当前位置:网站首页>Getting started with the go language is simple: go implements the Caesar password
Getting started with the go language is simple: go implements the Caesar password
2022-07-04 13:49:00 【51CTO】
Use Caesar's password to move characters on text . call strings.Map Method .
1 Caesar code encryption
Caesar code ( English :Caesar cipher), Or Caesar encryption 、 Caesar transforms 、 Transform encryption , It's the simplest and most widely known encryption technology .
The Caesar code is a kind of Replace encryption technology , All the letters in the plaintext go backwards in the alphabet ( Or forward ) Offset by a fixed number and replaced with ciphertext . for example , When the offset is zero 3 When , All the letters A Will be replaced by D;B become E, And so on . This encryption method is named after Caesar in the Roman Republic , It is said that Caesar used this method to contact his generals .
Plaintext alphabet :ABCDEFGHIJKLMNOPQRSTUVWXYZ Ciphertext alphabet :DEFGHIJKLMNOPQRSTUVWXYZABC
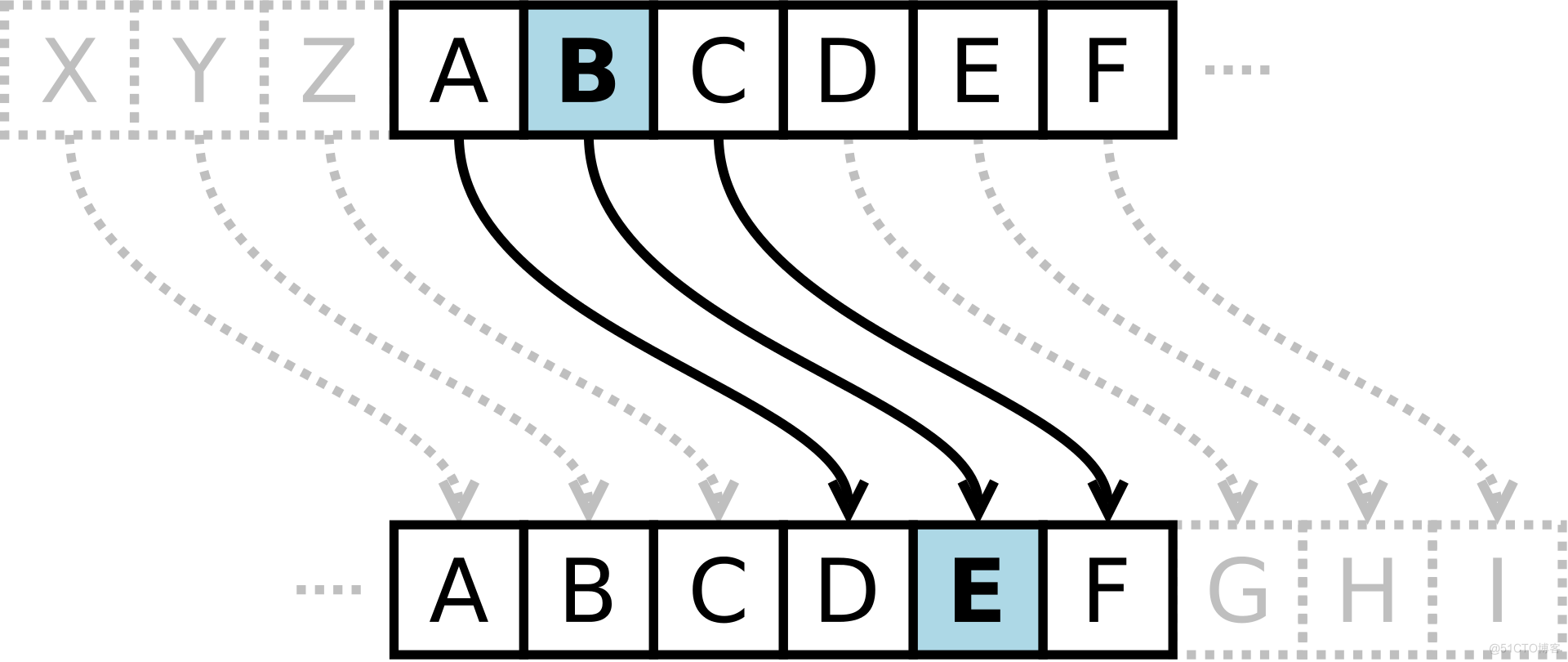
design idea
- Set plaintext and move step size ( Secret text )
- Convert clear text to lowercase , Prepare clear text byte slices and ciphertext slices
- Each plaintext character rotates according to the displacement step and is stored in the ciphertext
- Back to ciphertext
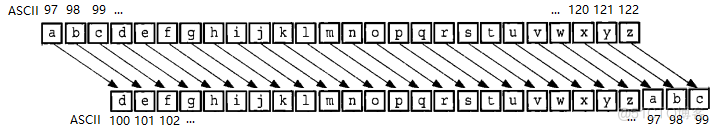
2 Go Realization
Caesar passwords are generally delivered in the form of passwords . Like this string of code “exxegoexsrgi” It's a password .
