1、WebSocket
WebSocket, Everybody knows , Since the name contains Socket, So and Socket There must be little difference , Yes , You're not mistaken , There's no big difference .
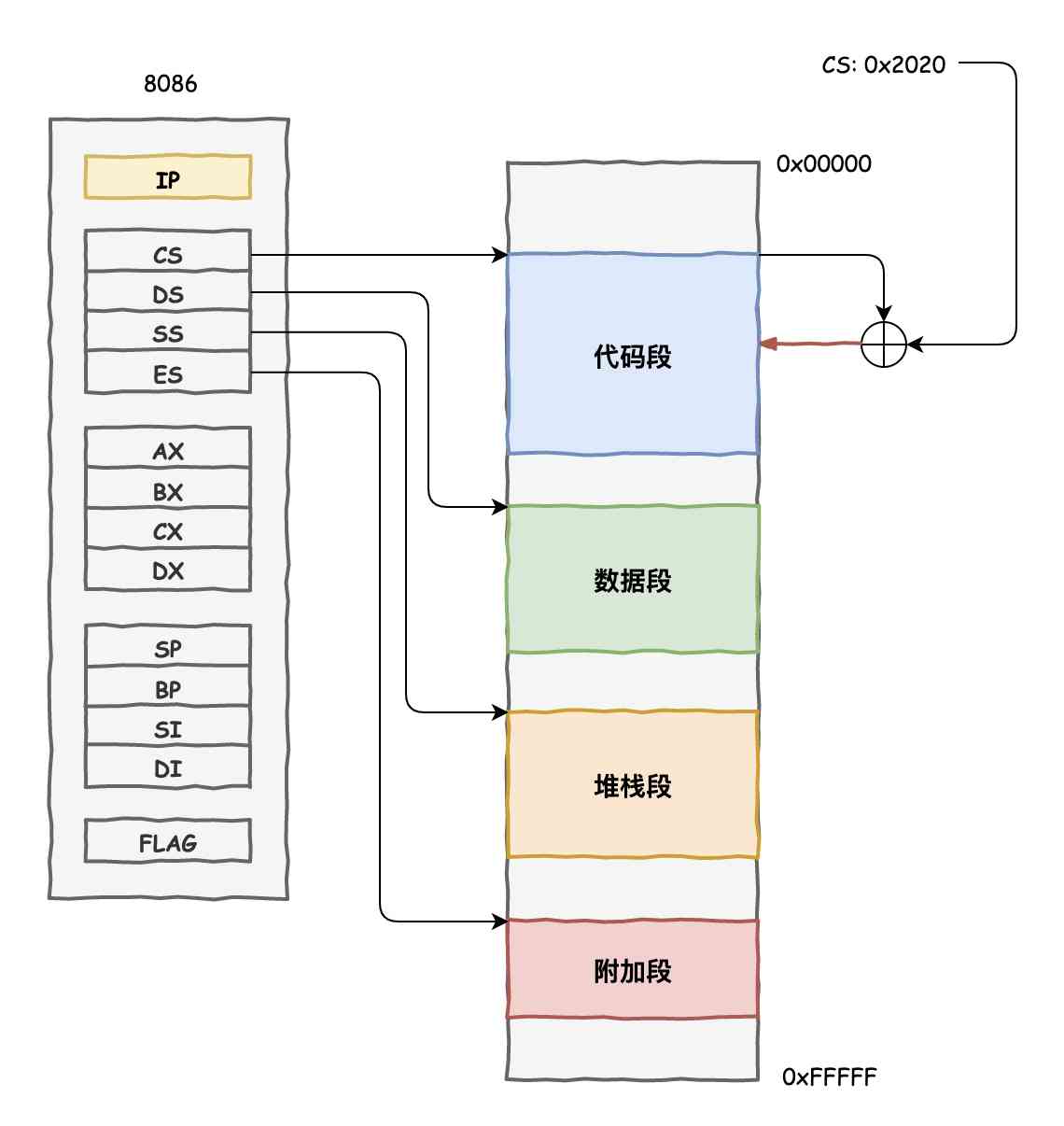
In network programming , Our general agreement is based on TCP/IP,WebSocket No exception . and HTTP equally , He also has his own head and specific data .
