当前位置:网站首页>[MySQL from introduction to proficiency] [advanced chapter] (IV) MySQL permission management and control
[MySQL from introduction to proficiency] [advanced chapter] (IV) MySQL permission management and control
2022-07-04 14:28:00 【Man Nong Feige】
Hello! , I'm Manon Feige , Thank you for reading this article , Welcome to three links with one button .
1. Python Basic column , Basic knowledge in a net ,9.9 Yuan can't buy a loss , I can't buy it . Python From entry to mastery
️ 2. Python Crawler column , Systematically learn the knowledge points of reptiles .9.9 Yuan can't buy a loss , I can't buy it .python Reptile beginner level
️ 3. Ceph actual combat , Everything from principle to actual combat . Ceph actual combat
️ 4. Java Introduction to high concurrency programming , Punch in to learn Java High concurrency . Java Introduction to high concurrency programming
5. Take a stroll around the community , Weekly benefits , There are surprises every week . Manon Feige community , Leap plan
The whole network has the same name 【 Manon Feige 】 Welcome to your attention , personal VX: wei158556
List of articles
1. brief introduction
In the last article, we introduced MySQL User creation in , Modify and delete . This article goes on to learn MySQL Authority management and control .
2. Environmental Science
| Environmental Science | edition |
|---|---|
| Red Hat | 4.8.5-39 |
| MySQL | 5.7 |
3. Rights management
MySQL The simple understanding of permission management is MySQL Allow you to do what is within your power , You can't cross the line , For example, only you are allowed to perform SELECT operation , Then you can't carry out UPDATE operation , Only allow you to connect from one machine MySQL, Then you can't connect from any other machine except that one MySQL. After creating a new account , By default, only information_schema Database permissions , If you want this user to operate other databases , This requires assigning specific permissions to users .
3.1. Permission list
MySQL What kind of authority do you have ?
mysql> show privileges;
GRANT and REVOKE The permissions that can be used in the statement are as follows :
| jurisdiction | user The corresponding column in the table | Scope of authority |
|---|---|---|
| CREATE | Create_priv | database 、 A table or index |
| Drop | Drop_priv | database , Table or view |
| GRANTOPTION | Grant_priv | database , Table or stored procedure |
| REFERENCES | Reference_priv | Database or table |
| EVENT | Event_priv | database |
| ALTRE | Alter_priv | database |
| DELETE | Delete_priv | surface |
CREATE and DROP jurisdiction, You can create new databases and tables 、 Or delete ( move away ) Existing databases and tables , If you will MySQL In the database DROP Permission granted to a user , The user can delete MySQL Access permission saved table .SELECT、INSERT、UPDATE and DELETE jurisdictionAllow operations on existing tables in a database .SELECT jurisdictionThey are only used when they actually retrieve rows from a table .INDEX jurisdictionAllow indexes to be created or deleted 、INDEX Applicable to existing tables , If you have a table CREATE jurisdiction , You can go to CREATE TABLE Include the index definition in the statement .ALTER jurisdictionhave access to ALTER TABLE To change the table structure and rename the table .CREATE ROUTINE jurisdictionTo create a saved program ( Functions and programs ),ALTER ROUTINE Permissions are used to change and delete saved programs ,EXECUTE jurisdictionUsed to execute saved programs .GRANT jurisdictionAllow authorization to other users , It can be used in database 、 Tables and procedures .FILE jurisdictionSo that users can use LOAD DATA INFILE and SELECT … INTO OUTFILE Statement to read or write to a file on the server , Any person who is granted FILE Users with permissions can read or write MySQL Any file on the server .
MySQL How permissions are distributed
| Authority distribution | Possible setting permissions |
|---|---|
| Table permissions | SELECT、INSERT、UPDATE、DELETE、CREATE、DROP、GRANT、REFERENCES、INDEX、ALTER |
| Column permissions | SELECT、INSERT、UPDATE、REFERENCES |
| Process authority | EXEUTE、ALTER ROUTINE、GRANT |
2.2. The principle of granting authority
Access control is mainly for security reasons , So we need to follow a few empirical principles :
- Grant only the minimum permissions that meet your needs , Prevent users from doing bad things , For example, users only need to query , Then just select Authority is enough . There is no need to give users UPDATE、INSERT perhaps DELETE jurisdiction .
