当前位置:网站首页>Wireshark data analysis and forensics a.pacapng
Wireshark data analysis and forensics a.pacapng
2022-07-03 01:27:00 【Lonely fish】
Wireshark( Pre name Ethereal) Is a network packet analysis software . The function of network packet analysis software is to retrieve network packets , At the same time, the most detailed network packet data is displayed .Wireshark Use WinPCAP As an interface , Data message exchange with network card directly .
Suppose you are a network security engineer , Need to analyze the data of a company , Analyze the operations performed by hackers to obtain computer permissions , In this chapter, we mainly analyze the key data by analyzing the case data package .
A.pacapng Data packets
1. Through analysis windows 7 Packets on the desktop A.pcapng, Find the password for the hacker to connect the Trojan horse in one sentence , Use this password as FLAG Submit ;
Screening
httpagreementctrl+FSearch for keyword@eval

2. Through analysis windows 7 Packets on the desktop A.pcapng, View call upload one sentence Trojan file ;
aaaa.php
3. By analyzing the data package A.pcapng, Find the range of network segments scanned by hackers (IP In between ”,” separate , example :192.168.1.1-192.168.1.2) Use this range as FLAG Submit ;
Screening
arpagreement spotInfoSort out Here we are31But it was swept30Start connecting the Trojan horse To be specific, try again during the competition .


