当前位置:网站首页>Kratos ares microservice framework (I)
Kratos ares microservice framework (I)
2022-07-06 09:13:00 【~Pompeii】
Catalog
Kratos Ares microservice framework
brief introduction
Kratos A lightweight Go Microservice framework , It contains a large number of microservice related frameworks and tools .
Name from :《 God of war 》 The game is set in Greek mythology , Tell Kratos (Kratos) The adventure of becoming a god of war by mortals and launching the killing of gods .
The goal is
We are committed to providing a complete R & D experience of microservices , After integrating relevant frameworks and tools , The relevant parts of microservice governance can be insensitive to the overall business development cycle , So more focus on business delivery . For every developer , A complete set of Kratos Framework is also a good learning warehouse , You can understand and refer to the technical accumulation and experience in microservices .
principle
- Simple : Don't over design , The code is plain and simple ;
- Universal : Functions of basic library needed by general business development ;
- Efficient : Improve the efficiency of business iterations ;
- Stable : The basic library has high testability , High coverage , It's safe and reliable to practice on the wire ;
- robust : Through good basic library design , Reduce misuse ;
- High performance : High performance , But not specifically for performance hack Optimize , introduce unsafe ;
- Extensibility : Good interface design , To extend the implementation , Or expand the function by adding the basic library directory ;
- Fault tolerance : Design for failure , The introduction of a large number of SRE The understanding of the , High robustness ;
- Tool chain : Contains a lot of tool chains , such as cache Code generation ,lint Tools, etc ;
characteristic
- APIs: Protocol communication to HTTP/gRPC Based on , adopt Protobuf Define ;
- Errors: adopt Protobuf Of Enum Define as error code , And tool generation decision interface ;
- Metadata: In protocol communication HTTP/gRPC in , adopt Middleware Standardized service meta information transmission ;
- Config: Support multiple data sources , Make configuration merge , adopt Atomic Mode supports dynamic configuration ;
- Logger: Standard log interface , It is convenient to integrate three parties log library , And through fluentd Collect the logs ;
- Metrics: Unified index interface , Various index systems can be realized , Default Integration Prometheus;
- Tracing: follow OpenTelemetry Specification definition , To achieve microservice link tracking ;
- Encoding: Support Accept and Content-Type Automatically select content encoding ;
- Transport: General purpose HTTP/gRPC Transport layer , unified Middleware Plug in support ;
