当前位置:网站首页>Introduction and experience of wazuh open source host security solution
Introduction and experience of wazuh open source host security solution
2022-07-05 05:38:00 【Operation and maintenance of watermelon】
Increasingly important host security management
With the surging development of various digital currencies , Originally run as Linux System oriented 、 The field of enterprise host security management, which is rarely invaded by viruses or trojans, is becoming more and more unstable , All kinds of people in order to get “ free ” Enterprise computing power to dig money , They have started the idea of enterprise server . The management of enterprise application information security is no longer satisfied with only a few “ Network security ” Equipment , If you only do this , I'm afraid I can't even pass the current level III standard of level protection .
At present, some powerful manufacturers have self-developed Linux Host security management tool , There are also several manufacturers specializing in enterprise services of safety products that have launched commercial products , The cloud application stores of several major public cloud manufacturers also include host security products and cloud firewalls 、DDos The protection package is provided to the customer .
Compared with network security protection products , The cost of host security products will be higher , Because it needs to be installed on every host agent node , Billing is basically based on the number of nodes . For enterprises with a certain scale of operation , Use hundreds of physical machines 、 Virtual machines or virtual machines are very common , The cost pressure of fully deploying commercial mainframe security products is great .
Today we introduce this open source host security product ——Wazuh, It's free open source software . Its components comply with GNU General public permit 2 Version and Apache license 2.0 edition (ALv2).Wazuh Provided by the platform XDR and SIEM Functions to protect the cloud 、 Container and server workloads . This includes log data analysis 、 Intrusion and malware detection 、 Document integrity monitoring 、 Configuration evaluation 、 Vulnerability detection , And support the inspection of compliance .
Several safety terms :
- XDR( Cross layer detection and response )
- EDR( Endpoint detection and response )
- NTA( Network traffic analysis )
- SIEM( Security information and event management )
Wazuh Usage scenarios of
- Log data analysis
- Rootkits testing
- Configuration evaluation
- Vulnerability detection
- Container service security
- Document integrity monitoring
- Actively respond and contain
- System resource list management
- Cloud service security
- Compliance
Wazuh Main components
Wazuh The solution is based on Wazuh agent, And three core components :Wazuh The server 、Wazuh Indexer and Wazuh The dashboard .
- Wazuh indexer: A highly extensible full-text retrieval and analysis engine