192.168.10.10-192.168.10.30
4. By analyzing the data package A.pcapng, What is the password to find the domain server , Use this password as FLAG Submit ;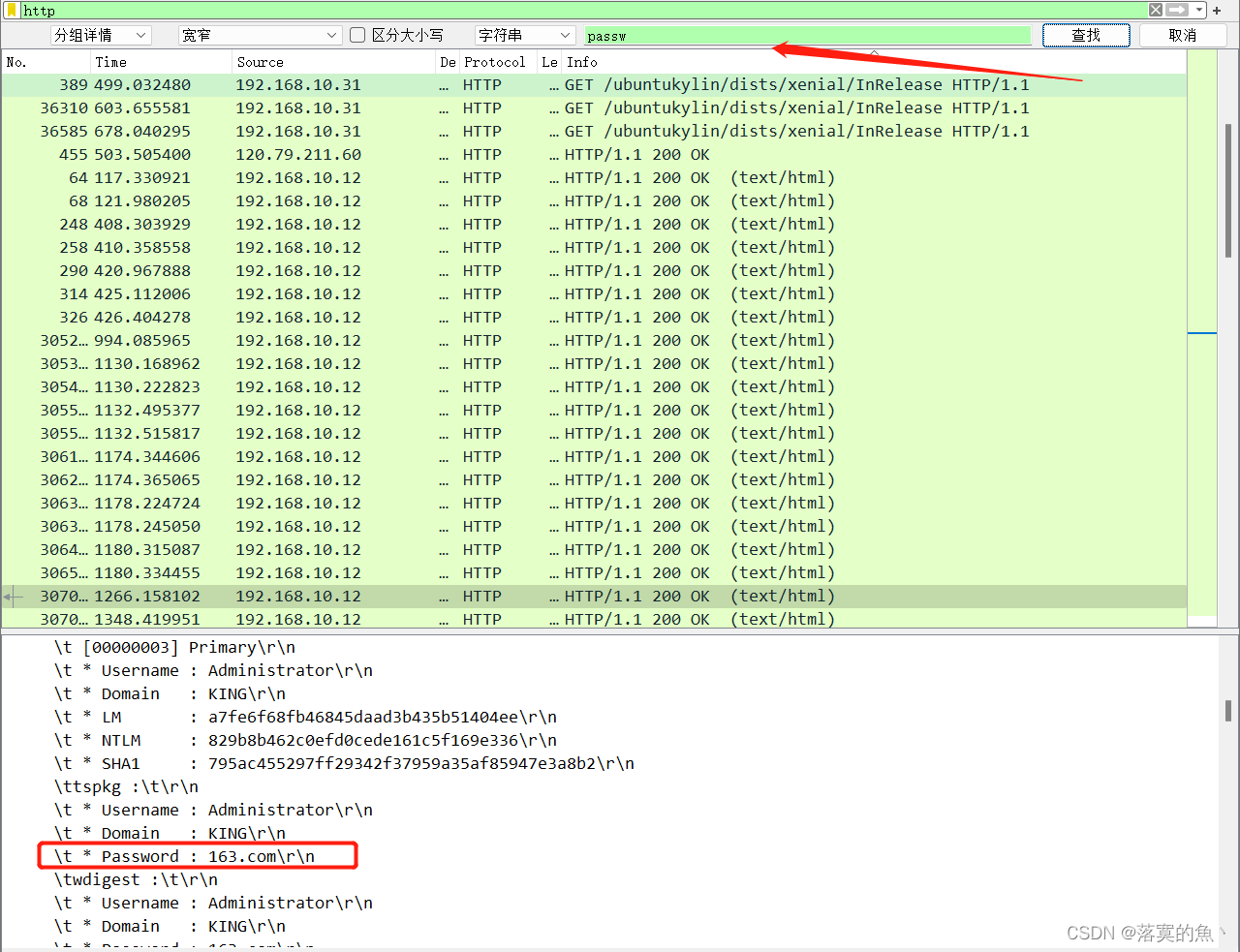
163.com
5. By analyzing the data package A.pcapng, Find the file uploaded by the hacker and use the name as FLAG Submit ;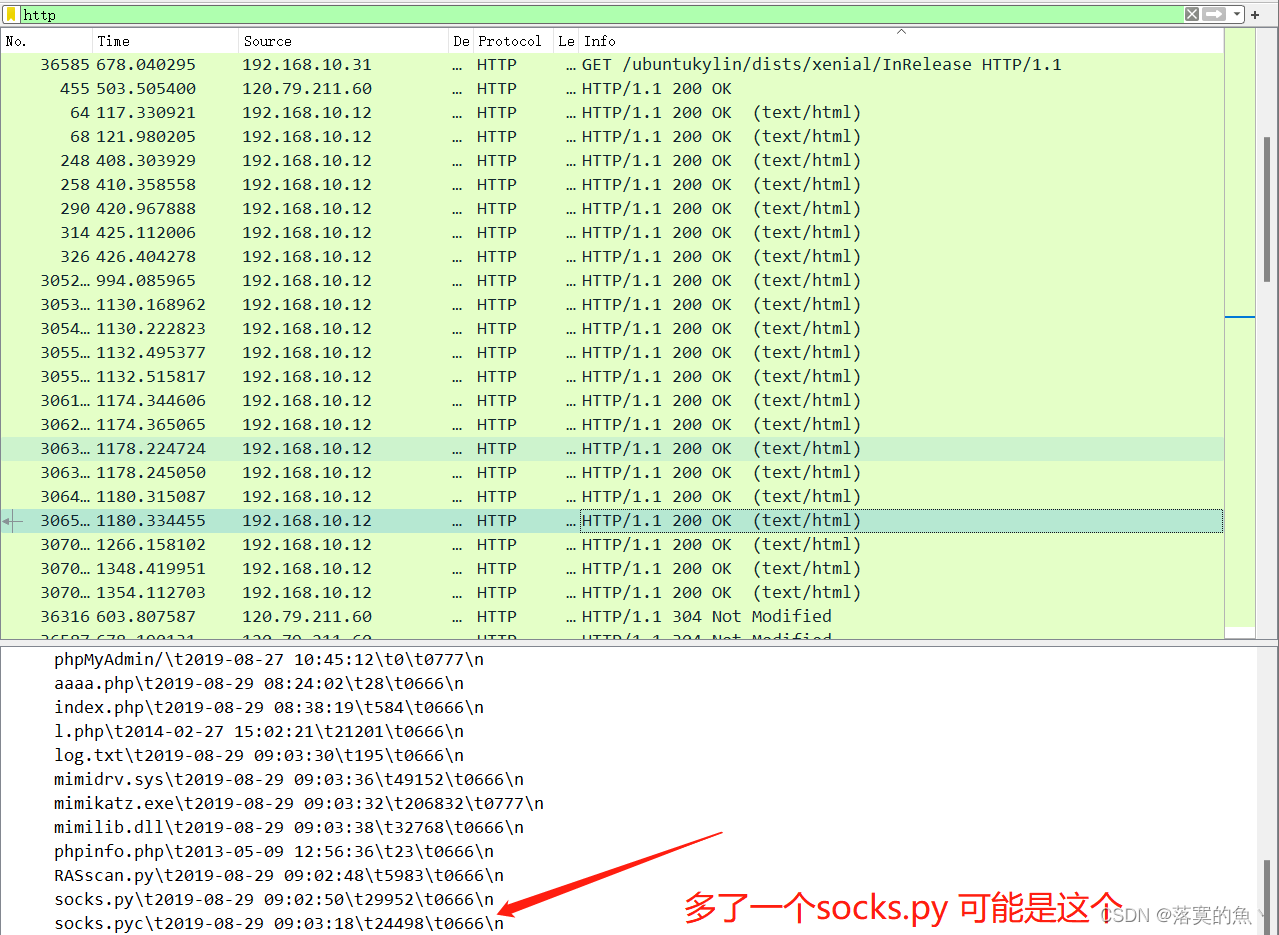
6. By analyzing the data package A.pcapng, Find out what the hacker downloaded , Treat the contents of this file as FLAG Submit ;
Put the packet into
kailiUsebinwalk -eTo separate
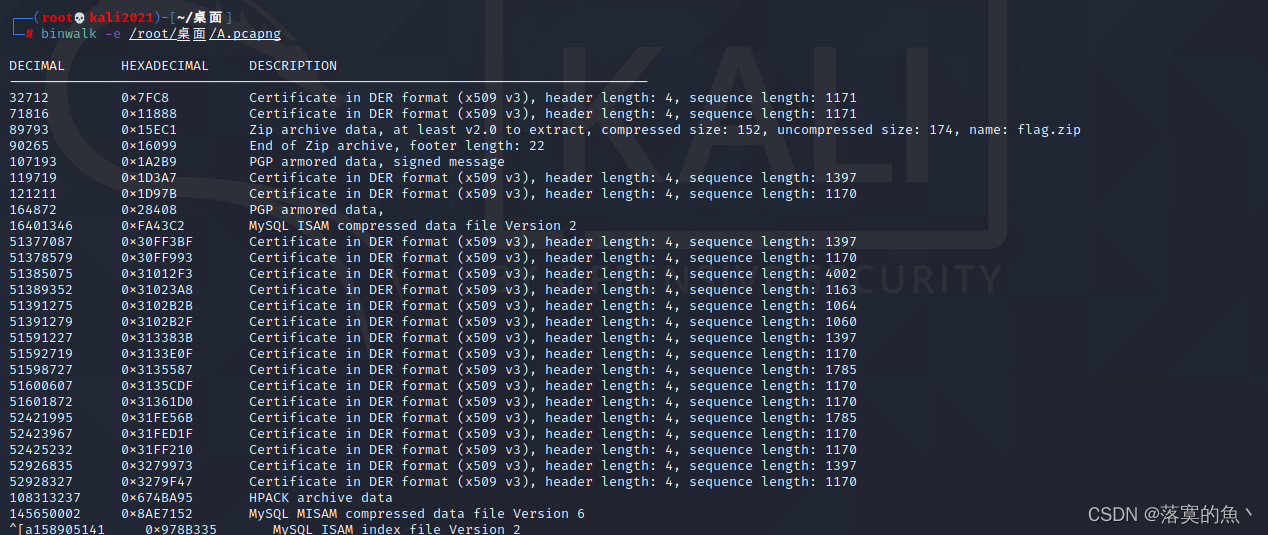
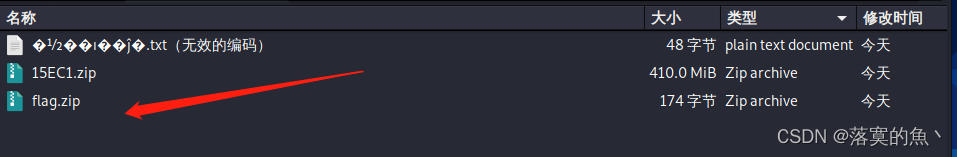
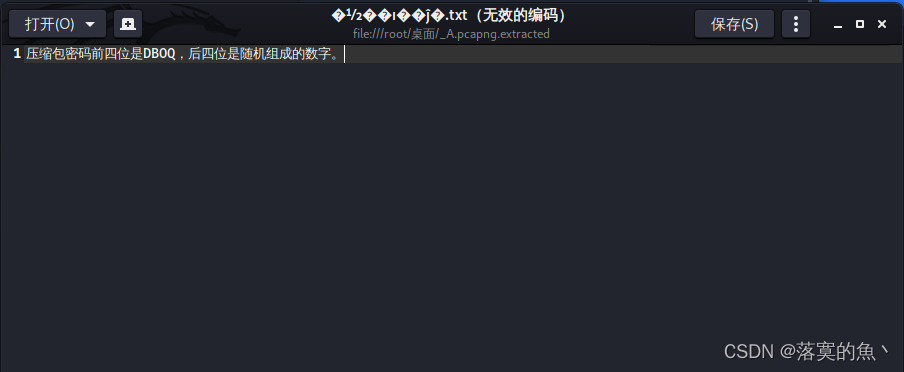
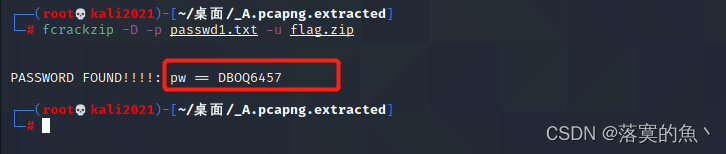
Use crunch Make a dictionary and insert it into the current directory passwd1.txt Next Use fcrackzip Blast zip The password for encrypting the file is DBOQ6457
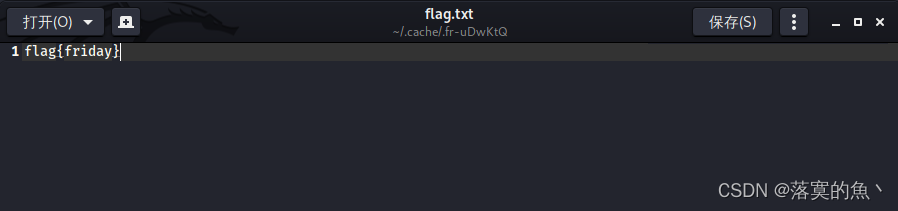
flag{friday}
If you don't know the place, you can confide in the blogger , Welcome to exchange !! Communication group :603813289( Just built )
Finally, if it helps you I hope you can support the blogger for the third company , Your support is my greatest motivation , Reprint please indicate the original link support original thank you !
边栏推荐
- MySQL foundation 04 MySQL architecture