- When creating users
Restrict the user's Login Host, Generally, it is limited to designated IP Or Intranet IP paragraph . - For each user
Set a password that meets the password complexity. Clean up unwanted users regularly, Reclaim permissions or delete users .
2.3. Grant authority
There are ways to authorize users 2 Kind of , By putting Role grants user authorization and Authorize users directly . The user is the user of the database , We can grant users access to resources in the database by , To control users' access to the database , Eliminate safety hazards .
Authorization command :
GRANT jurisdiction 1, jurisdiction 2,... jurisdiction n ON Database name . The name of the table TO user name @ Address of the user [IDENTIFIED BY ' Password '];
If the user is not found during authorization , A new user will be created directly .
such as :
- to zhang3 The user uses the local command line mode , grant test The authority to query, insert, delete and modify all tables under this library .
GRANT SELECT,INSERT,DELETE,UPDATE ON test.* TO zhang3 IDENTIFIED BY '[email protected]';
- Granted to log in through the network zhangsan user , Full permissions for all libraries, all tables , The password is set to [email protected], Only... Is not included here grant Authority .
GRANT ALL PRIVILEGES ON *.* TO zhangsan@'%' IDENTIFIED BY '[email protected]';
have access to GRANT Add permissions to users repeatedly , Authority stack , For example, you first add a SELECT jurisdiction , then Add another one to the user INSERT jurisdiction , Then the user has SELECT and INSERT jurisdiction .
2.4. View permissions
- View current user permissions
SHOW GRANTS;
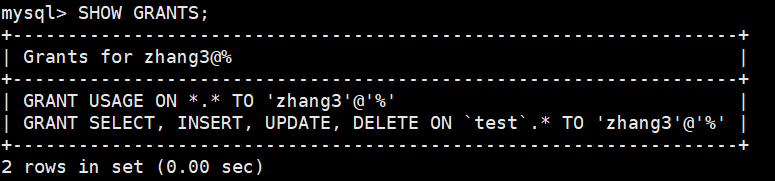
2. View the global permissions of a user
SHOW GRANTS FOR 'user'@' The host address '
It is recommended that you try to use the database's own role and user mechanism to control access rights , Don't use it easily root account number , because root The account and password are not safe in the code , In case of leakage , The database will be completely unprotected .
2.5. Take back authority
Withdrawing permissions means canceling some permissions that have been given to users , Taking back users' unnecessary permissions can ensure the security of the system to a certain extent .MySQL Use in REVOKE sentence Cancel some permissions of the user , Use REVOKE After taking back the authority , User account records will be from db、host、tables_priv and column_priv In the table to delete , But user account records are still user Save in the table ( Delete user The user information in the table is used DROP USER sentence ).
Be careful : The user account is being removed from user Before deleting the table , All permissions of the corresponding user should be revoked .
Withdraw the order :
REVOKE jurisdiction 1, jurisdiction 2,..., jurisdiction n ON Database name . The name of the table FROM User name @ Address of the user ;
give an example :
# Take back all permissions of the whole database and table
REVOKE ALL PRIVILEGES ON *.* FROM zhang3@'%';
and ,MySQL The authority control function of is very perfect , Should be used as much as possible , Can improve efficiency , And it's safe and reliable .