- Wazuh server: For configuration and management agents, receive agents Send the data and parse , Single instance deployment can support hundreds to thousands agents, Support cluster mode to provide greater processing power .
- Wazuh dashboard:Web UI, Mainly used for security events 、 Compliance 、 Intrusion detection 、 Visual display of document integrity monitoring and configuration evaluation results , Also used in Wazuh Service configuration and status monitoring .
- Wazuh agents: Software installed on various types of terminals , Support Linux, Windows, macOS, Solaris, AIX, and HP-UX. Provide threat prevention 、 Detection and response capability .
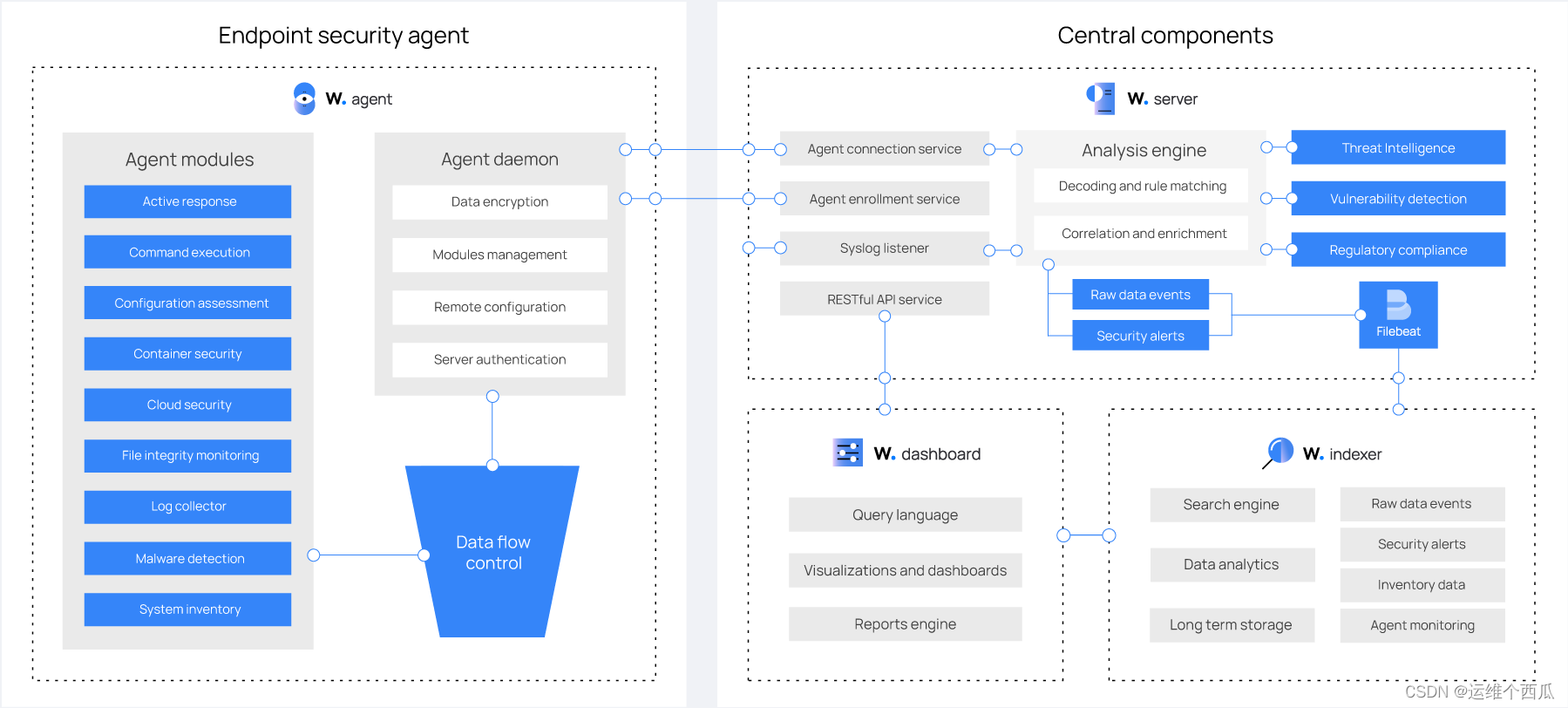
In addition to based on agent In addition to the monitoring function of ,Wazuh The platform can also monitor agentless equipment , Such as firewalls 、 Switch 、 Router or IDS etc. . for example , Can pass Syslog Collect system log data , And through SSH or API Regularly detect its data to monitor its configuration .
Wazuh Deployment architecture
For scenarios with heavy business load , It is suggested that server And indexer Deployed on different host nodes , Depending on the load size, you can also choose server/indexer Single instance or cluster mode deployment .
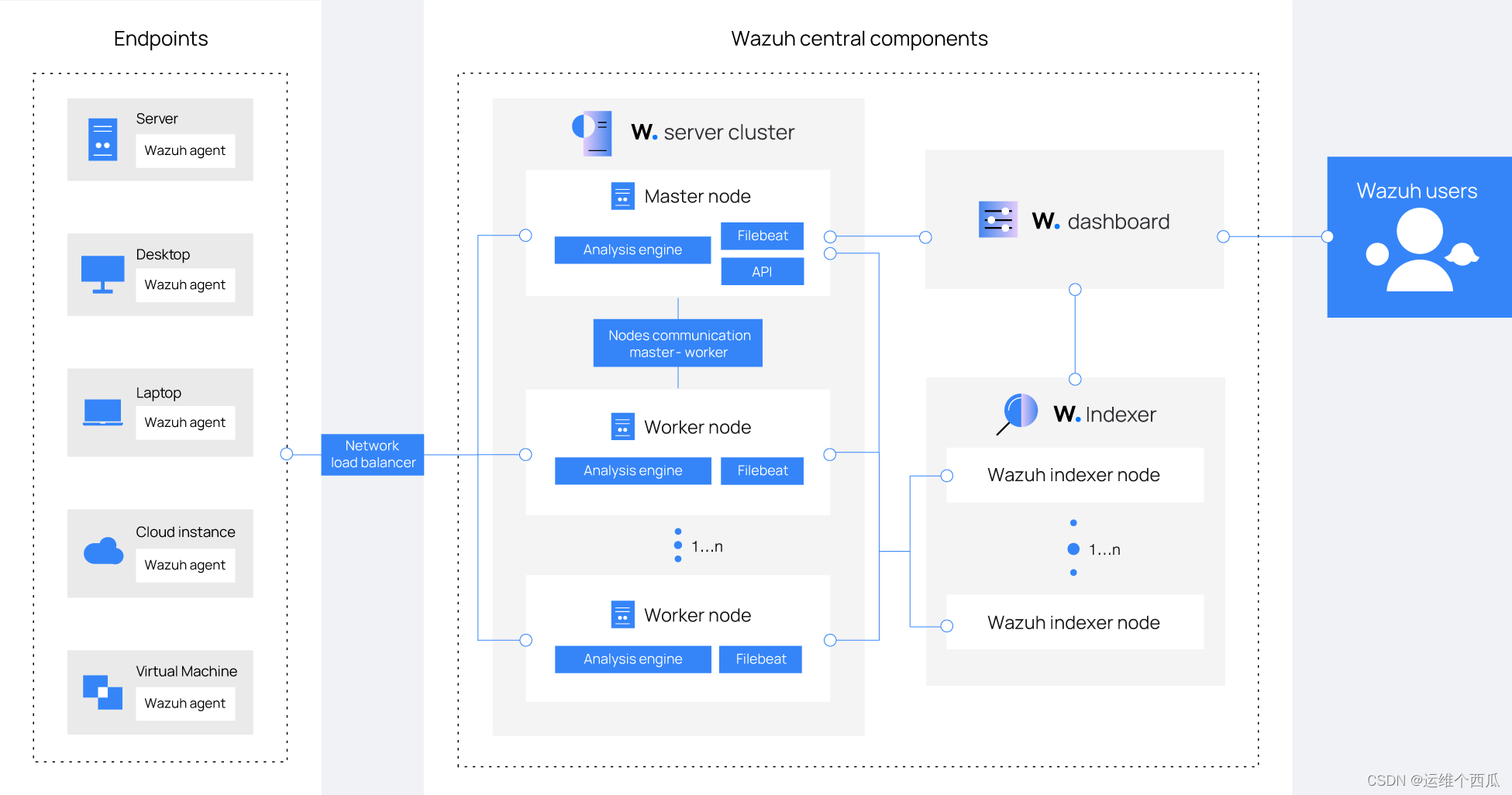
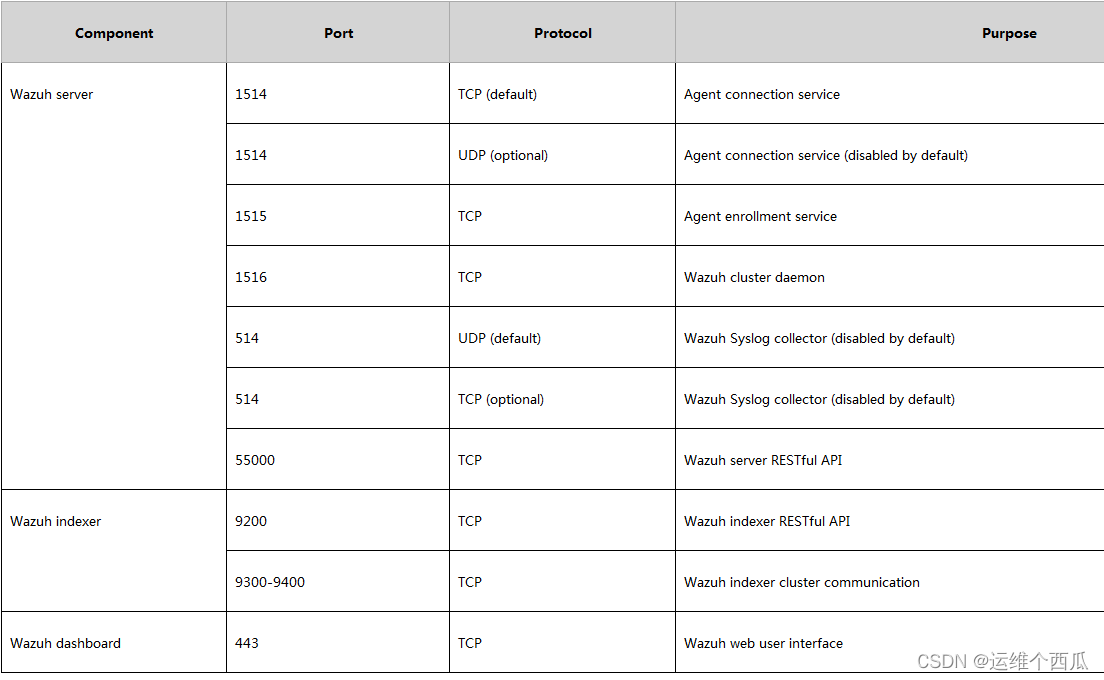
Wazuh Communication between components and common ports
Wazuh agent And Wazuh server Communication for
Wazuh server Default listening 1514 port , For processing and agents Communication for , By default AES The encrypted .
