当前位置:网站首页>Using Kube bench and Kube hunter to evaluate the risk of kubernetes cluster
Using Kube bench and Kube hunter to evaluate the risk of kubernetes cluster
2022-07-02 05:02:00 【CSDN cloud computing】

author | A small bowl of soup
source | Attack the cloud
With Kubernetes More and more popular , The threshold is getting lower and lower . But security problems still exist , Here are two open source tools for auditing cluster security .
kube-bench
kube-bench[1] It's a Go Applications , Have 4.5k star. Used for inspection Kubernetes Whether the cluster complies with CIS Kubernetes Benchmark[2] guide .
CIS: Internet Security Center . This is a non-profit organization , Use feedback from the community to solve network security problems . A list of suggestions for building an environment free from cyber attacks . These suggestions include looking for overly loose profile permissions 、 Potential risk settings for cluster components 、 Identify unprotected accounts and check general network policies .
By configuring YAML File to test , The advantage of this is that the tool is easy to update with the standardization of testing .
function
function kube-bench There are many ways [3]
docker Container operation
stay Kubernetes Running in cluster
stay AKS Running in cluster
stay EKS Running in cluster
stay OpenShift Up operation
stay GKE Running in cluster
stay ACK Running in cluster
Here's a demonstration in Docker Running in the container Kube-bench. It needs to access the host PID The name space , In order to check the running process , And accessing the configuration file on the host .
docker run --rm --pid=host -v /etc:/etc:ro -v /var/lib/etcd:/var/lib/etcd:ro -v /var/lib/kubelet/config.yaml:/var/lib/kubelet/config.yaml:ro -v $(which kubectl):/usr/local/mount-from-host/bin/kubectl -v $HOME/.kube:/.kube -e KUBECONFIG=/.kube/config -it aquasec/kube-bench:latest runAfter running, the inspection report will be output , The report is divided into five subject blocks , You can see from the title :
Master node security configuration ;
Etcd Node configuration ;
Control plane configuration ;
Work node security configuration ;
Kubernetes Policy
in the light of Master Node The inspection results of the configuration file of are as follows :
[INFO] 1 Master Node Security Configuration
[INFO] 1.1 Master Node Configuration Files
[PASS] 1.1.1 Ensure that the API server pod specification file permissions are set to 644 or more restrictive (Automated)
# Omit
[FAIL] 1.1.7 Ensure that the etcd pod specification file permissions are set to 644 or more restrictive (Automated)
[FAIL] 1.1.8 Ensure that the etcd pod specification file ownership is set to root:root (Automated)
== Remediations master ==
1.1.7 Run the below command (based on the file location on your system) on the master node.
For example,
chmod 644 /etc/kubernetes/manifests/etcd.yaml
1.1.8 Run the below command (based on the file location on your system) on the master node.
For example,
chown root:root /etc/kubernetes/manifests/etcd.yamlin the light of Etcd The inspection of :
[INFO] 2 Etcd Node Configuration
[INFO] 2 Etcd Node Configuration Files
[FAIL] 2.1 Ensure that the --cert-file and --key-file arguments are set as appropriate (Automated)
[FAIL] 2.2 Ensure that the --client-cert-auth argument is set to true (Automated)
== Remediations etcd ==
2.1 Follow the etcd service documentation and configure TLS encryption.
Then, edit the etcd pod specification file /etc/kubernetes/manifests/etcd.yaml
on the master node and set the below parameters.
--cert-file=</path/to/ca-file>
--key-file=</path/to/key-file>
2.2 Edit the etcd pod specification file /etc/kubernetes/manifests/etcd.yaml on the master
node and set the below parameter.
--client-cert-auth="true" The inspection result is FAIL、WARN Of , The modification scheme will be given corresponding to the serial number . But whether the modification scheme is applied to your cluster , We need to judge comprehensively by ourselves , You should have a comprehensive understanding of what impact the modification will have on the cluster .
kube-hunter[4]
It's a Python Tools , To discover Kubernetes Vulnerabilities in clusters . It is from The attacker Evaluate cluster security from the perspective of . Have 3.5K star.
function
Binary system
Containers
Pod
Let's use docker Container operation .
docker run -it --rm --network host aquasec/kube-hunterAfter running, you need to choose the scanning mode :
Choose one of the options below:
1. Remote scanning (scans one or more specific IPs or DNS names)
2. Interface scanning (scans subnets on all local network interfaces)
3. IP range scanning (scans a given IP range)Remote scanning
To specify a remote machine for scanning , Options 1 Or use --remote Options , Container mode operation :
docker run --rm aquasec/kube-hunter --remote 192.168.28.72Interface scan
To specify interface scanning , have access to --interface Options ( This will scan all network interfaces of the machine ), Container mode operation :
docker run --rm aquasec/kube-hunter --interfaceNetwork segment scanning
To specify a specific to scan CIDR, Use --cidr Options , Container mode operation :
docker run --rm aquasec/kube-hunter --cidr 192.168.0.0/24The following is the report output after running the check :
+--------+---------------------+----------------------+----------------------+----------------------+----------------------+
| KHV002 | 192.168.28.154:6443 | Initial Access // | K8s Version | The kubernetes | v1.19.8 |
| | | Exposed sensitive | Disclosure | version could be | |
| | | interfaces | | obtained from the | |
| | | | | /version endpoint | |
+--------+---------------------+----------------------+----------------------+----------------------+----------------------+
| KHV052 | 192.168.28.194:10255| Discovery // Access | Exposed Pods | An attacker could | count: 9 |
| | | Kubelet API | | view sensitive | |
| | | | | information about | |
| | | | | pods that are | |
| | | | | bound to a Node | |
| | | | | using the /pods | |
| | | | | endpoint | |
+--------+---------------------+----------------------+----------------------+----------------------+----------------------+List two vulnerabilities :
Attackers can get through
/versionGet k8s Version of ;Attackers can get through
/podsInterface to get the Pod Number .
Kubernetes Node auto discovery
Set up --k8s-auto-discover-nodes Flag query Kubernetes All nodes in the cluster , Then try to scan all nodes . By default , It will use the in cluster configuration [5] Connect to Kubernetes API. If you want to use explicit kubeconfig file , Please set up --kubeconfig /root/.kube/kubeconfig.
View command help , Can run :
# docker run -it --rm --network host aquasec/kube-hunter --helpkube-hunter Is used for Kubernetes Optional tools for cluster penetration testing . It is easy to install and run , And show how the cluster looks from the attacker's perspective . But the output report , There is no repair solution prompt , The operation and maintenance personnel need to evaluate the scheme by themselves .
Conclusion
Both utilities are very mature and easy to use , And provides a good description of cluster security . Despite some defects , But for those who care about cluster security , They are a good choice .
Security is not limited to cluster configuration , Keep the applications running in the container up to date 、 Prevent unauthorized access to the mirror registry 、 Use secure network protocols 、 Monitoring application activity is also noteworthy .
Other optional tools
In addition to these two analysis tools . kubescape [6] It is also a recommended choice .Kubescape Provides risk analysis 、 Safety compliance 、RBAC Visualization tools, image vulnerability scanning and other functions , So far, more than 5.1K star.
Reference material
[1]
kube-bench: https://github.com/aquasecurity/kube-bench
[2]CIS Kubernetes Benchmark: https://www.cisecurity.org/benchmark/kubernetes/
[3]many-ways : https://github.com/aquasecurity/kube-bench/blob/main/docs/running.md
[4]kube-hunter: https://github.com/aquasecurity/kube-hunter
[5]In cluster configuration : https://kubernetes.io/docs/reference/access-authn-authz/rbac/
[6]kubescape : https://github.com/armosec/kubescape
[7]Kubernetes cluster security assessment with kube-bench and kube-hunter: https://blog.flant.com/kubernetes-security-with-kube-bench-and-kube-hunter/