- Now that the teenager has returned, the world's fireworks are the most soothing and ordinary people return to work~
- MySQL --- 数据库查询 - 基本查询
- 信息熵的基础
- [principles of multithreading and high concurrency: 2. Solutions to cache consistency]
- Why can't the start method be called repeatedly? But the run method can?
- 数学知识:能被整除的数—容斥原理
- Concise analysis of redis source code 11 - Main IO threads and redis 6.0 multi IO threads
- 18_ The wechat video number of wechat applet scrolls and automatically plays the video effect to achieve 2.0
- Druid database connection pool
猜你喜欢

Expérience de recherche d'emploi d'un programmeur difficile

Correctly distinguish the similarities and differences among API, rest API, restful API and web service
信息熵的基础
Soft exam information system project manager_ Real topic over the years_ Wrong question set in the second half of 2019_ Morning comprehensive knowledge question - Senior Information System Project Man
MySQL foundation 05 DML language

Using tensorboard to visualize the model, data and training process
Excel removes the data after the decimal point and rounds the number

MySQL基础用法02
看完这篇 教你玩转渗透测试靶机Vulnhub——DriftingBlues-9
异步、邮件、定时三大任务
随机推荐
关于Fibonacci数列
The R language uses the ctree function in the party package to build conditional inference decision trees, uses the plot function to visualize the trained conditional inference decision tree, and the
