当前位置:网站首页>Popularization of security knowledge - twelve moves to protect mobile phones from network attacks
Popularization of security knowledge - twelve moves to protect mobile phones from network attacks
2022-07-06 09:40:00 【[email protected]】
Will mobile phones also be attacked by the Internet ? Yes . you 're right . Mobile phones have become the favorite target of attackers . Not only is it more vulnerable , It's his lack of security .
Enterprises , Although the infrastructure of the government can benefit attackers a lot , But the attack is very difficult , These organizations have professional teams dealing with network security .
As a mobile personal user , Most people don't have this safety awareness , I don't know how to identify and protect mobile phones from attacks .
Attack cell phones , You can get your personal information , Get your key APP Account or chat information . Get your contact information , Easy to read your text messages .
When an attacker sends an attack to your phone , There will be no alarm to tell you . This has become the biggest security vulnerability .
How to prevent , I have listed the following measures to help you maximize your protection from all kinds of attacks :
One 、 Please keep the mobile system version and APP Instant update of version
Mobile update system and APP The version is quite easy , As long as you have this awareness , Click the mobile screen to complete . And this is also the most effective and simplest protection method .
Two 、 Minimize unnecessary installation APP
Many domestic enterprises , They all like to let users install a lot of their own associations APP, Commonly known as family bucket . these APP in , There may only be one you need . Not only occupy your mobile resources , There are also more security vulnerabilities , While you bear these consequences , Just help this company increase APP Used number of . thankfully , National regulators have begun to implement regulation , Regulate and crack down on this kind of forced installation behavior .
When you buy a new phone , Mobile phone manufacturers also have many built-in APP, Many times in the past , These built-in phones APP You cannot uninstall , Although many people choose to brush the machine . These are built-in by mobile phone manufacturers APP, In fact, there are only a few that you can use , When there is a choice , Suggestions will not be used APP Choose Delete .
3、 ... and 、 install APP Be sure to choose official app storage
On this one ,iPhone Our system is the best ,iPhone There are reasons to be called the safest mobile phone . The open source of Android mobile phones , Especially the Android system highly customized by domestic mobile phone manufacturers , In fact, there are many loopholes , Not certified by a third party , Users can also install APP. This makes the mobile malware can be installed on your mobile phone without any detection .
Four 、 Try not to connect to the public WiFi
Many shopping malls 、 The hotel 、 Coffee shops offer free WiFi, Use these for free WiFi, May be required to register , And provide mobile phone number and verification code information , Inadvertently get your personal number and mobile phone hardware information . There are also many commercials in the authentication interface , And these advertisements are likely to be unregulated , You can often see gambling 、 Pornographic information . When you accidentally click , You create an opportunity for the other party to attack or cheat you .
And connect with you for free WiFi People who , One of them may be the attacker , When you are in a network at the same time , It is easy to intercept and change the data packets of your mobile phone .
free WiFi Often there is no network security engineer to manage , There are loopholes in the verification behavior , Internet behavior is not recorded , Users on the same network have no network isolation .
5、 ... and 、 Don't use 2G Mobile communication
2G Communication technology enables us to realize the freedom of remote calls , But there are also major technical loopholes in this technology , Commonly known as pseudo base station . The most typical is that this kind of pseudo base station can be erected anytime, anywhere , Operators cannot supervise . And you can ask 2G Users push many text messages that look real , Induce users to click the link to commit fraud or attack .
Personally, users will be advised to choose 5G mobile phone ,5G High altitude portal safety technology based on , This kind of pseudo base station is avoided as much as possible 、 False signal , Make sure you use the communication signal of a legal operator .
Also remind you to pay attention to the use of dual card dual standby mobile phones , Often, the card slot of the secondary slot can only be used 2G signal communication . This is for mobile phone manufacturers to realize dual card and dual standby , But at the same time, reduce costs and the consequences of operators creating barriers .
6、 ... and 、 Don't click on unknown and untrusted links
SMS 、 Wechat groups provide communication channels for such untrusted links , Many people click carelessly or their mobile phones are damaged , Or mobile phones and personal information are obtained . Toby is that many people like to store their personal photos in mobile photo albums .
