当前位置:网站首页>The MySQL database in Alibaba cloud was attacked, and finally the data was found
The MySQL database in Alibaba cloud was attacked, and finally the data was found
2022-07-07 01:09:00 【I pretend to be strong】
Introduce
When I posted my website yesterday , I found that I couldn't go up , Because it uses springboot Written , Stored in Alibaba cloud lightweight ECS , So I went backstage to check the log , I found that I couldn't find the data .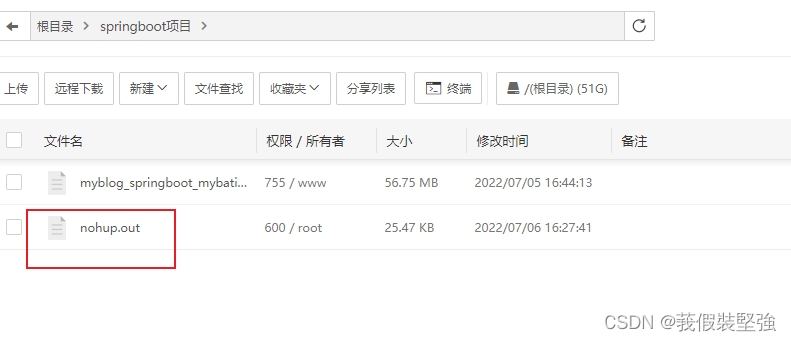
At this time, it was found that there was a problem with the database , Then I opened my own remote database through graphical tools , I found that all the databases I built were missing , I checked for a long time and didn't find out what was going on , At this time, I found Alibaba's customer service after being reminded by others , They assigned me engineers , The engineer helped me determine the scope of the investigation 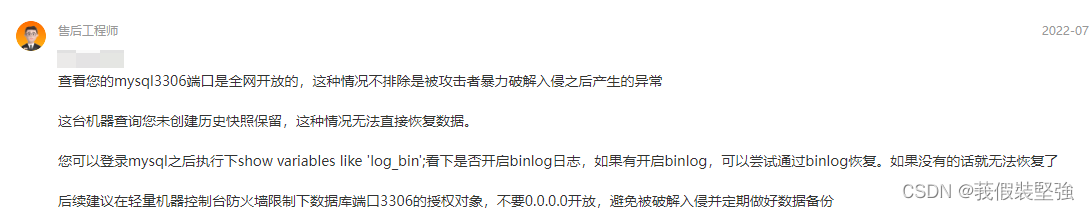
Finally, it was found by checking the binary file that it was attacked by foreign hackers
The following words probably mean to let me spend money to buy back the data, or sell my data , Fortunately, data is not very important .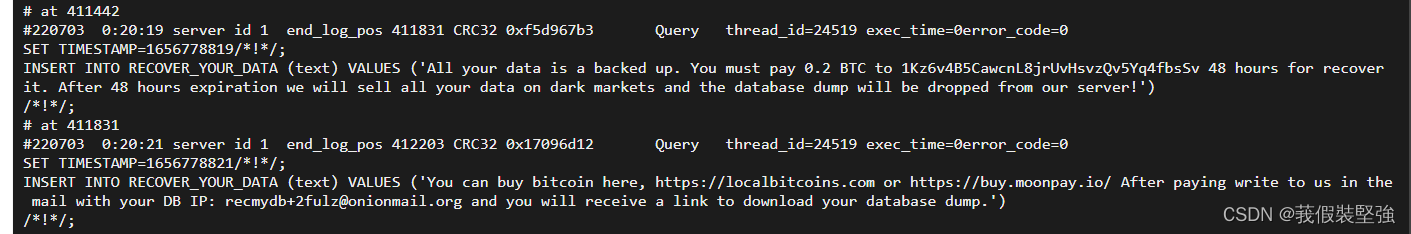
And deleted all my databases
mysql Configuration of
mysql5.6.46 In Alibaba cloud server mysql database , It has been used for less than a year
binlog
What is? binlog
In simple terms , In fact, it is a log that records all addition, deletion and modification operations . We can recover the misoperated data through it , Of course, it can also be used to synchronize master-slave databases .
binlog Three models of :
①statement: Record every piece of modified data sql.
advantage : The log file is small , save io operation , Good performance .
shortcoming : Only record execution statements , Therefore, it is also necessary to ensure that the same results are obtained in the master-slave execution . So the accuracy is poor .
②row: Save which record has been modified .
advantage : It's accurate .
shortcoming : The log file is large .