By moving the letters , We can encode messages . This prevents casual snooping . stay Go in , We can use strings.Map Method to achieve this .
2.1 Import package
2.2 To write caesar Method
Then let's write caesarEn() Caesar password encryption method . This will receive a string and return a modified string .
It moves characters , Then move the character to the valid range .
// Caesar code encryption
func
caesarEn(
strRaw
string,
step
byte)
string {
//1. Make text lowercase
str_raw :
=
strings.
ToLower(
strRaw)
//2. Define the step size
step_move :
=
step
//3. Convert a string to a plaintext character slice
str_slice_src :
= []
byte(
str_raw)
fmt.
Println(
"Clear text character slice:",
str_slice_src)
//4. Create a ciphertext character slice
str_slice_dst :
=
str_slice_src
//5. Loop through text slices
for
i :
=
0;
i
<
len(
str_slice_src);
i
++ {
//6. If the plaintext feature of the current period is within the displacement range , Please add a displacement step directly to save the ciphertext character slice
if
str_slice_src[
i]
<
123
-
step_move {
str_slice_dst[
i]
=
str_slice_src[
i]
+
step_move
}
else {
//7. If plaintext characters are out of range , Then add the step length after displacement and subtract 26
str_slice_dst[
i]
=
str_slice_src[
i]
+
step_move
-
26
}
}
//8. Output results
fmt.
Println(
"The encryption result is:",
step_move,
str_slice_dst,
string(
str_slice_dst))
return
string(
str_slice_dst)
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
3 Caesar password decryption
thought :
- Set ciphertext and displacement steps
- Prepare ciphertext character slice and plaintext character slice
- The characters of each ciphertext rotate according to the displacement step , And stored in the plaintext slice
- Return clear text
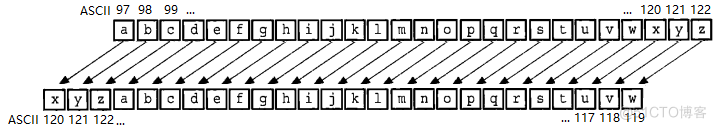
Go Caesar decrypts the code :
//2. Caesar password decryption
func
caesarDe(
strCipher
string,
step
byte)
string {
//1. Make text lowercase
str_cipher :
=
strings.
ToLower(
strCipher)
//2. Alternate step size
step_move :
=
step
//3. Convert a string to a plaintext character slice
str_slice_src :
= []
byte(
str_cipher)
fmt.
Println(
"Ciphertext character slice:",
str_slice_src)
//4. Create a ciphertext character slice
str_slice_dst :
=
str_slice_src
//5. Loop through character text slices
for
i :
=
0;
i
<
len(
str_slice_src);
i
++ {
//6. If the plaintext feature of the current period is within the displacement range , Please add a displacement step directly to save the ciphertext character slice
if
str_slice_src[
i]
>=
97
+
step_move {
str_slice_dst[
i]
=
str_slice_src[
i]
-
step_move
}
else {
//7. If plaintext characters are out of range , Then add 26 Step length after subtracting displacement
str_slice_dst[
i]
=
str_slice_src[
i]
+
26
-
step_move
}
}
//8. Output results
fmt.
Println(
"The decryption result is:",
step_move,
str_slice_dst,
string(
str_slice_dst))
return
string(
str_slice_dst)
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
4 Other implementations
package
main
import (
"errors"
"fmt"
"reflect"
"regexp"
)
var
TBL
= []
rune(
"abcdefghijklmnopqrstuvwxyz")
var
CLUES
= []
string{
"this",
"the",
"that"}
var (
ErrLength
=
errors.
