当前位置:网站首页>Retention policy of RMAN backup
Retention policy of RMAN backup
2022-07-06 09:54:00 【wx5caecf2ed0645】
What is the retention policy for backup (retention policy)
Retention policy refers to whether a backup should be retained and for how long . have access to configure retention policy Command to create a consistent 、 Automatic backup retention policy . When a backup strategy takes effect ,rman Think of data files 、 The backup of control files is obsolete Of , That is to say, according to user configuration , These backups are no longer needed for recovery . Users can use report obsolete Order to find out obsolete And use delete obsolete Delete them .
As the number of backups increases , Old backup files will become obsolete.rman Can identify obsolete The file of , But they will not be deleted automatically . You need to manually execute delete obsolete Delete them .
If the database is configured with a fast flashback area , The database will flash back the disk according to the fast quota Rules automatically delete files in the flashback area . Flashback zone quota Rule with rman Backup policy rules are different , But the flashback area will not delete backup files that do not exceed the backup policy .
obsolete and expired It's two different concepts
Whether the backup obsolete, It is determined by the backup strategy , It refers to exceeding the limit of the backup policy , Files that are no longer needed during recovery ;expired Refer to rman In execution crosscheck During the inspection , These files could not be found . In a word ,obsolete Refer to " No longer need ",expired Refer to " Can't find ".
Retention policies are for data files and control files full Back up or level 0 Backup ( Whether it's datafile image copy, a proxy copy, or part of a backup set). about datafile copies and proxy copies, If rman You can delete it if you think it is no longer needed . For backup set datafile Backup , Only the entire backup set becomes obsolete Before it can be deleted .
The backup strategy is not only for data files and control files full and level 0 The backup is valid , It also affects archived logs and level 1 Incremental backup . First rman Detect those data files 、 The control file backup is obsolete Of , then rman Archive logs that are no longer needed during recovery 、level 1 Incremental backup is considered obsolete Of .
report obsolete and delete obsolete How commands work :
It is mainly divided into two steps
(1) First , about full backup、datafile copy and level 0 Incremental backup of ,rman Will be based on retention policy Identify which are obsolete Of .
(2) then , For archive logs and level 1 Incremental backup of , If it corresponds to full backup、datafile copy and level 0 Incremental backup of has been obsolete Of , It would also be considered obsolete Of , Because they are no longer needed for data recovery .
NOTE: A 'delete obsolete' does not check that the archivelog files have been backed up before it deletes them.
Types of retention backup policies :( There are two types of backup )
(1)redundancy( redundancy ): Redundancy by default
1 | |
(2)recovery window( Restore window )
1 | |
When configuring the recovery window , The time should not be greater than the parameter control_file_record_keep_time Value .
Cancel the backup policy :( Never set backup to obsolete)
1 | |
How to make backup unaffected by backup strategy :
Users may need to keep data backup for a long time ( beyond rman Retention policy settings ). This backup information should be recorded in rman repository in , But it should exceed rman Limitations of backup retention policies , Otherwise it will be marked as obsolete Of .
Can be used during backup keep keyword 、 Or use after backup change...keep To achieve .
For archive logs, you can use logs keyword , This will not be identified as obsolete Of
Example :
1 2 3 4 5 6 7 8 | |
边栏推荐
- 【深度学习】语义分割:论文阅读:(CVPR 2022) MPViT(CNN+Transformer):用于密集预测的多路径视觉Transformer
- Nc29 search in two-dimensional array
- 【深度学习】语义分割-源代码汇总
- Vh6501 Learning Series
- [deep learning] semantic segmentation: thesis reading (neurips 2021) maskformer: per pixel classification is not all you need
- Processes of libuv
- Oom happened. Do you know the reason and how to solve it?
- Canoe CAPL file operation directory collection
- There are software load balancing and hardware load balancing. Which one to choose?
