当前位置:网站首页>Four problems and isolation level of MySQL concurrency
Four problems and isolation level of MySQL concurrency
2022-07-03 12:50:00 【Mcc_ mingchao】
What are the problems of concurrent transactions
In a typical application , Multiple transactions run concurrently , Often operate the same data to complete their own tasks ( Multiple users operate on the same data ). Concurrency is necessary , But it may cause the following problems .
Dirty reading (Dirty read): When a transaction is accessing data and modifying the data , This modification has not yet been committed to the database , At this time, another transaction also accesses the data , And then I used this data . Because of this Data is data that has not been submitted , So the data read by another transaction is “ Dirty data ”, basis “ Dirty data ” The operation may not be correct .( Read uncommitted data )
Missing changes (Lost to modify): When a transaction reads a data , Another transaction also accesses the data , After modifying the data in the first transaction , The second transaction also modifies the data . In this way, the modification result in the first transaction will be lost , So it's called lost modification . for example : Business 1 Read data from a table A=20, Business 2 Also read A=20, Business 1 modify A=A-1, Business 2 Also modify A=A-1, final result A=19, Business 1 The modification of is lost .
It can't be read repeatedly (Unrepeatableread): Reading the same data multiple times in a transaction . Before the end of the business , Another transaction also accesses the data . that , Between two reads in the first transaction , Due to the modification of the second transaction, the data read by the first transaction twice may be different . This happens when the data read twice in a transaction is different , So it's called unrepeatable reading .( The period of repeated reading is modified, resulting in different data read twice )
Fantasy reading (Phantom read): Unreal reading is similar to nonrepeatable reading . It happens in a transaction (T1) Read a few lines of data , Then another concurrent transaction (T2) When some data is inserted . In the subsequent query , The first thing (T1) There will be more records that don't exist , It's like an illusion , So it's called Unreal reading .( When reading multiple rows of data, the data is inserted by other transactions )
The difference between nonrepeatable reading and unreal reading :
The key point of non repeatable reading is to modify, such as reading a record many times and finding some columns Value is modified , The point of fantasy reading is Add or delete For example, read a record many times and find that the number of records increases or decreases .
What are the transaction isolation levels ?
SQL The standard defines four isolation levels :
READ-UNCOMMITTED( Read uncommitted ): Lowest isolation level , Allow read of uncommitted data changes , Can cause dirty reading 、 Phantom or unrepeatable reading .
READ-COMMITTED( Read committed ): Allow to read data submitted by concurrent transactions , Can prevent dirty reading , But phantom or unrepeatable reads can still occur .
REPEATABLE-READ( Repeatable ): Multiple reads of the same field are consistent , Unless the data is modified by the transaction itself , Can prevent dirty and unrepeatable read , But phantom reading can still happen .
SERIALIZABLE( Serializable ): Highest isolation level , Completely obey ACID Isolation level . All transactions are executed one by one , In this way, there is no interference between transactions , in other words , This level prevents dirty reads 、 Unrepeatable reading and phantom reading .
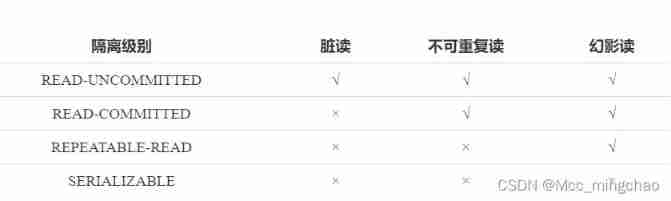
- MySQL InnoDB The default isolation level supported by the storage engine is REPEATABLE-READ( Can be reread )InnoDB The storage engine uses... By default REPEAaTABLE-READ( Can be reread ) There will be no loss of performance .
边栏推荐
- 剑指Offer04. 二维数组中的查找【中等】
- Differences between initial, inherit, unset, revert and all
- node的ORM使用-Sequelize
- What is more elegant for flutter to log out and confirm again?
- Do you feel like you've learned something and forgotten it?
- Bert running error: attributeerror: module'tensorflow contrib. tpu' has no attribute 'InputPipelineConfig'
- [exercice 7] [principe de la base de données]
- 剑指Offer03. 数组中重复的数字【简单】
- Official website of Unicode query
- JVM memory model
猜你喜欢

剑指Offer10- I. 斐波那契数列

Grid connection - Analysis of low voltage ride through and island coexistence

基于同步坐标变换的谐波电流检测
Use bloc to build a page instance of shutter

TOGAF认证自学宝典V2.0
最新版抽奖盲盒运营版
Detailed explanation of the most complete constraintlayout in history

(latest version) WiFi distribution multi format + installation framework

Sword finger offer06 Print linked list from end to end

最新版盲盒商城thinkphp+uniapp
随机推荐
How to convert a decimal number to binary in swift
Integer case study of packaging
【计网】第三章 数据链路层(2)流量控制与可靠传输、停止等待协议、后退N帧协议(GBN)、选择重传协议(SR)
[review questions of database principles]
低代码平台国际化多语言(i18n)技术方案
Nodejs+Express+MySQL实现登陆功能(含验证码)
[comprehensive question] [Database Principle]
剑指Offer07. 重建二叉树
Export the entire Oracle Database
十条职场规则
Glide 4.6.1 API initial
Method overloading and rewriting
启用MemCached的SASL认证
并网-低电压穿越与孤岛并存分析
Xctf mobile--rememberother problem solving
The latest version of lottery blind box operation version
alright alright alright
elastic_ L01_ summary
Swift Error Handling
Kubectl_ Command experience set