当前位置:网站首页>The number one malware in January 2022: lokibot returned to the list, and emotet returned to the top
The number one malware in January 2022: lokibot returned to the list, and emotet returned to the top
2022-07-02 02:33:00 【Netgoods world】
Check Point Research Pointed out that , Information stealing procedure Lokibot Return to the most rampant malware ranking , and Emotet Instead of Trickbot Top the list . As the number one vulnerability most often exploited ,Apache Log4j It's still raging .
2022 year 2 month , The world's leading provider of network security solutions Check Point Software Technology Co., Ltd ( Nasdaq stock code :CHKP) Threat Intelligence Check Point Research Published its 2022 year 1 The latest edition of the month 《 Global threat index 》 The report . The researchers report that ,Emotet Now it will occupy the top place for a long time Trickbot Squeeze out the first place , Become the most rampant malware this month , Affecting the world 6% Enterprises and institutions . The fact proved that ,Log4j Still rampant , The global 47.4% Our institutions suffer , education / The research industry remains the primary target .
Only two and a half months after returning to the list ,Emotet Has jumped to the top . This notorious botnet is mainly spread through phishing emails containing malicious attachments or links .Trickbot The increasing rampancy of this malware has boosted the increasing use of this malware . meanwhile ,Dridex It has completely fallen out of the top ten malware list , In its place Lokibot, This information theft program is used to obtain email credentials 、 Cryptocurrency wallet password and FTP Server and other data .
Check Point Vice president of research and development of software technology company Maya Horowitz Express :“Emotet A comeback is expected . It is a kind of runaway malware , Therefore, it is difficult to detect , And it uses a variety of methods to infect the network , This will only further aggravate the threat situation . This month, ,Dridex Disappear from our top ten malware list , and Lokibot Then appear again .Lokibot Take advantage of the victims' busiest moments , Spread through carefully disguised phishing emails . These threats and Log4j The ongoing battle for vulnerabilities highlights cross network 、 Cloud 、 The importance of deploying the best security protection for mobile and user endpoints .”
Check Point Research (CPR) Pointed out that , This month, , education / The research industry remains the primary target of attack in the world , Second, the government / Military departments and ISP/MSP.“Apache Log4j Remote code execution ” It is still the most frequently exploited vulnerability , The global 47.4% Our institutions suffer , The second is “Web Server Exposed Git Repository information disclosure ”, Affecting the world 45% Institutions .“HTTP Header remote code execution ” Ranked third in the list of most frequently exploited vulnerabilities , The global scope of influence is 42%.
The number one malware family
* The arrow indicates the ranking change compared with the previous month .
This month, ,Emotet Is the most rampant malware , The global 6% Of enterprises and institutions have been affected , Next to that is Trickbot and Formbook, Have affected the whole world 4% and 3% Institutions .
1. ↑ Emotet - Emotet It is an advanced modular Trojan horse that can spread itself .Emotet Once used as a bank Trojan horse , Recently, it has been used as a propagator of other malware or malicious attacks . It uses a variety of methods and evasion techniques to ensure long-term stability and avoid detection . Besides , It can also be spread through phishing spam that contains malicious attachments or links .
2. ↓ Trickbot - Trickbot It is a modular botnet and bank Trojan , Keep adding new features 、 Properties and propagation vectors . This makes it a flexible and customizable malware , It is widely used in multi-purpose attacks .
3. ↓ Formbook - Formbook It's an information theft program , Available from various Web Get credentials in the browser 、 Collect screenshots 、 Monitor and record keystrokes , And according to its C&C Command download and execute files .
The most frequently exploited vulnerability
This month, ,“Apache Log4j Remote code execution ” It is still the most frequently exploited vulnerability , The global 47.4% Our institutions suffer , The second is “Web Server Exposed Git Repository information disclosure ”, Affecting the world 45% Institutions and enterprises .“HTTP Header remote code execution ” Ranked third in the list of most frequently exploited vulnerabilities , The global scope of influence is 42%.