Let's see .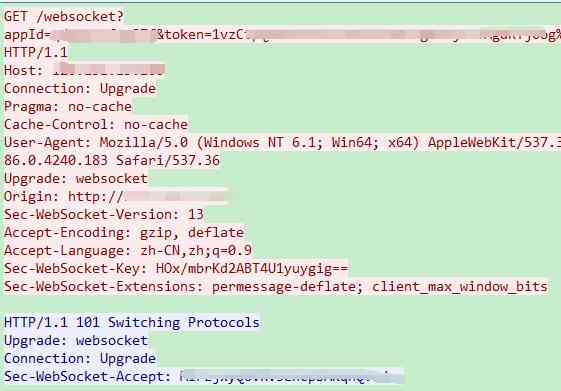
This is a ,websocket Initiated connection , First one http Request , Tell the server , I want to send WebSocket The connection of , The server , Return to a paragraph ok. You can continue to use this connection later , Carry out basic WebSocket Request the .
Actually ,WebSocket And ordinary Socket There's no difference , All are send,receive, Sending and receiving data , It's just that the data format needs special treatment . Let's explain .
WebSocket The data format sent by ( Receiving and sending are the same ):
Let's have a web map :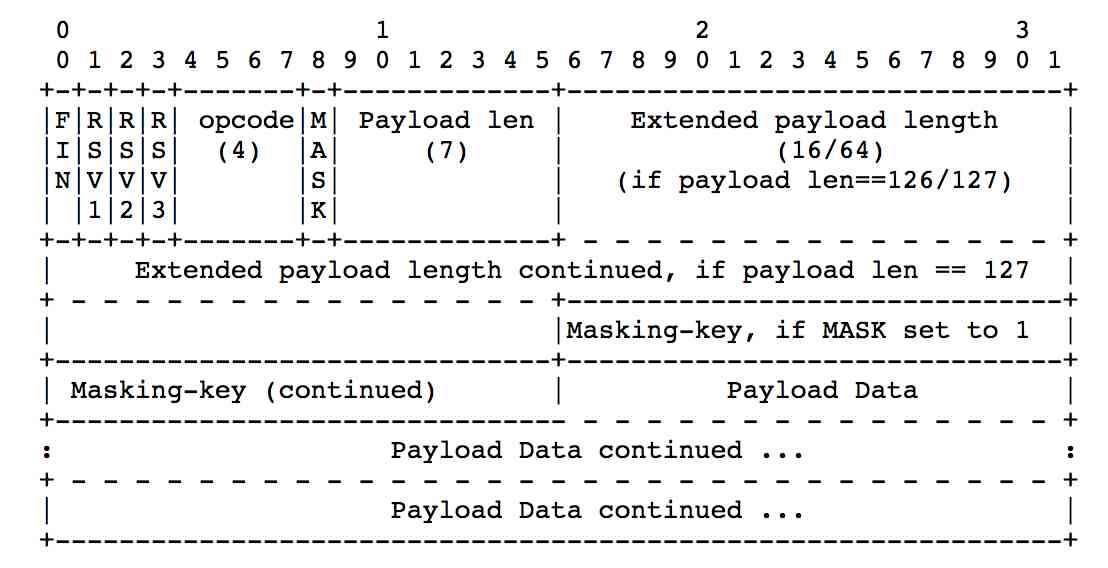
Here's an online post : Explain it. :
FIN, To specify Frame Is it a Message In the end Frame( I said one before Message There may be more Frame form )RSV1-3, must yes 0, Unless an extension defines the meaning of a nonzero value .Opcode, This is more important , The following values are defined by the protocol-
%x0 denotes a continuation frame
-
%x1 It means a text frame
-
%x2 It means a binary frame
-
%x3-7 are reserved for further non-control frames
-
%x8 Indicates that the connection is closed
-
%x9 Express ping ( Heart rate detection is related to , The back can speak )
-
%xA Express pong ( Heart rate detection is related to , The back can speak )
-
%xB-F are reserved for further control frames
-
Mask, This is to indicate “payload data” Whether the mask is calculated . This and the followingMasking-keyof ( If =0, There is no need to calculate the result : The result is clear , If it is =1,name With the next four bytes of masking-key, To handle decoding operations . Byte XOR by bit , Four at a time .)
if(mask == 1){
byte[] payload = xxxx; // It is assumed here that
byte[] mask_key = new byte[4];// It is assumed here that
for(int i=0;i<payload.Count;i++){
payload[i] = (byte)(payload[i] ^ mask_key[i%4]);
}
// So you can decode the plaintext
}else{
// In the case of plaintext ,2 After the byte or 4 byte ,12 After the byte is the specific data ,( The truth , According to the specific data ).
