当前位置:网站首页>[mrctf2020] thousand layer routine
[mrctf2020] thousand layer routine
2022-06-24 07:24:00 【[mzq]】
[MRCTF2020] Thousand layer routine
Title address : https://buuoj.cn/challenges#[MRCTF2020]%E5%8D%83%E5%B1%82%E5%A5%97%E8%B7%AF
Decompress the package , It is found that the password is actually the name of the compressed package , Then according to the topic ,tnnd It's a doll problem again

import zipfile
file_path = input('path : ')# Compress package path
path = "/Users/mzq/Desktop/ctf/buuctf/misc/[MRCTF2020] Thousand layer routine /"
# path = file_path[0:len(file_path)-len(file_path.split('//')[-1])]
print(path)
n = 0
s2 = ""
def extract():
i = file_path.split('\\')[-1]# Recursive decompression package name
print(i)
str1 = ''
for x in range(1000):
ss = i[:i.find(".")]
print(ss)
zpf = zipfile.ZipFile( path+ss + ".zip")
list = zpf.namelist()
#print(list)
print(x + 1)
for f in list:
#print(f)
passwd = ss
#passwd = f.split('.')[0]# Zip code
#print(passwd)
zpf.extract(f, path, bytes(passwd.encode('utf-8')))
if 'zip' in f:
print(path, passwd)
i = str(f)
extract()

In the end, we solved a qr.zip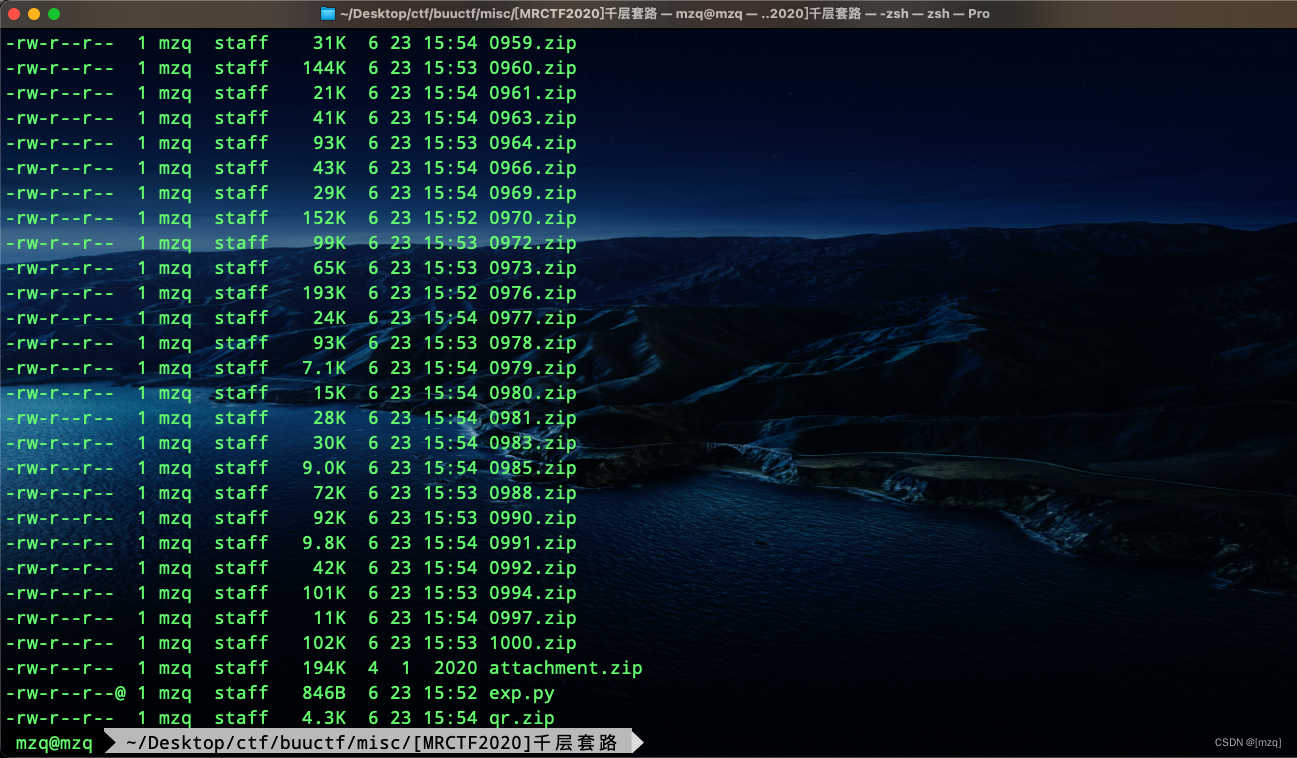
qr.zip After unzipping, we get qr.txt , There are some pixel values , Or coordinate value

