当前位置:网站首页>What are the software testing methods? Show you something different
What are the software testing methods? Show you something different
2022-07-06 15:13:00 【Test Xiaowan】
Catalog
4. Operation and shutdown test
5. Testing of service programs :
6. System management ( Parameter setting )
13. Statistics 、 Inquire about
1. Install the test
1) During the installation process, for the default installation directory and any specified installation directory , Whether it can be installed correctly ;
2) If you choose to install , See if it can achieve its corresponding function ;
3) After quitting the installation program at all places where you can quit the installation , Verify that this program was not successfully installed ( No program groups and program items are generated );
4) After the software is installed , Does it affect other installed software ;
5) After bare metal installation , Whether each function point is available ;
6) Before the installation , Does the installer determine the amount of free disk space , If the installation space requirements cannot be met , Can setup continue ;
7) Check during installation Copyright notice 、 Version information 、 Corporate name 、LOGO Whether it meets the standard ;
8) Whether the interface display and prompt language are accurate during installation 、 friendly ;
9) Whether there is a prompt when the installation is repeated 、 Can I overwrite the installation 、 Whether the installation can be upgraded 、 Whether to allow multiple versions to coexist ;
10) Whether there is a registration code or hardware dongle , Without them ( Or error ) Whether it can be installed smoothly under existing conditions .
2. Configuration testing
1) Can you follow the instructions in the user manual , Run on a variety of operating systems (Windows Various versions 、Unix 、Linux etc. );
2) Install and configure the software according to the minimum requirements of the system , Check whether various functions can be realized normally ;
3) Can you give a prompt when the data source and other information are not configured correctly ;
4) Can you follow the instructions in the user manual , Support multiple databases .
3. Uninstall test
1) Whether the registration information in the registry and the related program installation directory can be completely deleted after uninstallation ;
2) After the shared files are completely deleted during uninstallation , See if other programs work properly ;
3) After uninstalling , Whether it affects other installed software ;
4) After the system is uninstalled, the user determines whether to keep the document ;
5) Whether the software name and version information on the software uninstall screen are correct ;
6) Whether the unloading can be correctly exited at all positions that can exit halfway ;
7) Whether the interface display and prompt language are accurate during unloading 、 friendly ;
8) Whether the original saved file can be opened after uninstalling and installing this system , And everything works normally ;
9) Uninstall the program if it requires restarting the machine , Whether to prompt the user to save the existing running program data before restarting ;
10) Whether components can be selected for uninstallation ;
11) During uninstallation , Handling of unexpected situations ( Power down, etc ).
12) In the process of unloading , Whether there is a stop or end button .
4. Operation and shutdown test
1) Whether the runtime conflicts with other applications ( Memory conflict );
2) Whether it is possible to run multiple programs at the same time ;
3) Whether there is program running prompt in the taskbar ;
4) If there is unsaved data , Whether there is a prompt when closing the system ;
1) Whether there is a confirmation prompt when the background service program clicks the close button ;
2) Whether the runtime takes up too much system resources 、 Whether the occupied system resources can be released when exiting .
5. Testing of service programs :
1) Whether the system limits the number of server programs started , If not limited , Whether starting multiple services within the same scope has an impact on the system ;
2) Whether the service program can run normally for a long time ;
3) After external abnormality , Automatic recovery capability of service program ( Server power down 、 Recovery after network interruption 、 Recover after database exception …);
4) Whether there is a confirmation prompt when clicking the close button ;
5) Whether the application is compatible with other programs ( Can memory conflicts be avoided ).
6. System management ( Parameter setting )
1) After parameter setting , Whether it can be applied correctly ;
2) Set wrong parameters , The fault tolerance of the system ;
3) Modify the parameters , Impact on related modules ;
4) Whether the system has default parameters ,A Yes : Whether the default parameter works ;B No, : Not set up , Whether the system can run or give a prompt .
7. user 、 Rights management
1) After giving a person the corresponding authority , Check whether this person has this permission on the interface , And log in as this person , Verify that the permissions are set correctly ( Can we go beyond the authority given );
2) Delete or modify the permissions of the person who has logged in to the system and is operating , Whether the program can correctly handle ;
3) Re register the system, change the login identity, and then log in , See if the program can be executed correctly , Whether the permission is correct ;
4) With workgroup or role management , Delete the workgroup or role that contains the user , Whether the program can correctly handle ;
5) Users with different permissions log in to the same system , Whether the permission scope is correct ;
6) Overwrite all permission settings of the system ;
7) Can I add a user whose information is empty ( This includes an empty user name and password 、 Empty user name is not empty password 、 Non empty user name and password );
8) Can I add a long user name and password , If allowed , Whether the new user can log in correctly ;
9) Whether the system allows to delete the special user of system administrator or modify the password of system administrator , The actual situation of the system after deletion or modification ;
10) Whether the login user can modify his / her own permissions ;
11) Add users ( Marked or numbered ): Same identification , Different user names ; Same identification , Same user name ; The logo is different , Same user name ; The logo is different , Different user names ;
12) Whether the login user can modify himself ( Or someone else ) Information about , Delete me ( Or someone else );
13) Modify user information ( Including authority , password , Basic information, etc ), Impact on other modules ;
14) Modify user information : The modified user information is the same as the existing user information ; The modified user information is different from the existing user information ;
15) Do not authorize users , Is login allowed ;
15) When changing some settings , Whether it will affect the settings of personnel with superior permission and the same permission ;
16) The system administrator modified some data , Whether the data changes when logging in as another person ;
17) Whether users can belong to multiple groups at the same time , Whether the permissions of each group can be crossed ;
18) Whether the user added again after deletion has the previous permission ; Change user attributes ( Including authority ) See if it affects the permission .
