Take notes of studying this thesis .
Abstract

(1) Single key homomorphic encryption
Only one private key , And the ciphertexts encrypted by different public keys cannot be calculated with each other .
(2) Threshold homomorphic encryption ( Multi key encryption )
Support multiple private keys , Ciphertexts encrypted by different public keys can be calculated with each other .
introduction
(1) big data Well developed , combination machine learning Better serve the society , But there is a problem : The data of a single enterprise cannot support the landing of the algorithm in its own business scenario ( Your data volume is not enough , Need someone else's ), So we need to Data interconnection , Data sharing .
(2) Privacy computing Can solve , Definition , effect , Common technologies , This paper mainly introduces Homomorphic encryption technology , And focus on the analysis Homomorphic encryption of single key and threshold homomorphic encryption technology , And the application advantages of the latter in privacy Computing .
Single key homomorphic encryption
Definition


summary :
(1) In single key homomorphic encryption , Ciphertext that can perform homomorphic computation , Must be encrypted with the same key .
problem
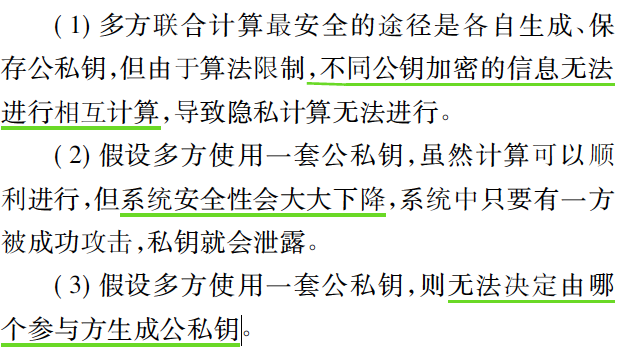
here ,CA I'm sure I'll jump out and say , What do I do !
summary :
(1) Have to admit , Single key homomorphic encryption does have shortcomings in this aspect !
Threshold homomorphic encryption

summary :
(1) There are not only multiple private keys , The public key can also be multiple !
Definition

