当前位置:网站首页>[CF1476F]Lanterns
[CF1476F]Lanterns
2022-07-01 18:17:00 【OneInDark】
subject
Ideas
First of all, this is a d p \tt dp dp problem . Then we need to find the recursive subproblem .
Generally, the case of a particular value will be enumerated . For example, the last lantern . Consider which lanterns it covers ? The unlighted lanterns are discrete , no way . Then you can consider who covers it .
You might as well set up lanterns j j j Covered it . that ( j , n ] (j,n] (j,n] All the lanterns illuminate the lanterns on the left , The illuminated lantern continues to illuminate to the left , Until some p i = 0 p_i=0 pi=0 stop it ( I can't see the left ). There's only one left [ 1 , i ) [1,i) [1,i) My lantern is not illuminated , See if they can light up internally .
This is a O ( n 2 ) \mathcal O(n^2) O(n2) Of . be aware d p \tt dp dp Values are b o o l \tt bool bool type , Consider changing it to i n t \tt int int type , So as to reduce the information that needs to be processed during the transfer —— Obviously, it's using i n t \tt int int Dynamically achieve “ The illuminated lantern continues to illuminate to the left ” The process of , Just store the number of lanterns that are illuminated .
Of course, there is no need for recursion , Direct recursion . Say it completely , remember f ( i ) f(i) f(i) For the former i i i The longest prefix length that a lantern can illuminate . There are two kinds of transfer , Corresponding to the original enumeration j j j And continue to iterate back to illuminate .
- Take whatever you like j ⩾ i j\geqslant i j⩾i Satisfy j − p j ⩽ f ( i − 1 ) + 1 j-p_j\leqslant f(i{\rm-}1)+1 j−pj⩽f(i−1)+1, be f ( j ) f(j) f(j) You can use max t = i j − 1 t + p t \max_{t=i}^{j-1}t+p_t maxt=ij−1t+pt to update . Specially , if j = i j=i j=i, use ( j − 1 ) (j{\rm-}1) (j−1) to update .
- if f ( i − 1 ) ⩾ i f(i{\rm-}1)\geqslant i f(i−1)⩾i, be f ( i ) f(i) f(i) You can use max { f ( i − 1 ) , i + p i } \max\{f(i{\rm-}1),i+p_i\} max{ f(i−1),i+pi} to update .
The most interesting thing is , The first kind of transfer does not need to f ( i − 1 ) f(i{\rm-}1) f(i−1) To update , Because it was originally when it could not continue to illuminate , You need to enumerate again j j j . Understand from the formula , It's just f ( i − 1 ) < i f(i{\rm-}1)<i f(i−1)<i We need to consider the first kind of transfer , here t = i t=i t=i Have already let max \max max Take a larger value .
At this time, use the form filling method . For one j j j, Its optimal i i i The smaller the better ; So the goal is to find the smallest i i i Satisfy f ( i − 1 ) ⩾ j − p j − 1 f(i{\rm-}1)\geqslant j-p_j-1 f(i−1)⩾j−pj−1 . Monotonic stack can be achieved by two points . Query the maximum value to S T \tt ST ST surface , Or any data structure . Time complexity O ( n log n ) \mathcal O(n\log n) O(nlogn) .
Code
#include <cstdio> // JZM yydJUNK!!!
#include <iostream> // XJX yyds!!!
#include <algorithm> // XYX yydLONELY!!!
#include <cstring> // (the STRONG long for LONELINESS)
#include <cctype> // ZXY yydSISTER!!!
using namespace std;
# define rep(i,a,b) for(int i=(a); i<=(b); ++i)
# define drep(i,a,b) for(int i=(a); i>=(b); --i)
typedef long long llong;
inline int readint(){
int a = 0, c = getchar(), f = 1;
for(; !isdigit(c); c=getchar())
if(c == '-') f = -f;
for(; isdigit(c); c=getchar())
a = (a<<3)+(a<<1)+(c^48);
return a*f;
}
inline void getMax(int &x, const int &y){
if(x < y) x = y;
}
const int MAXN = 300005;
int p[MAXN];
namespace ST{
const int LOGN = 19;
int st[LOGN][MAXN], logtwo[MAXN];
void init(int n){
rep(i,2^(logtwo[1]=0),n) logtwo[i] = logtwo[i>>1]+1;
}
void build(int n){
rep(i,1,n) st[0][i] = i+p[i];
rep(j,0,LOGN-2) rep(i,1,n-(2<<j)+1)
st[j+1][i] = max(st[j][i],st[j][i+(1<<j)]);
}
inline int query(const int &l, const int &r){
const int &k = logtwo[r-l+1];
return max(st[k][l],st[k][r-(1<<k)+1]);
}
}
int best[MAXN], dp[MAXN], sta[MAXN], top;
void paint(int x){
if(!x) return ;
if(best[x] == -1){
paint(x-1), putchar('R');
return ; // covered
}
paint(best[x]);
rep(i,best[x]+1,x-1) putchar('R');
putchar('L'); // x is chosen to be left
}
bool cmp(const int &x, const int &y){
return dp[x] < y;
}
int main(){
ST::init(MAXN-1);
for(int T=readint(); T; --T){
int n = readint();
rep(i,1,n) p[i] = readint();
ST::build(n), sta[0] = top = 0;
for(int i=1; i<=n; ++i){
sta[top+1] = i; // force best[i] = i
dp[i] = (dp[i-1] >= i) ? max(dp[i-1],i+p[i]) : 0;
best[i] = *lower_bound(sta,sta+top+1,i-p[i]-1,cmp);
int got = (best[i] == i) ? -1 : ((best[i] == i-1) ?
i-1 : ST::query(best[i]+1,i-1)); // at least j-1
if(dp[i] < got) dp[i] = got; else best[i] = -1;
if(dp[sta[top]] < dp[i]) sta[++ top] = i;
}
if(dp[n] < n) puts("NO");
else puts("YES"), paint(n), putchar('\n');
}
return 0;
}
边栏推荐
- Set the style of QT property sheet control
- 证券开户安全么,有没有什么样的危险呢
- transform. Forward and vector3 Differences in the use of forward
- SCP -i private key usage
- Software construction scheme of smart factory collaborative management and control application system
- Small exercise -- subnet division and summary
- Happy new year | 202112 monthly summary
- Nearly 60% of the employees strongly support Ctrip's "3+2" working mode, and work at home for two days a week
- Review Net 20th anniversary development and 51aspx growth
- An example of data analysis of an old swatch and an old hard disk disassembly and assembly combined with the sensor of an electromagnetic press
猜你喜欢
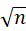
Euler function: find the number of numbers less than or equal to N and coprime with n
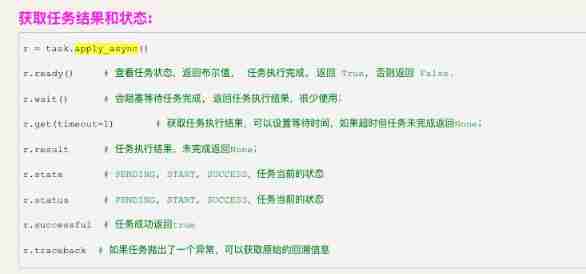
Distributed task queue: Celery usage record
Penetration practice vulnhub range Tornado
Review Net 20th anniversary development and 51aspx growth