- History of object recognition
猜你喜欢

51单片机进修的一些感悟
[Yu Yue education] Wuhan University of science and technology securities investment reference
![[deep learning] semantic segmentation: paper reading: (CVPR 2022) mpvit (cnn+transformer): multipath visual transformer for dense prediction](/img/f1/6f22f00843072fa4ad83dc0ef2fad8.png)
[deep learning] semantic segmentation: paper reading: (CVPR 2022) mpvit (cnn+transformer): multipath visual transformer for dense prediction
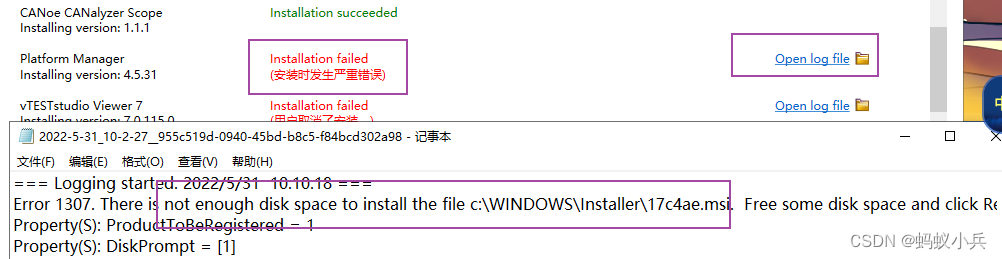
CANoe下载地址以及CAN Demo 16的下载与激活,并附录所有CANoe软件版本
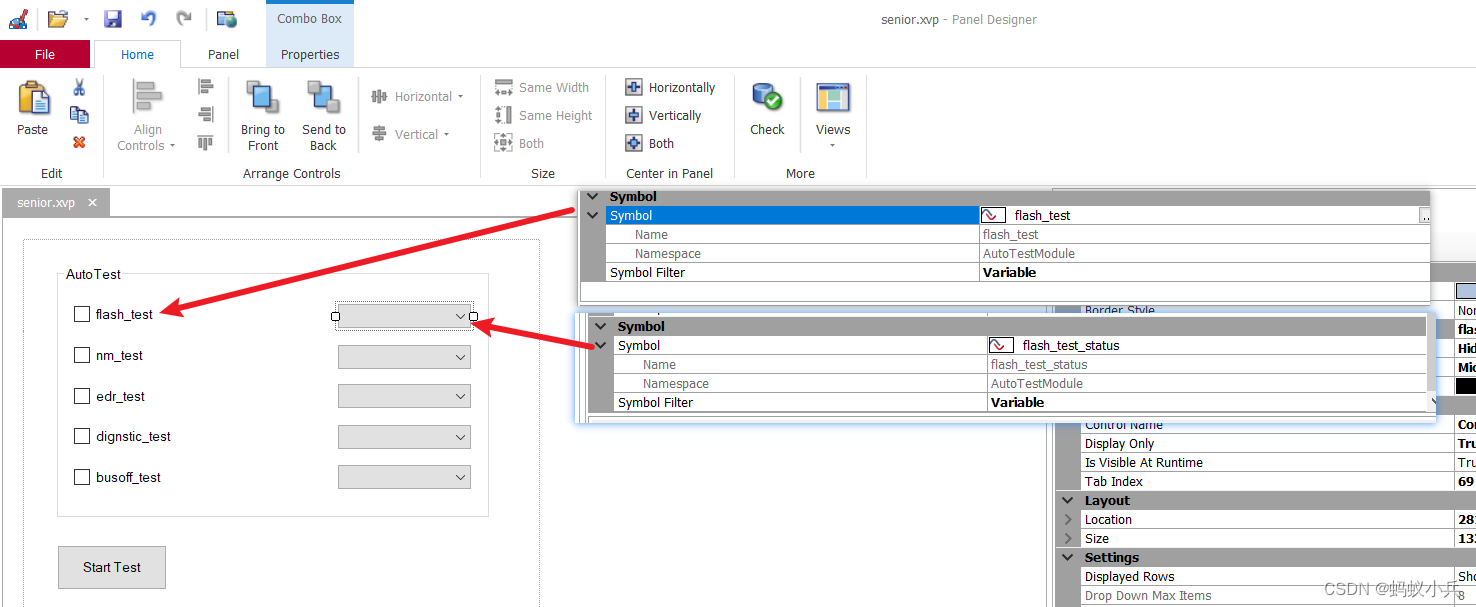
在CANoe中通过Panel面板控制Test Module 运行(高级)
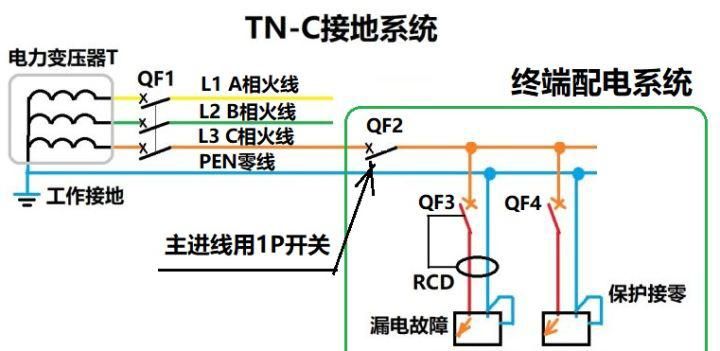
Why can't TN-C use 2p circuit breaker?
华南技术栈CNN+Bilstm+Attention
What are the models of data modeling
在CANoe中通過Panel面板控制Test Module 運行(初級)
【深度学习】语义分割:论文阅读(NeurIPS 2021)MaskFormer: per-pixel classification is not all you need
随机推荐
Release of the sample chapter of "uncover the secrets of asp.net core 6 framework" [200 pages /5 chapters]
美新泽西州州长签署七项提高枪支安全的法案
五月刷题03——排序
《ASP.NET Core 6框架揭秘》样章发布[200页/5章]
Yarn organizational structure
oracle sys_ Context() function
C杂讲 浅拷贝 与 深拷贝
Nc17 longest palindrome substring
嵌入式开发比单片机要难很多?谈谈单片机和嵌入式开发设计经历
【深度学习】语义分割:论文阅读:(2021-12)Mask2Former
MapReduce working mechanism
Target detection -- yolov2 paper intensive reading
Processes of libuv
Combined search /dfs solution - leetcode daily question - number of 1020 enclaves
Why is 51+ assembly in college SCM class? Why not come directly to STM32
[deep learning] semantic segmentation - source code summary
Configure system environment variables through bat script
Hero League rotation chart manual rotation
Nc29 search in two-dimensional array
Hero League rotation map automatic rotation
![[Yu Yue education] Wuhan University of science and technology securities investment reference](/img/4f/8e702cc244ec5d4de32740c0ecbd97)