Kivy tutorial - example of using Matplotlib in Kivy app
Give you an array numbers that may have duplicate element values. It was originally an array arranged in ascending order, and it was rotated once according to the above situation. Please return the sm
Androd Gradle 对其使用模块依赖的替换
Find a benchmark comrade in arms | a million level real-time data platform, which can be used for free for life
Now that the teenager has returned, the world's fireworks are the most soothing and ordinary people return to work~
wirehark数据分析与取证A.pacapng
MySQL foundation 06 DDL
2022 Jiangxi Provincial Safety Officer B certificate reexamination examination and Jiangxi Provincial Safety Officer B certificate simulation examination question bank
数学知识:台阶-Nim游戏—博弈论
如今少年已归来,人间烟火气最抚凡人心 复工了~
【C语言】指针与数组笔试题详解
The industrial scope of industrial Internet is large enough. The era of consumer Internet is only a limited existence in the Internet industry
一比特苦逼程序員的找工作經曆
Excel calculates the difference between time and date and converts it into minutes
R language generalized linear model function GLM, (model fit and expression diagnostics), model adequacy evaluation method, use plot function and car package function
力扣 204. 计数质数
【FPGA教程案例5】基于vivado核的ROM设计与实现
Create your first Kivy program Hello word (tutorial includes source code)