author |Trung Anh Dang
compile |Flin
source |towardsdatascience

Thanks to the rapid development of computer science and electronic technology , Now , In terms of market share , Face recognition is becoming the second largest biometric authentication method in the world after fingerprint .
Every day , More and more manufacturers are adding face recognition to their products , Apple, for example, uses face recognition technology , Banks use eKYC The solution goes through the induction process .
The main purpose of face recognition research is to improve the performance of verification and recognition tasks , On the contrary , In the past, there is little research on the security vulnerability of face recognition system , Until recent years , People are beginning to focus on different types of face recognition attacks , It includes testing whether a biometric comes from a living person or a photograph .
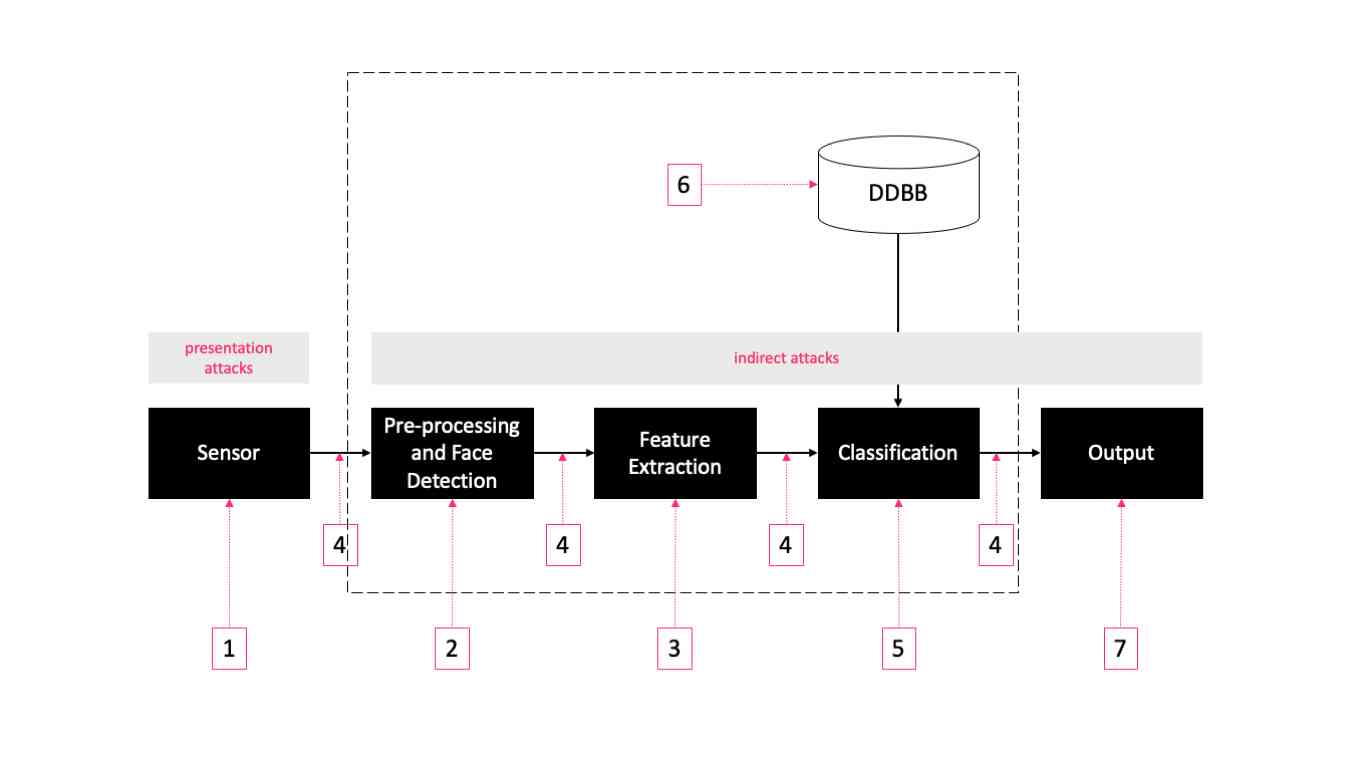
Two kinds of attacks used on face recognition systems
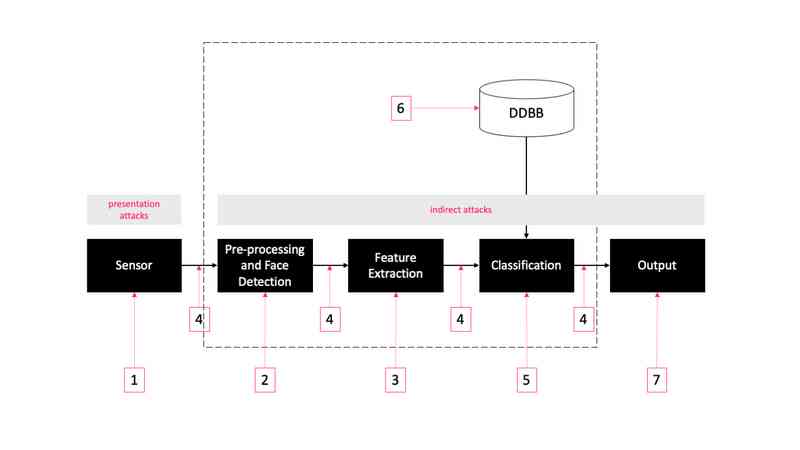
As shown in the figure above , There are seven modules and points that can be targeted , They fall into two types : Demonstrate attacks and indirect attacks .
Demonstrate the attack
Demonstrate the attack at the sensor level (1) Conduct , You don't have to access the system .
Demonstration attacks are related to purely biometric vulnerabilities . In these attacks , The intruder uses some kind of artifact , for example , Photo , Mask , Synthetic fingerprint or printed iris image , Or trying to mimic the behavior of real users ( For example, gait , Signature ) Fraudulent access to biometric systems .
because “ Biometrics are no secret ”, The attacker is aware of this reality , That is, it exposed a lot of biological characteristics data , It shows people's faces , eyes , Voice and behavior , So they use these information resources to try to trick the face recognition system with the following example .
- The attacker uses the photo of the user to be impersonated .
- They use user videos to mimic .
- Hackers can build and use the 3D Model , for example , Super realistic mask
We use anti spoofing techniques to prevent these attacks .
Indirect attack
It can be in the database , Indirect attack on matched communication channels, etc (2-7). In this type of attack , The attacker needs to access the inside of the system .
It can be done through “ classic ” Technology related to network security ( Not with biometrics ) Related technology to prevent indirect attacks , So in this article we will not discuss .
Attack style
If you don't implement demo attack detection , Most of the latest facial biometric systems are vulnerable to simple attacks .
Usually , You can present a picture of the target person to the camera , Video or 3D Mask the face recognition system . Or make-up or plastic surgery . however , Due to the high exposure rate of high resolution digital camera 、 The cost is low , Using photos and videos is the most common type of attack .
- Photo attack : Photo attacks include displaying photos of the attacked identity on the sensors of the face recognition system .
- Video attack : An attacker can play a legitimate user's video on any device that copies the video , And then it's presented to the sensor / The camera .
- 3D Masked attack : In this type of attack , Attackers construct facial 3D Rebuild and present it to the sensor / The camera .
- Other attacks : Make up , Operation

