当前位置:网站首页>[concept of network principle]
[concept of network principle]
2022-07-07 20:23:00 【DJL_ new_ life】
( Click jump )
List of articles
Network principle
Basic principle
User mode and kernel mode are just different areas of memory User mode -> Kernel mode : The process of copying data in memory
network card : Realize physical signal <-> Digital signal conversion
Data transmission between two hosts
User mode -> Kernel mode : The process of copying data in memory
Internal replication here It's code like this ( It's just like )
byte[] User mode = new byte[1024]; // Data to be sent
byte[] Kernel mode = new byte[1024]; // Kernel buffer
os.write( User mode );
for(int i = 0; i < bytes.length; i++){
Kernel mode [i] = User mode [i];
}
How to deal with the data sent by the network card ?
- Load the data into the network card : Replication of data
- Send data :fire()
- To send data, you need to change the data signal into a physical signal
The data is on the transmission medium ( Ethernet cable 、 Optical fiber ) Spread on ( Signal decay 、 Signal error and other problems )
When the data goes to another host , here CPU Stop the current execution cycle , Give Way CPU Execute a piece of code prepared in advance ( This is the interrupt processing flow ). Transfer the data from the corresponding location of the network card Copied to the Kernel memory
here , Only one network medium can be used to connect the two hosts , Data exchange can be realized from the perspective of hardware
How about the networking of multiple hosts ?
The basic structure of network topology : Bus type 、 Stars 、 ring 、 Tree form
agreement / layered
To complete the whole communication , The problems to be dealt with in the middle are still very complex . Therefore, it is very necessary to adopt division of labor and cooperation
When there is layering , You need to target each layer , Specify some specifications , Let everyone abide by , And then better complete the work .
These norms are authoritative , Under the network discipline , Call it agreement (protocal)
Network standard layering :
- Academic school :OSI (Open System Interconnect) Provides a 7 Layer solution
application layer
The presentation layer
The session layer
Transport layer
The network layer
Data link layer
The physical layer
Practical school :TCP / IP 5 Layer protocol ( four layers , In expression The physical layer is omitted )
application layer (Application Layer): Implement and apply your own business problems ( Business is different , Different agreements )
Transport layer (Transmission Layer): Realize any process on the host To The problem of any process communication on another host
The network layer (NetWork Layer): Based on the function of data routing , Finally, cross LAN The host To The communication problem of the host
Data link layer (Data Link Layer) : The problem of connecting and communicating between one host and another host in the LAN ( Conflict domain / Broadcast area )
The physical layer (Physical Layer) : Hardware ensures data conversion / How to spread in network media
The physical layer
LAN Internal communication problems :
- The simplest LAN : That is, two hosts are directly connected
- LAN with certain topology
These hosts are using a channel together, and the channel can only travel a limited number of signals at a time , This will cause the signal to conflict on the channel
Conflict domain :
For example, in the scene of self-study , Everyone can take the initiative to speak , As a result, they can't hear each other's statements
Hub can effectively solve the problem of data transmission in network topology
The hub works in The physical layer (1. Copy the data 2. Signal amplification )
Use a hub for networking , Born in the same conflict domain , This is caused by the working principle of the hub
Data link layer
Already under the same conflict domain , How to solve , Through a certain conflict avoidance algorithm , Avoid conflicts .—— Data link layer to solve
The most common conflict avoidance algorithm : After discovering the conflict , Silent random time , Send... Again
Even if there is a conflict avoidance algorithm , The data in the same conflict domain can be effectively transmitted , But the efficiency of signal transmission will still have an impact
- Don't have too many hosts in the conflict domain
- Minimize the occurrence of conflict domains
Switch (switch) Used to reduce conflict domains ( Divide the conflict domain )
A hub : Just copy , I don't know what the data is
Switch : You need to understand the target address put into the data link layer ( Need to be able to parse the data link layer protocol ), Destination address of format data , Decide who to give the data or not
The switch works at the data link layer , According to the target address in the data , Send data only to the corresponding target
therefore , LAN can also be built through switches .
Address : The address of the data link layer refers to MAC Address ( Physical address )
MAC The length of the address is 48 position (6 Bytes ), Usually expressed as 12 individual 16 Hexadecimal number , Such as 00-16-EA-AE-3C-40 It's just one. MAC Address
The network card was dead when it was produced . Network cards all over the world MAC The address will not conflict
Between different routers Divided into different broadcast domains
Responsibilities of data link layer protocol : One LAN Inside , No matter what kind of equipment 、 Which topology , The host and the host can communicate normally
The network layer
Solve through data routing Span LAN Communication problems between hosts .
The router is located in at least two LANs ( There are at least two network cards )
Routers work on the network layer .