The received data will be saved to the following default path :
- /var/ossec/logs/archives/archives.json, Save from agents All event messages received , It is recommended to deploy cron Schedule tasks to keep only recent data , Avoid the failure of full storage space
- /var/ossec/logs/alerts/alerts.json, Save the event message matching the recognition rule on
Wazuh server And Wazuh indexer Communication for
Wazuh server adopt TLS encryption , Use Filebeat Send alarm and event data to Wazuh indexer.Filebeat Read Wazuh server Output data and send it to Wazuh indexer( By default , Listening port 9200/TCP). Once the data is Wazuh indexer Indexes ,Wazuh The dashboard will be used for further information mining and visual presentation .
Wazuh Dashboard query Wazuh RESTful API( Listen by default Wazuh server Upper 55000/TCP port ), To display Wazuh server and agent Information about the configuration and status of .
Wazuh The service port used is the same as the default value
Wazuh Single instance deployment and experience
To experience Wazuh The function of , We can quickly deploy a single instance service in the test environment , namely Wazuh server, Wazuh indexer and Wazuh dashboard All deployed on one host .
Host operating system recommendations :CentOS7/8,Ubuntu 16.04/18.04/20.04/22.04
install Wazuh:
$ curl -sO https://packages.wazuh.com/4.3/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
Deploy on the terminal host that needs to be monitored Wazuh agent Software , Reference method :https://documentation.wazuh.com/current/installation-guide/wazuh-agent/index.html
install Linux Wazuh agnet:
rpm --import https://packages.wazuh.com/key/GPG-KEY-WAZUH
cat > /etc/yum.repos.d/wazuh.repo << EOF [wazuh] gpgcheck=1 gpgkey=https://packages.wazuh.com/key/GPG-KEY-WAZUH enabled=1 name=EL-\$releasever - Wazuh baseurl=https://packages.wazuh.com/4.x/yum/ protect=1 EOF
WAZUH_MANAGER="10.0.0.2" yum install wazuh-agent
systemctl daemon-reload
systemctl enable wazuh-agent
systemctl start wazuh-agent
More deployments agent See Deployment variables for Linux
About Wazuh agent Please refer to Wazuh agent enrollment
Ban Wazuh agent Update , To avoid agent Because of carelessness, the version of was upgraded to higher than server Version of :
sed -i "s/^enabled=1/enabled=0/" /etc/yum.repos.d/wazuh.repo
How to delete Wazuh service :
$ sudo bash ./wazuh-install.sh --uninstall
notes : If the network condition is poor ,yum Installation error , You can try downloading related from the official website rpm Package for installation https://documentation.wazuh.com/current/installation-guide/packages-list.html
Integrated deployment Wazuh And Elastic Stack basic license
Realized Wazuh And Elastic Stack Function integration of , Message data is stored in Elastic And based on Elastic Stack Carry out data retrieval and graphic display .
There are two ways to deploy :
- All-in-one deployment , Single machine deployment all , For testing or small-scale environment .