③mixed: Take into account the advantages of the first two .( I belong to this )
Actual operation :
① see binlog Has it been turned on : If it's not turned on , It's completely cool , There is little chance of recovery , But you can find an attacker to buy back the data
stay mysql Enter command in :SHOW VARIABLES LIKE ‘log_bin’; As shown below 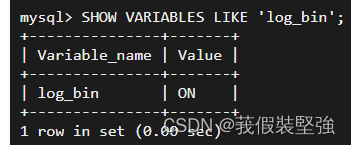
You can see Value yes ON
If it's not turned on , You can refer to the following article ,
https://blog.csdn.net/qq_21996541/article/details/107280382
You can also use fuzzy query , See more information 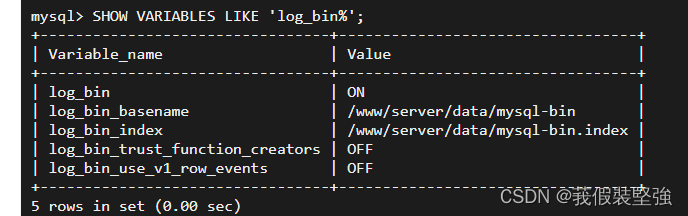
③ see binlog journal :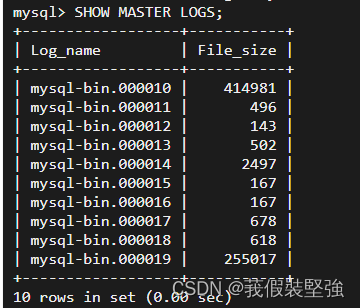
Through the command :SHOW MASTER STATUS; You can check which log file is currently in ,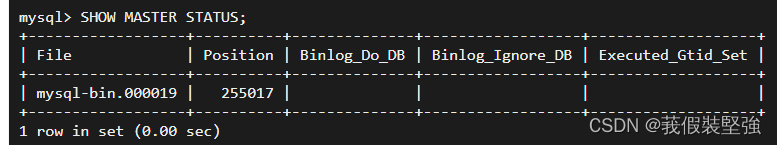
Through the command :FLUSH LOGS; Log files can be truncated , Redirect to a new log file , When we are actually operating , Every operation binlog Before recovery , You need to execute this command , It can ensure that the previous log file will not have new logs in this file , Impact recovery .
There will be another one when you check again after execution 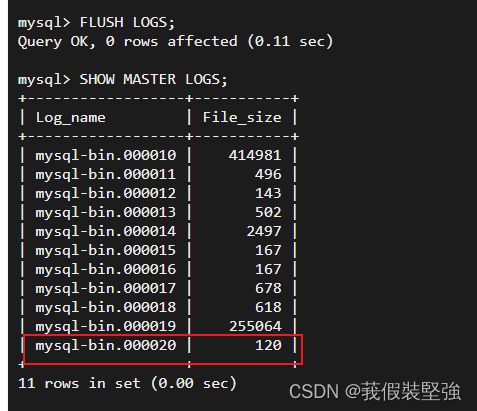
then , According to the order :show variables like ‘%datadir%’; Find the path where these log files are saved 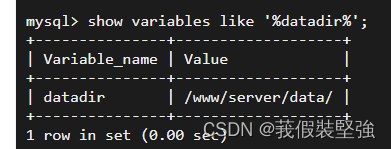
We're on the server ,cd Go to this directory , These files do exist . But these files are binary files , use cat/vi These commands cannot be viewed normally .
We need our mysqlbinlog This order is on the stage ,
First , We enter the command in the server :mysqlbinlog /www/serverl/data/mysql-bin.000020;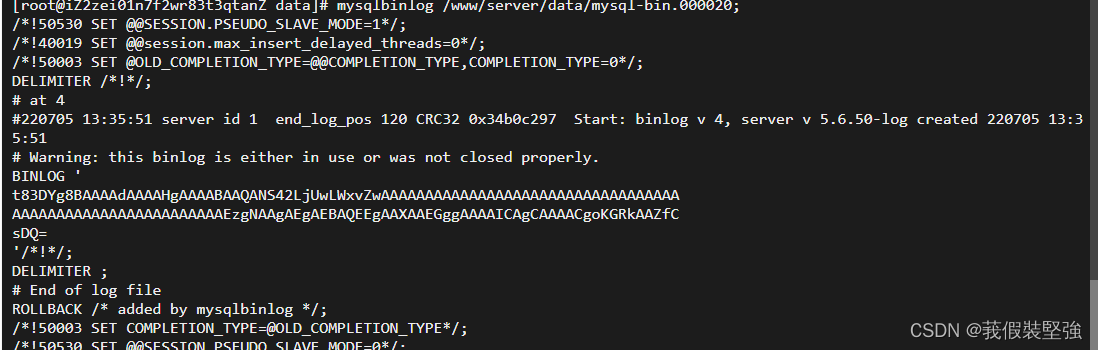
If you enter the above command and an error is reported , You can enter the following command
Enter the command :mysqlbinlog --no-defaults /www/server/data/mysql-bin.000020; You can see the following file information .