Data can only be in the same LAN transmission , Routers span Two LAN, So cross LAN The transmission of needs to pass through the router .
route (route): Do pathfinding ;
Router (router): A device used to complete the pathfinding function
The network layer protocol is to complete pathfinding , Realize cross LAN Host to host
The network layer has its own address :IP Address
IP The address is a 32 The binary number of bits , Usually divided into 4 individual ”8 Bit binary number “ ( That is to say 4 Bytes )
Usually use ” dotted decimal “ In the way of , namely a.b.c.d In the form of (a,b,c,d All are 0~255 A decimal integer between )
IP The address is the software address : Within the same network IP It shouldn't be ” repeat “ Of .IP The address changes at any time .
Transport layer
Host to host has been fully connected . A process Want to be with Processes on another host communicate .
port (port):0~65525 Unsigned number of two bytes
process <-> port : Write the port , Corresponding to the specific process
people <-> cell-phone number : Express delivery : Recipient phone
A process can have multiple ports ( No conflict )
A port can only be assigned to one person ( Can't repeat )
Three important network devices
A hub
Working on the physical level
Switch
Working at the data link layer
Router
Working at the network layer
Summary :
| application layer | Business | User mode | ||
|---|---|---|---|---|
| Transport layer | process To the process | port | Inside | |
| The network layer | Span LAN Of Host to host | IP Address / route | Router | nucleus |
| Data link layer | LAN Inside Host to host | MAC Address / Broadcast area / Conflict domain | Switch | state OS Completion of the code |
| The physical layer | Physically ensure that the line is unblocked | A hub | Hardware |
Important agreement :
HTTP/HTTPS/DNS Belongs to application layer
TCP/UDP Belong to Transport layer
IP Belong to The network layer
send out : encapsulation ( You must carry the distribution and unpacking information )
Accept : Unpack / Divide up ( According to the control information of this layer )
Packaging and distribution
Different protocol layers have different names for packets , At the transport layer, it's called segments (segment), In the network layer, it's called datagram (datagram), In the link layer, it's called frames (frame).