8. System login test
1) Log in to the system with a legal user ;
2) user name 、 Can I log in if the password is wrong or missing ;
3) Whether the system allows multiple illegal logins , Is there a limit on the number of times ;
4) Whether the system can handle correctly by using the logged in account ;
5) Whether the login system with a disabled account can correctly handle ;
6) The deleted or modified user logs in with the original user ;
7) Do not enter user name and password , Repeat point “ determine ” and “ Cancel ” Button , Is login allowed .
9. Cancellation
1) Log out to the original module 、 Whether the new module system can correctly handle ;
2) Whether the abort logoff can return to the original module 、 The original user ;
3) Log off as the original user 、 Whether the new user system can handle ;
4) Using the wrong account 、 Password or unauthorized account 、 Disabled account to log off .
10. Modify password
1) Normal condition ;
2) Whether the system can correctly handle the incorrect original or new password that is inconsistent with the confirmed password ;
3) After changing the password , Whether you can log in with the original password ( At the same time, verify whether the new password is valid );
4) Whether the passwords of other users can be modified .
11. Right click function
1) Whether the functions in the right-click menu are the same as those in the menu ( Or toolbar ) The corresponding functions in are consistent ;
2) Can the functions in the right-click menu be realized correctly ;
3) Whether the hotkeys under the same menu are the same .
12. Record list
1) Add duplicate records 、 Blank record , Whether the system can handle ;
2) Do not save after modification ( There is a save button ), Whether the system can handle ;
3) Delete or modify information in use , Whether the system can handle ;
4) Delete upstream or downstream records of cascading records , Whether the system can handle ;
5) Whether there is a prompt when deleting records ;
6) Can the default system information contained in the record be deleted and modified ;
7) Whether the record list can reflect the changes of records in time ;
8) Whether the relevant information of the system can be updated in time after the change is recorded ;
13. Statistics 、 Inquire about
1) Whether the system can correctly handle the illegal time range ;
2) When the statistical query statement contains multiple and or non conditions , Whether the system can handle ;
3) The conditional logic is confused , Whether the system can handle ;
4) Whether the multi table query statistics and single table query statistics functions are correctly implemented ;
5) Search by category 、 Precise query 、 Unconditional query 、 Whether the combined query can completely list the records that meet the conditions ;
6) Can you query according to the default conditions of the system ;
7) When the statistical period is the current day 、 extend into the next day 、 extend into next month 、 Cross season 、 Cross year , Check whether the query results are correct ;
8) When some operations are cancelled by others , Set the condition segment to before cancellation 、 After the cancellation 、 A period of time that contains the cancellation operation ;
9) When logging in with different permissions , Statistics 、 Is the query correct ;
10) When querying or counting large amounts of data , Whether the system allows the operation to be terminated ;
11) Inquire about 、 Whether the statistics button allows double clicking or more clicks , How does the system react ;
1) Whether the queried data can be modified .
14. File operations
a) preservation
1) Whether the file can be correctly saved in the default location or the specified location ( Local 、 The Internet );
2) Whether the system can correctly handle long file names 、 Save special character file name ;
3) Whether the file can be saved with other extensions ;
4) For example, the application is case sensitive for file names , When these files are exported to media , Whether the system can handle ;
5) When media space is full , Whether the system gives a prompt .
b) open
1) Whether the last saved content is displayed correctly when opening the file ;
2) Whether the system can correctly handle files with non system default extensions ;
3) Whether the file can be opened correctly by other programs ;
4) Open the dialog box , Whether there is a file type with a default extension ;
5) When the dialog box opens , Whether there is a default path .
c) Printout
1) Whether to print in the set format ;
2) Whether there is print preview , Whether the print font can be set , Whether the printing effect meets the customer's requirements ;
3) Whether the content of the print preview is correct , Whether the content can be dragged , Whether it affects the actual printing ;
4) Install or not install the printing function module , Does it affect other modules ;
5) If the printer is not installed, will the system prompt ;
6) Whether normal printing interruption can be carried out in the middle of printing , Whether you can choose what to print .