1. Apache Log4j Remote code execution (CVE-2021-44228) - One exists in Apache Log4j Remote Code Execution Vulnerability in . Remote attackers can use this vulnerability to execute arbitrary code on the affected system .
2. Web Server Exposed Git Repository information disclosure - Git An information disclosure vulnerability reported by the repository . Once the attacker successfully exploits the vulnerability , It will make the user inadvertently cause the disclosure of account information .
3. HTTP Header remote code execution (CVE-2020-10826、CVE-2020-10827、CVE-2020-10828、CVE-2020-13756) - HTTP Headers allow clients and servers to pass along HTTP Other information requested . Remote attackers may use vulnerable HTTP Header runs arbitrary code on the infected machine .
Mainly mobile malware
This month, ,xHelper Ranked first among the most rampant mobile malware , The second is AlienBot and FluBot.
1. xHelper - since 2019 year 3 Malicious applications that have disappeared since September , Used to download other malicious applications and display malicious advertisements . The application can be invisible to users , And reinstall after uninstallation .
2. AlienBot - AlienBot The malware family is a family that targets Android Device malware as a service (MaaS), It allows remote attackers to first inject malicious code into legitimate financial applications . An attacker can gain access to the victim's account , And finally completely control its equipment .
3. FluBot - FluBot It is spread through phishing short messages Android Botnet malware , Usually posing as logistics distribution brand . Once the user clicks the link in the message ,FluBot Will quickly install and access all sensitive information on the phone .
Check Point《 Global threat impact index 》 And its 《ThreatCloud The roadmap 》 be based on Check Point ThreatCloud Written from intelligence data .ThreatCloud The Real-time Threat Intelligence provided comes from the deployment in the global network 、 Hundreds of millions of sensors on endpoints and mobile devices .AI The engine and Check Point Information and Research Department of software technology company Check Point Research Our exclusive research data further enrich the intelligence content .
To view 1 A complete list of the top ten malware families in August , Please visit Check Point Blog .
About Check Point Research
Check Point Research Can be Check Point Software Customers and the entire intelligence community provide leading cyber Threat Intelligence .Check Point The research team is responsible for collecting and analyzing ThreatCloud Stored global cyber attack data , In order to prevent hackers at the same time , Ensure that all Check Point All products enjoy the latest protection measures . Besides , The team consists of 100 A number of analysts and researchers , Be able to work with other security vendors 、 Law enforcement agencies and various computer security emergency response teams cooperate .
About Check Point Software Technology Co., Ltd
Check Point Software Technology Co., Ltd. is a leading provider of network security solutions for governments and enterprises around the world .Check Point Infinity Solution portfolio for malware 、 The capture rate of ransomware and other threats is at the industry-leading level , It can effectively protect enterprises and public organizations from the fifth generation network attacks .Infinity It contains three core pillars , It can provide excellent security protection and fifth generation threat protection across enterprise environments :Check Point Harmony( For remote users );Check Point CloudGuard( Automatically protect the cloud environment );Check Point Quantum( Effectively protect network boundaries and data centers )— All of this is through the most comprehensive 、 Intuitive unified safety management for control .Check Point Provide protection for more than 100000 enterprises of all sizes .