When the application layer data is sent to the network through the protocol stack , Each layer of protocol has to add a data header (header), It's called encapsulation (Encapsulation).
The first message contains something similar to how long the first one is , load (payload) How long is , What is the upper layer protocol .
Data is packaged into frames and sent to the transmission medium , After reaching the destination host, the corresponding header of each layer protocol is stripped , According to the first part Of “ Upper layer protocol field ” The data is handed over to the corresponding upper layer protocol for processing .
Each layer can perform necessary operations according to the control information added by each layer
Between corresponding levels , It's completely transparent , This process can be completely ignored
If it helps you , Please give me a compliment .
边栏推荐
- 复杂因子计算优化案例:深度不平衡、买卖压力指标、波动率计算
- How to implement safety practice in software development stage
- Force buckle 1961 Check whether the string is an array prefix
- AIRIOT助力城市管廊工程,智慧物联守护城市生命线
- Nebula importer data import practice
- CIS芯片测试到底怎么测?
- 使用camunda做工作流设计,驳回操作
- Solve the problem of incomplete display around LCD display of rk3128 projector
- 使用高斯Redis实现二级索引
- Splicing and splitting of integer ints
猜你喜欢
【mysql篇-基础篇】事务
不落人后!简单好用的低代码开发,快速搭建智慧管理信息系统
机械臂速成小指南(十二):逆运动学分析
机械臂速成小指南(十一):坐标系的标准命名
一键部署Redis任意版本
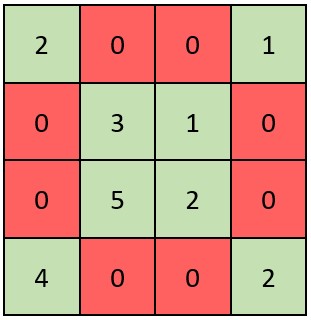
Force buckle 2319 Judge whether the matrix is an X matrix

Helix QAC 2020.2新版静态测试工具,最大限度扩展了标准合规性的覆盖范围

上海交大最新《标签高效深度分割》研究进展综述,全面阐述无监督、粗监督、不完全监督和噪声监督的深度分割方法

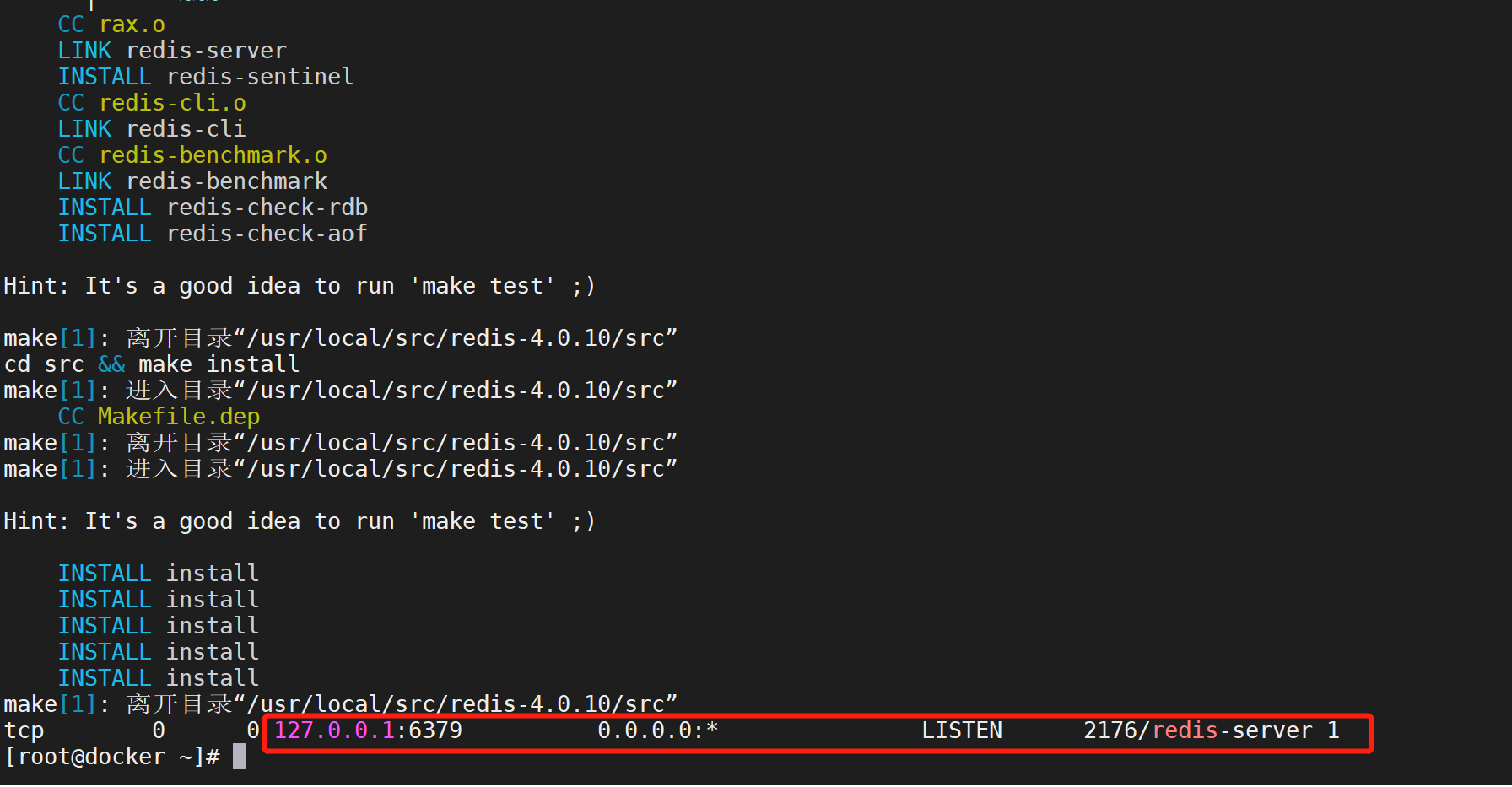
One click deployment of any version of redis
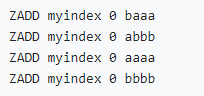
Implement secondary index with Gaussian redis
随机推荐
EasyGBS级联时,上级平台重启导致推流失败、画面卡住该如何解决?
Helix QAC 2020.2新版静态测试工具,最大限度扩展了标准合规性的覆盖范围
华为CE交换机下载文件FTP步骤
【哲思与实战】程序设计之道
Precautions for cjson memory leakage
第二十章 使用工作队列管理器(三)
一键部署Redis任意版本
Creation of kubernetes mysql8
[philosophy and practice] the way of program design
如何在软件研发阶段落地安全实践
Cantata9.0 | 全 新 功 能
How to test CIS chip?
软件缺陷静态分析 CodeSonar 5.2 新版发布
School 1 of vulnhub
让这个CRMEB单商户微信商城系统火起来,太好用了!
整型int的拼接和拆分
力扣 1790. 仅执行一次字符串交换能否使两个字符串相等
智能软件分析平台Embold
有用的win11小技巧
《数字图像处理原理与实践(MATLAB版)》一书之代码Part2[通俗易懂]