Previous recommendation
CSS State management , It's a trick !
k8s The cluster can be installed graphically ?
Use this library , Let your service operate Redis Speed up
take k8s Made into 3D Shooting games , It's so fun that I can't stop
Share

Point collection

A little bit of praise
Click to see
边栏推荐
- Mapping settings in elk (8) es
- Mysql database learning
- Line by line explanation of yolox source code of anchor free series network (7) -- obj in head_ loss、Cls_ Loss and reg_ Calculation and reverse transmission of loss I
- Solution: the agent throws an exception error
- 2022 Alibaba global mathematics competition, question 4, huhushengwei (blind box problem, truck problem) solution ideas
- Video multiple effects production, fade in effect and border background are added at the same time
- 将光盘中的cda保存到电脑中
- 案例分享|智慧化的西部机场
- C# 图片显示占用问题
- Mapping location after kotlin confusion
猜你喜欢
Learn BeanShell before you dare to say you know JMeter
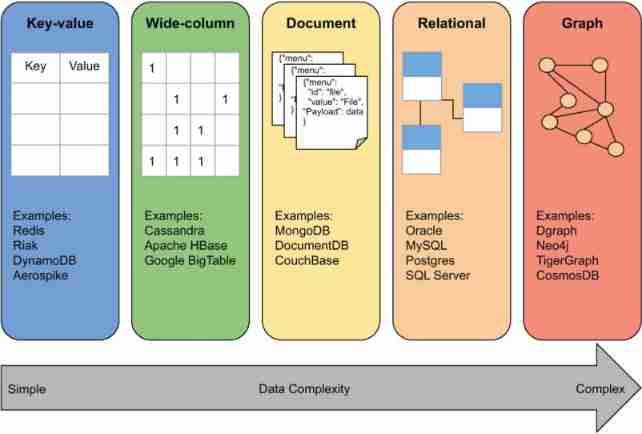
Starting from the classification of database, I understand the map database

Mathematical knowledge (Euler function)