- Registry: Implement the unified registry interface , Plug in connection with various registration centers ;
framework

CLI Tools
install
go install github.com/go-kratos/kratos/cmd/kratos/[email protected]
Create project
adopt kratos Command to create a project template :
kratos new helloworld
Use --nomod Add service , share go.mod , Large warehouse mode
kratos new helloworld
cd helloworld
kratos new app/user --nomod
Project structure
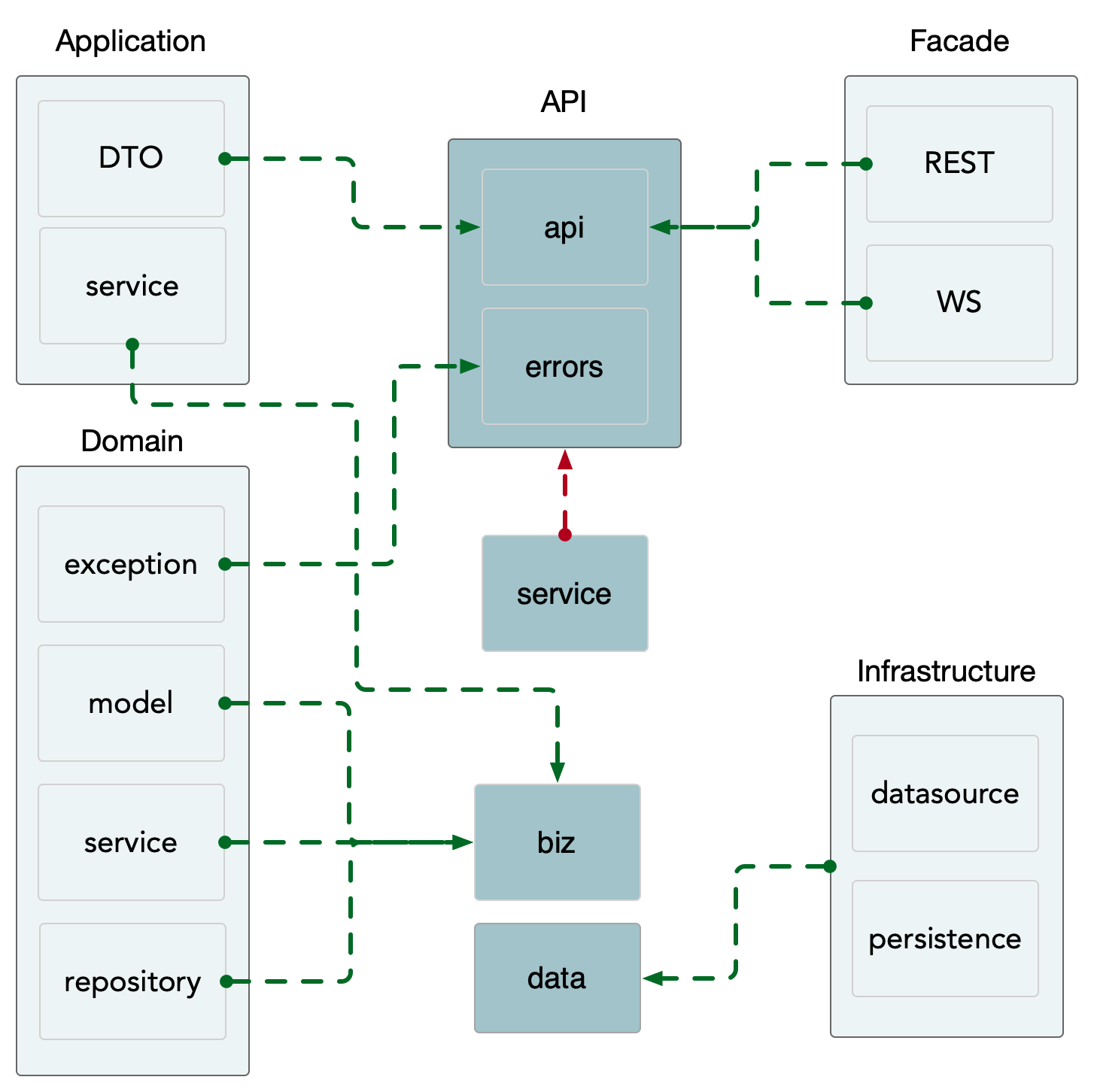
.
├── Dockerfile
├── LICENSE
├── Makefile
├── README.md
├── api // The following maintains the usage of microservices proto Files and the files generated from them go file
│ └── helloworld
│ └── v1
│ ├── error_reason.pb.go
│ ├── error_reason.proto
│ ├── error_reason.swagger.json
│ ├── greeter.pb.go
│ ├── greeter.proto
│ ├── greeter.swagger.json
│ ├── greeter_grpc.pb.go
│ └── greeter_http.pb.go
├── cmd // The entry file for the start of the whole project
│ └── server
│ ├── main.go
│ ├── wire.go // We use wire To maintain dependency injection
│ └── wire_gen.go
├── configs // Some sample configuration files for local debugging are usually maintained here
│ └── config.yaml
├── generate.go
├── go.mod
├── go.sum
├── internal // All the code of the service that is not exposed to the public , The usual business logic is down here , Use internal Avoid misreferencing
│ ├── biz // The assembly layer of business logic , similar DDD Of domain layer ,data similar DDD Of repo, and repo The interface is defined here , Use the principle of dependency inversion .
│ │ ├── README.md
│ │ ├── biz.go
│ │ └── greeter.go
│ ├── conf // For internal use config Structure definition of , Use proto Format generation
│ │ ├── conf.pb.go
│ │ └── conf.proto
│ ├── data // Business data access , contain cache、db Equal package , Realized biz Of repo Interface . We may put data And dao Mix it up ,data Focus on the meaning of business , All it has to do is bring out the domain objects again , We took it out DDD Of infra layer .
│ │ ├── README.md
│ │ ├── data.go
│ │ └── greeter.go
│ ├── server // http and grpc Instance creation and configuration
│ │ ├── grpc.go
│ │ ├── http.go
│ │ └── server.go
│ └── service // Realized api Defined service layer , similar DDD Of application layer , Handle DTO To biz Transformation of domain entities (DTO -> DO), At the same time, cooperate with all kinds of biz Interaction , But complex logic should not be dealt with
│ ├── README.md
│ ├── greeter.go
│ └── service.go
└── third_party // api Relying on a third party proto
├── README.md
├── google
│ └── api
│ ├── annotations.proto
│ ├── http.proto
│ └── httpbody.proto
└── validate
├── README.md
└── validate.proto
Code generation and running
Generate
# Generate all proto Source code 、wire wait
go generate ./...