- Distributed deployment
ad locum , We deploy a All-in-one Environment , Give you a demonstration .
notes : The following tests , We are all based on centos7 System deployment .
Install several toolkits
yum install zip unzip curl
install Elasticsearch
rpm --import https://artifacts.elastic.co/GPG-KEY-elasticsearch
cat > /etc/yum.repos.d/elastic.repo << EOF [elasticsearch-7.x] name=Elasticsearch repository for 7.x packages baseurl=https://artifacts.elastic.co/packages/7.x/yum gpgcheck=1 gpgkey=https://artifacts.elastic.co/GPG-KEY-elasticsearch enabled=1 autorefresh=1 type=rpm-md EOF
yum install elasticsearch-7.10.2
elastic The configuration file :
curl -so /etc/elasticsearch/elasticsearch.yml https://packages.wazuh.com/4.3/tpl/elastic-basic/elasticsearch_all_in_one.yml
Install digital certificate :
curl -so /usr/share/elasticsearch/instances.yml https://packages.wazuh.com/4.3/tpl/elastic-basic/instances_aio.yml
/usr/share/elasticsearch/bin/elasticsearch-certutil cert ca --pem --in instances.yml --keep-ca-key --out ~/certs.zip
unzip ~/certs.zip -d ~/certs
mkdir /etc/elasticsearch/certs/ca -p
cp -R ~/certs/ca/ ~/certs/elasticsearch/* /etc/elasticsearch/certs/
chown -R elasticsearch: /etc/elasticsearch/certs
chmod -R 500 /etc/elasticsearch/certs
chmod 400 /etc/elasticsearch/certs/ca/ca.* /etc/elasticsearch/certs/elasticsearch.*
rm -rf ~/certs/ ~/certs.zip
chown -R elasticsearch.elasticsearch /etc/elasticsearch/
Pay attention to the need to use jdk8
Set service startup mode :
systemctl daemon-reload
systemctl enable elasticsearch
systemctl start elasticsearch
establish Elastic Stack pre-built roles and users:
/usr/share/elasticsearch/bin/elasticsearch-setup-passwords auto
Check the installation results :
curl -XGET https://localhost:9200 -u elastic:<elastic_password> -k
install Wazuh server
Wazuh server In charge of from agents Collect data and analyze it , Mainly includes Wazuh manager、Wazuh API and Filebeat Three components .
rpm --import https://packages.wazuh.com/key/GPG-KEY-WAZUH
cat > /etc/yum.repos.d/wazuh.repo << EOF [wazuh] gpgcheck=1 gpgkey=https://packages.wazuh.com/key/GPG-KEY-WAZUH enabled=1 name=EL-\$releasever - Wazuh baseurl=https://packages.wazuh.com/4.x/yum/ protect=1 EOF
install wazuh-manager:
yum install wazuh-manager
systemctl daemon-reload
systemctl enable wazuh-manager
systemctl start wazuh-manager
install Filebeat:
Used to forward alarm events and archived messages to Elasticsearch Storage .