7) Can I print locally or online .
d) Import 、 Export function
1) When the imported file format is not required , How does the system deal with ;
2) Import 、 Whether the exported valid files can be completely and correctly displayed and used ;
3) Whether the exported file can be modified , If allowed , Can I use ; If not allowed , What are the limitations of the system ;
4) Import , Export whether you can choose a path ;
5) Import on the client and server side , export ;
6) Import between client and client , export ;
7) Import locally , export ;
8) Import of different file formats , export .
e) Check in and check out
1) A single file 、 Multiple file check-in and check-out ;
2) Can I check in and check out multiple times ;
3) What can others do with the document after it is checked out .

Thank everyone who reads my article carefully !!!
If you can use the following information, you can take it away directly :
1、 Self study development or test the necessary complete project source code and environment
2、 Test all templates in the work ( test plan 、 The test case 、 Test report, etc )
3、 Classic interview questions for software testing
4、Python/Java Automation test practice .pdf
5、Jmeter/postman Interface test full set of video acquisition
I personally sorted out some technical materials I have sorted out in my software testing career in recent years , contain : e-book , Resume module , Various work templates , Interview treasure , Self study projects, etc . Please leave a message in the comment area. Thank you .
边栏推荐
- 几款开源自动化测试框架优缺点对比你知道吗?
- Nest and merge new videos, and preset new video titles
- Pedestrian re identification (Reid) - data set description market-1501
- [oiclass] maximum formula
- STC-B学习板蜂鸣器播放音乐
- Currently, mysql5.6 is used. Which version would you like to upgrade to?
- The salary of testers is polarized. How to become an automated test with a monthly salary of 20K?
- ucore lab5用户进程管理 实验报告
- Four methods of exchanging the values of a and B
- pytest
猜你喜欢
软件测试方法有哪些?带你看点不一样的东西
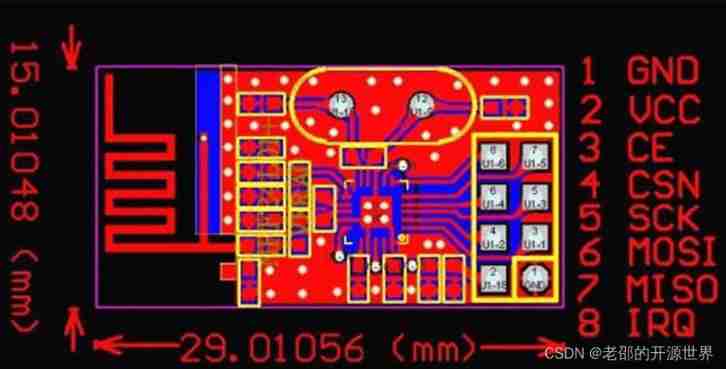
Portapack application development tutorial (XVII) nRF24L01 launch B

C language do while loop classic Level 2 questions
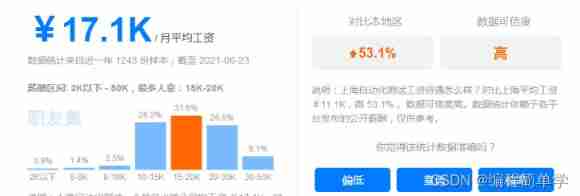
The salary of testers is polarized. How to become an automated test with a monthly salary of 20K?