However, we can also mysql Enter command in :SHOW BINLOG EVENTS IN 'mysql-bin.000020';
In this way, you can also see binlog Some events recorded in :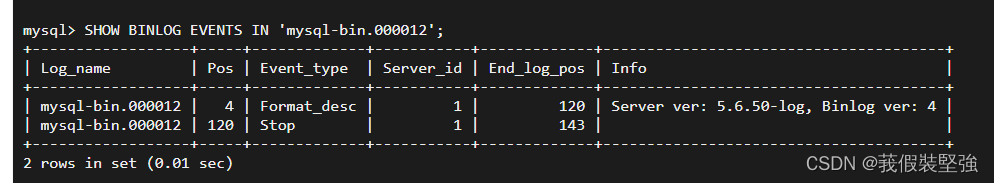
among ,server_id =1, Because we didn't set up , It means the default host ,Pos What I understand is an offset pointer , It is similar to a time node , What operations have been completed at this time node .event_type It means the event type ,xid Business ,query Inquire about ,write rows Means insert data ,delete_rows Delete data , It's easy to recognize .
④ adopt binlog Data recovery :
By looking at , I found my data base in mysql-bin.000010 In this binary file
In this file, you can clearly see that the last operation time before my database was deleted is 7 month 2 Number 10:35:34
The time before deleting the database is 7 month 3 Number 0:20:06, It didn't stop until one o'clock .
Ah , flowers 40 Attack a useless database for more than minutes , I feel a little unworthy , And it's still in the middle of the night .
You can see the name of the deleted database , Yes 8 A database , But for me , The more important one is , A few are built during normal testing , There are few data in it ,
Just for the most important , I must get it back , As long as there is a trace .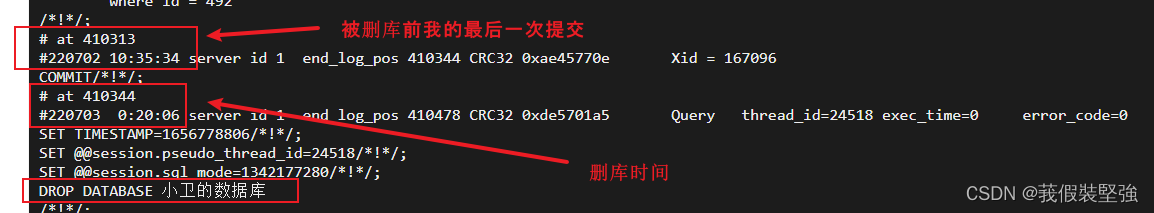
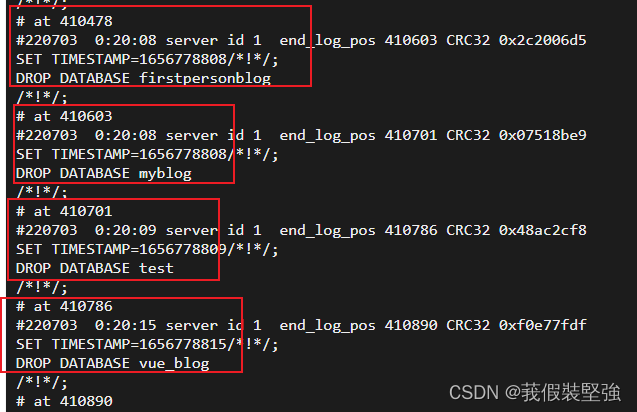
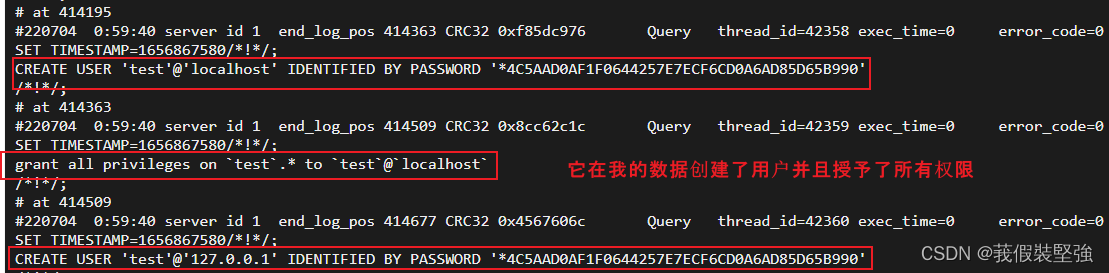
Because for me, what is more important is a database , There are no other data , Not very important , All are restored by restoring the specified database .