Calculation key here \(evk\) And many ?\(k\) Private key ,\(N\) Public key and calculation key , Threshold homomorphic encryption true NB!
Current threshold homomorphic encryption scheme
Most of the current schemes are based on the improvement of single key homomorphic encryption algorithm , The encryption mode is roughly the same , That is, it supports multiple private keys , Ciphertext under different public keys ( Convert under the calculation key , key exchange ?) Can calculate each other .
threshold :
- Different private keys , Different public keys , Different calculation keys
- When decrypting , Less need \(K\leq N\) To decrypt successfully
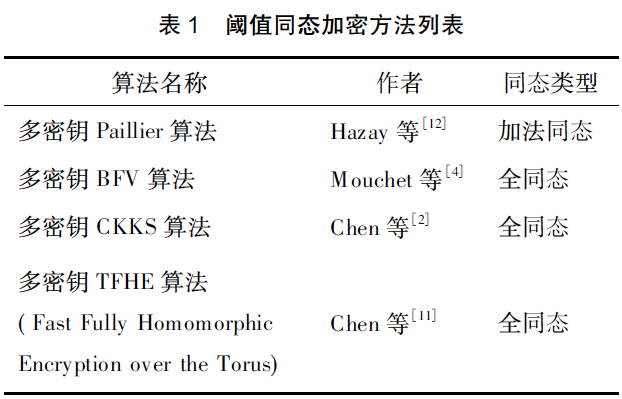
【12】:Efficient RSA key generation and threshold paillier in the two-party setting-2019
【4】:Multiparty homomorphic encryption: from theory to practice-2020
【2】:Efficient multi-key homomorphic encryption with packed ciphertexts with application to oblivious neural network inference-2019
【11】:Multi-key homomorphic encryption from TFHE-2019
application
Secure multi-party horizontal Federation modeling
The paper :POSEIDON: privacy-preserving federated neural network learning-2020
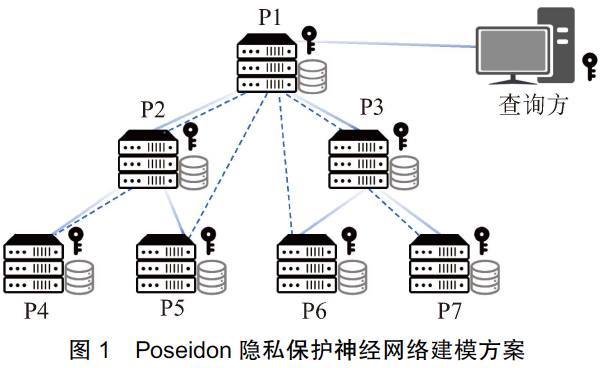
Specific process :
summary :
(1) Parameter encryption
(2) The inquired data is encrypted with their own public key , To decrypt , All participants are required ( Inquirer + node ) The private key .
Security model reasoning
The paper :Efficient multi-key homomorphic encryption with packed ciphertexts with application to oblivious neural network inference-2019
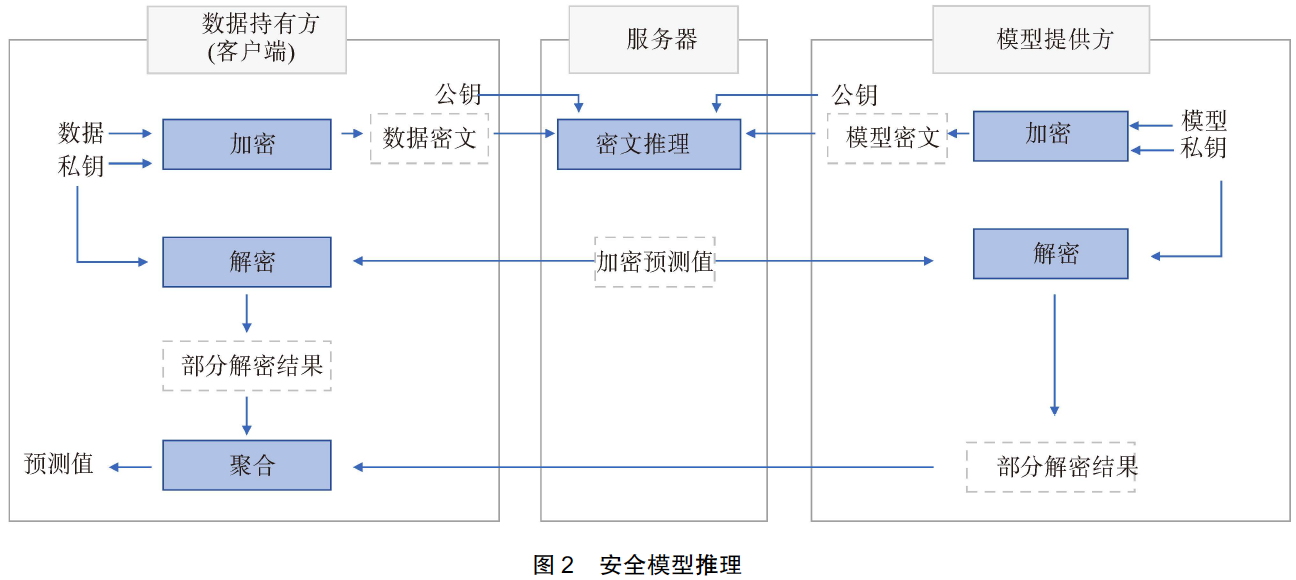
Specific process :
summary :
(1) Server as “ The mediation ” Deal with tenants and landlords , Data is always secret , And the private key is not exposed .
(2) Here are two copies of the public key , Two copies of private key , And you can decrypt with your own private key , But it needs to be aggregated to recover plaintext , This is different from the joint decryption of multiple private keys !
Secure multi-party Cloud Computing
Multi-key privacypreserving deep learning in cloud computing-2017
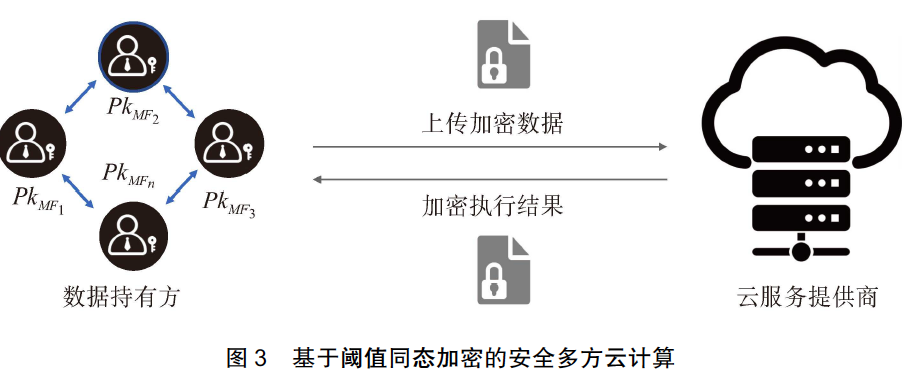
Specific process :
summary :
(1) Different public keys , Different private keys
other
(1) With the help of threshold homomorphic encryption technology MPC frame , And with the existing MPC Scheme comparison
- Multiparty homomorphic encryption: from theory to practice-2020
- On-the-fly multiparty computation on the cloud via multikey fully homomorphic encryption-2012
- Multiparty computation with low communication, computation and interaction via threshold FHE-2012
- Multiparty computation from threshold homomorphic encryption-2001
(2) With the help of threshold homomorphic encryption, a federated integration tree model is proposed
Privacy preserving vertical federated learning for tree-based models-2020
(3) A federated learning scheme based on threshold homomorphic encryption is proposed
Privacy-preserving federated learning based on multi-key homomorphic encryption-2021
(4) With the help of threshold homomorphic encryption, a secure biometric authentication scheme is implemented
THRIVE: threshold homomorphic encryption based secure and privacy preserving bIometric VErification system-2014
summary

summary :
(1) Privacy data protection is currently highly valued .
(2) How to calculate in privacy , Data flow , share , Giving full play to the maximum value is very popular at present , Worthy of research input .
(3) Article content : It introduces 、 Pointed out 、 Also on .. Analyzed and studied .
(4) Officially connected “Lifted ElGamal Threshold encryption algorithm ”

![[team PK competition] the task of this week has been opened | question answering challenge to consolidate the knowledge of commodity details](/img/d8/a367c26b51d9dbaf53bf4fe2a13917.png)