Use script puzzles
from PIL import Image
file=open('qr.txt')
MAX=200
picture=Image.new("RGB",(MAX,MAX))
for y in range(MAX):
for x in range(MAX):
string =file.readline()
picture.putpixel([x,y],eval(string)) # Use it directly eval() Can be converted to tuples
picture.show()

MRCTF{ta01uyout1nreet1n0usandtimes}
边栏推荐
- RDD基础知识点
- [GUET-CTF2019]zips
- The P2V and V2V software starwind converter is really easy to use
- 在终端pip install xxx但在pycharm却no module named xxx
- 使用SystemParametersInfo访问用户界面设置
- Huawei experimental topology set, learning methods are attached at the end of the article!
- Tutorial on simple use of Modbus to BACnet gateway
- Outils de débogage JVM - Arthas
- What is the mentality of spot gold worth learning from
- 电脑如何打开软键盘,教大家Win10如何打开软键盘的方法
猜你喜欢
![[cloud based co creation] overview of the IOT of Huawei cloud HCIA IOT v2.5 training series](/img/80/1be6a87639ac8da41bc881b3341646.png)
[cloud based co creation] overview of the IOT of Huawei cloud HCIA IOT v2.5 training series
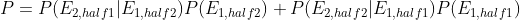
Leetcode probability interview shock series 11~15

【Proteus】Arduino UNO + DS1307+LCD1602时间显示
![[OGeek2019]babyrop](/img/74/5f93dcee9ea5a562a7fba5c17aab76.png)
[OGeek2019]babyrop

两个链表的第一个公共节点_链表中环的入口(剑指offer)

捏脸师: 炙手可热的元宇宙造型师
![buuctf misc [UTCTF2020]docx](/img/e4/e160f704d6aa754e85056840e14bd2.png)
buuctf misc [UTCTF2020]docx

二分专题训练

Spark project Packaging Optimization Practice
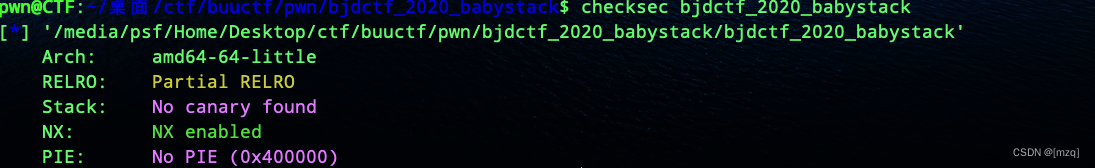
bjdctf_2020_babystack
随机推荐
游戏思考14:对cache_server缓冲服务器的问题思考(读云峰博客有感)
Development of IOT device end - establishment of development environment
JVM debugging tool -jmap
Coding helps promote the internationalization of Tencent games
High energy ahead: Figure 18 shows you how to use the waterfall chart to visually reflect data changes
[image segmentation] retinal vessel segmentation based on morphology with matlab code
Unexpected token u in JSON at position 0
The P2V and V2V software starwind converter is really easy to use
【图像特征提取】基于脉冲耦合神经网络(PCNN)实现图像特征提取含Matlab源码
捏脸师: 炙手可热的元宇宙造型师
Tencent host security captures Yapi remote code execution 0day vulnerability for wild exploitation. The attack is spreading and can be intercepted by firewall
【图像融合】基于NSST结合PCNN实现图像融合附matlab代码
第三方软件测试公司如何选择?2022国内软件测试机构排名
[WUSTCTF2020]alison_likes_jojo
What is a CC attack? How to judge whether a website is attacked by CC? How to defend against CC attacks?
【pointNet】基于pointNet的三维点云目标分类识别matlab仿真
0 foundation a literature club low code development member management applet (6)
A case study of apiserver avalanche caused by serviceaccount
只显示两行,超出部分省略号显示
【TS】函数类型