yum install filebeat-7.10.2
filebeat Configuration file for :
curl -so /etc/filebeat/filebeat.yml https://packages.wazuh.com/4.3/tpl/elastic-basic/filebeat_all_in_one.yml
Wazuh Alarm configuration template :
curl -so /etc/filebeat/wazuh-template.json https://raw.githubusercontent.com/wazuh/wazuh/4.3/extensions/elasticsearch/7.x/wazuh-template.json
chmod go+r /etc/filebeat/wazuh-template.json
download Filebeat The use of Wazuh modular :
curl -s https://packages.wazuh.com/4.x/filebeat/wazuh-filebeat-0.2.tar.gz | tar -xvz -C /usr/share/filebeat/module
to update /etc/filebeat/filebeat.yml Password information in the configuration file :
output.elasticsearch.password: <elasticsearch_password>
The above password The parameter value is set to elastic User's password
Deployment Certificate :
cp -r /etc/elasticsearch/certs/ca/ /etc/filebeat/certs/
cp /etc/elasticsearch/certs/elasticsearch.crt /etc/filebeat/certs/filebeat.crt
cp /etc/elasticsearch/certs/elasticsearch.key /etc/filebeat/certs/filebeat.key
start-up Filebeat:
systemctl daemon-reload
systemctl enable filebeat
systemctl start filebeat
Test installation results :
filebeat test output
install Kibana:
yum install kibana-7.10.2
Deployment Certificate :
mkdir /etc/kibana/certs/ca -p
cp -R /etc/elasticsearch/certs/ca/ /etc/kibana/certs/
cp /etc/elasticsearch/certs/elasticsearch.key /etc/kibana/certs/kibana.key
cp /etc/elasticsearch/certs/elasticsearch.crt /etc/kibana/certs/kibana.crt
chown -R kibana:kibana /etc/kibana/
chmod -R 500 /etc/kibana/certs
chmod 440 /etc/kibana/certs/ca/ca.* /etc/kibana/certs/kibana.*
curl -so /etc/kibana/kibana.yml https://packages.wazuh.com/4.3/tpl/elastic-basic/kibana_all_in_one.yml
edit /etc/kibana/kibana.yml, Update the password :