3. Permissions on the table
MySQL Server pass Permissions on the table To control users' access to the database , The authority list is stored in mysql database in ,MySQL The database system will give each user corresponding permissions according to the contents of these permission tables . The most important of these permission tables is user surface 、db surface . besides , also table_priv surface 、column_priv surface and proc_priv surface . stay MySQL Startup time , The server reads the permission information in these databases into memory .
| Table name | describe |
|---|---|
| user | User account and permission information |
| global_grants | Dynamic global authorization |
| db | Database level permissions |
| tables_priv | Surface level permissions |
| columns_priv | Column level permissions |
| procs_priv | Stored procedure and function permissions |
| proxics_priv | Delegate user permissions |
Let's say db Table as an example .
among ,zhang3 This account has test The authority of checking, deleting, modifying and inserting under the Library .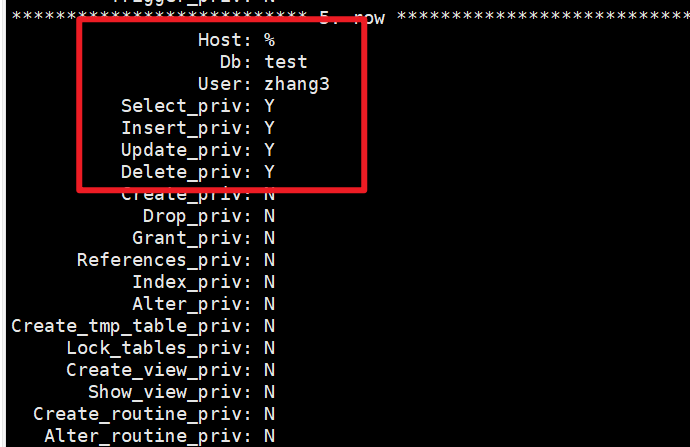
summary
This article introduces in detail how to assign permissions to users and withdraw permissions
边栏推荐
- Leetcode T48: rotating images
- 92.(cesium篇)cesium楼栋分层
- Nowcoder rearrange linked list
- Map of mL: Based on Boston house price regression prediction data set, an interpretable case is realized by using the map value to the LIR linear regression model
- 实战解惑 | OpenCV中如何提取不规则ROI区域
- Some problems and ideas of data embedding point
- The implementation of OSD on rk1126 platform supports color translucency and multi-channel support for Chinese
- Industrial Internet has greater development potential and more industry scenarios
- Real time data warehouse
- Ml: introduction, principle, use method and detailed introduction of classic cases of snap value
猜你喜欢
富文本编辑:wangEditor使用教程
Chapter 17 process memory
Digi重启XBee-Pro S2C生产,有些差别需要注意
Why should Base64 encoding be used for image transmission
ML之shap:基于boston波士顿房价回归预测数据集利用shap值对XGBoost模型实现可解释性案例
Stm32f1 and stm32subeide programming example -max7219 drives 8-bit 7-segment nixie tube (based on GPIO)
学内核之三:使用GDB跟踪内核调用链
一文概览2D人体姿态估计
Practical puzzle solving | how to extract irregular ROI regions in opencv
NowCoder 反转链表
随机推荐
Talk about 10 tips to ensure thread safety
尊重他人的行为
去除重複字母[貪心+單調棧(用數組+len來維持單調序列)]
opencv3.2 和opencv2.4安装
迅为IMX6Q开发板QT系统移植tinyplay
Rich text editing: wangeditor tutorial
MySQL stored procedure exercise
[MySQL from introduction to proficiency] [advanced chapter] (V) SQL statement execution process of MySQL
Stm32f1 and stm32subeide programming example -max7219 drives 8-bit 7-segment nixie tube (based on GPIO)
去除重复字母[贪心+单调栈(用数组+len来维持单调序列)]
What is the difference between Bi financial analysis in a narrow sense and financial analysis in a broad sense?
ML之shap:基于boston波士顿房价回归预测数据集利用Shap值对LiR线性回归模型实现可解释性案例
数据埋点的一些问题和想法
Use of arouter
数据湖(十三):Spark与Iceberg整合DDL操作
Redis daily notes
一种架构来完成所有任务—Transformer架构正在以一己之力统一AI江湖
Golang uses JSON unmarshal number to interface{} number to become float64 type (turn)
R语言ggplot2可视化:gganimate包创建动态折线图动画(gif)、使用transition_reveal函数在动画中沿给定维度逐步显示数据
關於miui12.5 紅米k20pro用au或者povo2出現問題的解决辦法