Debiasing word embeddings | talking about word embedding and deviation removal # yyds dry goods inventory #

This is the latest opportunity of the London bank trend
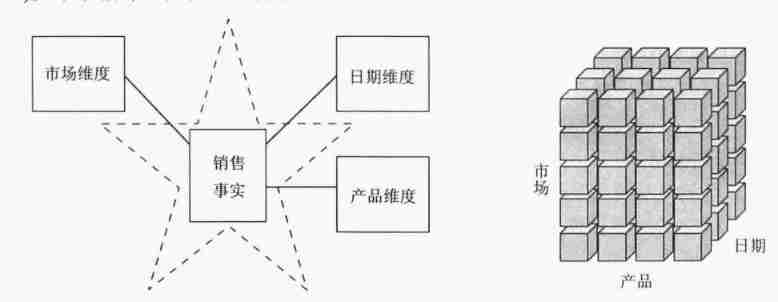
Data warehouse (3) star model and dimension modeling of data warehouse modeling

Check log4j problems using stain analysis
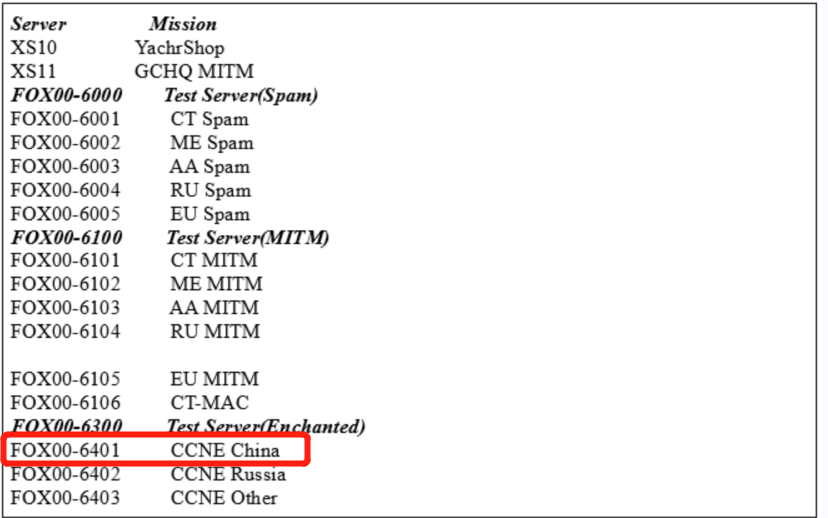
Heavy disclosure! Hundreds of important information systems have been invaded, and the host has become a key attack target

Mujoco's biped robot Darwin model
随机推荐
Is the software of futures pioneer formal and safe? Which futures company is safer to choose?
Growing up in the competition -- (Guangyou's most handsome cub) Pikachu walking
Zabbix报警执行远程命令
聊聊项目经理最爱使用的工具
Leetcode problem solving series -- continuous positive sequence with sum as s (sliding window)
JDBC: deep understanding of Preparedstatement and statement[easy to understand]
ZABBIX alarm execute remote command
. Net cloud native architect training camp (permission system code implements actionaccess) -- learning notes
Heavy disclosure! Hundreds of important information systems have been invaded, and the host has become a key attack target
Setting up a time server requires the client to automatically synchronize the time of the server at 9 a.m. every day
SQL injection vulnerability (MySQL and MSSQL features)
MFC obtains local IP (used more in network communication)
Code example of libcurl download file
Distributed task queue: Celery usage record
Gameframework eating guide
Yuancosmos game farmersworld farmers world - core content of the second conference in China!
Alibaba cloud Li Feifei: China's cloud database has taken the lead in many mainstream technological innovations abroad
Is it safe to open a stock account by mobile phone? What do you need to bring with you to open an account?
Unity3d extended toolbar
SPIE Western optoelectronics exhibition returned offline and successfully held a science and engineering event