Anti spoofing technology
Because most face recognition systems are vulnerable to spoofing attacks . therefore , In order to design a secure face recognition system in real scenes , Start with the initial planning of the system , Anti spoofing technology should be the top priority .
Because facial recognition systems try to distinguish real users , Therefore, there is no need to determine whether the biometric sample provided to the sensor is true or false . We can achieve them in four different ways .
sensor
We use sensors to detect real-time features in the signal .
Special hardware
With dedicated hardware ( for example 3D The camera ) To detect signs of life , But it's not always possible to deploy .
Challenge response method
Use the challenge response method , The demonstration attack can be detected by asking the user to interact with the system in a specific way .
- smile
- Sad or happy facial expressions
- Head movements
Algorithm
Using the following recognition algorithm has the ability to resist attacks in essence .
Mirror feature projection : First , By depicting the mirror feature space corresponding to the real image , On this basis, we learn the projection of real data and false data . secondly , Training according to real projection SVM Model , And then use 3D Mask projection and print photo projection are used as anti deception models for detection simulation .
Deep feature fusion : Through in-depth study of the importance of face image color feature information for face detection , Using deep convolution neural networks ResNet and SENet The network structure of deep feature fusion is constructed , Effectively train the relevant face anti deception data .
Image quality assessment : The method is based on the combination of image quality metrics . The solution compares the original image with the processed image .
Deep learning : This method is based on multi input architecture , The architecture combines a pre trained convolutional neural network model with a local binary pattern descriptor .
Biometric authentication methods
https://towardsdatascience.co...
How to implement ?
We can use anti spoofing technology to build demonstration attack detection system (PAD), And integrate it with the face recognition system .

Using this method , The anti spoofing system makes the decision first , Only after it's confirmed that the samples came from living people , The face recognition system will process it .
Link to the original text :https://towardsdatascience.co...
Welcome to join us AI Blog station :
http://panchuang.net/
sklearn Machine learning Chinese official documents :
http://sklearn123.com/
Welcome to pay attention to pan Chuang blog resource summary station :
http://docs.panchuang.net/