}
Payload len, The total length of the data , There are three situations [<126,>126 && <= 65535,> 65535], These three situations , It's not the same , The first one is , Default footprint ( It itself ),( The following bytes are data or masking-key(mask by 1 Only then masking-key))
Masking-key, Encryption functionPayload data, The data that the frame really wants to send , It can be any length , But although theoretically there is no limit to the size of the frame , But you can't send too much data , Otherwise, it will lead to the inability to Efficient use of network bandwidth , As mentioned above Websocket Provide slicing .
2、Probuf
Our network often encodes and transmits data , In general, some of the ways we use back content original text ,xml,json, And there's what we're all about probuf 了 .
What are the benefits of this coding , It greatly reduces the consumption of network bandwidth , At the same time, it reduces the time consumption of data analysis .
Let's have another wave of network graphics , The arrangement of data .
chart 1: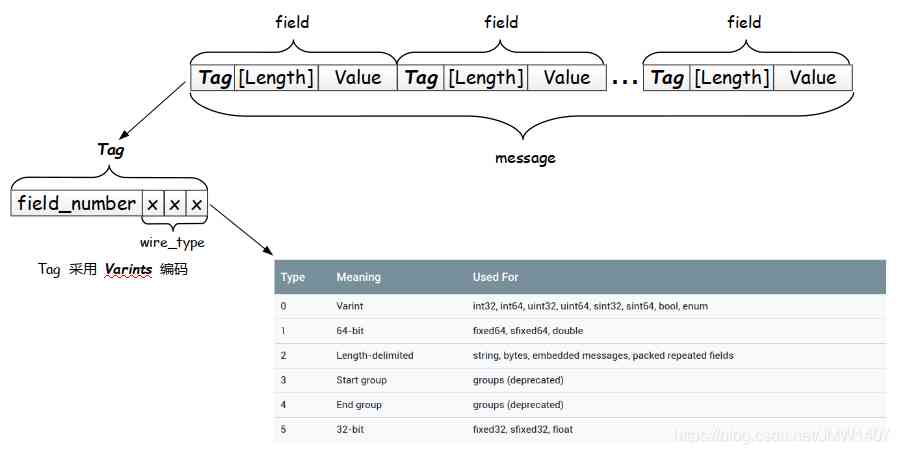
obvious , You can see it here ,Tag Take a place ,length Take a place , General situation , If it's long data ,namelength It may take up more than one byte . according to length The first decision of .(length Also the first one is to identify whether the second direct join calculation is needed , One analogy , Here's an explanation :
Varint: A kind of , Put the first place , As a condition of judgment , Come on length The way the calculation is done .
0-0111 1111, A byte can represent a range : [0,0x7f] Size ,
1000 0000 - 0000 0001 ----- 1111 1111 - 0111 1111 , Two bytes can represent the range :[1<<7, 0x7f<<7 + 0x7f]
1000 0000 - 0000 0000 - 0000 0001 ----- 1111 1111 - 1111 1111 - 0111 1111 , Three bytes can represent the range :[1 << 7 * 2, 0x7f<<7 <<7 + 0x7f<<7 + 0x7f]
So generally speaking , You just need a small number of direct mail to process most of the data .
So was born probuf Description or parsing file of :( Have a chestnut )
message DownStreamMessages { repeated DownStreamMessage list = 1; required int64 syncTime = 2; optional bool finished = 3; } message DownStreamMessage { required string fromUserId = 1; required ChannelType type = 2; optional string groupId = 3; required string classname = 4; required bytes content = 5; required int64 dataTime = 6; required int64 status = 7; optional int64 extra = 8; optional string msgId = 9; optional int32 direction = 10; optional int32 plantform =11; optional int32 isRemoved = 12; optional string source = 13; optional int64 clientUniqueId = 14; optional string extraContent = 15; } enum ChannelType { PERSON = 1; PERSONS = 2; GROUP = 3; TEMPGROUP = 4; CUSTOMERSERVICE = 5; NOTIFY = 6; MC=7; MP=8; }
There are several key words to deal with :(bool and enum They are all treated as integers ), After field = 1; = 2 On the surface filed_number. value .
required It's usually necessary
optional Not a must
repeated Repetitive , A representation set .