7、 ... and 、app Authorization should be careful
quite a lot APP It is achieved by maximizing the access to mobile phones APP The positioning of 、 Get verification code 、 Get photos and other functions , While realizing these functions , Also exist APP Maliciously force your personal information to be obtained and used . such as cache, Otherwise, why are you shopping APP Browse information , In another news APP It's displayed inside ?
There are some video editors APP, You will also ask for permission to get your mobile photo album , When your mobile photo album stores some sensitive photos , Like a bank card , Selfie, etc . Without your knowledge , These sensitive information may spread on the Internet . So please choose video editing carefully APP And careful authorization .
8、 ... and 、 Clean the unused mobile phones regularly APP
Somewhat APP After downloading and using just for some reason , Just use it this time . This kind of APP Delete and uninstall in time . The utilization rate is very low APP, It is recommended to download and install when necessary , After use , Delete in time .
Nine 、 Cell phone Bluetooth 、NFC On demand
Many people like to use Bluetooth 、NFC Wait and keep it open , It's convenient to use , For example, when cars are interconnected . exactly , This is very convenient , But it also creates opportunities for others to make malicious connections and attacks . If possible , Change your habits , It will be safer to open it when necessary .
Ten 、 Try not to choose secret free payment
It is still a convenient and safe choice , Once joked with colleagues , Now I encounter robbery , There is no need to ask your password . Unlock your phone with your face or fingers , Use an overseas QR code or payment link , You don't need to say a word to finish the robbery silently . The mobile phone is not lost , The money is gone . It's hard to protect rights .
11、 ... and 、 Install reliable mobile security software
about iPhone Come on , It's not really necessary , But for Android mobile phone users , It is very necessary , Whether it's Tencent 、360, Or the security management software of each mobile phone brand , Can be installed to protect the security of mobile phones .
Twelve 、 Develop safety awareness
Fraud prevention 、 Prevent personal information disclosure 、 It is important to prevent network attacks , Even an ordinary person , Also have such safety awareness . Many foreign countries have safety awareness training programs , Help every citizen establish safety awareness , Have basic safety disposal ability , Have the necessary security tools .
If you think the above is helpful , Hope you can click thumb to like , Click follow up updates . Your support , Is the driving force of our creation .
You can also browse the following blog to get measures to reduce network security threats :
How can small businesses simply and effectively guard against the threat of cyber attacks
Server Vulnerability fix - Check and close the transmission of blackmail virus SMBv1 agreement
Popularization of safety knowledge : How to make your computer safe on the Internet , Carefree surfing
OT Network security -OT What measures should be taken for client security protection
Popularization of safety knowledge : Telecommuting , Employees must abide by 5 Grand code
版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/02/202202131748593188.html
边栏推荐
- Mapreduce实例(十):ChainMapReduce
- Blue Bridge Cup_ Single chip microcomputer_ Measure the frequency of 555
- Global and Chinese market of airport kiosks 2022-2028: Research Report on technology, participants, trends, market size and share
- Design and implementation of online snack sales system based on b/s (attached: source code paper SQL file)
- 软件负载均衡和硬件负载均衡的选择
- What is an R-value reference and what is the difference between it and an l-value?
- 为什么大学单片机课上51+汇编,为什么不直接来STM32
- 018.有效的回文
- Appears when importing MySQL
- Redis分布式锁实现Redisson 15问
猜你喜欢

A wave of open source notebooks is coming
Full stack development of quartz distributed timed task scheduling cluster

Oom happened. Do you know the reason and how to solve it?