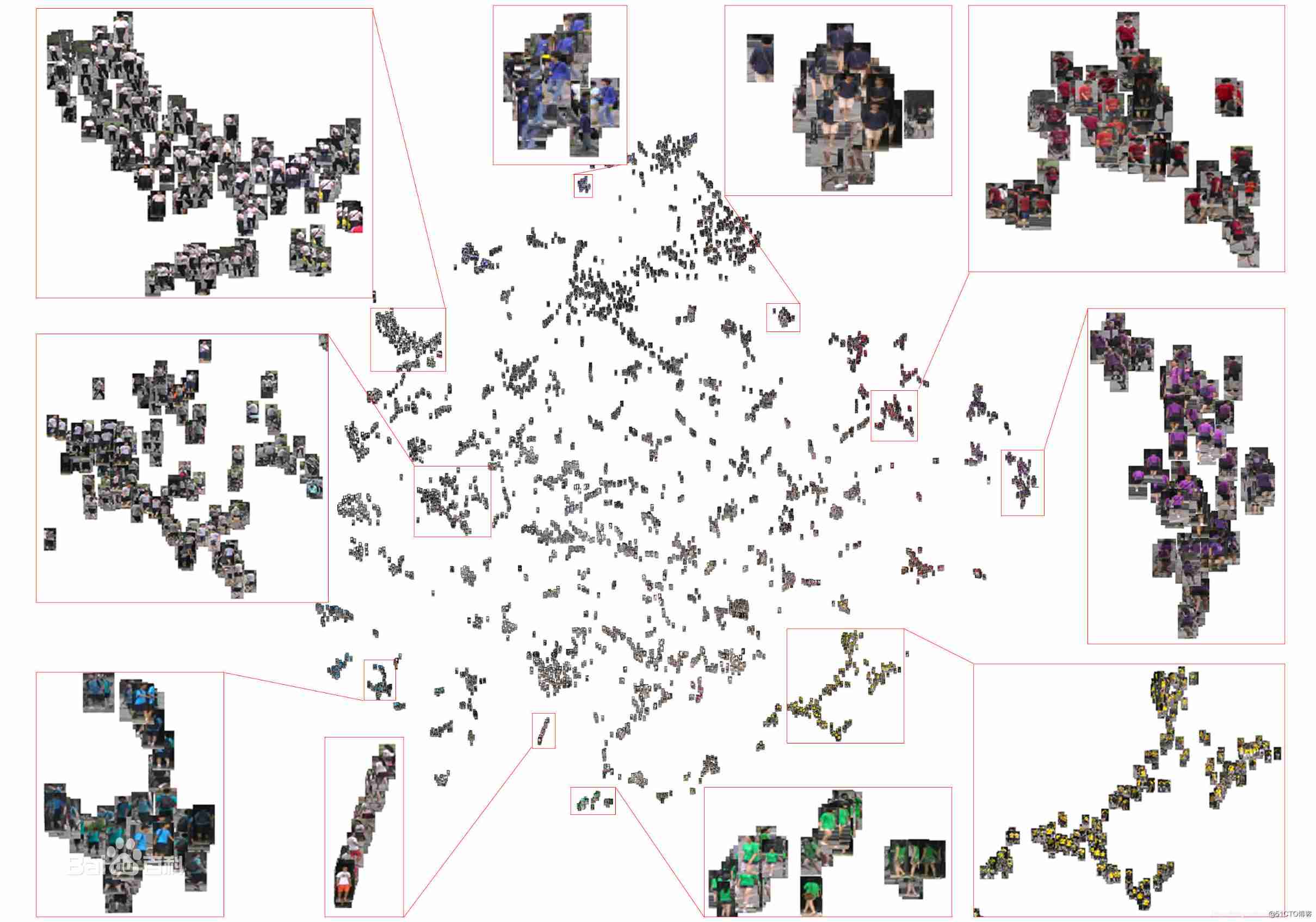
Pedestrian re identification (Reid) - Overview
想跳槽?面试软件测试需要掌握的7个技能你知道吗

How to transform functional testing into automated testing?
What is an index in MySQL? What kinds of indexes are commonly used? Under what circumstances will the index fail?

Fundamentals of digital circuits (III) encoder and decoder
![[pytorch] simple use of interpolate](/img/16/87aa8a49e60801404822fe644e70c8.jpg)
[pytorch] simple use of interpolate
随机推荐
Pedestrian re identification (Reid) - data set description market-1501
Global and Chinese market of portable and handheld TVs 2022-2028: Research Report on technology, participants, trends, market size and share
Common Oracle commands
Leetcode simple question: check whether the numbers in the sentence are increasing
Collection集合与Map集合
Iterators and generators
UCORE lab1 system software startup process experimental report
STC-B学习板蜂鸣器播放音乐2.0
软件测试面试要问的性能测试术语你知道吗?
MySQL数据库(四)事务和函数
安全测试入门介绍
MySQL transactions
Video scrolling subtitle addition, easy to make with this technique
Global and Chinese markets of electronic grade hexafluorobutadiene (C4F6) 2022-2028: Research Report on technology, participants, trends, market size and share
Global and Chinese markets of MPV ACC ECU 2022-2028: Research Report on technology, participants, trends, market size and share
Emqtt distribution cluster and node bridge construction
Query method of database multi table link
Four methods of exchanging the values of a and B
CSAPP家庭作業答案7 8 9章
Public key box



 https://mp.weixin.qq.com/s?__biz=MzU1ODc2NzAxMw==&mid=2247483738&idx=1&sn=32e1bfb005ad0fdf609e86186fb5eaf8&chksm=fc20cf90cb5746865ecc97a3a3c4ef4a4eec8e26c16358f743194e548469c90af1a2dc6c0078#rd
https://mp.weixin.qq.com/s?__biz=MzU1ODc2NzAxMw==&mid=2247483738&idx=1&sn=32e1bfb005ad0fdf609e86186fb5eaf8&chksm=fc20cf90cb5746865ecc97a3a3c4ef4a4eec8e26c16358f743194e548469c90af1a2dc6c0078#rd