elasticsearch.password: <elasticsearch_password>
password The parameter value is set to elastic User's password
mkdir /usr/share/kibana/data
chown -R kibana:kibana /usr/share/kibana
install Wazuh kibana plug-in unit :
cd /usr/share/kibana
sudo -u kibana /usr/share/kibana/bin/kibana-plugin install https://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.3.5_7.10.2-1.zip
allow kibana The user to use 443 port :
setcap 'cap_net_bind_service=+ep' /usr/share/kibana/node/bin/node
Sign in web platform :
URL: https://<wazuh_server_ip>
user: elastic
password: <PASSWORD_elastic>
Ban wazuh,elastic Of yum Install source , To avoid compatibility problems caused by some software packages being automatically updated :
sed -i "s/^enabled=1/enabled=0/" /etc/yum.repos.d/wazuh.repo
sed -i "s/^enabled=1/enabled=0/" /etc/yum.repos.d/elastic.repo
install Wazuh agent
Find a testing machine , install Wazuh agent, Used to verify and test related functions .
https://documentation.wazuh.com/current/installation-guide/wazuh-agent/index.html
rpm --import https://packages.wazuh.com/key/GPG-KEY-WAZUH
cat > /etc/yum.repos.d/wazuh.repo << EOF [wazuh] gpgcheck=1 gpgkey=https://packages.wazuh.com/key/GPG-KEY-WAZUH enabled=1 name=EL-\$releasever - Wazuh baseurl=https://packages.wazuh.com/4.x/yum/ protect=1 EOF
WAZUH_MANAGER="IP-OF-WAZUH-MANAGER" yum install wazuh-agent
Please put WAZUH_MANAGER Replace the parameter value with Wazuh-manager The host IP Address
systemctl daemon-reload
systemctl enable wazuh-agent
systemctl start wazuh-agent
sed -i "s/^enabled=1/enabled=0/" /etc/yum.repos.d/wazuh.repo
Sign in kibana web Platform view configuration results