边栏推荐
- A quick understanding of analog electricity
- Es interview questions
- 大厂裁员潮不断,双非本科出身的我却逆风翻盘挺进阿里
- flutter 中間一個元素,最右邊一個元素
- LFM signal denoising, time-frequency analysis, filtering
- Questions d'entrevue
- What is the principle of bone conduction earphones and who is suitable for bone conduction earphones
- es面试题
- es面試題
- Leetcode face T10 (1-9) array, ByteDance interview sharing
猜你喜欢

CVPR 2022 | Dalian Institute of technology proposes a self calibration lighting framework for low light level image enhancement of real scenes
![[opencv] - comprehensive examples of five image filters](/img/c7/aec9f2e03a17c22030d7813dd47c48.png)
[opencv] - comprehensive examples of five image filters
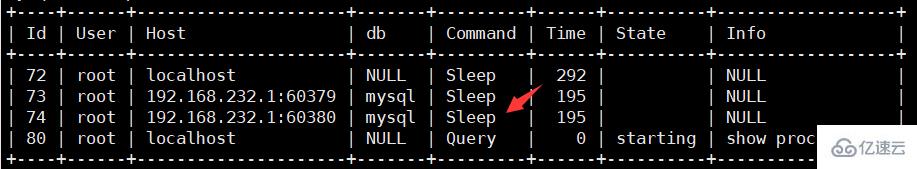
How to execute an SQL in MySQL

STM32__ 05 - PWM controlled DC motor
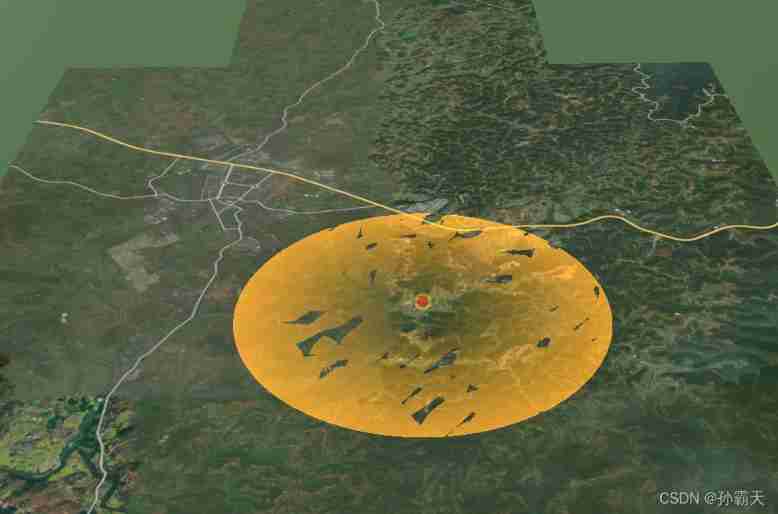
Cesium dynamic diffusion point effect

An analysis of circuit for quick understanding

AR增强现实可应用的场景