Here is a picture of the net :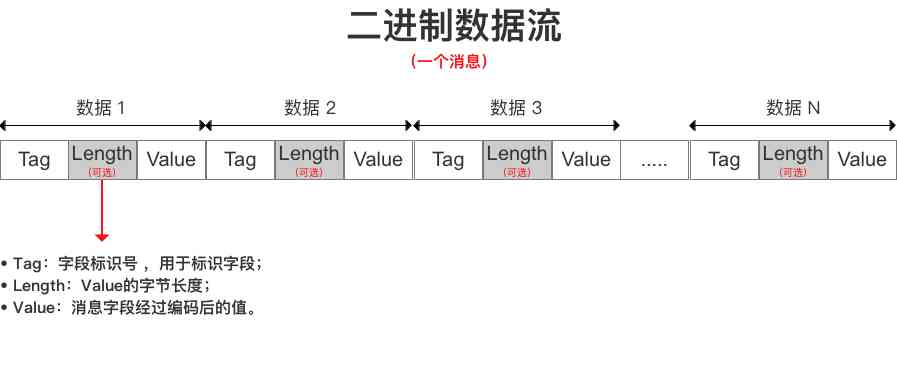
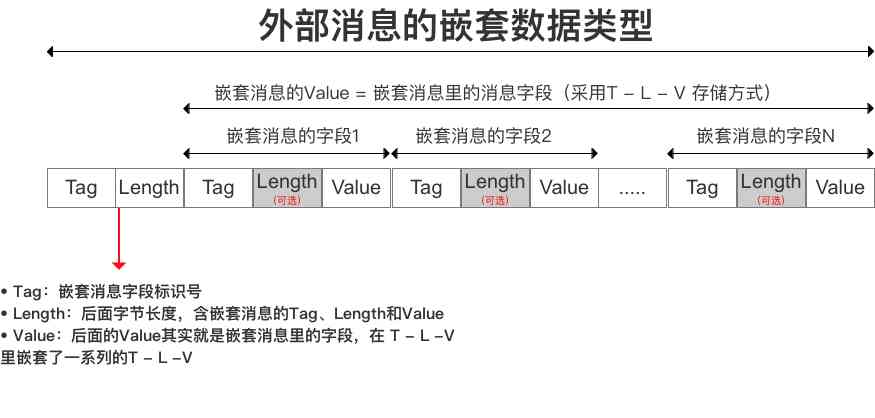
Encoding data length .
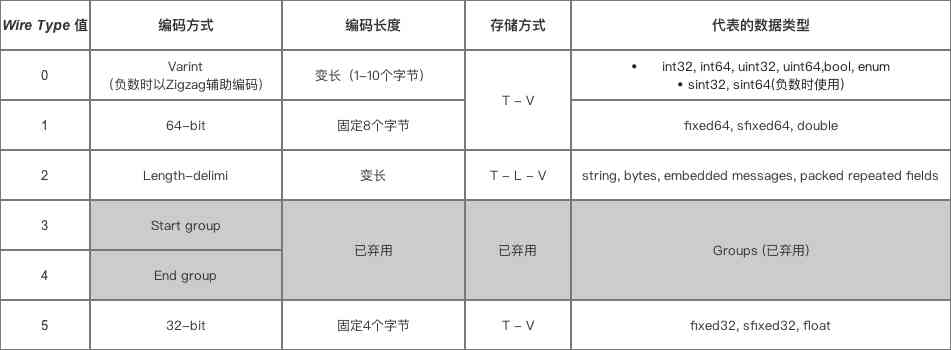
The figure above shows the data The arrangement is regular , The data is compact .
In particular repeat The situation of ,repeat hinder length It refers to the number of bytes needed to read this . Not the number of repetitions .
Reference resources :https://juejin.im/post/6844903582290935822
Reference resources :https://blog.csdn.net/carson_ho/article/details/70568606
Reference resources :https://blog.csdn.net/JMW1407/article/details/107197938/