function
# Run the project
kratos run
# Output
INFO msg=config loaded: config.yaml format: yaml # Default load configs/config.yaml The configuration file
INFO msg=[gRPC] server listening on: [::]:9000 # gRPC Service monitoring 9000 port
INFO msg=[HTTP] server listening on: [::]:8000 # HTTP Service monitoring 8000 port
Test interface
test HTTP Interface
The relevant logic code is located in internal/service/greeter.go
curl 'http://127.0.0.1:8000/helloworld/kratos'
# Output :
{
"message": "Hello kratos"
}
curl 'http://127.0.0.1:8000/helloworld/error'
# Output
{
"code": 404,
"reason": "USER_NOT_FOUND",
"message": "user not found: error",
"metadata": {
}
}
边栏推荐
- The carousel component of ant design calls prev and next methods in TS (typescript) environment
- UML图记忆技巧
- KDD 2022论文合集(持续更新中)
- Nacos 的安装与服务的注册
- [MySQL] limit implements paging
- Advance Computer Network Review(1)——FatTree
- I-BERT
- [shell script] - archive file script
- [MySQL] multi table query
- 一篇文章带你了解-selenium工作原理详解
猜你喜欢

In depth analysis and encapsulation call of requests
LeetCode41——First Missing Positive——hashing in place & swap
Reids之删除策略
Mongodb installation and basic operation
Selenium+Pytest自动化测试框架实战(下)
![[OC-Foundation框架]---【集合数组】](/img/b5/5e49ab9d026c60816f90f0c47b2ad8.png)
[OC-Foundation框架]---【集合数组】
![[sword finger offer] serialized binary tree](/img/e2/25c9322da3acda06c4517b0c50f81e.png)
[sword finger offer] serialized binary tree

Pytest's collection use case rules and running specified use cases
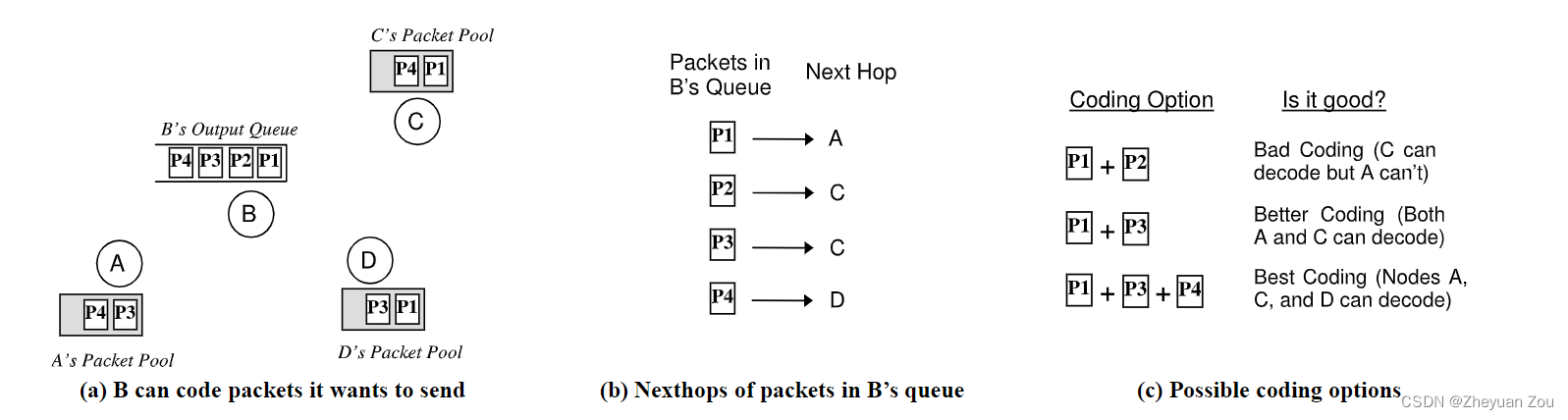
Advanced Computer Network Review(5)——COPE

Once you change the test steps, write all the code. Why not try yaml to realize data-driven?
随机推荐
Redis之五大基础数据结构深入、应用场景
不同的数据驱动代码执行相同的测试场景
Intel distiller Toolkit - Quantitative implementation 2
UML图记忆技巧
Pytest parameterization some tips you don't know / pytest you don't know
I-BERT
[today in history] February 13: the father of transistors was born The 20th anniversary of net; Agile software development manifesto was born
Li Kou daily question 1 (2)
如何正确截取字符串(例:应用报错信息截取入库操作)
Different data-driven code executes the same test scenario
BMINF的后训练量化实现
Advanced Computer Network Review(4)——Congestion Control of MPTCP
Post training quantification of bminf
Ijcai2022 collection of papers (continuously updated)
Advanced Computer Network Review(5)——COPE
自定义卷积注意力算子的CUDA实现
Philosophical enlightenment from single point to distributed
[OC-Foundation框架]---【集合数组】
LeetCode:26. Remove duplicates from an ordered array
[MySQL] limit implements paging