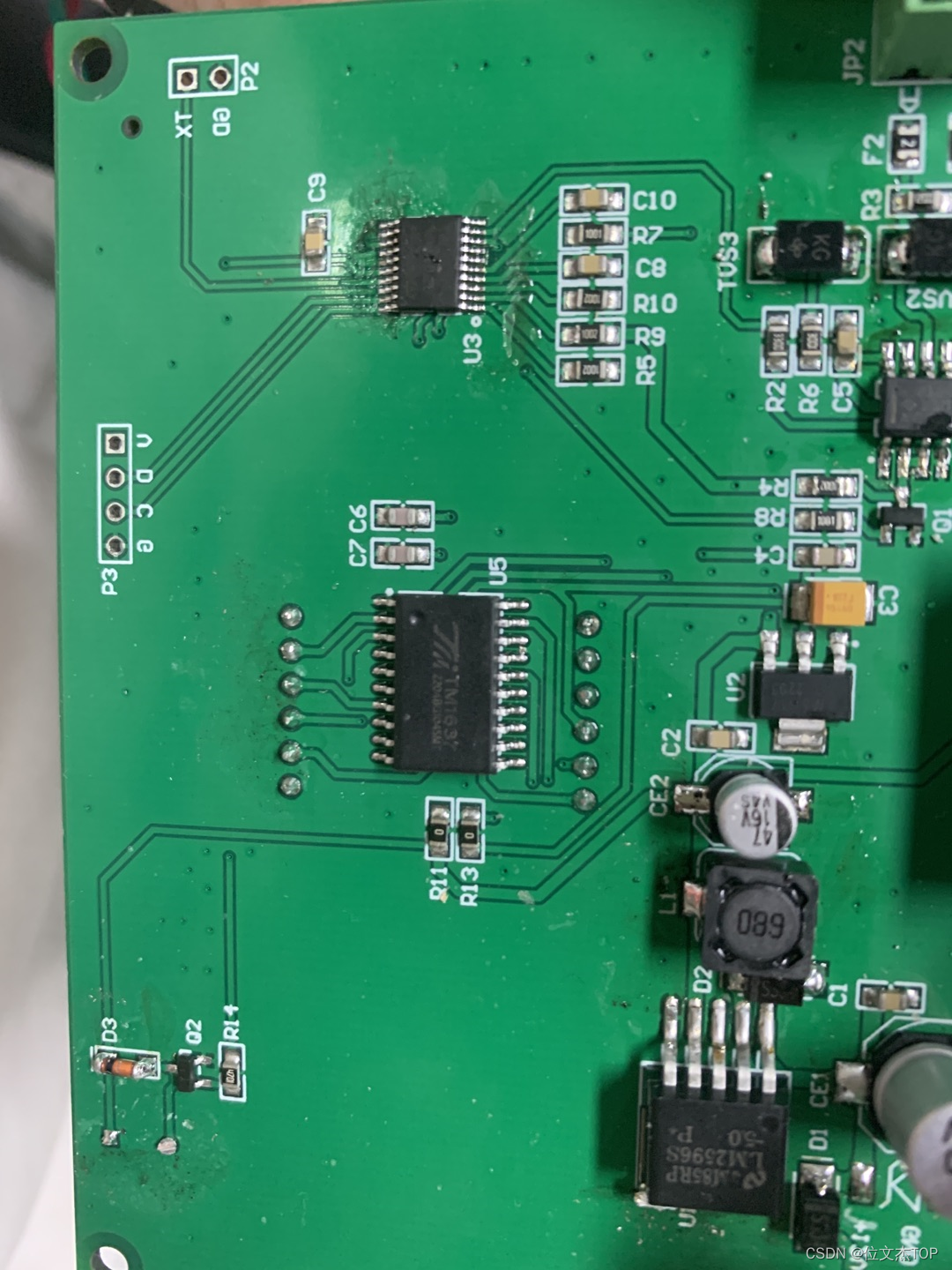
Stm32f030f4 drives tim1637 nixie tube chip

Three development trends of enterprise application from the perspective of the third technological revolution

第六章 数据流建模
随机推荐
What category does the Internet of things application technology major belong to
小程序表单校验封装
dat. GUI
Switch to software testing, knowing these four points is enough!
云信小课堂 | IM及音视频中常见的认知误区
Practical application and extension of plain framework
Typescript enumeration
VIM color the catalogue
from pip._internal.cli.main import main ModuleNotFoundError: No module named ‘pip‘
图的遍历之深度优先搜索和广度优先搜索
SWT / anr problem - SWT causes kernel fuse deadlock
Applet form verification encapsulation
golang中的iota
共享电商的背后: 共创、共生、共享、共富,共赢的共富精神
Win 10 mstsc connect RemoteApp
SWT/ANR问题--SWT 导致 low memory killer(LMK)
物联网应用技术专业是属于什么类
The best smart home open source system in 2022: introduction to Alexa, home assistant and homekit ecosystem
学成在线案例实战
ConcurrentSkipListMap——跳表原理