As you can see from the screenshot below ,Wazuh The security management functions provided are very rich , There are many dimensions and levels , The display and use experience of graphical interface is also very good .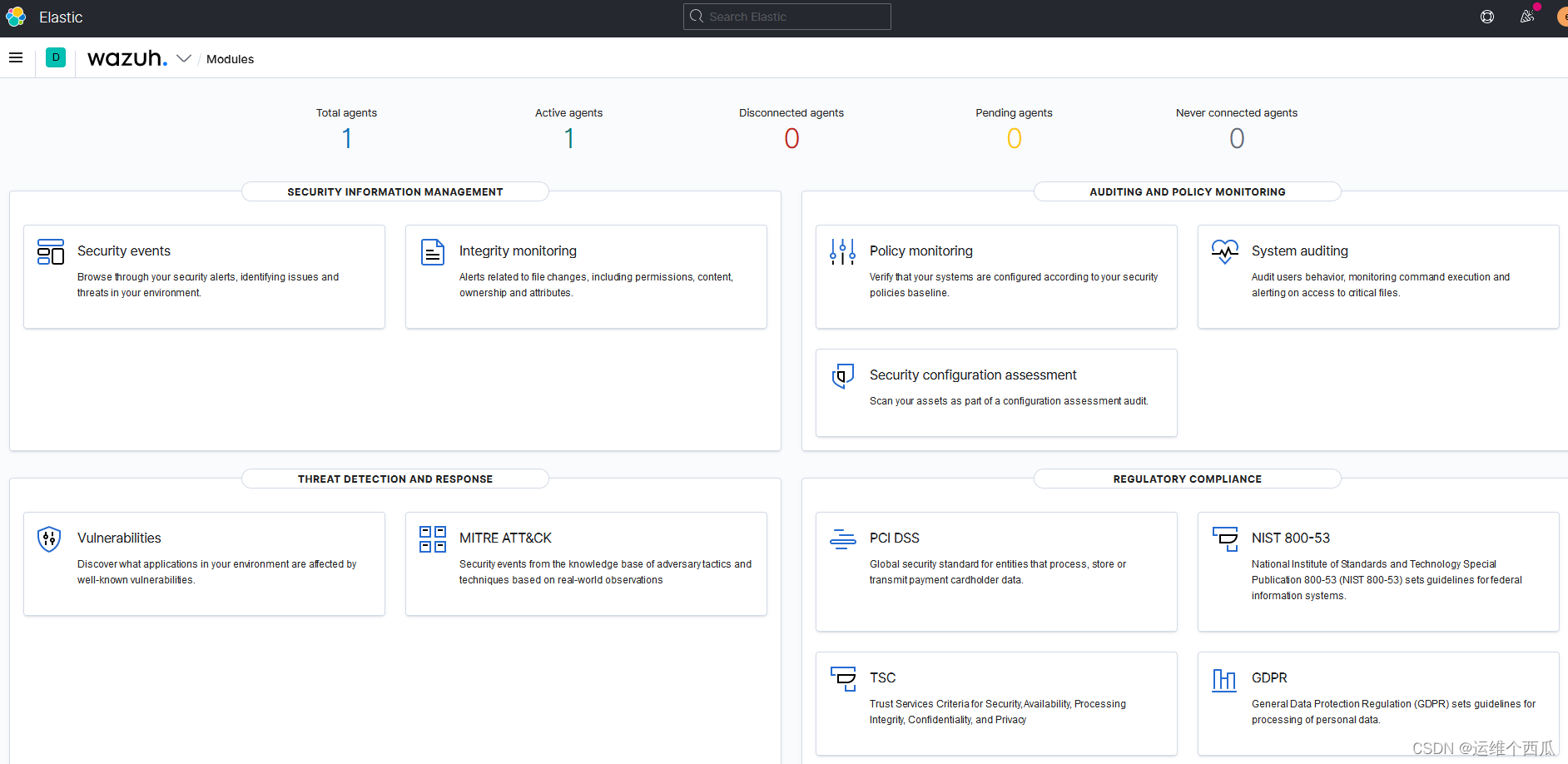
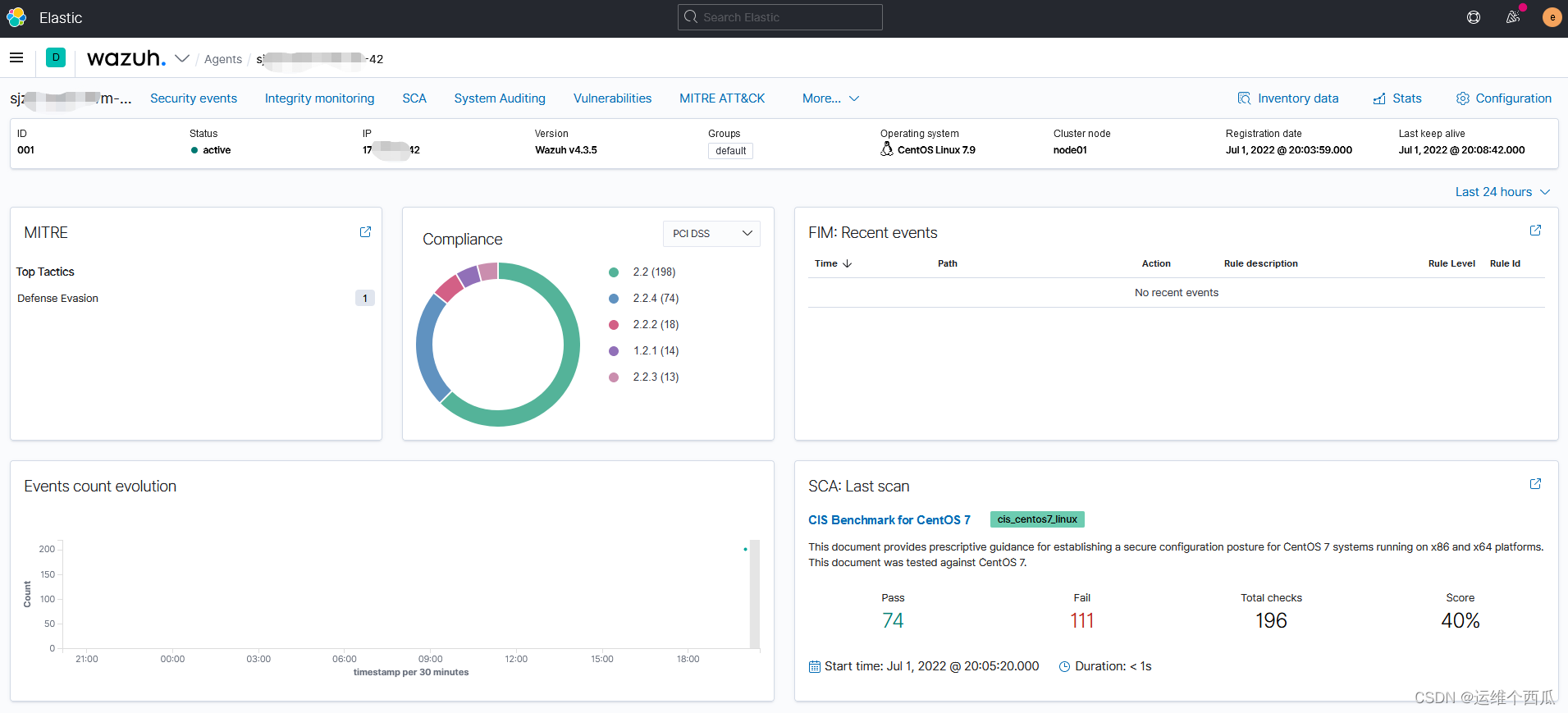
Next , We will continue to share in the following articles Wazuh Distributed deployment scheme and practice of production environment , And the design and implementation of customized configuration template for information security management requirements .
边栏推荐
猜你喜欢
On-off and on-off of quality system construction
R语言【数据集的导入导出】
SAP method of modifying system table data
【Jailhouse 文章】Jailhouse Hypervisor
Reader writer model

Educational Codeforces Round 116 (Rated for Div. 2) E. Arena
YOLOv5-Shufflenetv2
API related to TCP connection
Sword finger offer 05 Replace spaces
全国中职网络安全B模块之国赛题远程代码执行渗透测试 //PHPstudy的后门漏洞分析
随机推荐
Educational codeforces round 109 (rated for Div. 2) C. robot collisions D. armchairs
Find a good teaching video for Solon framework test (Solon, lightweight application development framework)
剑指 Offer 58 - II. 左旋转字符串
卷积神经网络——卷积层
剑指 Offer 06.从头到尾打印链表
Haut OJ 1218: maximum continuous sub segment sum
ALU逻辑运算单元
第六章 数据流建模—课后习题
Haut OJ 1357: lunch question (I) -- high precision multiplication
In this indifferent world, light crying
Pointnet++ learning
CCPC Weihai 2021m eight hundred and ten thousand nine hundred and seventy-five
SSH password free login settings and use scripts to SSH login and execute instructions
Control Unit 控制部件
剑指 Offer 53 - I. 在排序数组中查找数字 I
Zzulioj 1673: b: clever characters???
Kubedm series-00-overview
Daily question - longest substring without repeated characters
A new micro ORM open source framework
剑指 Offer 53 - II. 0~n-1中缺失的数字