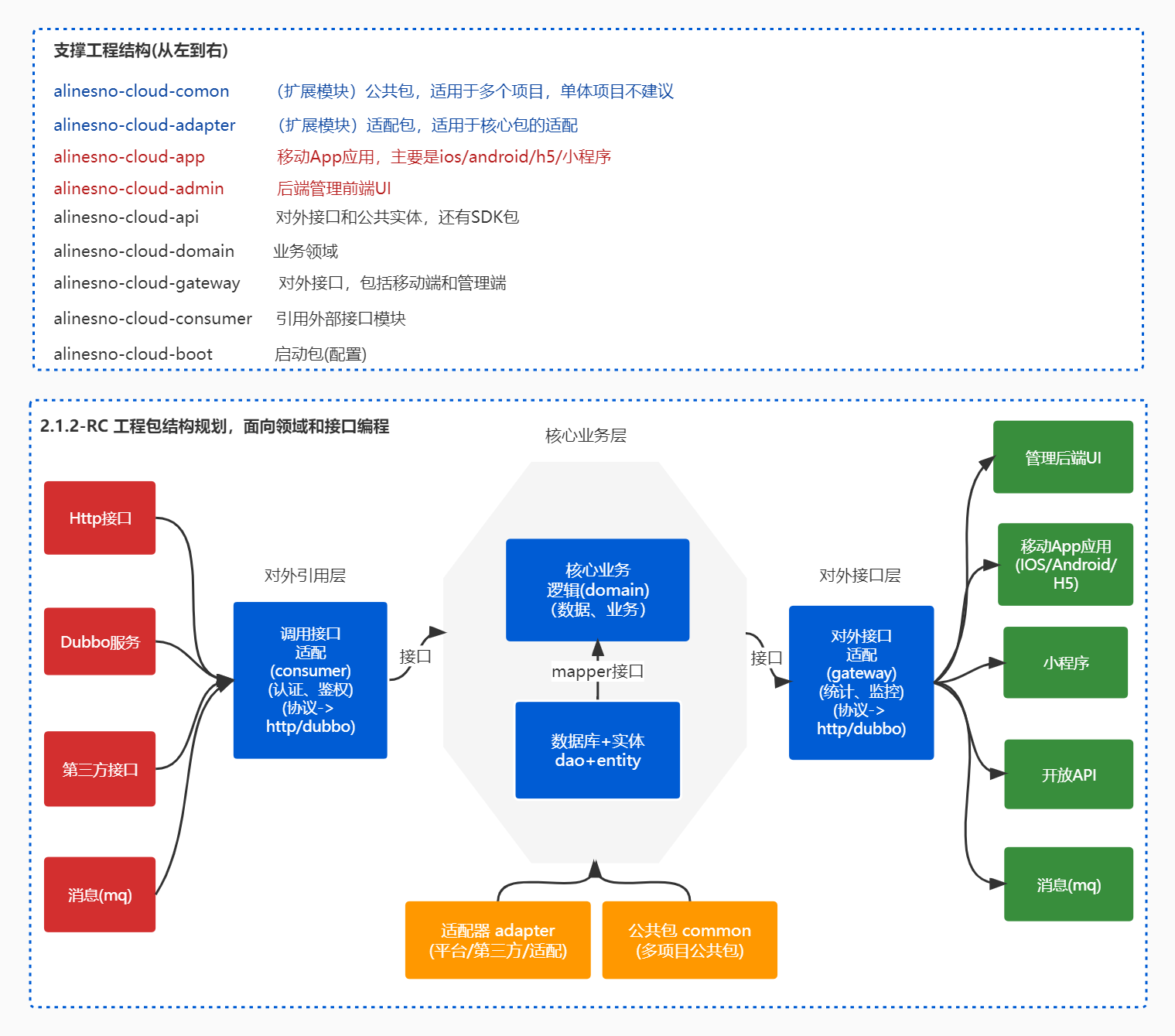
研发中台拆分过程的一些心得总结
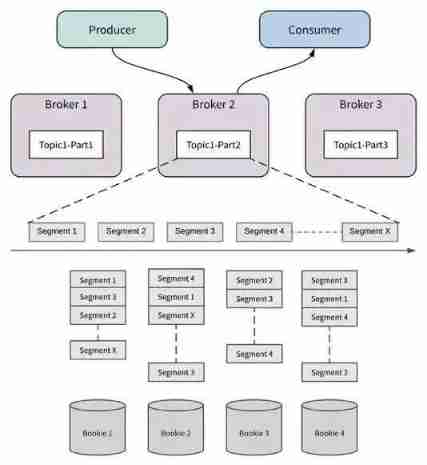
New programmer magazine | Li Penghui talks about open source cloud native message flow system

超图iServer rest服务之feature查询
随机推荐
Kibana操控ES
An analysis of circuit for quick understanding
结婚后
Sword finger offer 47 Maximum value of gifts
AR增强现实可应用的场景
QT实现界面跳转
Sword finger offer 42 Maximum sum of continuous subarrays
C write TXT file
As a software testing engineer, will you choose the bank post? Laolao bank test post
【带你学c带你飞】day 5 第2章 用C语言编写程序(习题2)
Quality means doing it right when no one is looking
Realize the code scanning function of a custom layout
how to come in an investnent bank team
pytest 测试框架
how to add one row in the dataframe?
Email picture attachment
What is the function of the headphone driver
Cesium dynamic diffusion point effect
Websocket + spingboot realize code scanning login
[pit] how to understand "parameter fishing"