Generate by the following command sql file , And then through sql File for recovery
mysqlbinlog --no-defaults --database=xiaochengxu_ks --skip-gtids --stop-position=410161 /www/server/data/mysql-bin.000010 > /xiaochengxu_ks.sql
among xiaochengxu_ks Is the name of the database you want to recover --stop-position=410161 The position before the deleted database corresponds to at Number followed by /www/server/data/mysql-bin.000010 The specific location of the binary file /xiaochengxu_ks.sql Generated from binary files sql The location of the file 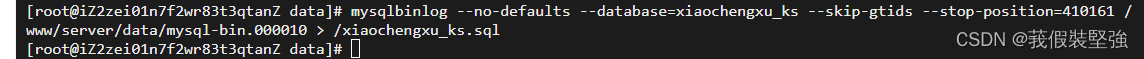
Generate corresponding sql The file is under the change directory 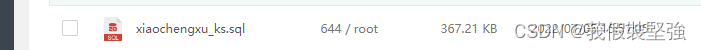
stay MySQL The client command line enters xaiochengxu_ks database , perform source /xiaochengxu_ks.sql Just restore the data .
You can also set the start and end points , But I don't think it's necessary , Through or through time interval
- Start locator
mysqlbinlog --start-position=249 binlog.000006 - End locator
mysqlbinlog --stop-position=249 binlog.000006
summary
I used to think that network security is not very important , That's because it didn't happen to me , These days, I feel its extremely important , Swear to pay attention to network security in the future , At the same time, strengthen your own examples , Avoid recurrence
边栏推荐
- 【批处理DOS-CMD命令-汇总和小结】-跳转、循环、条件命令(goto、errorlevel、if、for[读取、切分、提取字符串]、)cmd命令错误汇总,cmd错误
- Periodic flash screen failure of Dell notebook
- Return to blowing marshland -- travel notes of zhailidong, founder of duanzhitang
- Atomic in golang and CAS operations
- Anfulai embedded weekly report no. 272: 2022.06.27--2022.07.03
- [hfctf2020]babyupload session parsing engine
- 动态规划思想《从入门到放弃》
- ZABBIX 5.0: automatically monitor Alibaba cloud RDS through LLD
- 实现mysql与ES的增量数据同步
- 迈动互联中标北京人寿保险,助推客户提升品牌价值
猜你喜欢
![[batch dos-cmd command - summary and summary] - string search, search, and filter commands (find, findstr), and the difference and discrimination between find and findstr](/img/4a/0dcc28f76ce99982f930c21d0d76c3.png)
[batch dos-cmd command - summary and summary] - string search, search, and filter commands (find, findstr), and the difference and discrimination between find and findstr
线段树(SegmentTree)
资产安全问题或制约加密行业发展 风控+合规成为平台破局关键
.class文件的字节码结构
![[Niuke] [noip2015] jumping stone](/img/9f/b48f3c504e511e79935a481b15045e.png)
[Niuke] [noip2015] jumping stone
Js+svg love diffusion animation JS special effects

筑梦数字时代,城链科技战略峰会西安站顺利落幕
Activereportsjs 3.1 Chinese version | | | activereportsjs 3.1 English version

城联优品入股浩柏国际进军国际资本市场,已完成第一步
![[Batch dos - cmd Command - Summary and Summary] - String search, find, Filter Commands (FIND, findstr), differentiation and Analysis of Find and findstr](/img/4a/0dcc28f76ce99982f930c21d0d76c3.png)
[Batch dos - cmd Command - Summary and Summary] - String search, find, Filter Commands (FIND, findstr), differentiation and Analysis of Find and findstr
随机推荐
The printf function is realized through the serial port, and the serial port data reception is realized by interrupt
[牛客] B-完全平方数
golang中的WaitGroup实现原理
动态规划思想《从入门到放弃》
Windows installation mysql8 (5 minutes)
再聊聊我常用的15个数据源网站
[software reverse automation] complete collection of reverse tools
详解OpenCV的矩阵规范化函数normalize()【范围化矩阵的范数或值范围(归一化处理)】,并附NORM_MINMAX情况下的示例代码
tensorflow 1.14指定gpu运行设置
Threejs image deformation enlarge full screen animation JS special effect
Dell筆記本周期性閃屏故障
.class文件的字节码结构
Activereportsjs 3.1 Chinese version | | | activereportsjs 3.1 English version
windows安装mysql8(5分钟)
Let's talk about 15 data source websites I often use
第四篇,STM32中断控制编程
from . cv2 import * ImportError: libGL. so. 1: cannot open shared object file: No such file or direc
Learning notes 5: ram and ROM
Trace tool for MySQL further implementation plan
一行代码实现地址信息解析