Redis之主从复制
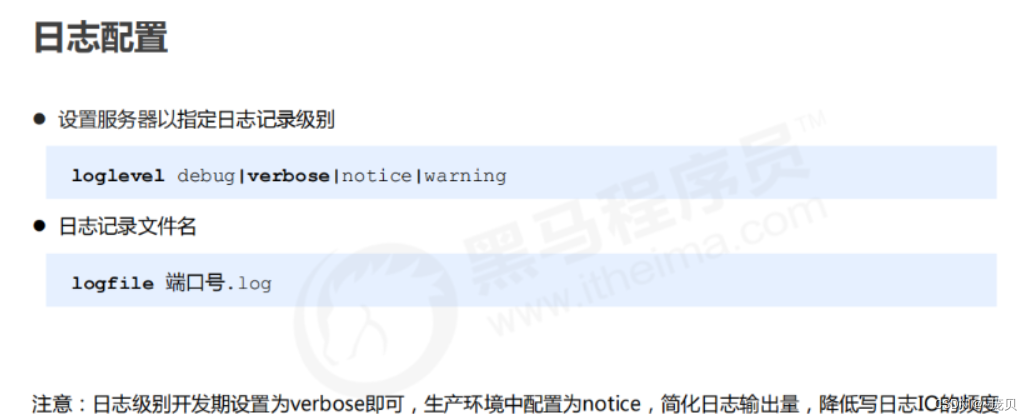
Redis之核心配置
Solve the problem of inconsistency between database field name and entity class attribute name (resultmap result set mapping)
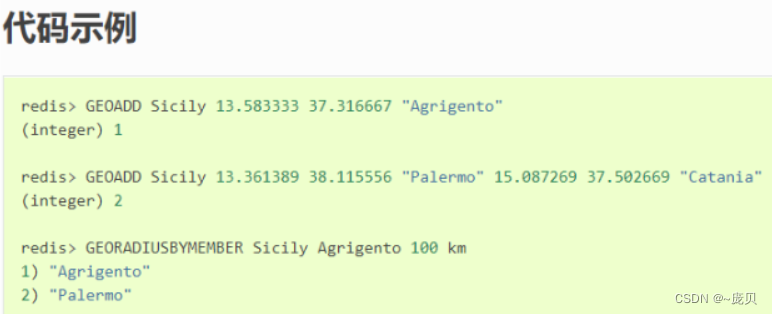
Redis geospatial
基于B/S的医院管理住院系统的研究与实现(附:源码 论文 sql文件)
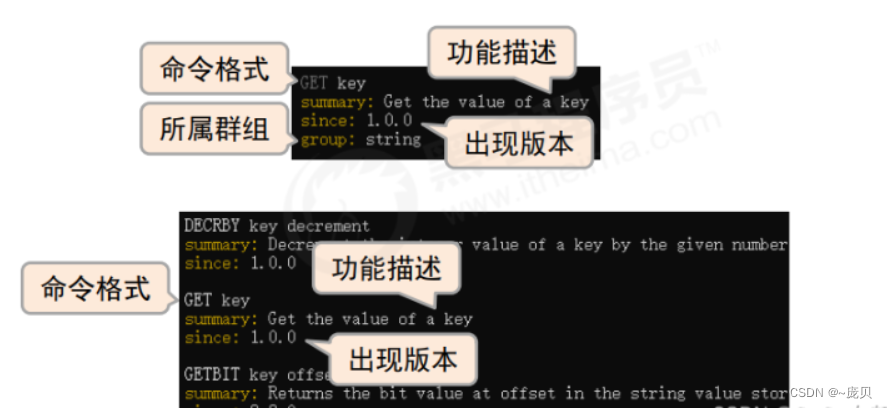
Redis connection redis service command
Heap (priority queue) topic
随机推荐
Kratos ares microservice framework (II)
Solve the problem of inconsistency between database field name and entity class attribute name (resultmap result set mapping)
五月刷题01——数组
Design and implementation of online shopping system based on Web (attached: source code paper SQL file)
Meituan Er Mian: why does redis have sentinels?
May brush question 26 - concurrent search
MapReduce instance (VII): single table join
Interview shock 62: what are the precautions for group by?
Redis' bitmap
Research and implementation of hospital management inpatient system based on b/s (attached: source code paper SQL file)
【深度学习】语义分割:论文阅读(NeurIPS 2021)MaskFormer: per-pixel classification is not all you need
一大波開源小抄來襲
Global and Chinese markets of SERS substrates 2022-2028: Research Report on technology, participants, trends, market size and share
面试突击62:group by 有哪些注意事项?
IDS cache preheating, avalanche, penetration
Sqlmap installation tutorial and problem explanation under Windows Environment -- "sqlmap installation | CSDN creation punch in"
The five basic data structures of redis are in-depth and application scenarios
Withdrawal of wechat applet (enterprise payment to change)
One article read, DDD landing database design practice
Redis之核心配置