Promise all()
Here comes the chicken soup! Keep this quick guide for data analysts
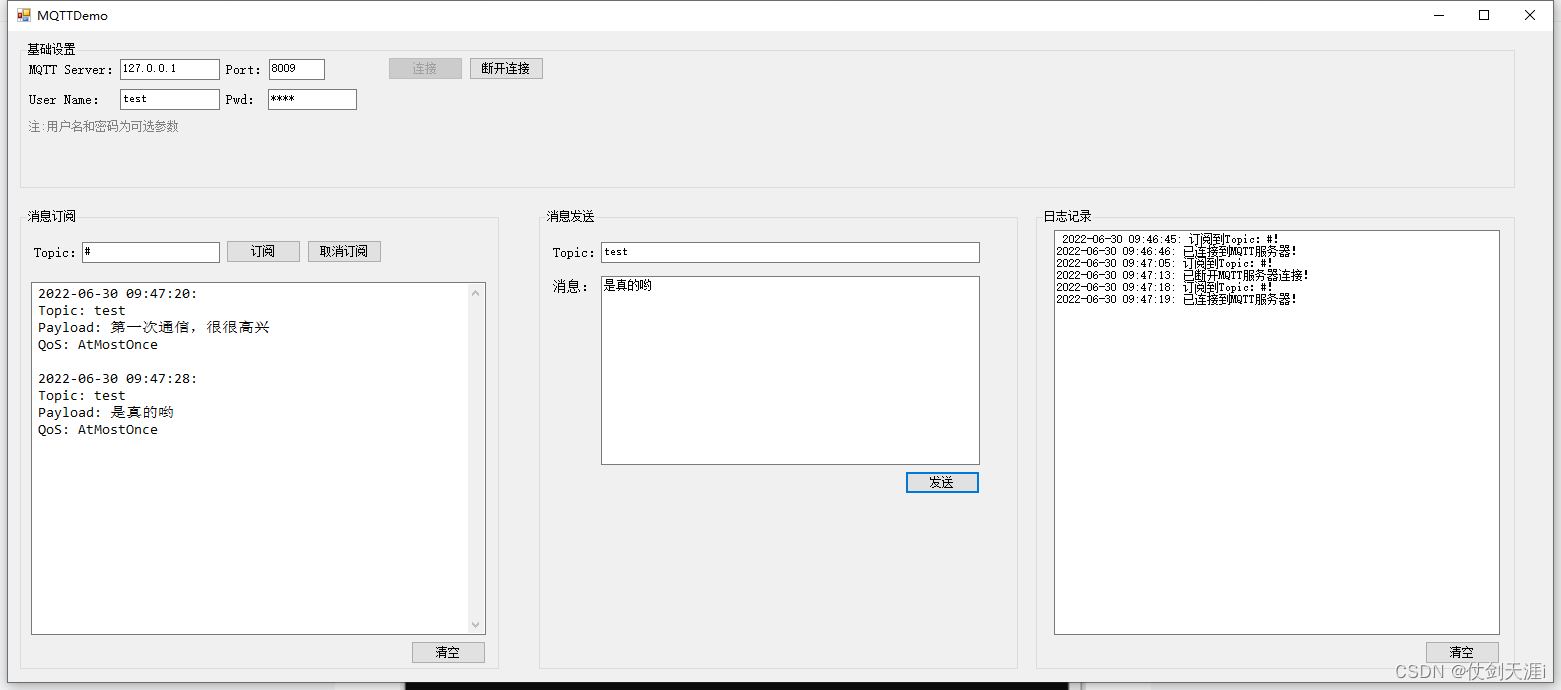
C case of communication between server and client based on mqttnet
![[opencv] image binarization](/img/7e/b56a59ffae3bf6cac9c0bb7e090b85.jpg)
[opencv] image binarization

Lay the foundation for children's programming to become a basic discipline
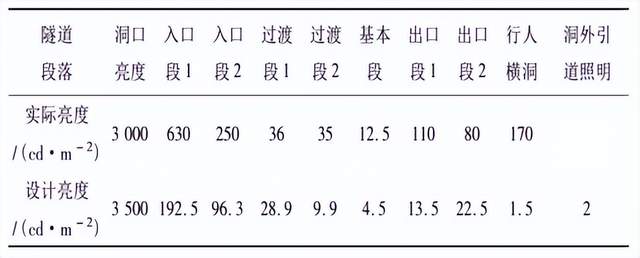
Acelems Expressway microgrid energy efficiency management platform and intelligent lighting solution intelligent lighting tunnel

Summary of main account information of zhengdaliu 4
随机推荐
Hcip day 17
js中的Map(含leetcode例题)
Leetcode- insert and sort the linked list
将光盘中的cda保存到电脑中
About PROFIBUS: communication backbone network of production plant
oracle 存储过程与job任务设置
Idea automatic package import and automatic package deletion settings
C case of communication between server and client based on mqttnet
初学爬虫-笔趣阁爬虫
Comp 250 parsing
数学知识——快速幂的理解及例题
奠定少儿编程成为基础学科的原理
There are duplicate elements in leetcode. Go implementation
fastText文本分类
Cubemx DMA notes
Application d'un robot intelligent dans le domaine de l'agroécologie
数据库问题汇总
Summary of database problems
Analyze the space occupied by the table according to segments, clusters and pages
Save the CDA from the disc to the computer