New(
"invalid length")
ErrChar
=
errors.
New(
"invalid char")
ErrNoClue
=
errors.
New(
"no clue word")
ErrShift
=
errors.
New(
"invalid shift value")
)
func
Encrypt(
in
string,
sh
int) (
enc
string,
err
error) {
err
=
assert(
in)
if
sh
<
0 {
err
=
ErrShift
}
if
err
!=
nil {
return
}
enc
=
shift(
in,
sh)
return
}
func
Decrypt(
in
string) (
dec
string,
sh
int,
err
error) {
err
=
assert(
in)
if
err
!=
nil {
return
}
var
hit
bool
=
false
subin :
=
subStr(
in)
for
i :
=
0;
i
<
len(
CLUES);
i
++ {
subclue :
=
subStr(
CLUES[
i])
for
j :
=
0;
j
<
len(
subin)
-
len(
subclue)
+
1;
j
++ {
if
reflect.
DeepEqual(
subin[
j:
j
+
1],
subclue[
0:
len(
subclue)
-
1]) {
sh
=
subtract([]
rune(
in)[
j], []
rune(
CLUES[
i])[
0])
hit
=
true
break
}
}
}
if
!
hit {
err
=
ErrNoClue
return
}
dec
=
shift(
in,
-
sh)
return
}
func
assert(
in
string) (
err
error) {
if
regexp.
MustCompile(
`[^a-z\. \r\n]`).
MatchString(
in) {
err
=
ErrChar
}
else
if
len(
in)
>
80 {
err
=
ErrLength
}
return
}
func
shift(
in
string,
sh
int) (
out
string) {
for
_,
v :
=
range
in {
if
v
==
'.'
||
v
==
' '
||
v
==
'\r'
||
v
==
'\n' {
out
+=
string(
v)
continue
}
i :
=
indexOf(
TBL,
v)
len :
=
len(
TBL)
var
ii
int
= (
i
+
sh)
%
len
if
ii
<
0 {
ii
+=
len
}
if
ii
>
len {
ii
-=
len
}
out
+=
string(
TBL[
ii])
}
return
}
func
subtract(
left
rune,
right
rune) (
out
int) {
l :
=
indexOf(
TBL,
left)
r :
=
indexOf(
TBL,
right)
out
=
l
-
r
if
out
<
0 {
out
+=
len(
TBL)
}
return
}
func
subStr(
in
string) []
int {
subin :
=
make([]
int,
0,
79)
for
i :
=
range
in {
if
i
>
len(
in)
-
2 {
break
}
subin
=
append(
subin,
subtract([]
rune(
in)[
i], []
rune(
in)[
i
+
1]))
}
// return
return
subin
}
func
indexOf(
target []
rune,
searchChar
rune)
int {
for
i,
v :
=
range
target {
if
v
==
searchChar {
return
i
}
}
return
-
1
}
func
main() {
in :
=
"xlmw mw xli tmgxyvi xlex m xsso mr xli xvmt."
fmt.
Printf(
"in : '%s'\n",
in)
out,
sh,
err :
=
Decrypt(
in)
fmt.
Printf(
"out: '%s'\n",
out)
fmt.
Printf(
"sh : %d\n",
sh)
fmt.
Printf(
"err: %v\n",
err)
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
- 73.
- 74.
- 75.
- 76.
- 77.
- 78.
- 79.
- 80.
- 81.
- 82.
- 83.
- 84.
- 85.
- 86.
- 87.
- 88.
- 89.
- 90.
- 91.
- 92.
- 93.
- 94.
- 95.
- 96.
- 97.
- 98.
- 99.
- 100.
- 101.
- 102.
- 103.
- 104.
- 105.
- 106.
- 107.
- 108.
- 109.
- 110.
- 111.
- 112.
- 113.
- 114.
- 115.
- 116.
- 117.
- 118.
- 119.
- 120.
- 121.
- 122.
- 123.
- 124.
- 125.
- 126.
- 127.
- 128.
- 129.
- 130.
- 131.
- 132.
- 133.
- 134.
- 135.
- 136.
- 137.
- 138.
- 139.
- 140.
- 141.
- 142.
- 143.
- 144.
- 145.
- 146.
- 147.
- 148.
- 149.
- 150.
- 151.
- 152.
- 153.
5 test
package
main
import (
"fmt"
"strings"
)
func
caesar(
r
rune,
shift
int)
rune {
// Shift character by specified number of places.
// ... If beyond range, shift backward or forward.
s :
=
int(
r)
+
shift
if
s
>
'z' {
return
rune(
s
-
26)
}
else
if
s
<
'a' {
return
rune(
s
+
26)
}
return
rune(
s)
}
func
main() {
value :
=
"test"
fmt.
Println(
value)
// Test the caesar method in a func argument to strings.Map.
value2 :
=
strings.
Map(
func(
r
rune)
rune {
return
caesar(
r,
18)
},
value)
value3 :
=
strings.
Map(
func(
r
rune)
rune {
return
caesar(
r,
-
18)
},
value2)
fmt.
Println(
value2,
value3)
value4 :
=
strings.
Map(
func(
r
rune)
rune {
return
caesar(
r,
1)
},
value)
value5 :
=
strings.
Map(
func(
r
rune)
rune {
return
caesar(
r,
-
1)
},
value4)
fmt.
Println(
value4,
value5)
value
=
"exxegoexsrgi"
result :
=
strings.
Map(
func(
r
rune)
rune {
return
caesar(
r,
-
4)
},
value)
fmt.
Println(
value,
result)
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
Run the program :
6 summary
This paper briefly introduces an interesting Caesar cipher in cryptography , The algorithm is an alternative encryption technology , And in Go The code implements the encryption and decryption process of the algorithm .
边栏推荐
- 分布式BASE理论
- 洞见科技解决方案总监薛婧:联邦学习助力数据要素安全流通
- Solution: how to delete the information of Jack in two tables with delete in one statement in Oracle
- N++ is not reliable
- Deploy halo blog with pagoda
- 2022年中国移动阅读市场年度综合分析
- C language staff management system
- In 2022, it will be es2022 soon. Do you only know the new features of ES6?
- C语言小型商品管理系统
- MySQL45讲——学习极客时间MySQL实战45讲笔记—— 06 | 全局锁和表锁_给表加个字段怎么有这么多阻碍
猜你喜欢
高质量软件架构的唯一核心指标
It is six orders of magnitude faster than the quantum chemical method. An adiabatic artificial neural network method based on adiabatic state can accelerate the simulation of dual nitrogen benzene der
CTF competition problem solution STM32 reverse introduction

【AI系统前沿动态第40期】Hinton:我的深度学习生涯与研究心法;Google辟谣放弃TensorFlow;封神框架正式开源

基于链表管理的单片机轮询程序框架
从0到1建设智能灰度数据体系:以vivo游戏中心为例
高效!用虚拟用户搭建FTP工作环境
一个数据人对领域模型理解与深入

2022KDD预讲 | 11位一作学者带你提前解锁优秀论文
HAProxy高可用解决方案
随机推荐
再说rsync+inotify实现数据的实时备份
After the game starts, you will be prompted to install HMS core. Click Cancel, and you will not be prompted to install HMS core again (initialization failure returns 907135003)
【AI系统前沿动态第40期】Hinton:我的深度学习生涯与研究心法;Google辟谣放弃TensorFlow;封神框架正式开源
Annual comprehensive analysis of China's mobile reading market in 2022
模块化笔记软件综合评测:Craft、Notion、FlowUs
基于STM32+华为云IOT设计的酒驾监控系统
Etcd storage, watch and expiration mechanism
Reading cognitive Awakening
数据库公共字段自动填充
Dgraph: large scale dynamic graph dataset
Golang sets the small details of goproxy proxy proxy, which is applicable to go module download timeout and Alibaba cloud image go module download timeout
SQL语言
C语言程序设计选题参考
高效!用虚拟用户搭建FTP工作环境
After the game starts, you will be prompted to install HMS core. Click Cancel, and you will not be prompted to install HMS core again (initialization failure returns 907135003)
Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
A data person understands and deepens the domain model
2022KDD预讲 | 11位一作学者带你提前解锁优秀论文
#yyds干货盘点# 解决名企真题:连续最大和
2022G3锅炉水处理考试题模拟考试题库及模拟考试
